Intel SGX state consistency protection method and system
A state preservation and state technology, applied in the field of cloud computing and information security, can solve problems such as poor platform migration effect and poor performance, and achieve improved fluency and reliability, strong versatility and portability, and good platform migration effect. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
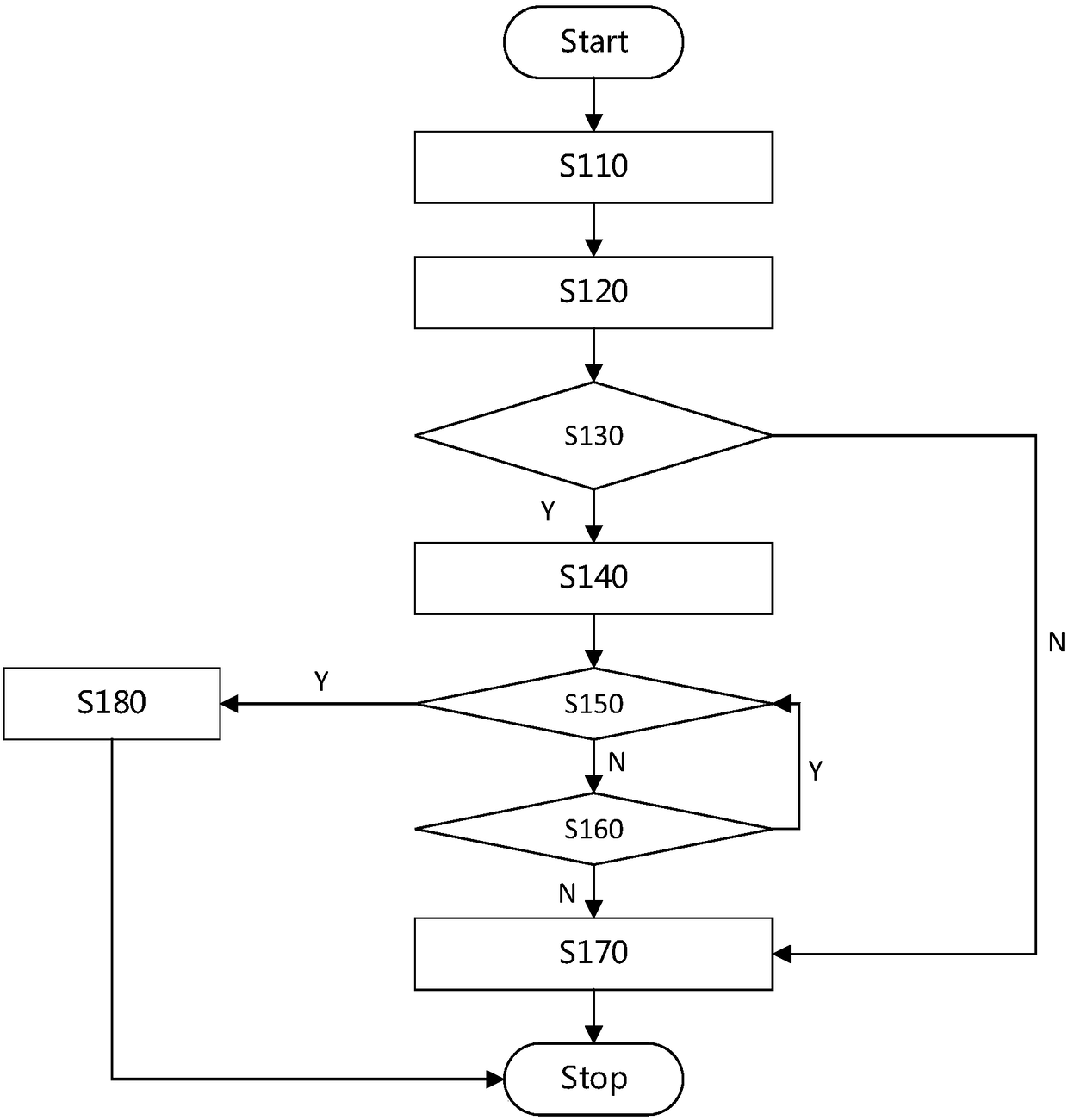
[0032] This embodiment discloses a state consistent protection method for a central processing unit capable of building a security zone, preferably, especially a state consistent protection method for Intel SGX. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0033] Preferably, in this method, the central processing unit can support the construction of at least one security zone. Preferably, the security zone is a trusted execution environment built by the central processing unit. The code and data in the security zone can be protected from malicious software attacks, and neither privileged nor unprivileged software can access the security zone. Preferably, the central processing unit can construct several security zones for concurrent execution. For example, a CPU that supports Intel SGX builds several enclaves that execute concurrently. Alternatively, the central processing u...
