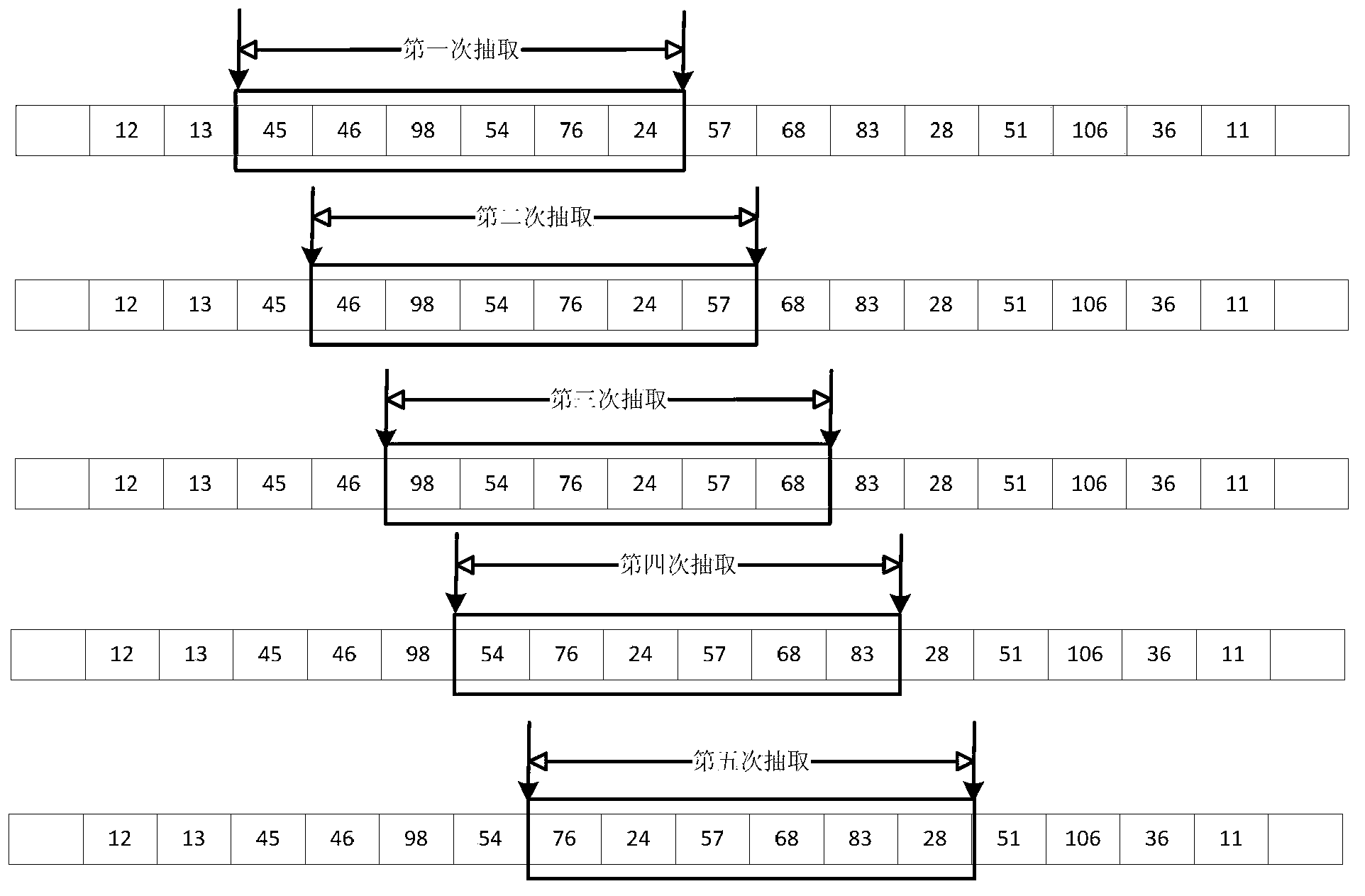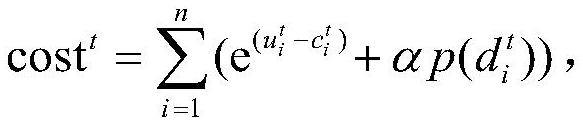Patents
Literature
39results about How to "Relieve overload" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
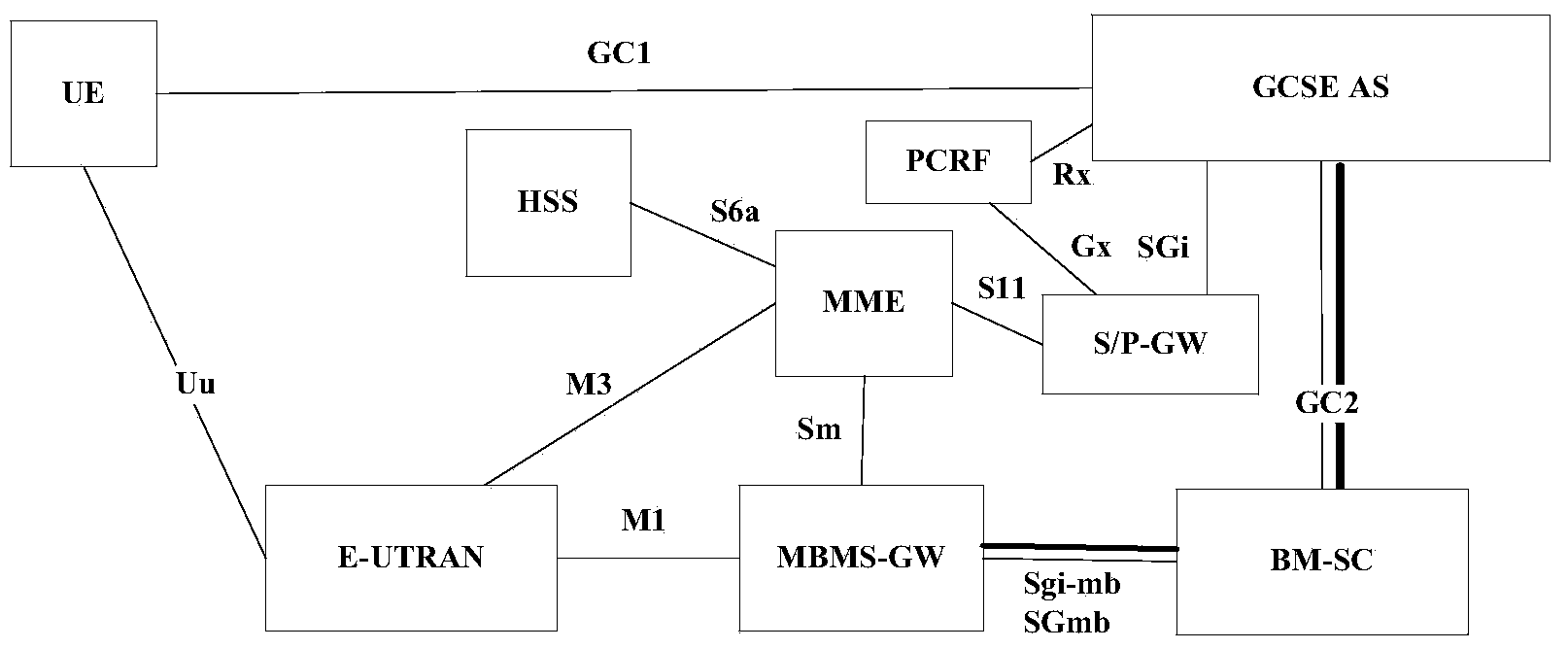
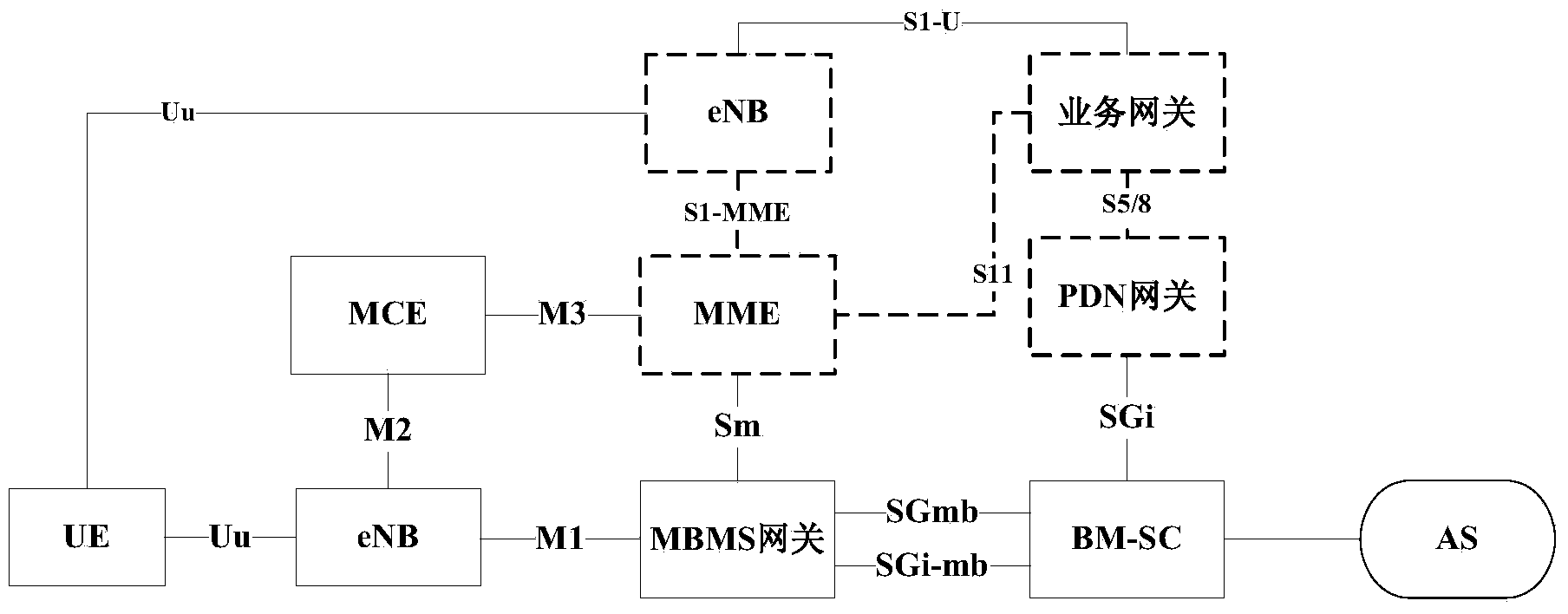
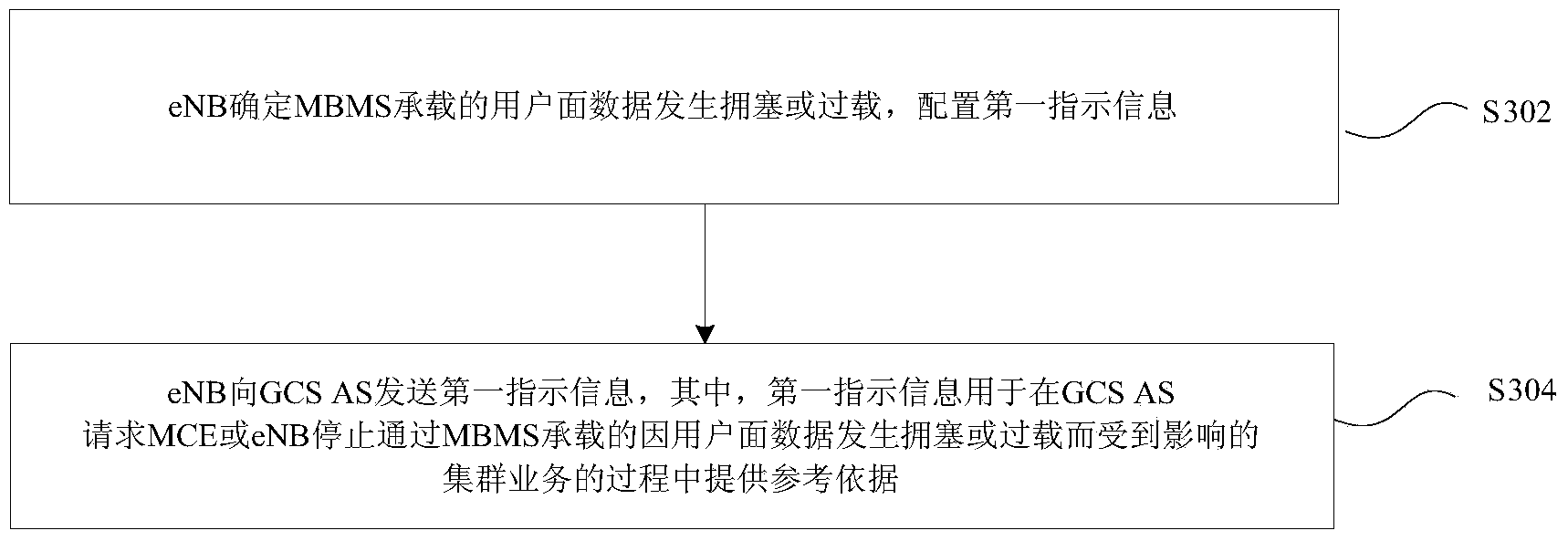
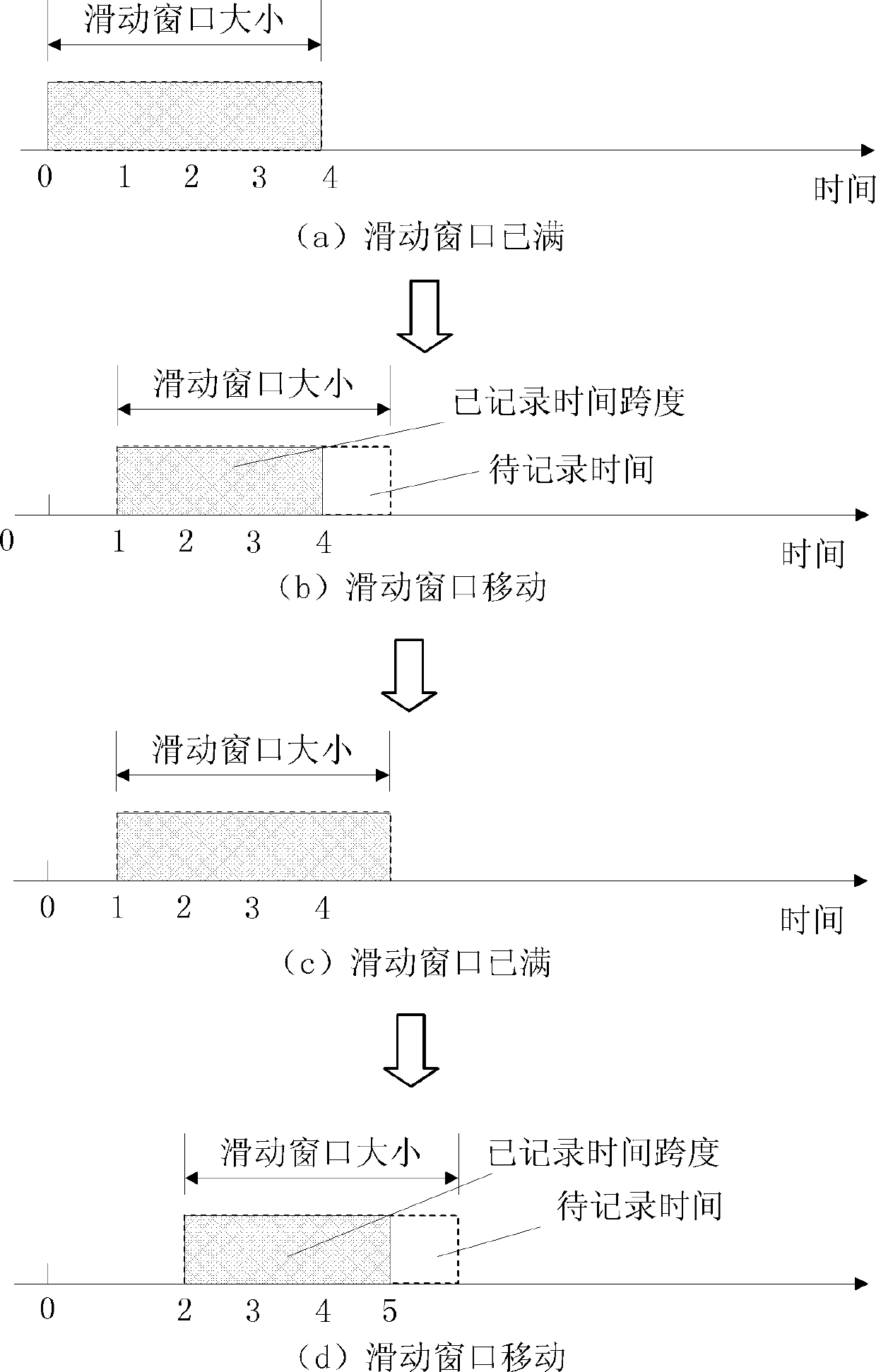
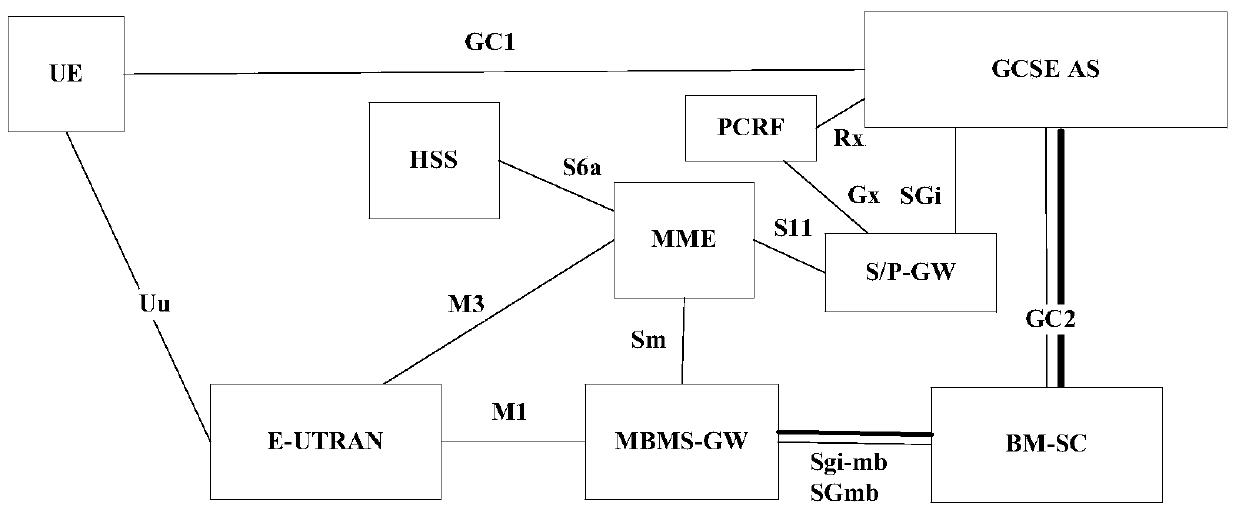
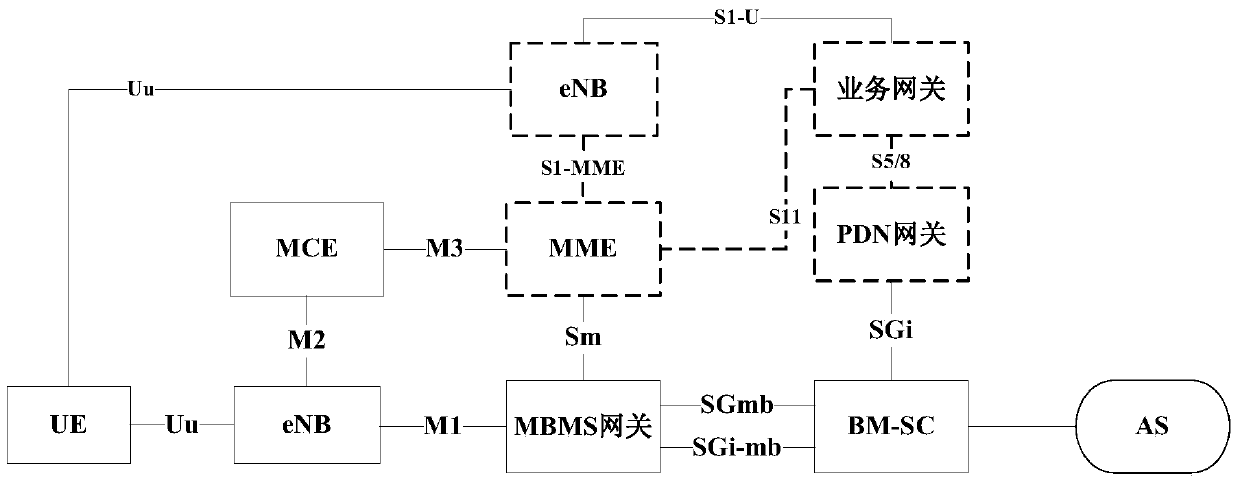
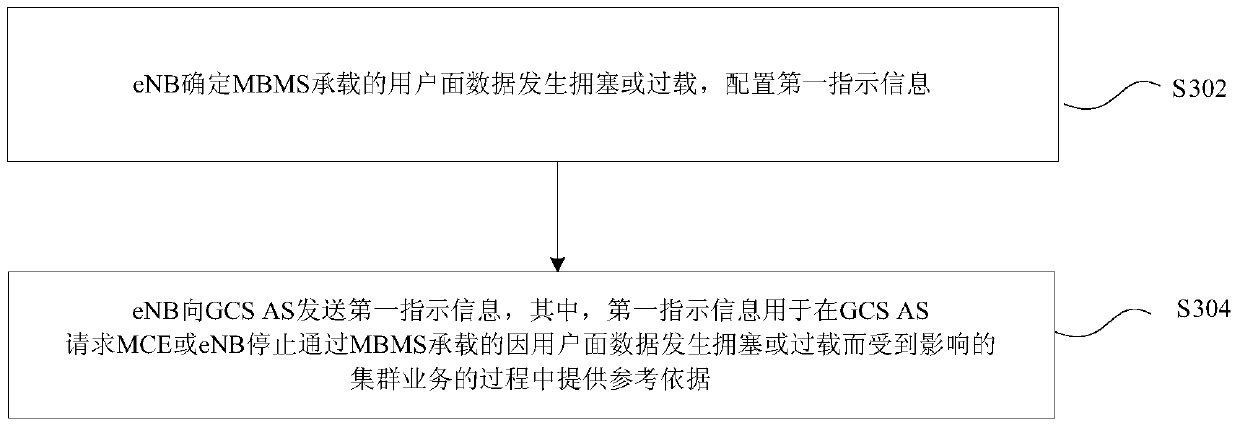
Indication information determination and processing method and device and request message processing method and device
InactiveCN104270725AReduce the impact of UEs in congested/overloaded areasReduce congestionNetwork traffic/resource managementComputer security arrangementsMultimedia Broadcast Multicast ServiceApplication server
The invention discloses an indication information determination and processing method and device and a request message processing method and device. The indication information determination method includes the steps that whether user plane data of a multimedia broadcast multicast service (MBMS) bearer are congested or overloaded is determined, and first indication information is configured; the first indication information is sent to a group communication service (GCS) application server (AS), wherein the first indication information is used for providing reference data in the process that the GCS AS requests an MCE or an eNB to stop passing of cluster service, affected by the fact that the user plane data are congested or overloaded, of the MBMS bearer. According to the technical scheme, congestion or overload of the MBMS bearer can be relieved, so that influences on non-congestion or non-overload area UE are reduced.
Owner:ZTE CORP
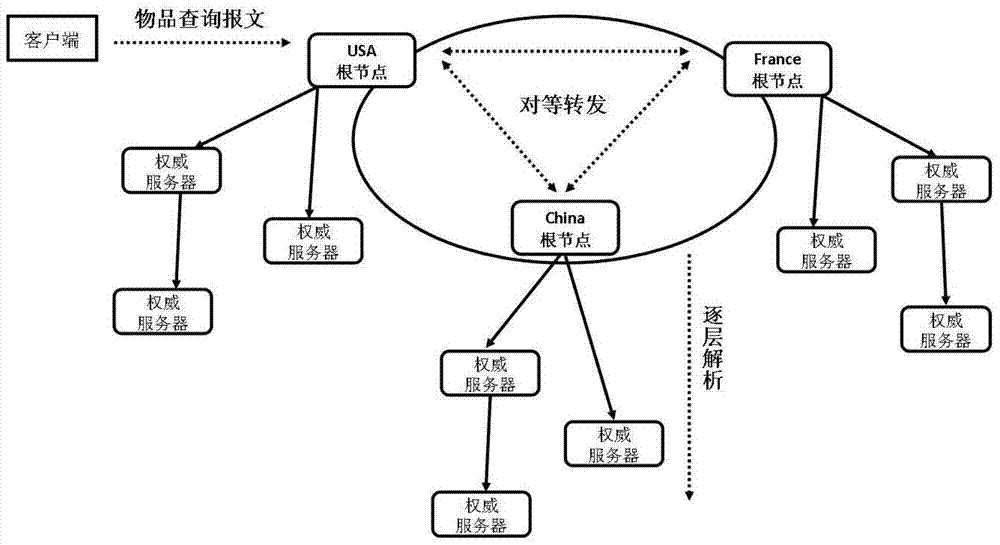
Analytic method for multi-root peer-to-peer identity of internet of things
ActiveCN103248726AMaintain political authorityGuarantee good developmentUser identity/authority verificationData switching by path configurationClient-sideSingle point
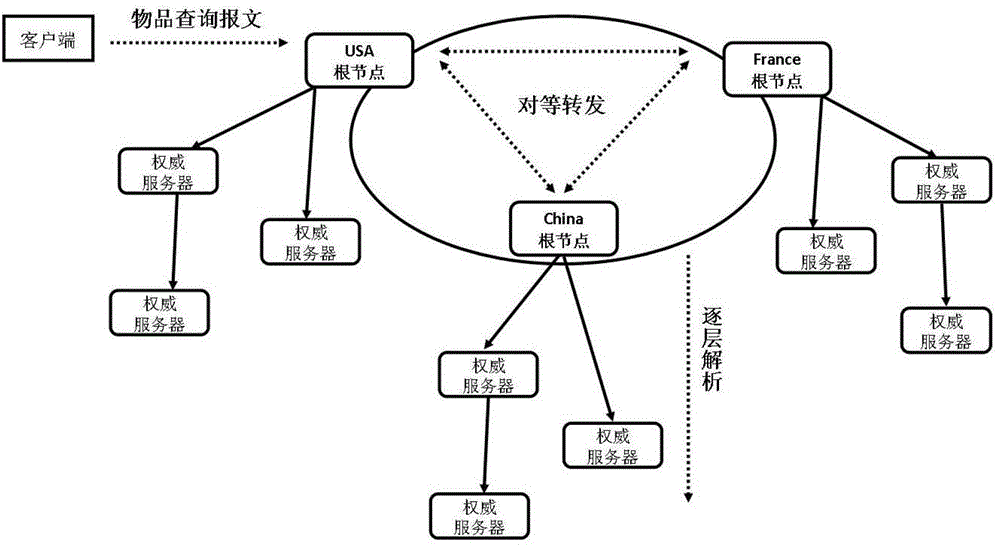
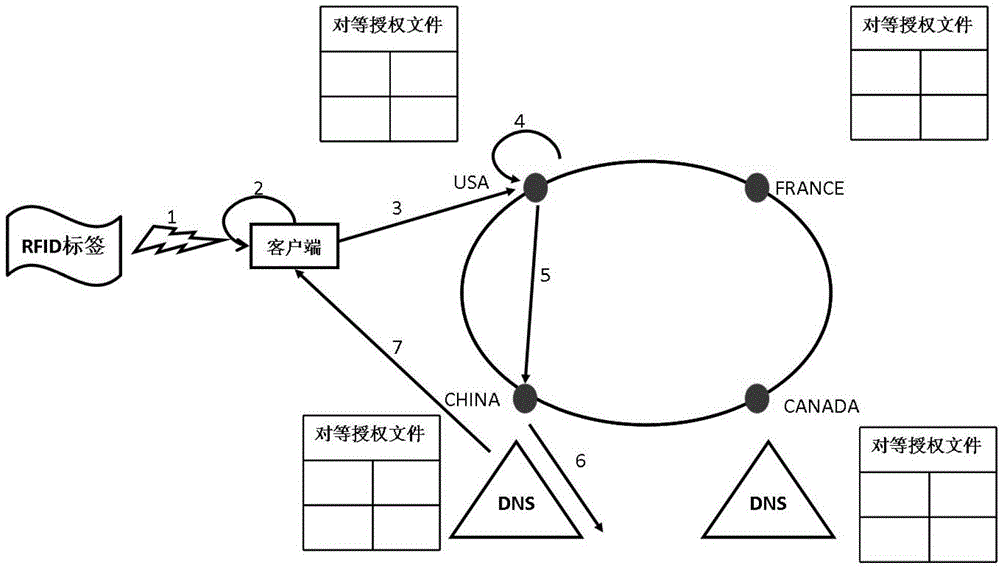
