Method for detecting authenticity and validity of account
An authentic and effective technology, applied in the Internet field, can solve the problems that the main body of the enterprise cannot judge whether the fake account holder is the same person, and the interests of the business are damaged, so as to achieve risk control, reduce pressure, and ensure security and stability. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
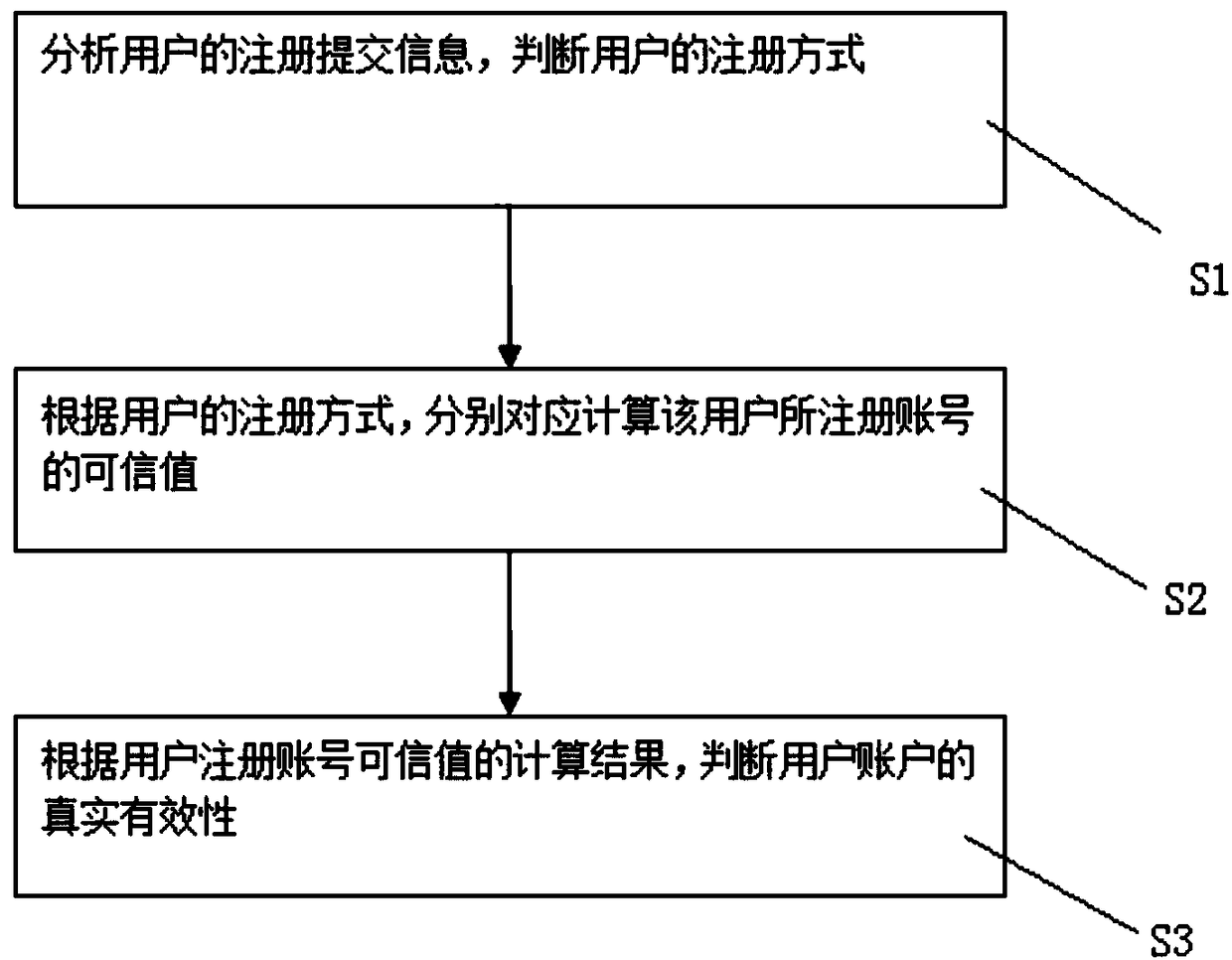
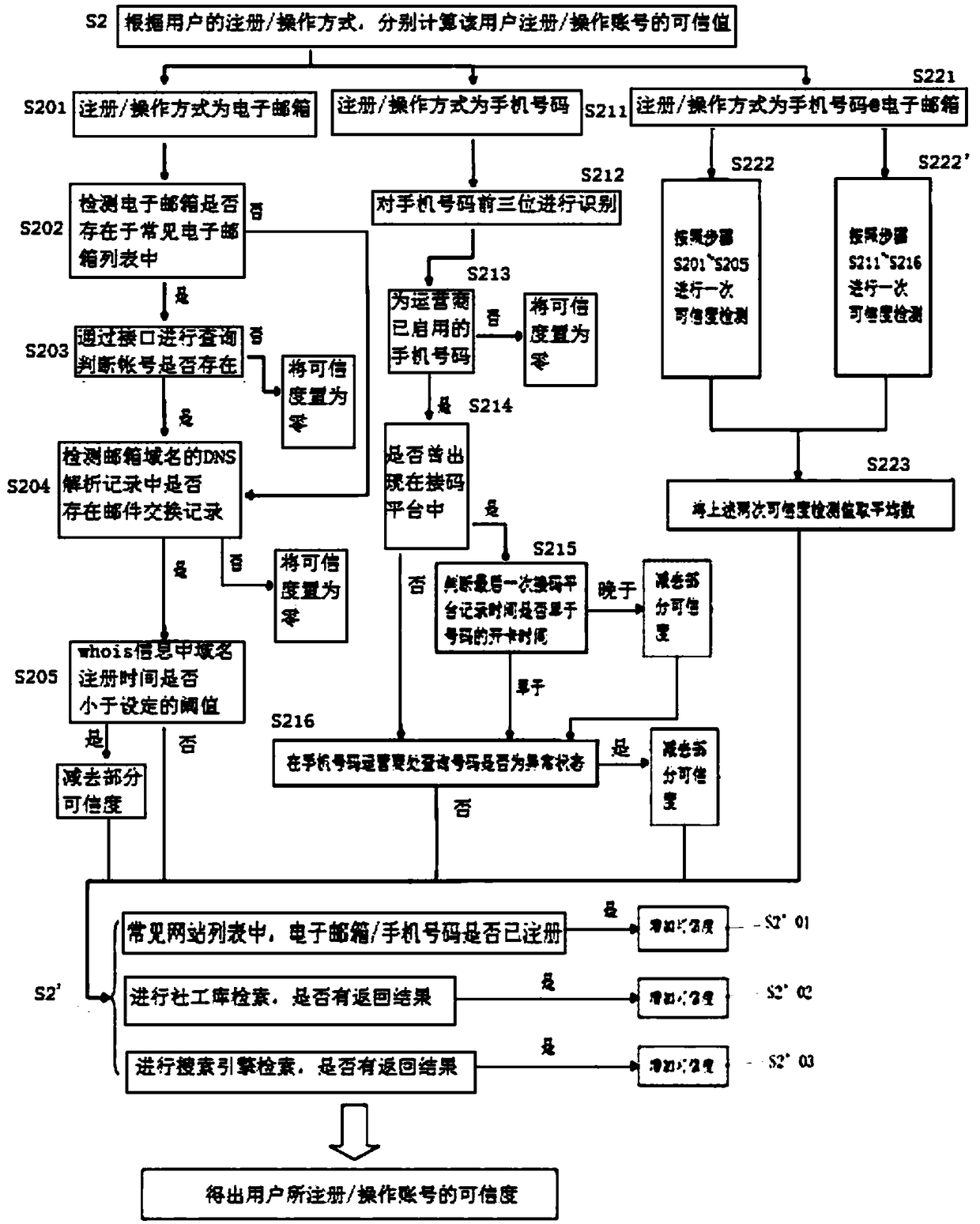
