Access control method, access network element, core network element and user equipment
A technology for access control and user equipment, applied in electrical components, network traffic/resource management, wireless communication, etc., can solve problems such as low system transmission efficiency, congestion, network element overload, etc., and achieve the effect of alleviating overload or congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0160] This example is used to illustrate the access restriction process initiated by the radio access network itself.
[0161] In this example, an LTE access network is used as an example, and a network element of the radio access network is an eNB.
[0162] Such as Figure 5 As shown, the access restriction methods provided in this example include:
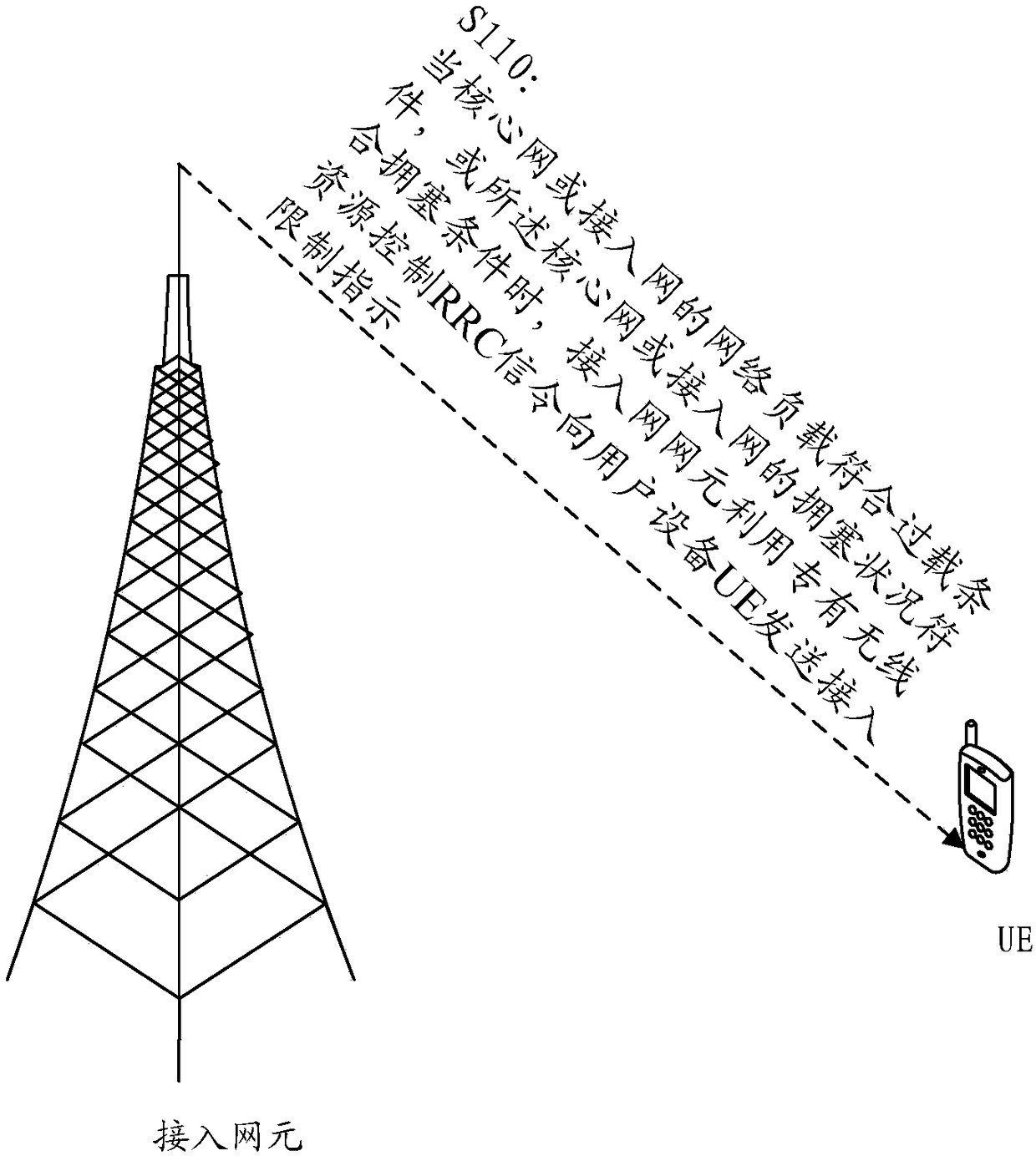
[0163] Step 101: the eNB judges whether its own load level is high or overloaded, and if so, the eNB initiates access restriction on the UE.