The invention relates to an analytic method for multi-root peer-to-peer identity of internet of things, which comprises the steps that peer-to-peer authorization files are established and stored into analytic root nodes, and each analytic root node edits a DNAME record in a root area space according to the corresponding peer-to-peer authorization file; a client side acquires the object identity code of an item, converts the object identity code of the item into a URI in a standard FQDN form and sends an item object identity code query message to a local analytic root node NX; the NX extracts a country code from the message, and forwards the message to a root node NY having the right to analyze the message according to the DNAME record; the NY carries out layer-by-layer analysis based on a DNS (domain name system) until a certain authoritative server feeds back a name authority pointer record containing an information server address; and finally, the client side is communicated with a corresponding information server to acquire the detailed attribute information of the item. The analytic method can overcome the defect of single point failure existing in the existing analytic system and improve the query efficiency of the object identity of the item.
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Source driver applied to TFT-LCD, drive circuit and drive method
ActiveCN104867474ARelieve overloadMitigate the pull effectStatic indicating devicesData displayDigital-to-analog converter
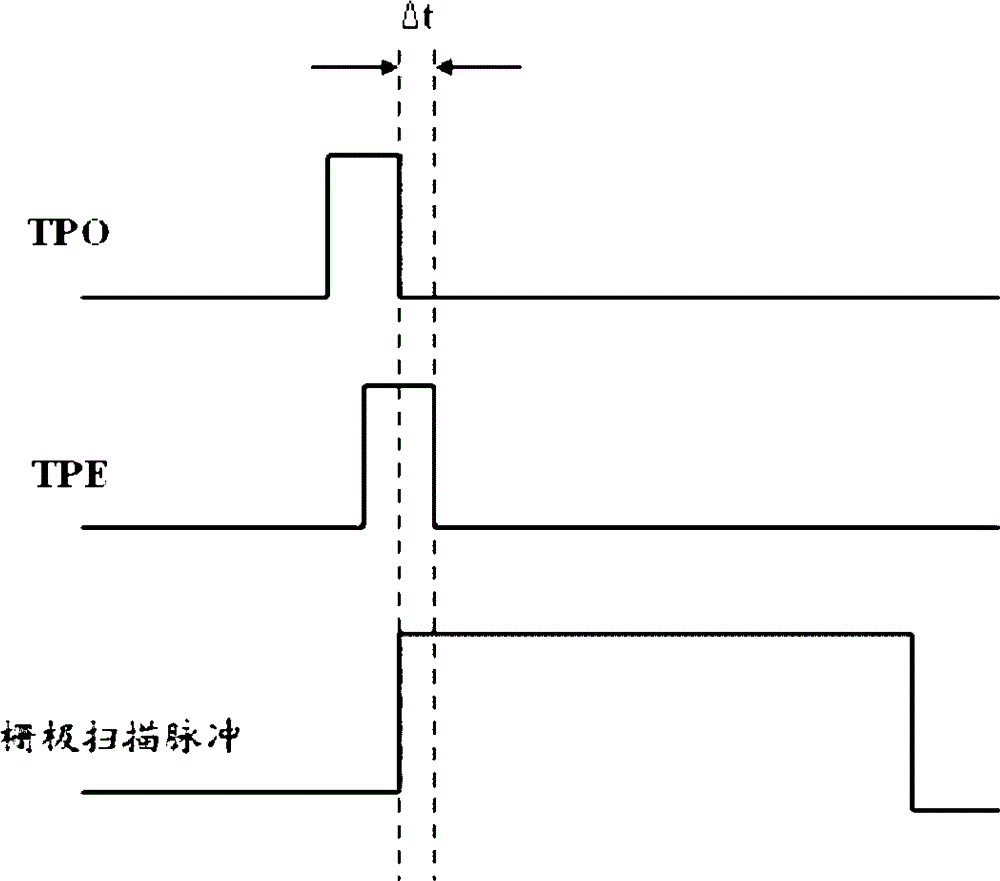
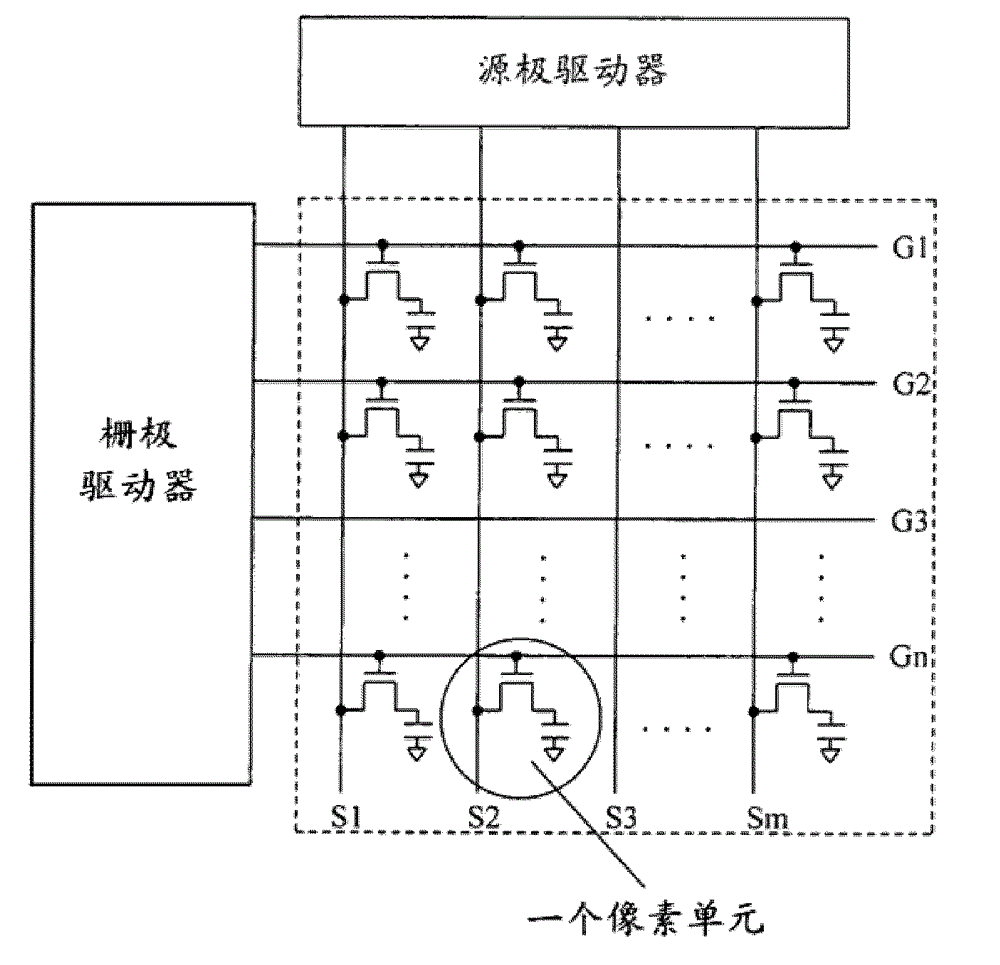
The invention provides a source driver applied to TFT-LCD. The source driver comprises a data register, a data latch, a digital to analog converter and an output buffer, wherein a first load pulse is supplied to the output buffer, so that the output buffer responds to a second edge, from a second level to a first level and closely following a first edge, of the first load pulse, and begins to output the greyscale voltages of odd numbered output ends to a corresponding TFT source; a second load pulse is supplied to the output buffer, so that the output buffer responds to a second edge, from a second level to a first level and closely following a first edge, of the second load pulse, and begins to output the greyscale voltages of even numbered output ends to a corresponding TFT source; at least the second edge of the first load pulse and the second edge of the second load pulse are asynchronous. The invention further provides a corresponding drive circuit and a drive method. The source driver, the drive circuit and the drive method can alleviate the adverse consequences arisen by excessive differences of two adjacent lines of data displayed.