Embodiment 2
[0056] This embodiment is a further improvement on Embodiment 1, and repeated content will not be repeated here. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0057] The invention also discloses a communication system, which is suitable for executing each method step recorded in the invention, so as to achieve the expected technical effect.
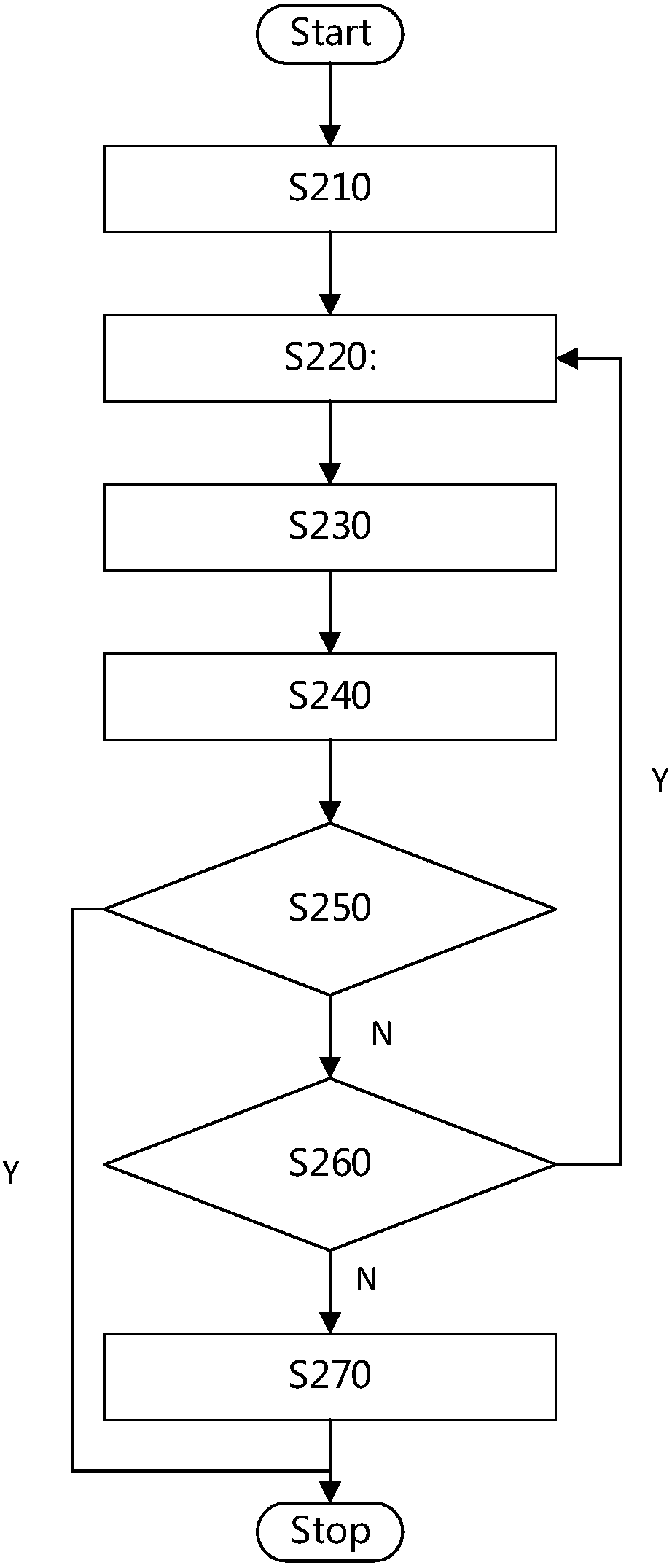
[0058] According to a preferred embodiment, a communication system may include a first communication terminal and a second communication terminal. Preferably, both the first central processing unit of the first communication terminal and the second central processing unit of the second communication terminal can support the construction of at least one security zone. Preferably, the first communication terminal communicates remotely with the second communication terminal providing services thereto. Preferably, the second communication ter...
Embodiment 3
[0063]This embodiment is a further improvement on Embodiments 1 and 2 or their combination, and repeated content will not be repeated here. In the case of no conflict or contradiction, preferred implementation manners of other embodiments may serve as supplements to this embodiment.
[0064] This embodiment discloses a state consistent protection system based on central processing unit hardware, and the system is suitable for executing each method step described in the present invention to achieve expected technical effects.
[0065] According to a preferred embodiment, the system may include a first central processing unit and a second central processing unit. Preferably, both the first central processing unit and the second central processing unit support building at least one security zone. Preferably, the first central processing unit communicates remotely with the second central processing unit providing services thereto.
[0066] According to a preferred embodiment, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com