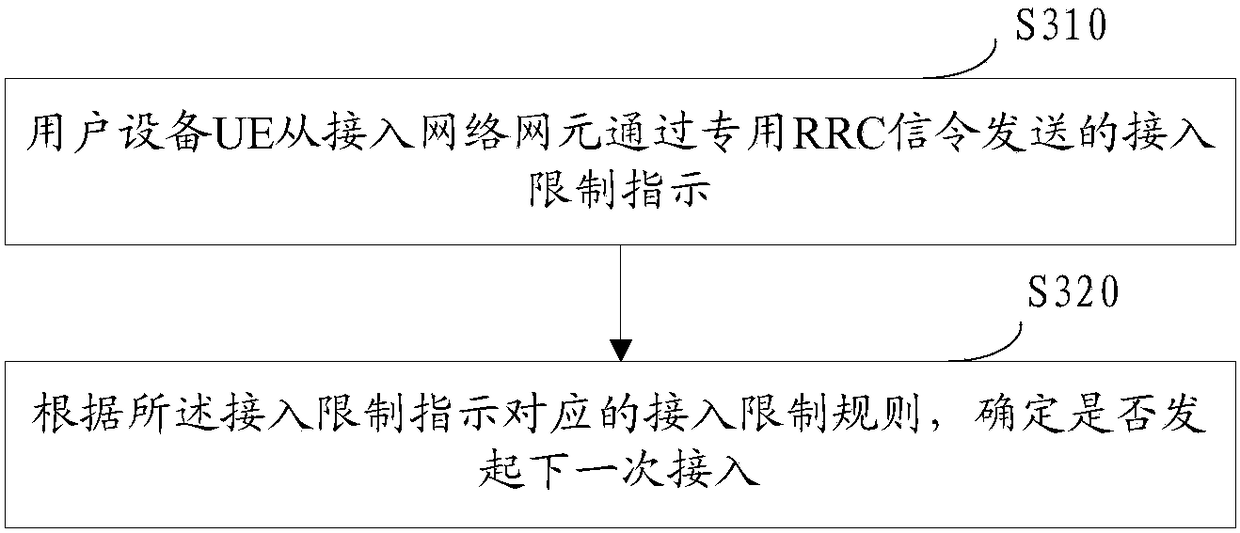
[0164] Step 102: For a UE that newly initiates an access request or a connection re-establishment request, the eNB can restrict the UE's access behavior through the RRC connection rejection process or the RRC re-establishment rejection process, and the RRC connection rejection signaling or the RRC connection re-establishment rejection signaling Carry specific access restriction rules and / or access restriction parameters; for a UE in the RRC connection state, the eNB can release the RRC ...
example 2
[0170] This example is used to illustrate the access restriction process initiated by the wireless access network according to the instructions of the core network elements;
[0171] This example takes the LTE access network as an example, the network element of the radio access network is an eNB, and the network element of the core network is an MME (Mobility Management Entity).