Owner:HEFEI XINSHENG OPTOELECTRONICS TECH CO LTD +1
Method for breaking high-voltage (HV) superconducting current-limiting direct current (DC) circuit breaker
InactiveCN103633631AReduce weightReduce volumeEmergency protective circuit arrangementsSuperconductor elements usageElectronic switchCurrent decay
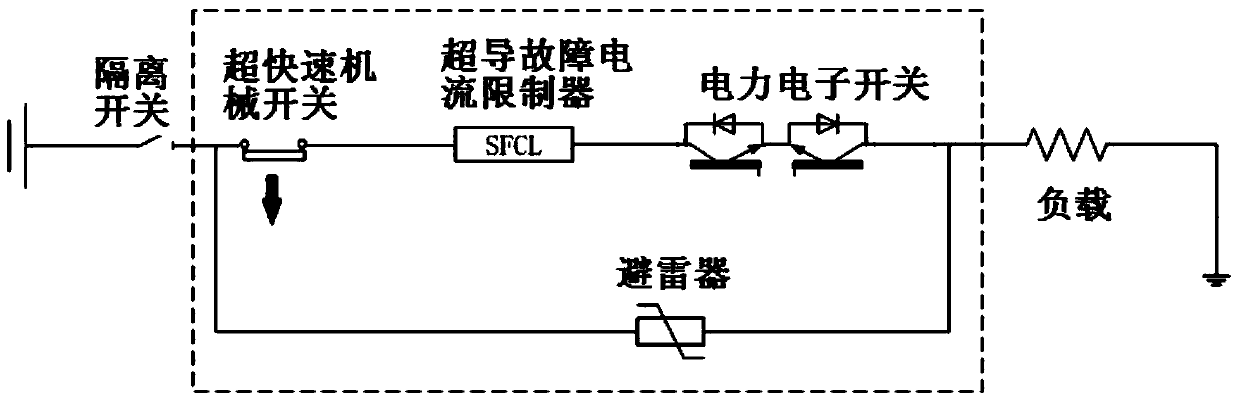
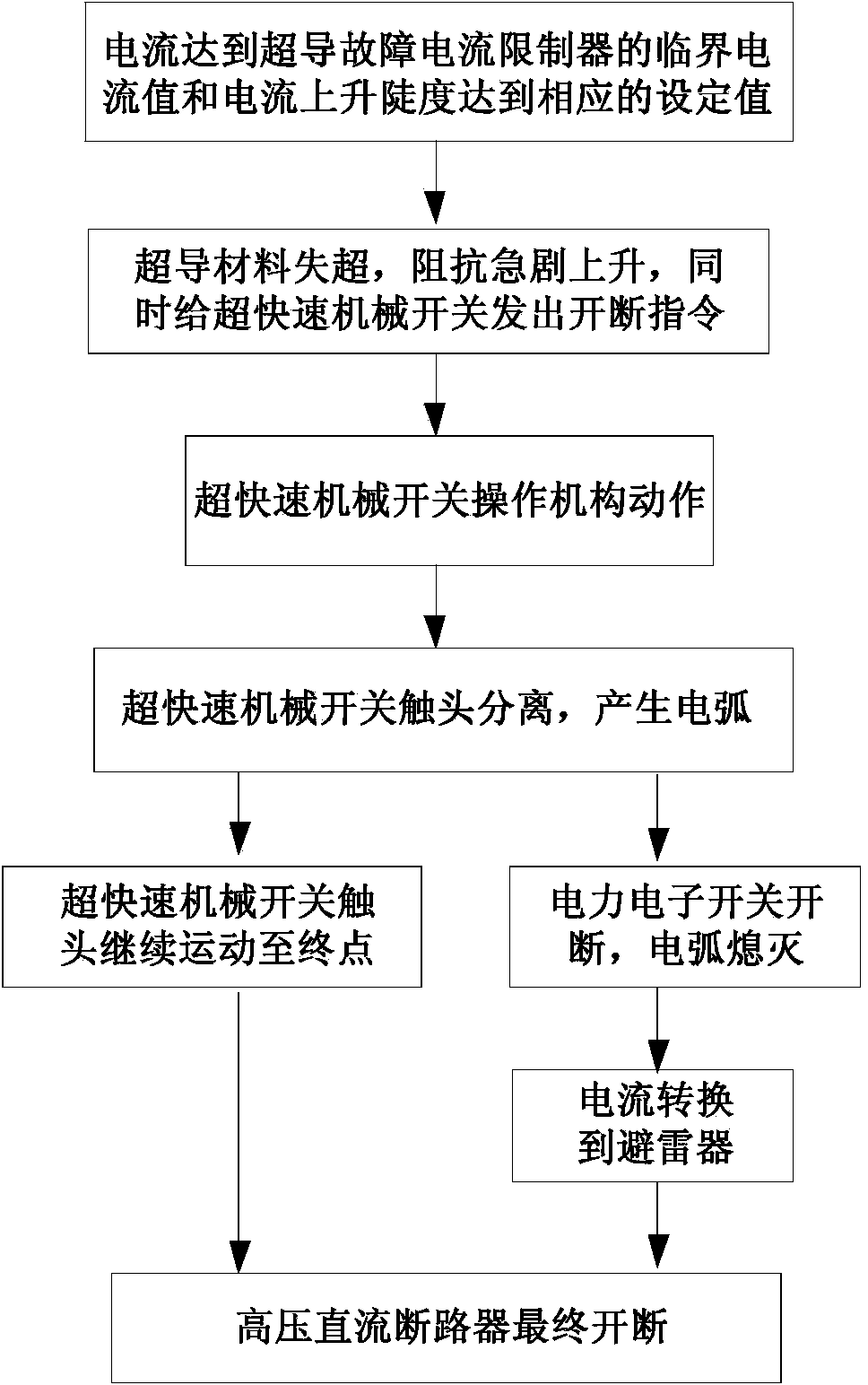
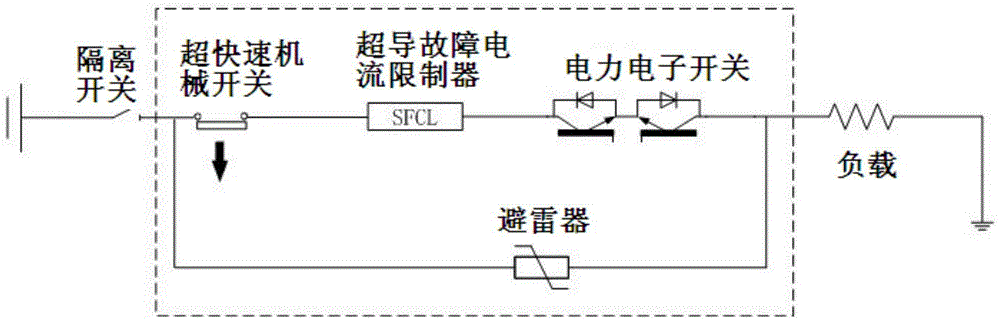
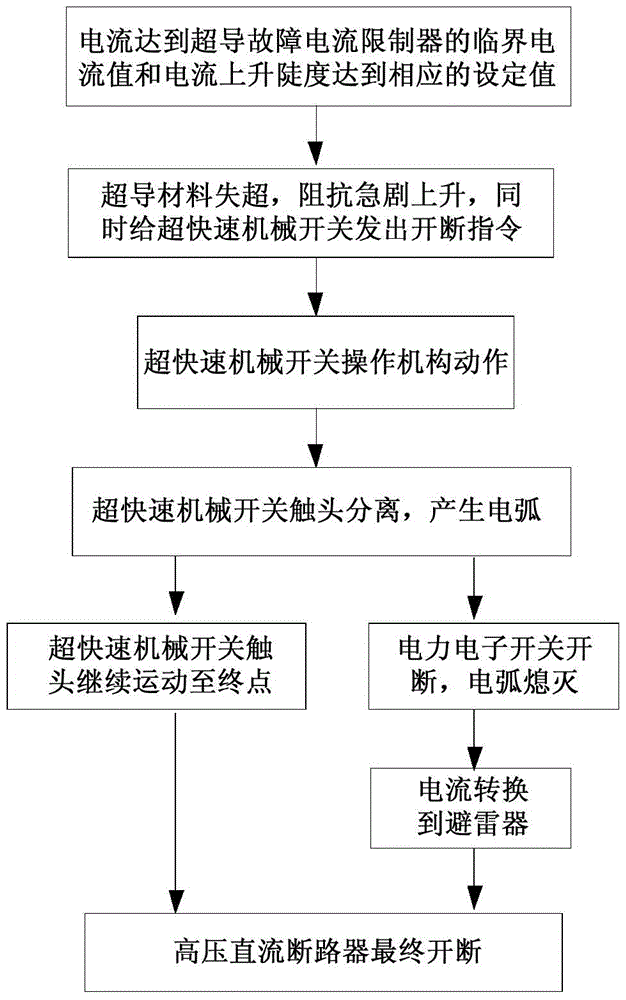
The invention provides a method for breaking a high-voltage (HV) superconducting current-limiting direct current (DC) circuit breaker. The method comprises the following steps: when a HVDC side is in short-circuit fault and current / current rising steepness rises rapidly and reaches a critical value of a current limiter, a superconducting material quenches immediately, impedance rises steeply, short-circuit current is limited within set values, and meanwhile, an instruction is sent to an ultra-quick mechanical switch; the ultra-quick mechanical switch acts immediately, enables contacts to separate at an ultrahigh rigid separating speed so as to form a physical gap and generate electric arcs, and immediately sends a breaking instruction to a power electronic switch; the power electronic switch quickly breaks the short-circuit current and enables the electric arcs between the contacts to be extinguished, so as to form an isolated fracture; when the contacts are separated to final open positions and current in a lightning arrester is attenuated to zero, the HV superconducting current-limiting DC circuit breaker completes a whole breaking process, and a HVDC transmission power grid is isolated from a faulty line. The method has the advantages that the cost performances of different components are taken into account comprehensively, so that the cooperation is optimized; the number of components and devices is reduced as much as possible, so that the size is reduced, the weight is reduced, and the reliability is improved.