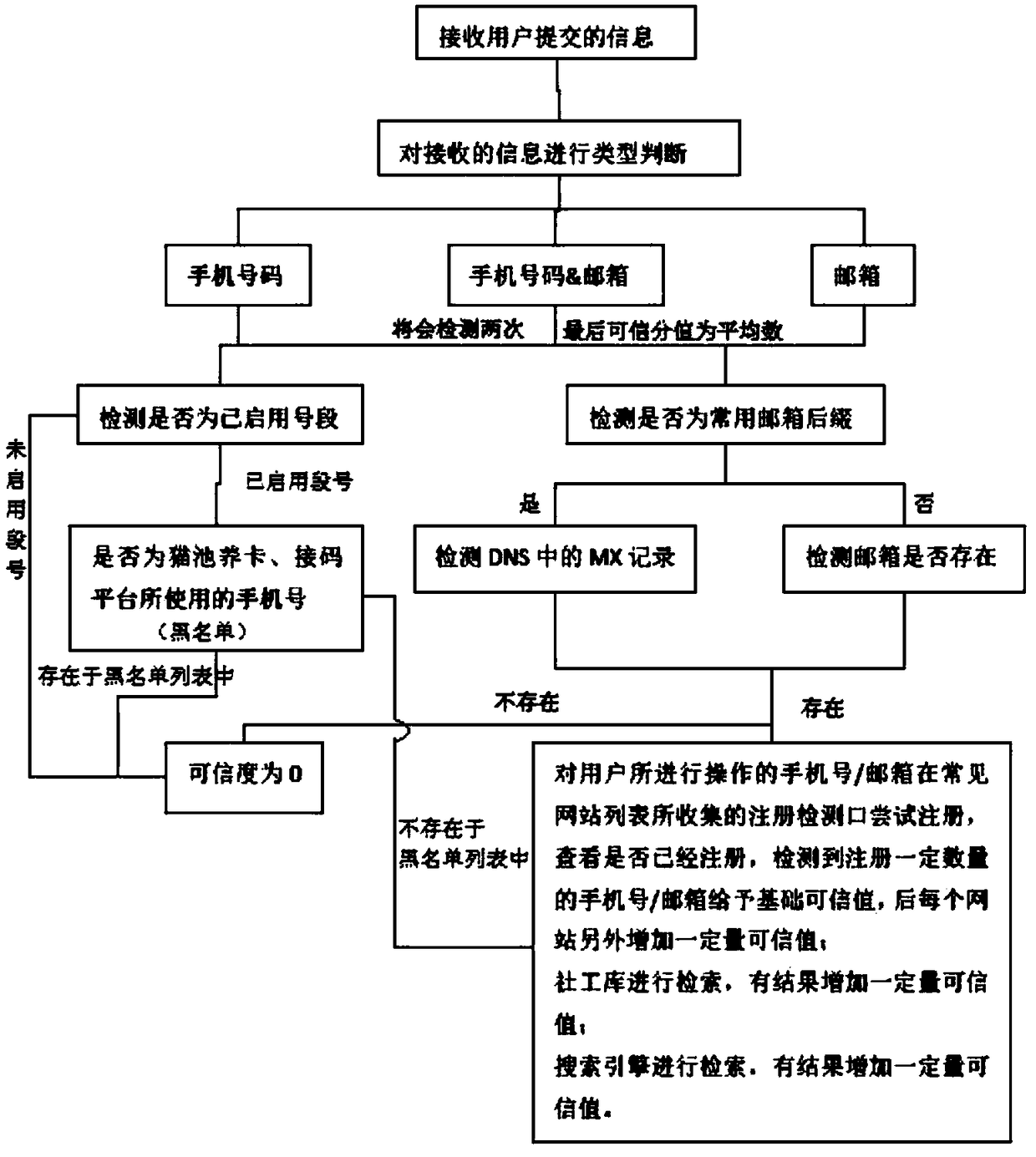
[0040] Embodiments of the present invention are described in detail below, examples of which are shown in the drawings, wherein the same or similar reference numerals denote the same or similar elements or elements having the same or similar functions throughout. The embodiments described below by referring to the figures are exemplary only for explaining the present invention and should not be construed as limiting the present invention.
[0041] Below, the technical solution of the present invention and its specific application scenarios will be further described in detail in combination with specific embodiments:
[0042] In reality, some lawbreakers take advantage of loopholes in software and programs to exchange for preferential promotions in various channels such as travel platforms, online lending platforms, electronic malls, online banking, and credit cards at low or even zero cost. The promotional dividends generated, this behavior is vividly called "sweeping wool", a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com