[0172] Such as Figure 6 As shown, the access restriction methods provided in this example include:
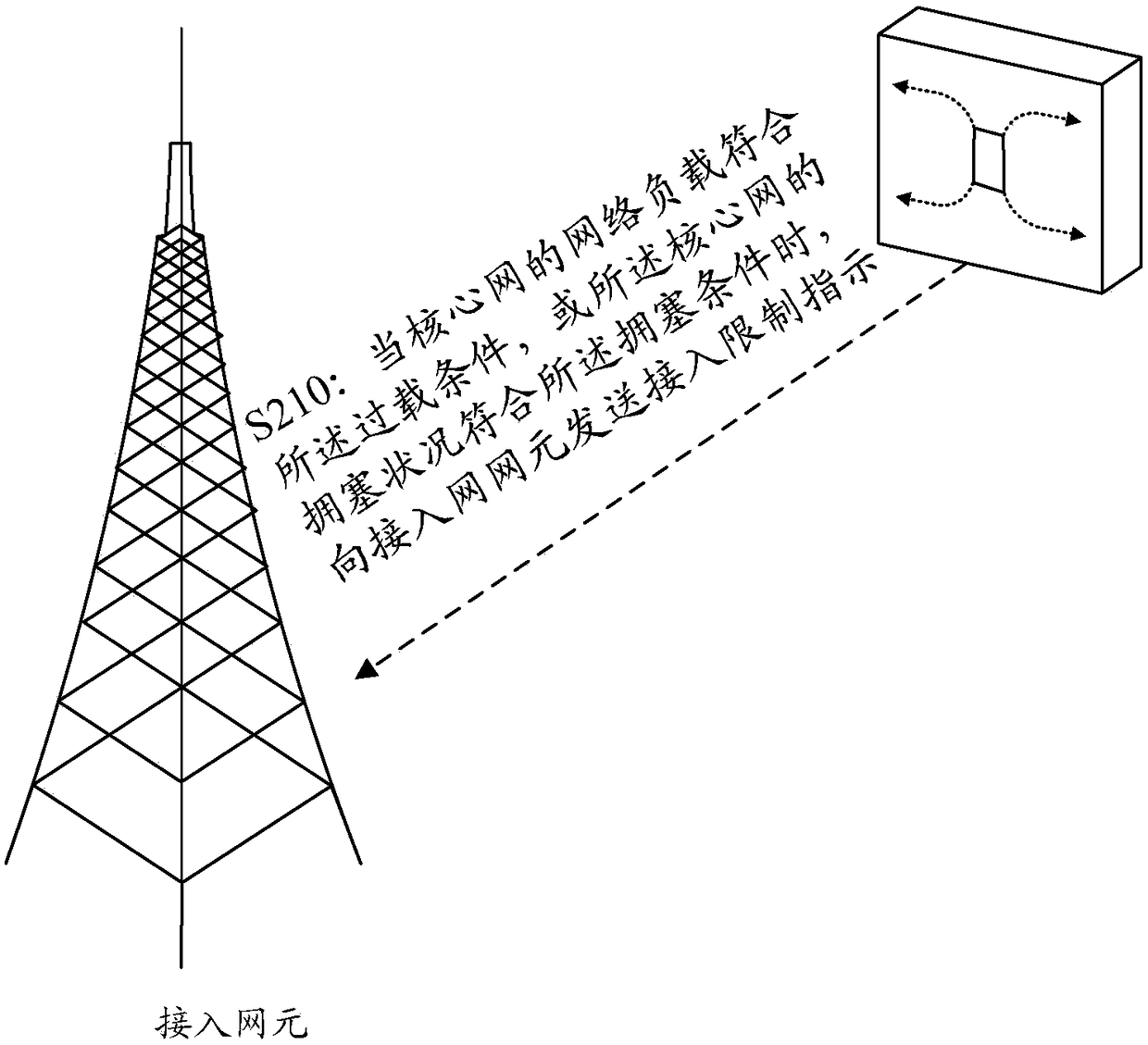
[0173] Step 201: The MME judges whether its own load level is high or overloaded, and if so, sends overload control information to the eNB through the interface with the eNB, and the information can be sent through the Overload start message or through other S1 interface signaling. The overload control information includes access restriction rules and or access restriction parameters;
[0174] Step 202: The eNB performs access control on UEs in its own cell according to the received overload contr...
example 3
[0177] This example is used to illustrate which access restriction methods and effects can be formed by combining different access restriction indications.
[0178]This implementation specifically explains in examples 1 and 2, what methods can be included in the access restriction rules and / or access restriction parameters contained in the RRC connection rejection signaling or RRC connection release signaling by the eNB, and what kind of access control can be achieved Effect;
[0179] Combining this example with examples 1 and 2, a complete and detailed example including access control procedures and access control parameters can be formed.
[0180] The access restriction rules and / or access restriction parameters contained in the RRC connection rejection signaling, RRC connection reestablishment rejection signaling or RRC connection release signaling by the eNB include the following categories:
[0181] (1) It is forbidden to use UP or legacy to initiate mo-data, or mo-Excep...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com