Owner:STATE GRID CORP OF CHINA +1
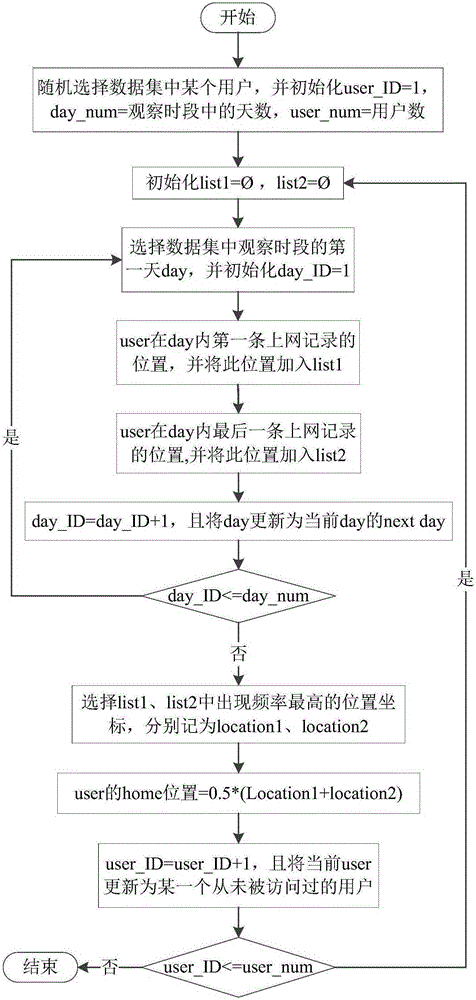
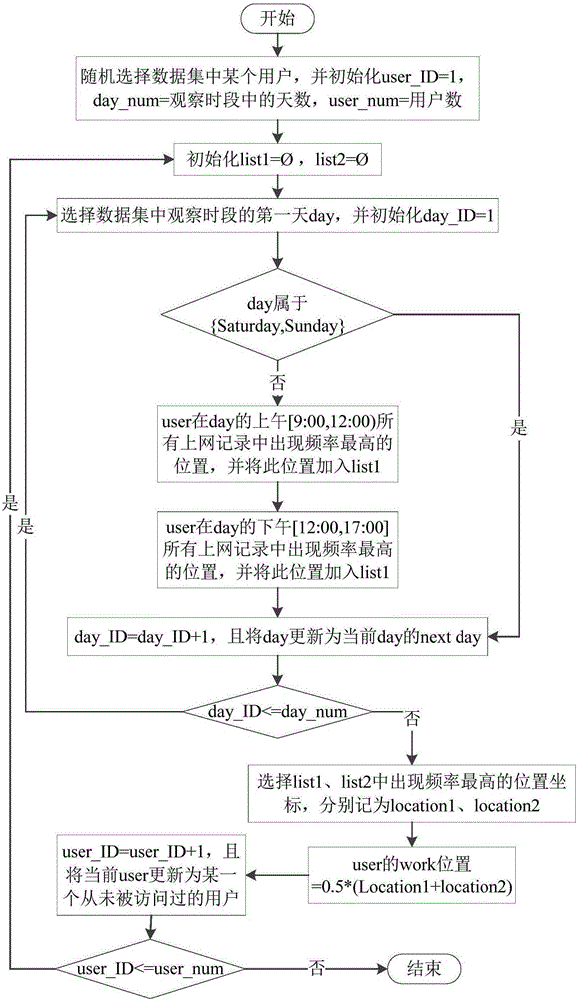
Method and system for obtaining user demand based on context environment of household workplace
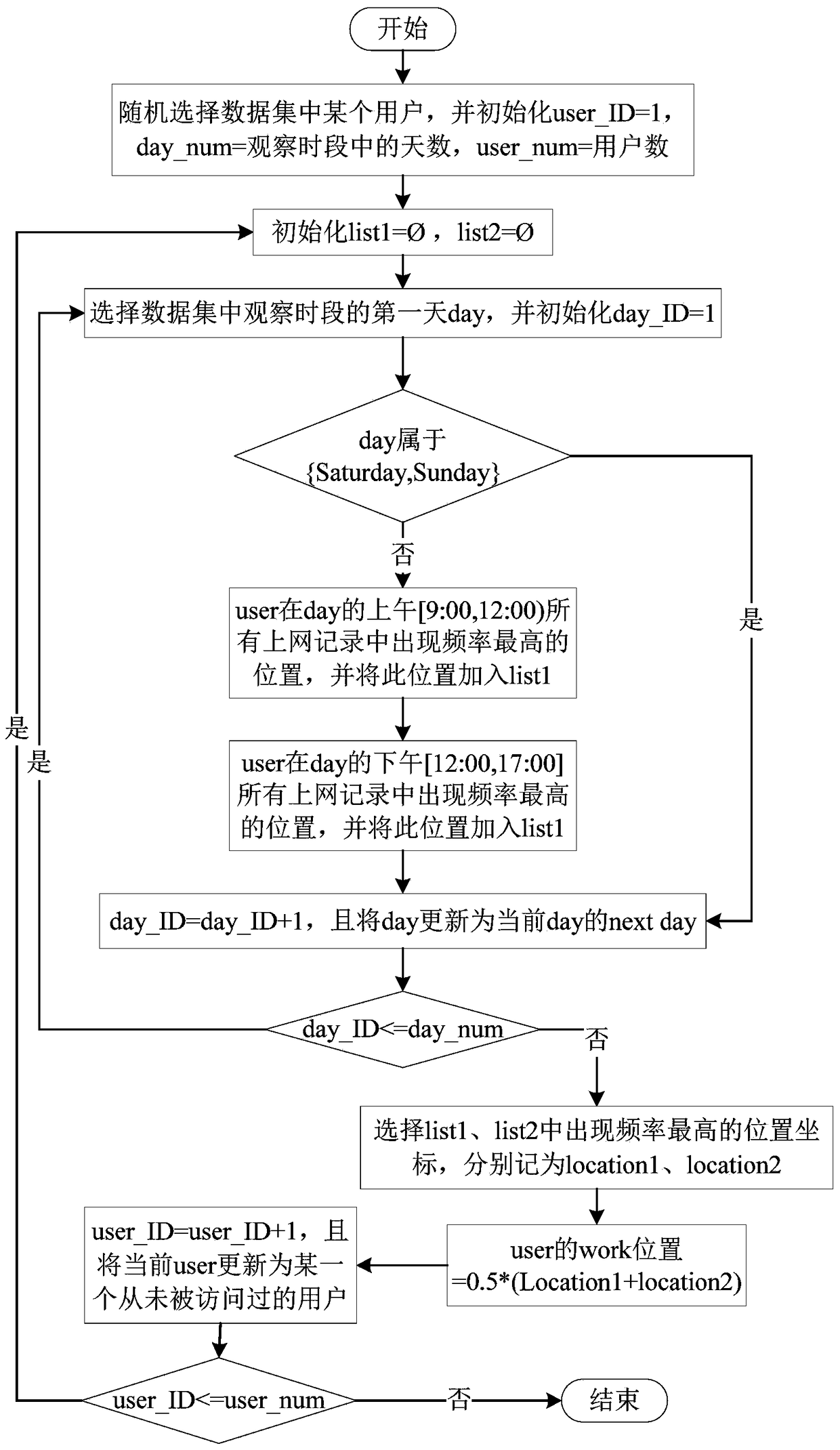
ActiveCN105224681AImprove experienceAdvancing the business modelSpecial data processing applicationsWeb data retrieval using information identifiersFamily basedData cleansing
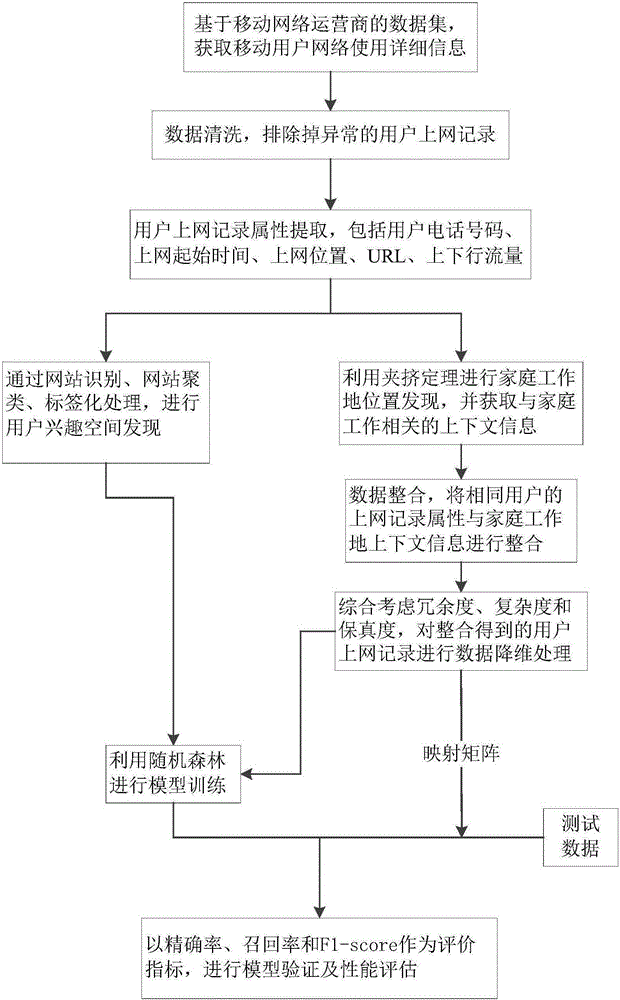
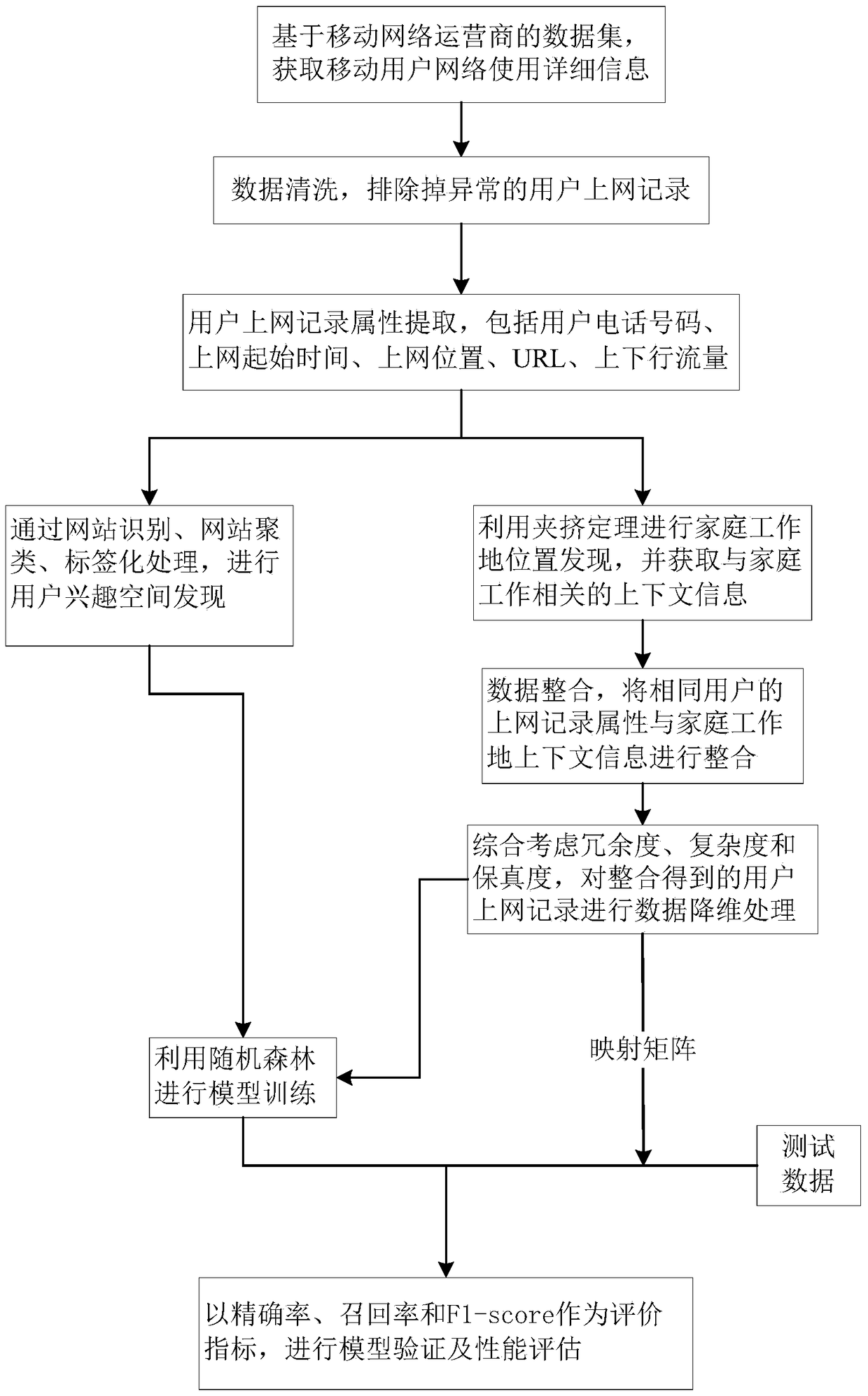
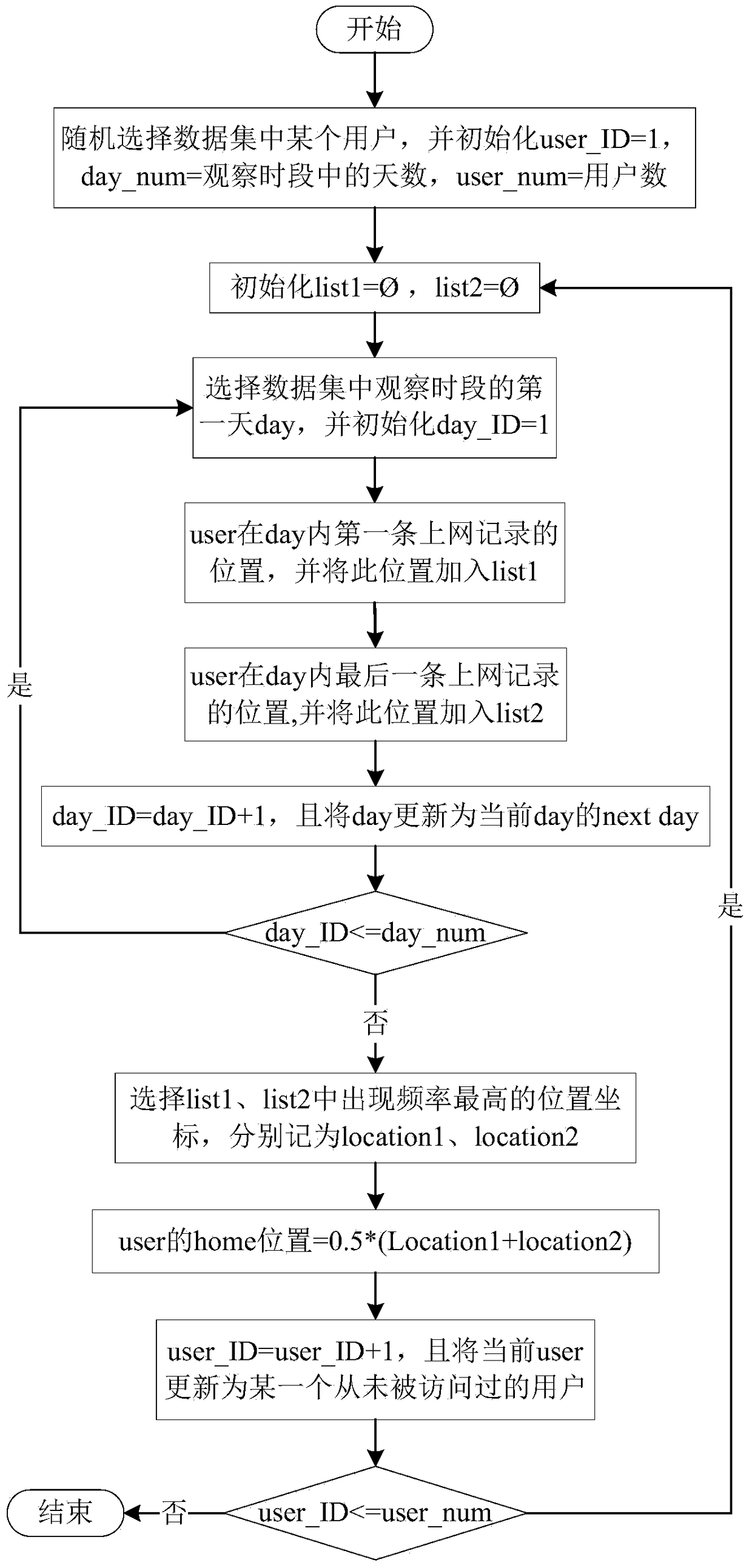
The invention provides a method and a system for obtaining a user demand based on a context environment of a household workplace. The method comprises the steps of obtaining mobile user network usage information based on a dataset of a mobile network operator; performing data cleaning to remove abnormal user Internet-surfing records; extracting and remaining attributes related to user interests from the user Internet-surfing records; discovering user interest space; discovering the position of the household workplace by utilizing a squeezing principle; performing data integration and data dimension reduction; and performing model training by utilizing a random forest and classifying. According to the method and the system for obtaining the user demand based on the context environment of the household workplace, a new technical scheme is provided for mining user demands and interests conveniently and efficiently by utilizing the dataset which is composed of the user network usage detailed information and comes from a mobile network operator and based on the position discovery of the household workplace and the context environment thereof.
Owner:WUHAN UNIV
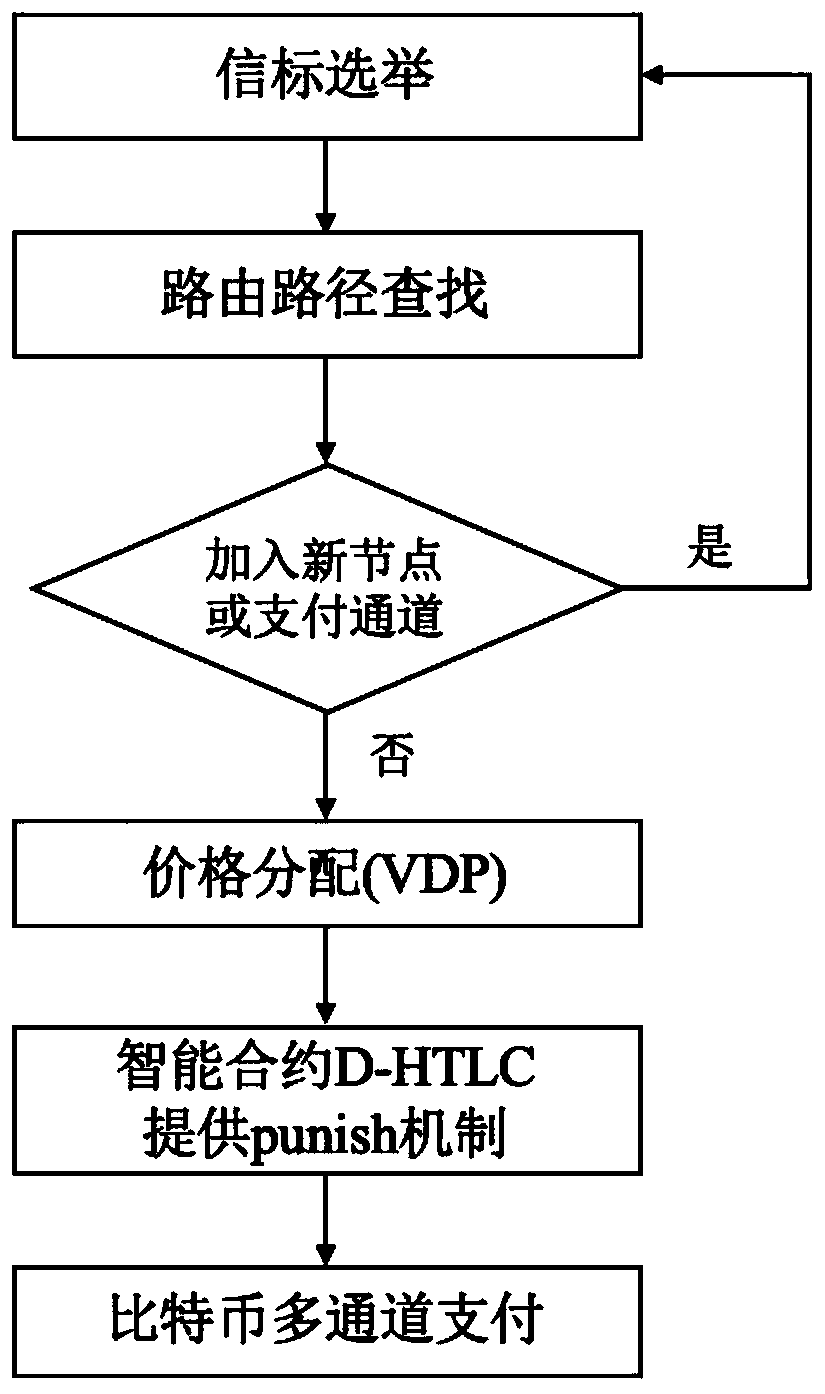
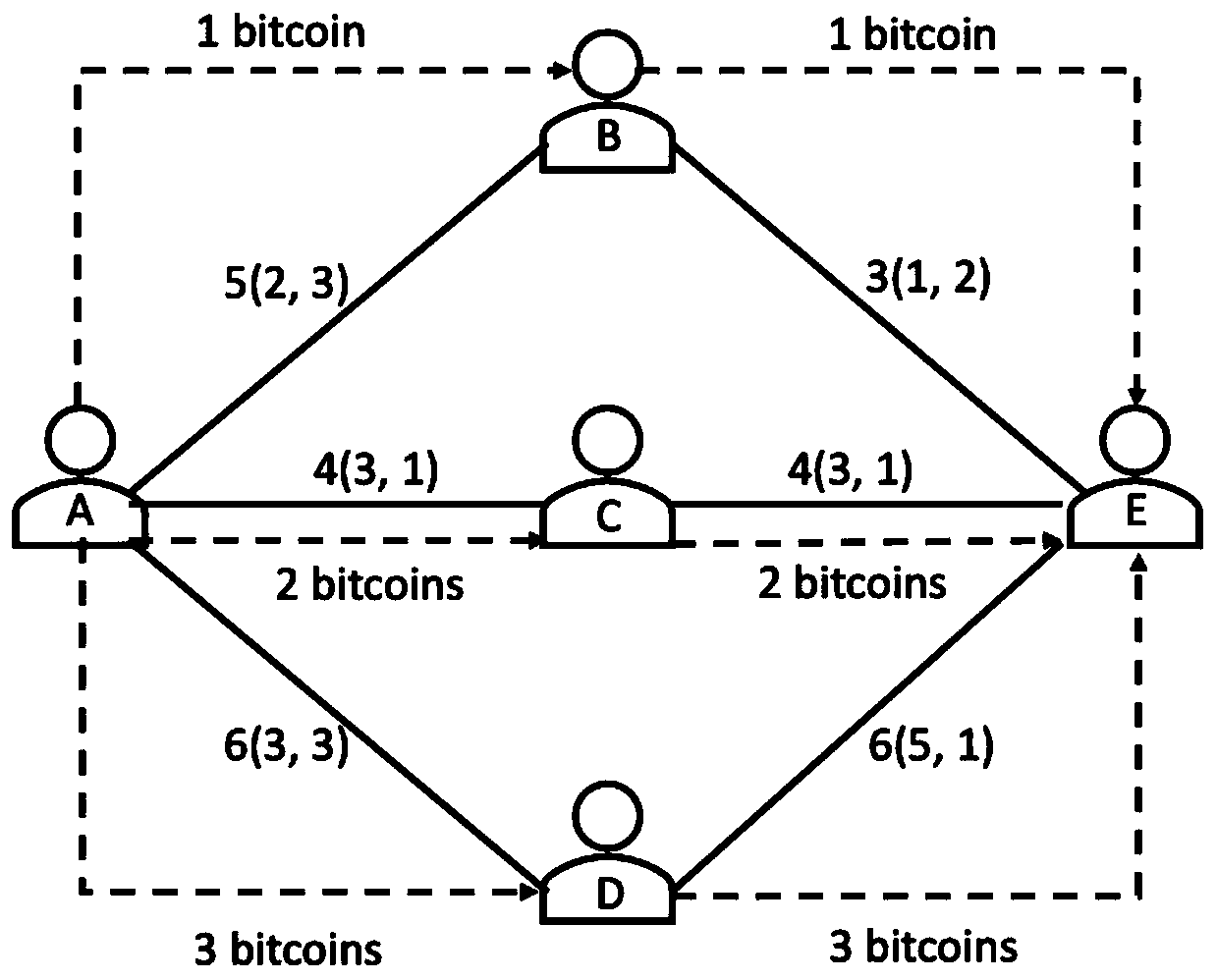
Encrypted currency multi-channel payment method based on smart contract
InactiveCN110751469AImprove efficiencyImprove securityDigital data protectionPayment protocolsPaymentAllocation algorithm
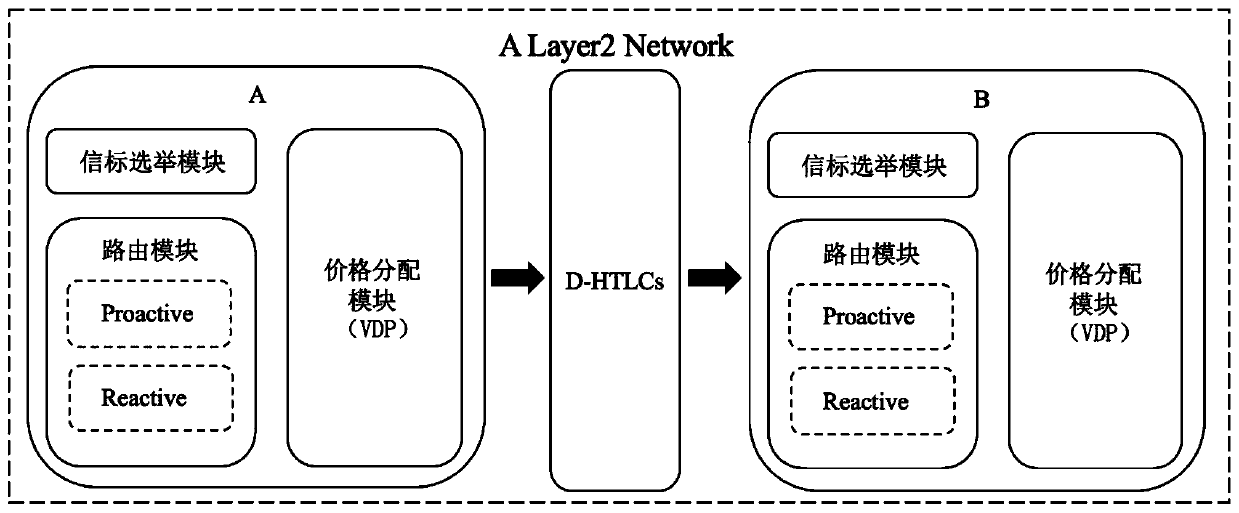
The invention provides an encrypted currency multi-channel payment method based on a smart contract. Encrypted currency multi-channel payment is realized through a beacon election algorithm, a routingpath search algorithm, a price allocation algorithm and an intelligent contract D-HTLC. The method specifically comprises the steps of constructing a beacon election module, constructing a routing path search module, constructing a price allocation module and constructing an intelligent contract D-HTLC module. According to the method, a multi-channel payment mechanism of the cryptocurrency is realized, the overload problem and the privacy problem of single-channel payment are solved, the efficiency and the safety of cryptocurrency payment are ensured, and the method not only has good universality and practical value, but also is suitable for all payment in a block chain Layer 2 network.
Owner:ZHEJIANG GONGSHANG UNIVERSITY
Method and system for controlling instant congestion of server
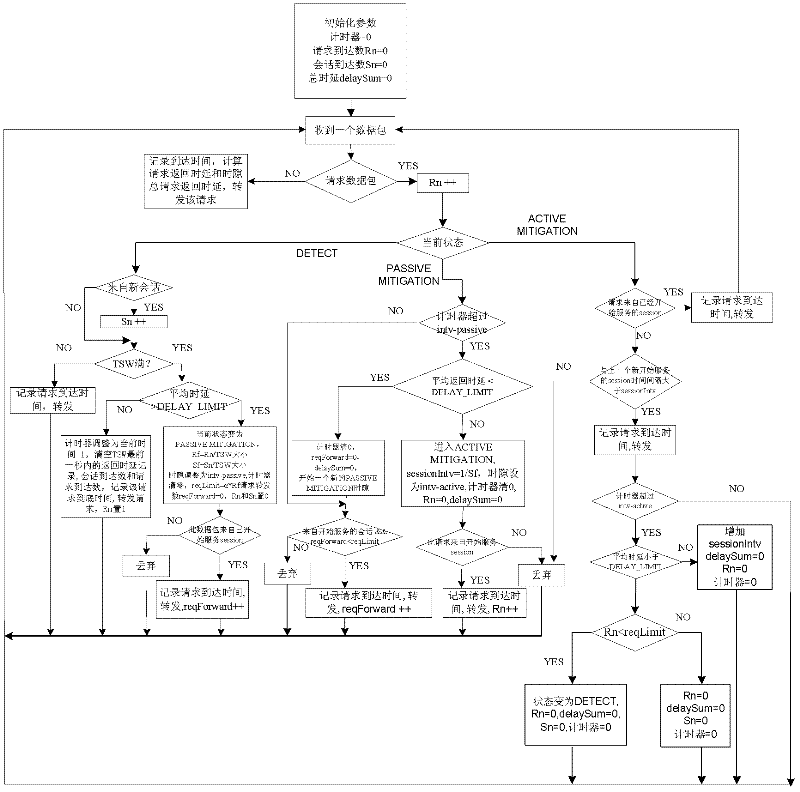
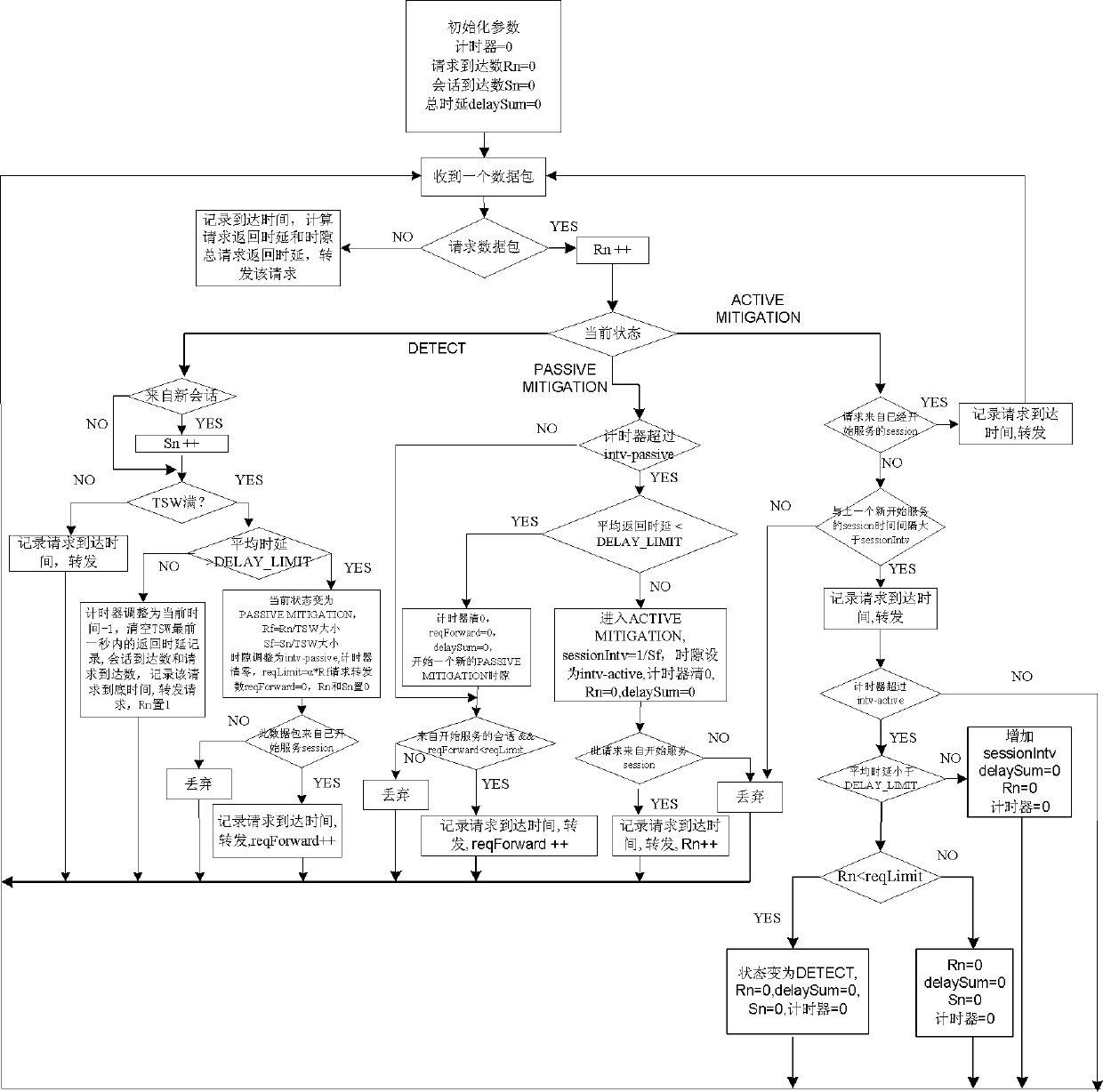
InactiveCN102333040ARelieve overloadIncrease profitData switching networksDistributed computingServer load
The invention provides a method and a system for controlling the instant congestion of a server. In the method, controlling state comprises a first state, a second state and a third state, in each state, a data packet is processed by different methods under different conditions. The method comprises the following steps of: 1) receiving a data packet, then discarding or forwarding the data packet according to the controlling state; and 2) comparing the average request return time delay of the data packet with a detection threshold value, then changing controlling state or keeping an original state according to a comparison result, when the average request return time delay is greater than the detection threshold value, switching from the first state to the second state, or switching from the second state to the third state, and when congestion condition is improved, switching from the third state to the first state. By the method and the system, session integrity can be protected, the retransmission of massive data packets caused by the oscillation of server load can be avoided, and learning or training is not required and computation cost is low.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Power distribution network reconstruction calculating method based on OBDD (ordered binary decision diagram)
ActiveCN108616124ACalculation speedReduce memory usageAc network circuit arrangementsBoolean functionBinary decision diagram
The invention provides a power distribution network reconstruction calculating method based on an OBDD (ordered binary decision diagram), and the method comprises the steps: S1, constructing an objective function according to a target task; S2, initializing an OBDD model of a power distribution network by combining the associated data of the target task; S3, establishing a Boolean function of thepower distribution network reconstruction constraint, generating an OBDD and solving the OBDD; S4, correcting a model and constraint conditions, and carrying out the dynamic reconstruction of the distribution network. The method employs the OBDD as the core algorithm, and a networking reconstruction scheme of the power distribution network containing a distributed power supply in a fault state iscalculated, and a regulative reconstruction scheme for the structural defects of the power distribution network in a normal state is calculated, thereby achieving the purposes that the power failure risk of the power distribution network is the lowest, the consumption degree of new energy is the highest, the network loss of the power distribution network is the lowest, the voltage fluctuation ratio is the smallest and the line loads are uniformly distributed.
Owner:STATE GRID SHANDONG ELECTRIC POWER +1
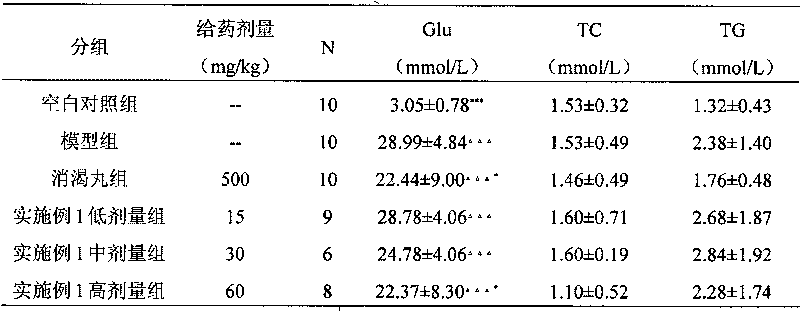
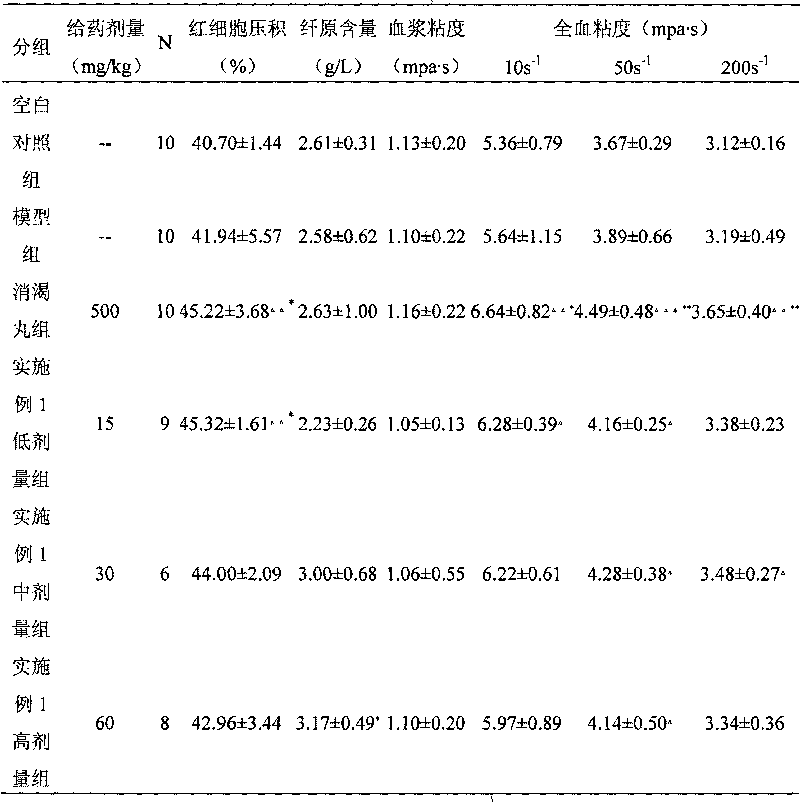
Application of pseudo-ginseng and extract thereof in preparing medicament for curing and/or preventing diabetic microangiopathies
ActiveCN101700265AImprove high viscosity stateImprove hypoxia toleranceMetabolism disorderUrinary disorderPANAX NOTOGINSENG ROOTPanax notoginseng extract
The invention relates to a new application of pseudo-ginseng, pseudo-ginseng extract, panax notoginseng saponins, and panax notoginseng saponins composite, namely, a new application in preparing medicament for curing and / or preventing diabetic microangiopathies.
Owner:许淑清
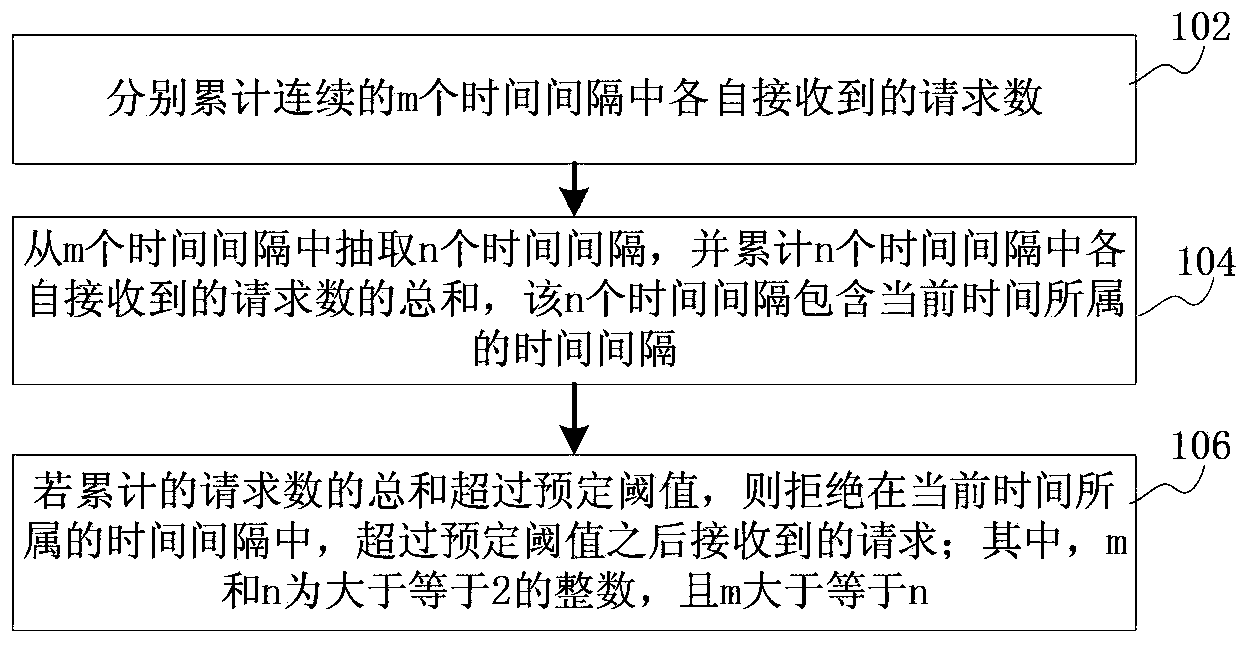
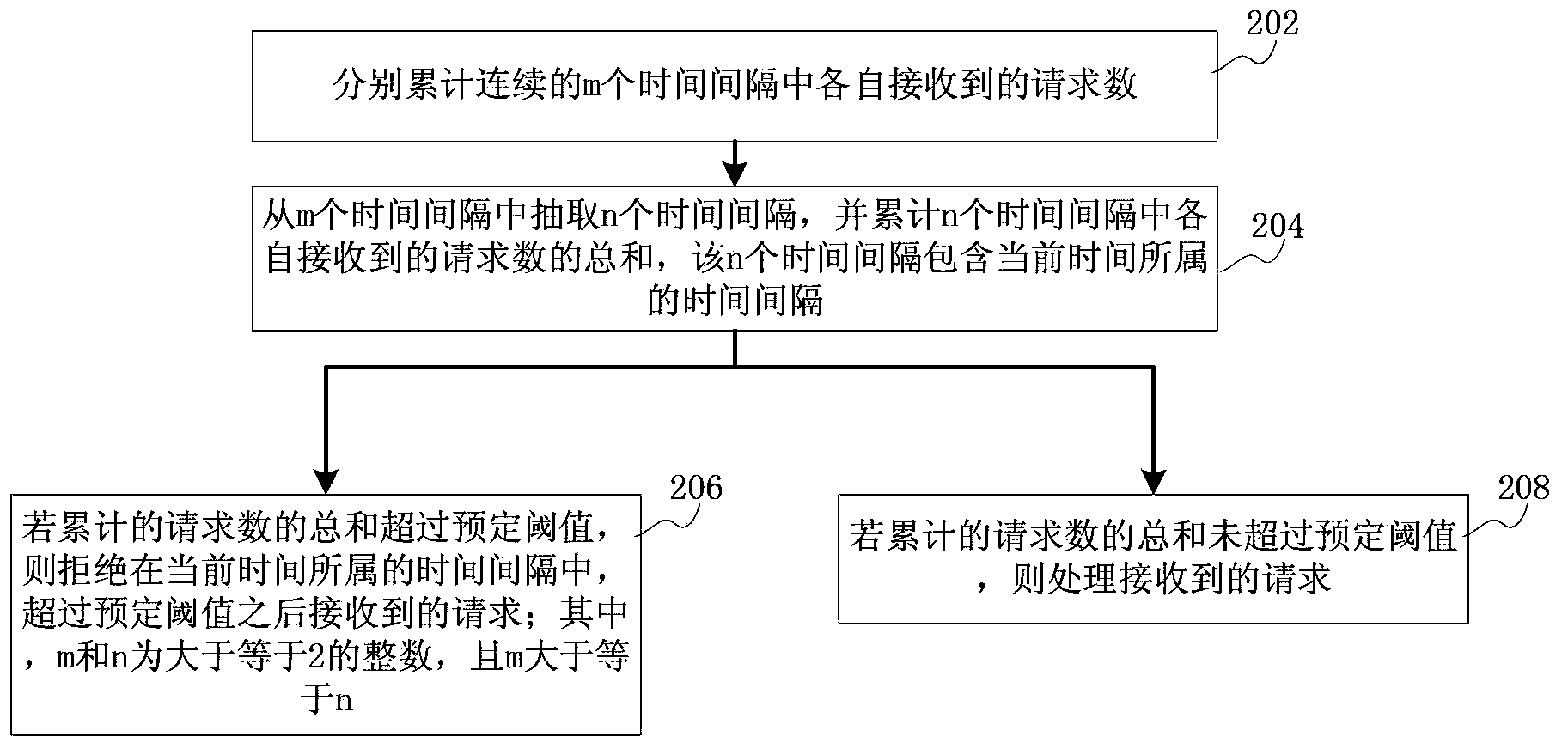
Overload protection method, device and server
ActiveCN103685336ARelieve overloadThe effect of mitigating overloadTransmissionInternet communicationCurrent time
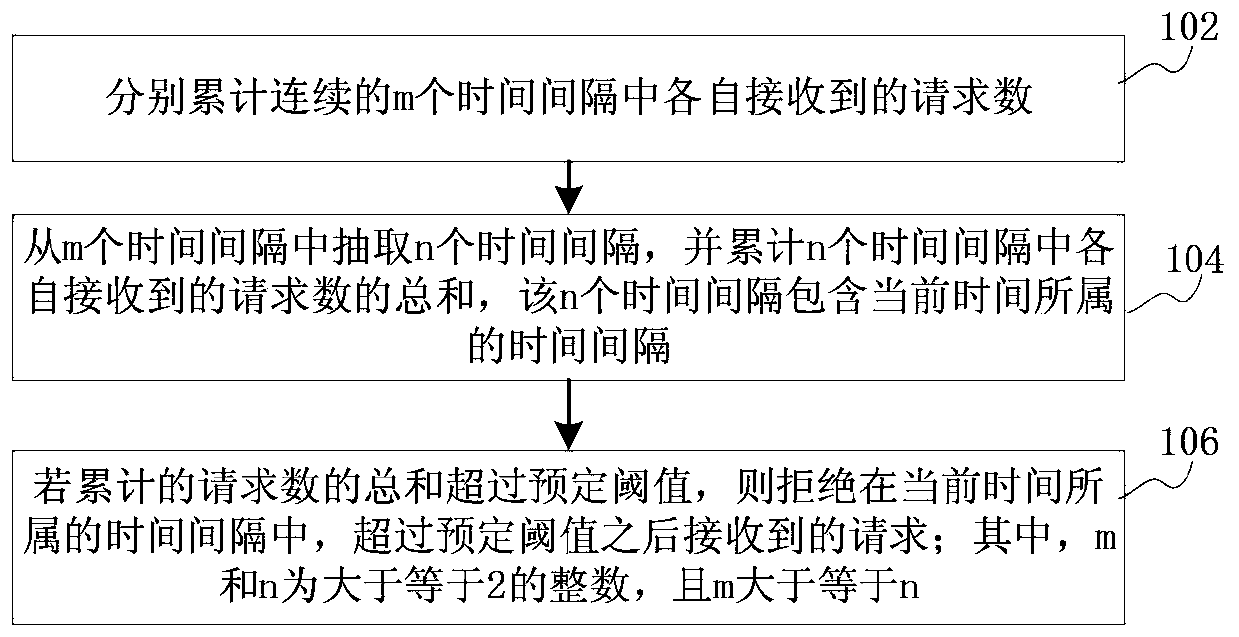
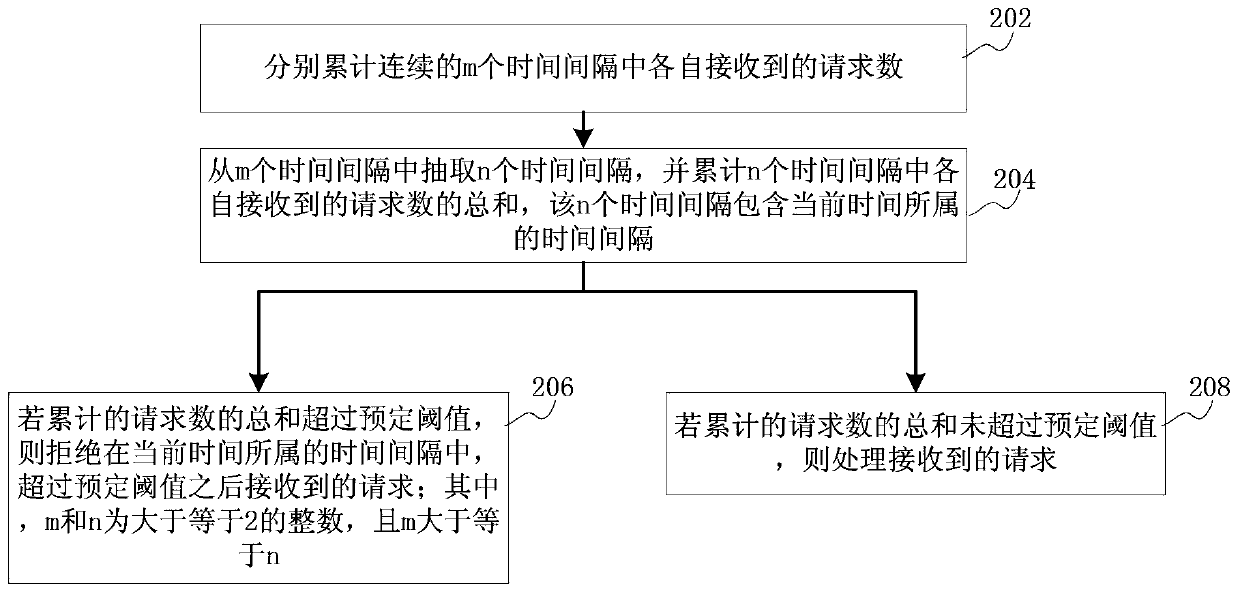
The invention discloses an overload protection method, device and server and belongs to the field of Internet communication. The method comprises the following steps: respectively adding up requests which are received in each time interval of continuous m time intervals; extracting n time intervals from the m time intervals, and obtaining the sum of requests which are received by each time interval in the n time intervals, wherein the n time intervals comprise the time interval to which the current time belongs; if the accumulative sum of the requests exceeds a preset threshold, refusing the requests which are received after the preset threshold is exceeded in the time interval to which the current time belongs, wherein both m and n are integers bigger than or equal to 2, and m is bigger than or equal to n. The problem that server overloading in rush hours cannot be effectively mitigated by the existing overload protection method is solved. The purpose of realizing overload protection through the comprehensive accumulation of accumulative number in multiple time intervals is achieved, so that the server overloading in the rush hours is effectively mitigated.
Owner:TENCENT TECH (SHENZHEN) CO LTD
Automatic summarization generating method and device
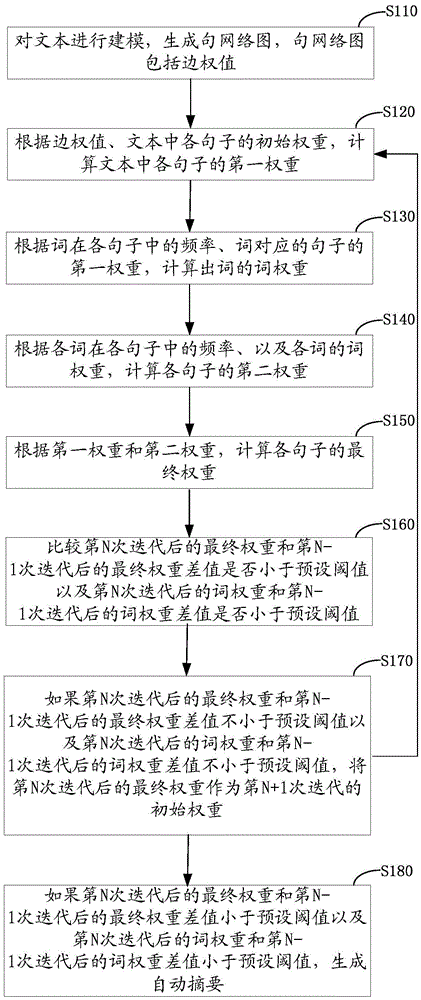
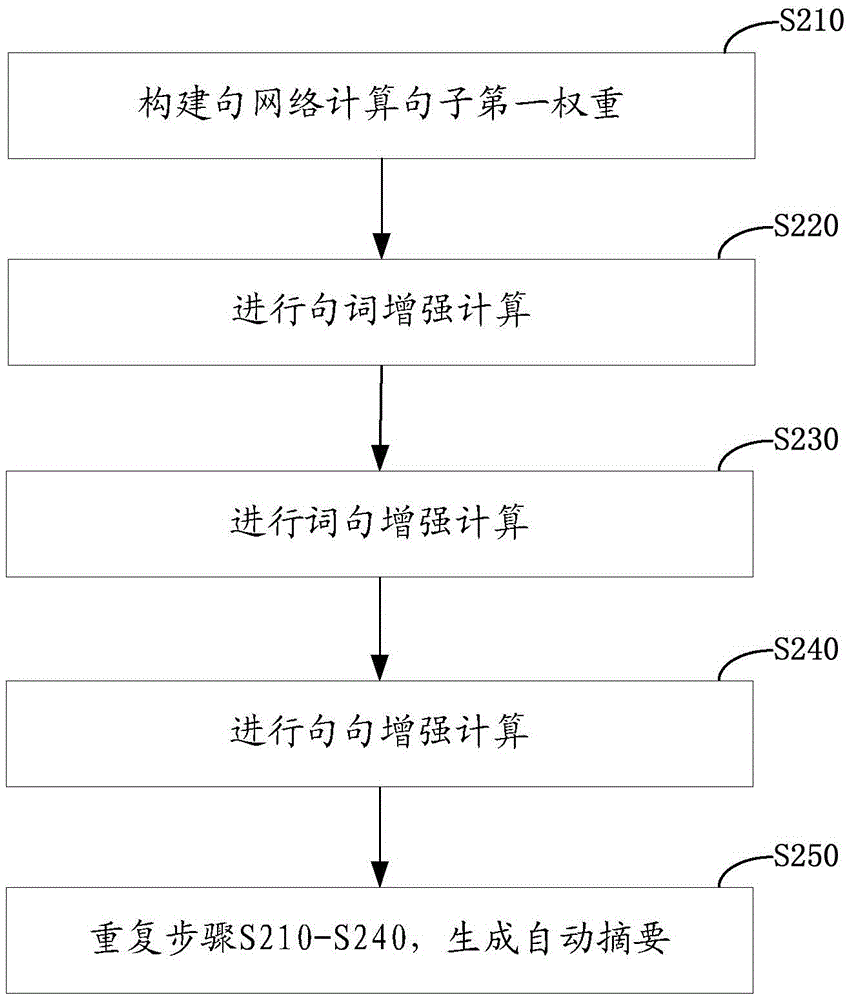
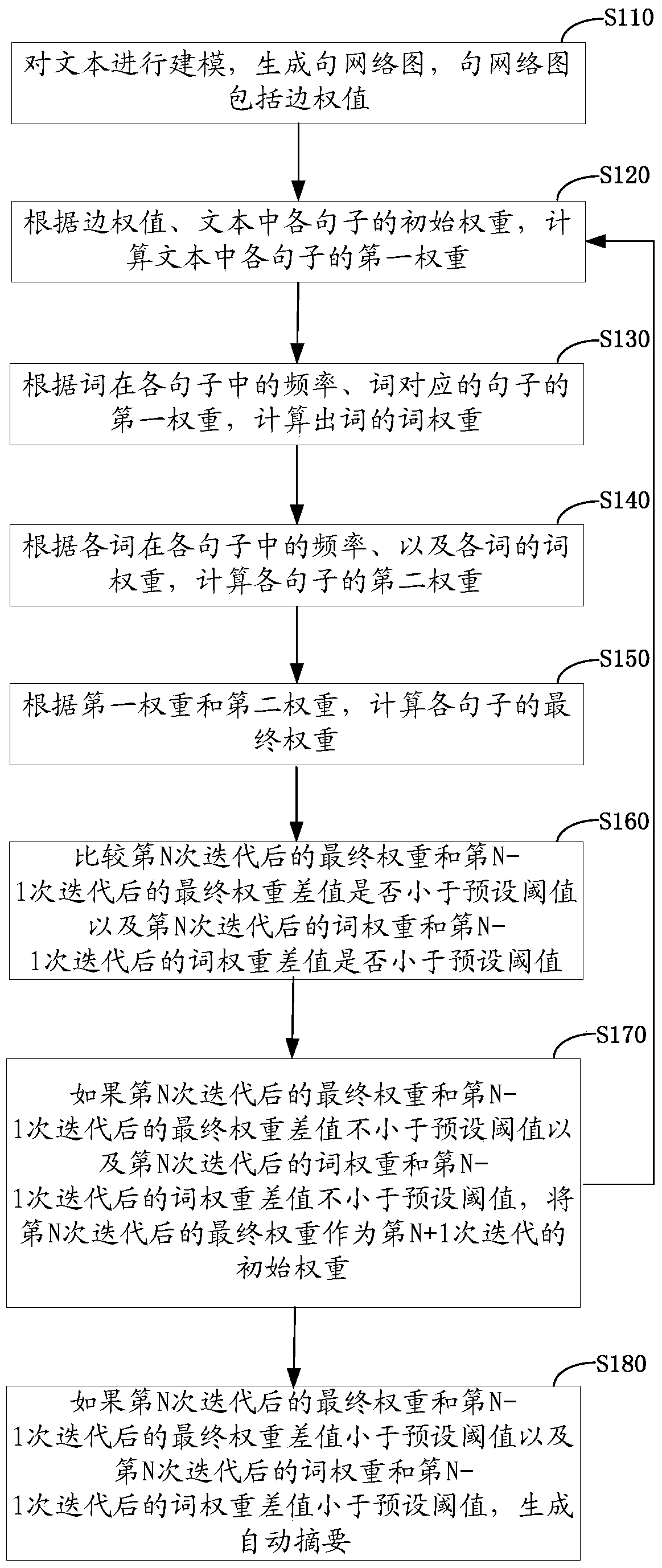
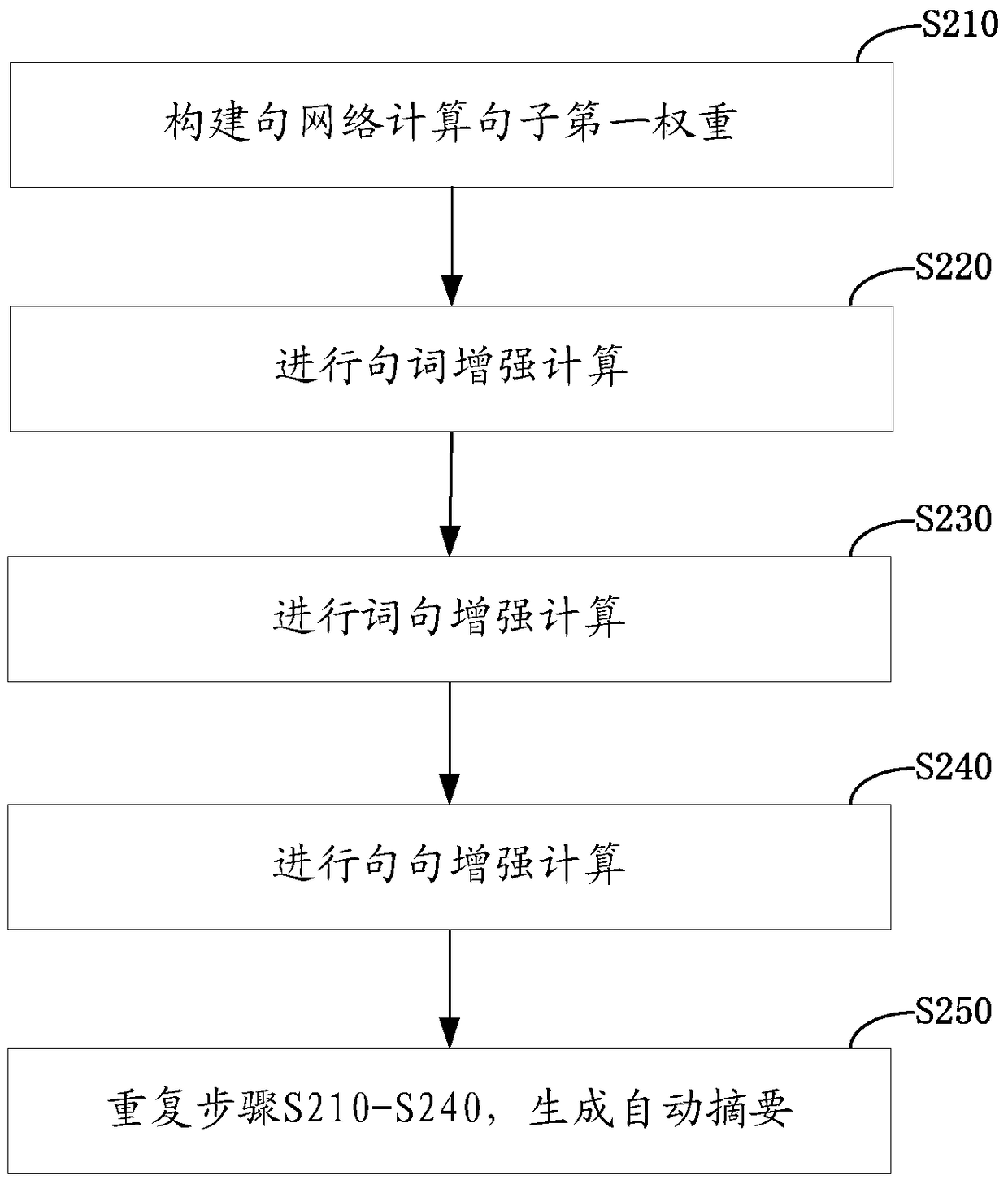
ActiveCN105653704AFix low-quality summariesRelieve overloadSpecial data processing applicationsAlgorithmTheoretical computer science
The invention relates to an automatic summarization generating method and device. The method comprises the steps of modeling a text to generate a sentential network diagram which comprises edge weights; computing first weights of sentences in the text according to the edge weights and initial weights of the sentences in the text; computing term weights according to frequencies of terms in the sentences and the first weights of the sentences corresponding to the terms; computing second weights of the sentences according to the frequencies of the terms in the sentences and the term weights of the terms; computing final weights of the sentences according to the first weights and the second weights; and if the difference between the final weight after nth iterations and the final weight after (n-1)th iterations is less than a preset threshold value and the difference between the term weight after nth iterations and the term weight after (n-1)th iterations is less than a preset threshold value, generating an automatic summarization. By means of the method, the problem that the quality of single long text summarizations is low is solved; the information overload is alleviated; and the summarization quality is improved.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
Decentralized Internet of Things heterogeneous identifier analysis method based on super account book
ActiveCN111431960AImprove analysis efficiencyAvoid single point of failure, centralization of power, etc.Securing communicationTheoretical computer scienceEngineering
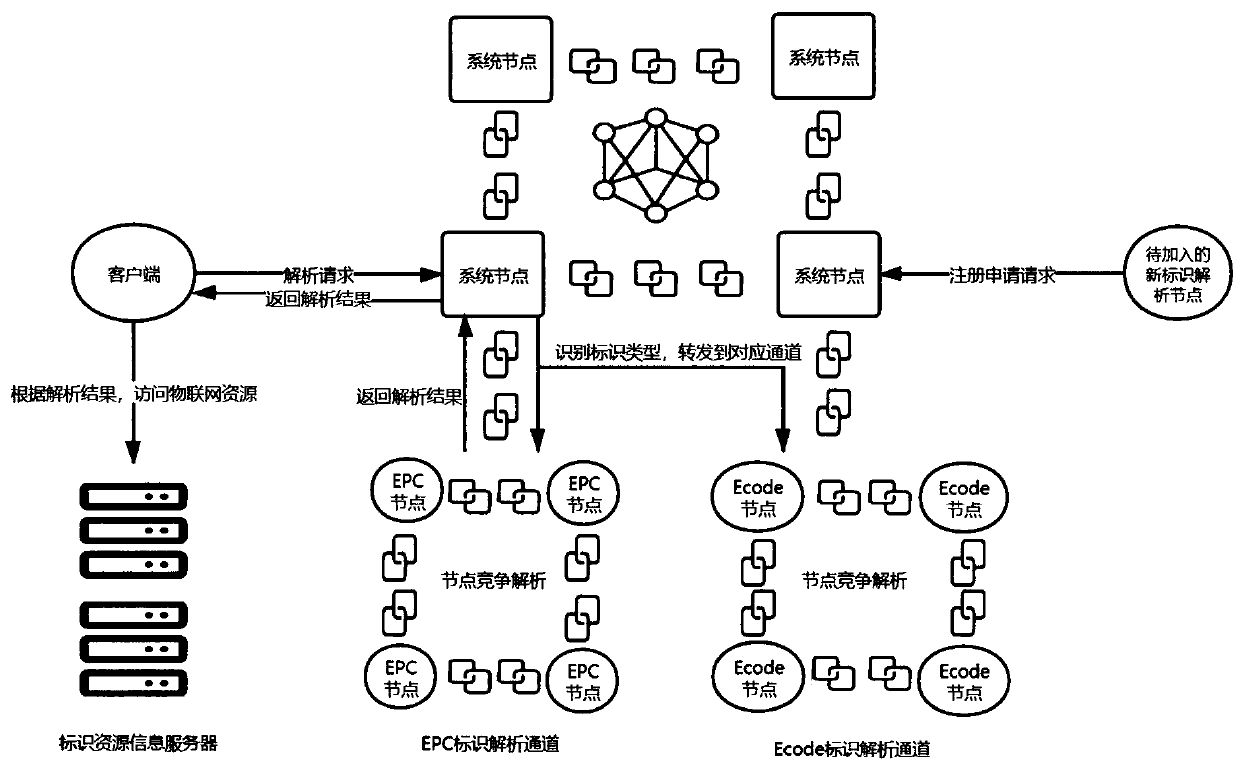
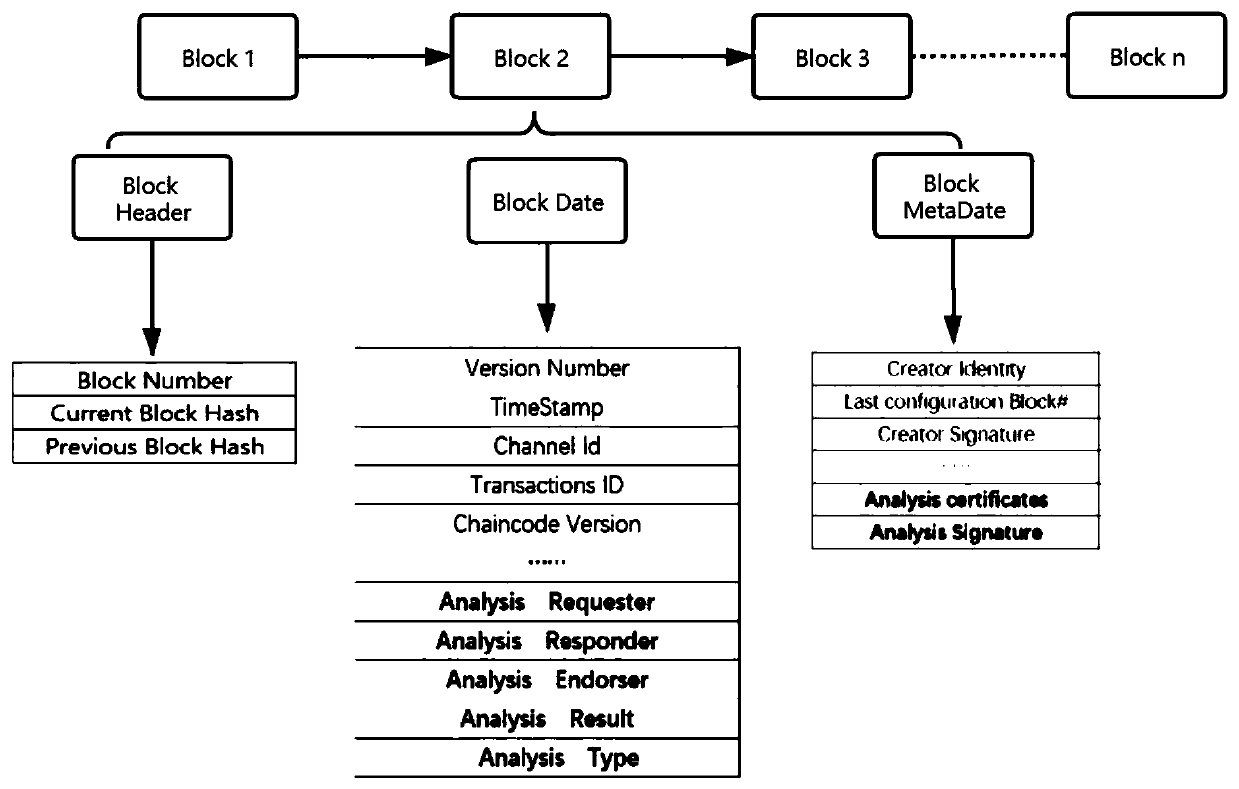
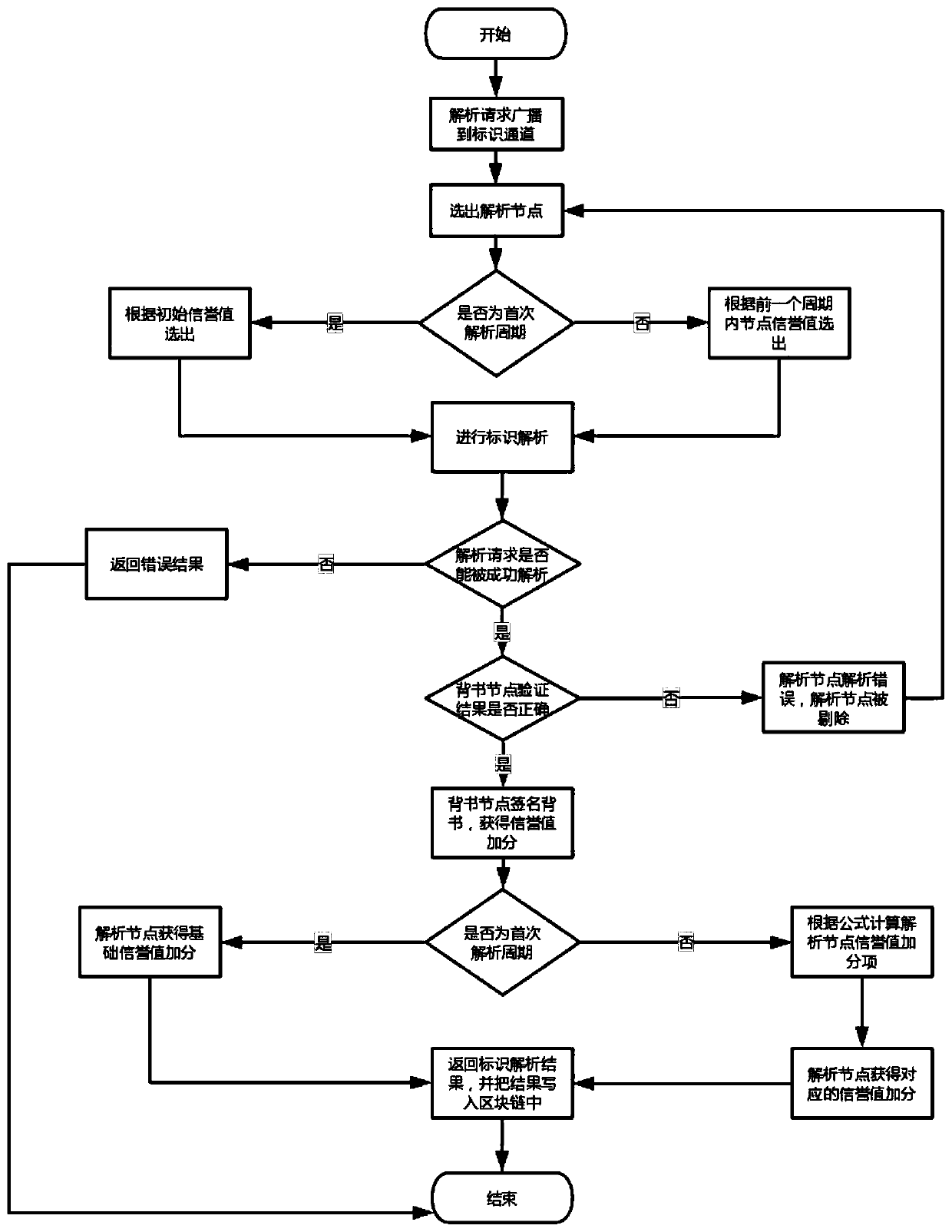
The invention relates to a decentralized Internet of Things heterogeneous identifier analysis method based on a super account book, and belongs to the technical field of Internet of Things. The methodcomprises the following steps: S1, constructing a decentralized Internet of Things identifier analysis architecture based on a block chain, and converting traditional single-root node analysis into multi-root node peer-to-peer analysis by utilizing the multichannel characteristic of a Hyperleder Fabric super account book; S2, introducing a Gini coefficient, constructing an analysis service competition model of the reputation value of the heterogeneous identifier analysis node, dynamically balancing the load of each analysis server, and improving the identifier analysis efficiency; and S3, designing a block structure suitable for identifier analysis, and realizing internet of things heterogeneous identifier peer-to-peer analysis through an intelligent contract. According to the method, decentration and stability of heterogeneous identifier analysis are guaranteed through node uplink analysis and multi-channel analysis, the problem of centralization of a single-root node analysis structure in a traditional identifier analysis system is solved, and the problem that the load of a single node is too heavy is avoided.
Owner:CHONGQING UNIV OF POSTS & TELECOMM
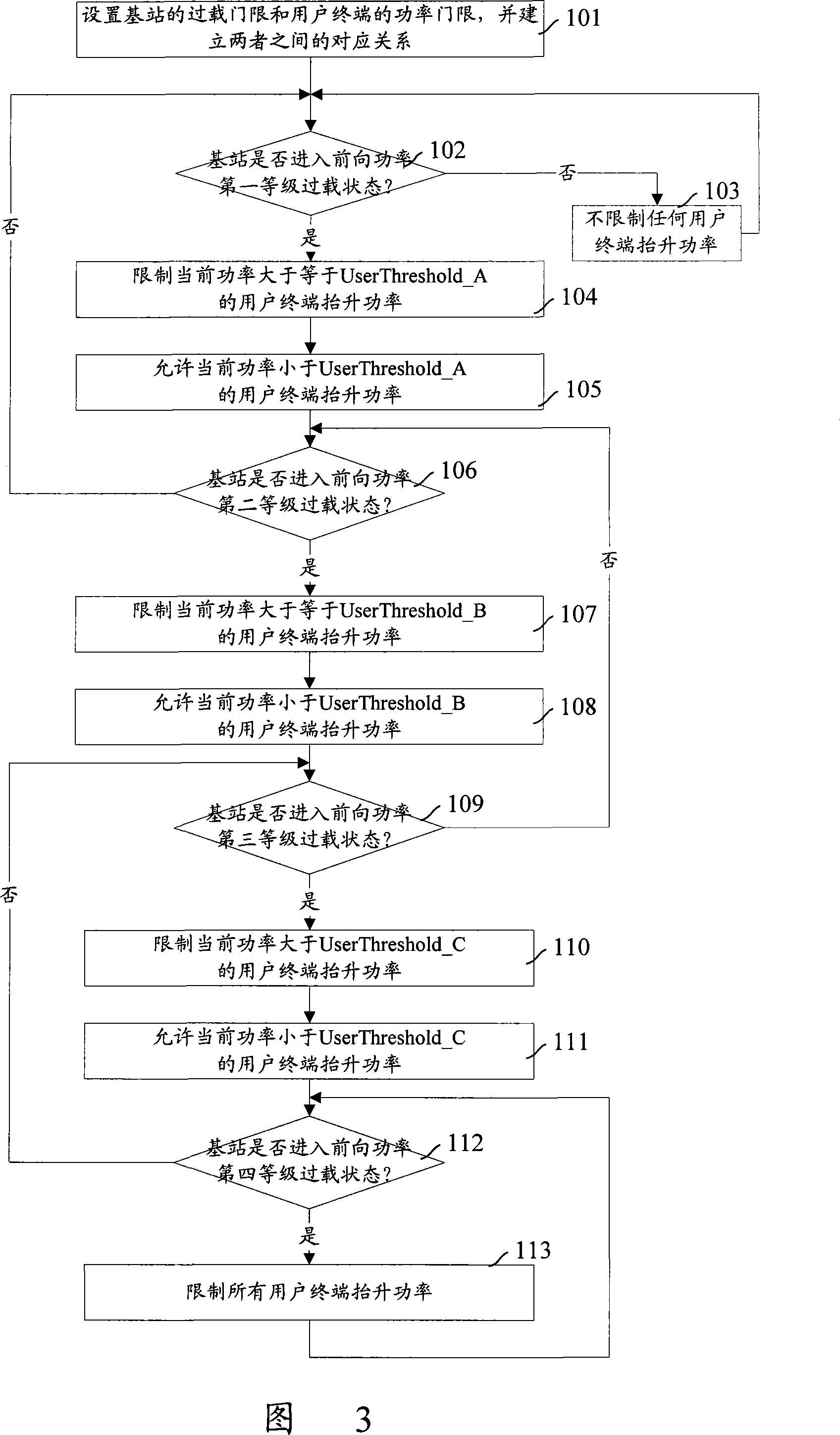
Forward power overloads control method
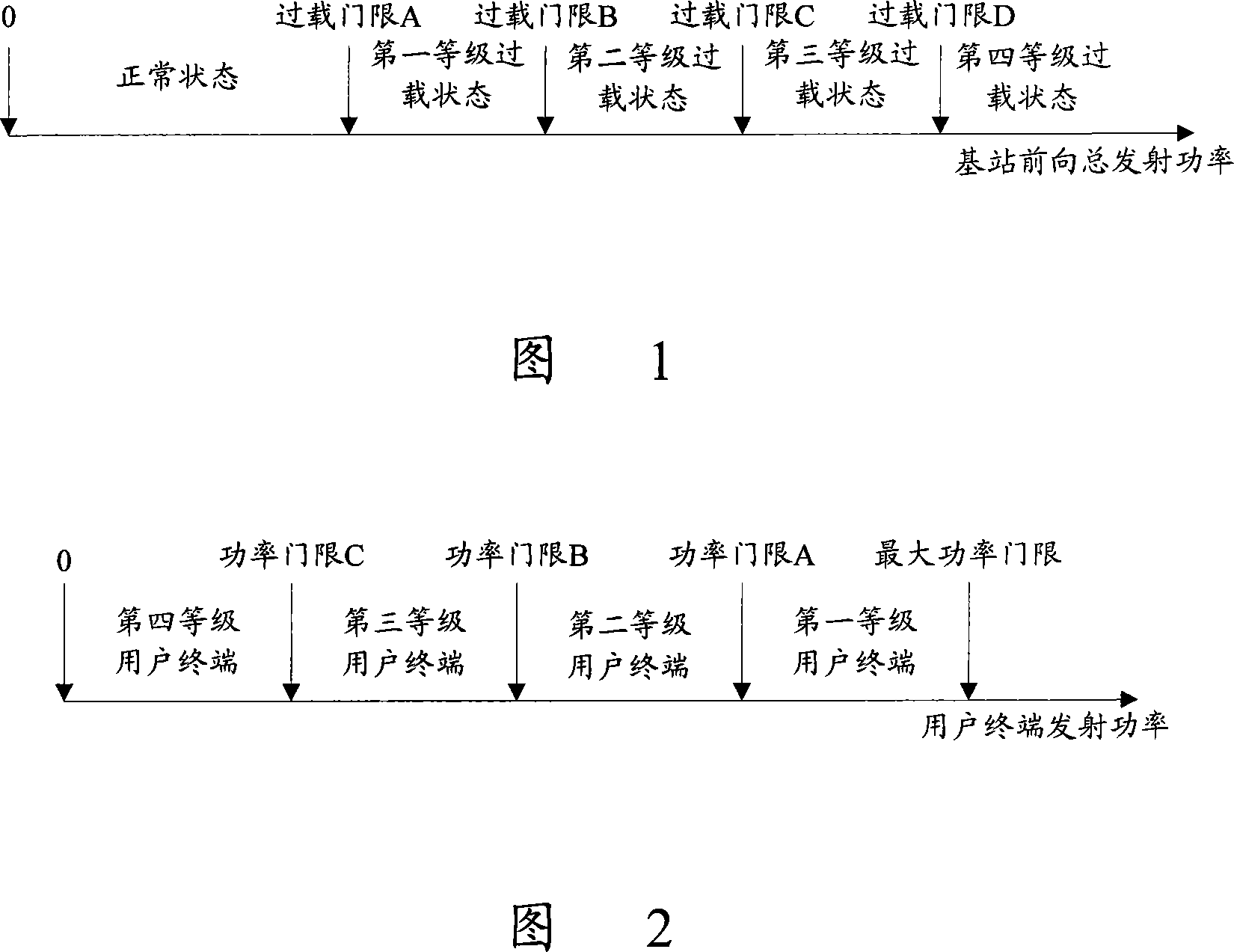
InactiveCN101174860ARelieve overloadReduce adverse effectsTransmission control/equalisingHigh level techniquesQuality of serviceOverload control
The present invention discloses a method for the forward power overload control; a plurality of power thresholds is arranged on the user terminal and a plurality of overload thresholds is arranged at the base station, and the correspondence between the power and overload thresholds is established; the method also comprises that the method judge that whether the forward gross emitting power of the base station increases to surpass a overload threshold; if the power surpasses, the forward emitting power of the user terminal is forbidden to be lifted if the forward-link emitting power is more than the power threshold which is corresponding to the overload threshold. With the present invention, when the forward emitting power of the base station is overloaded, the user terminal with comparatively large power is limited to lift power first; and then when the overload situation becomes more and more serious, the user terminal with comparatively small power is limited to lift power; in this way, the overload situation of the base station is effectively alleviated and the adverse effect of user terminal which is provided with good forward-link chain circuit and low forward-link emitting power is prevented; moreover, the service quality is effectively ensured.
Owner:ZTE CORP
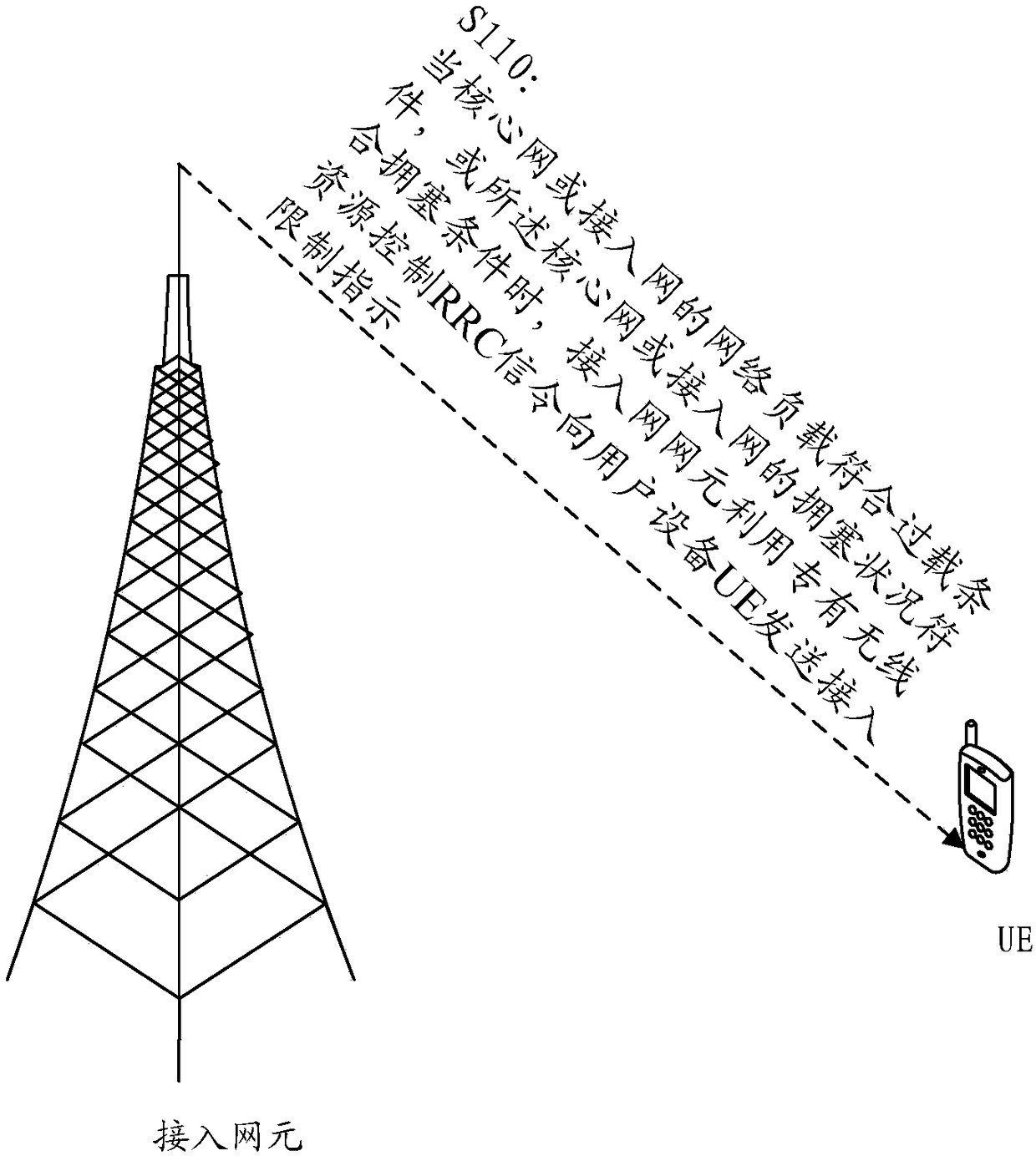
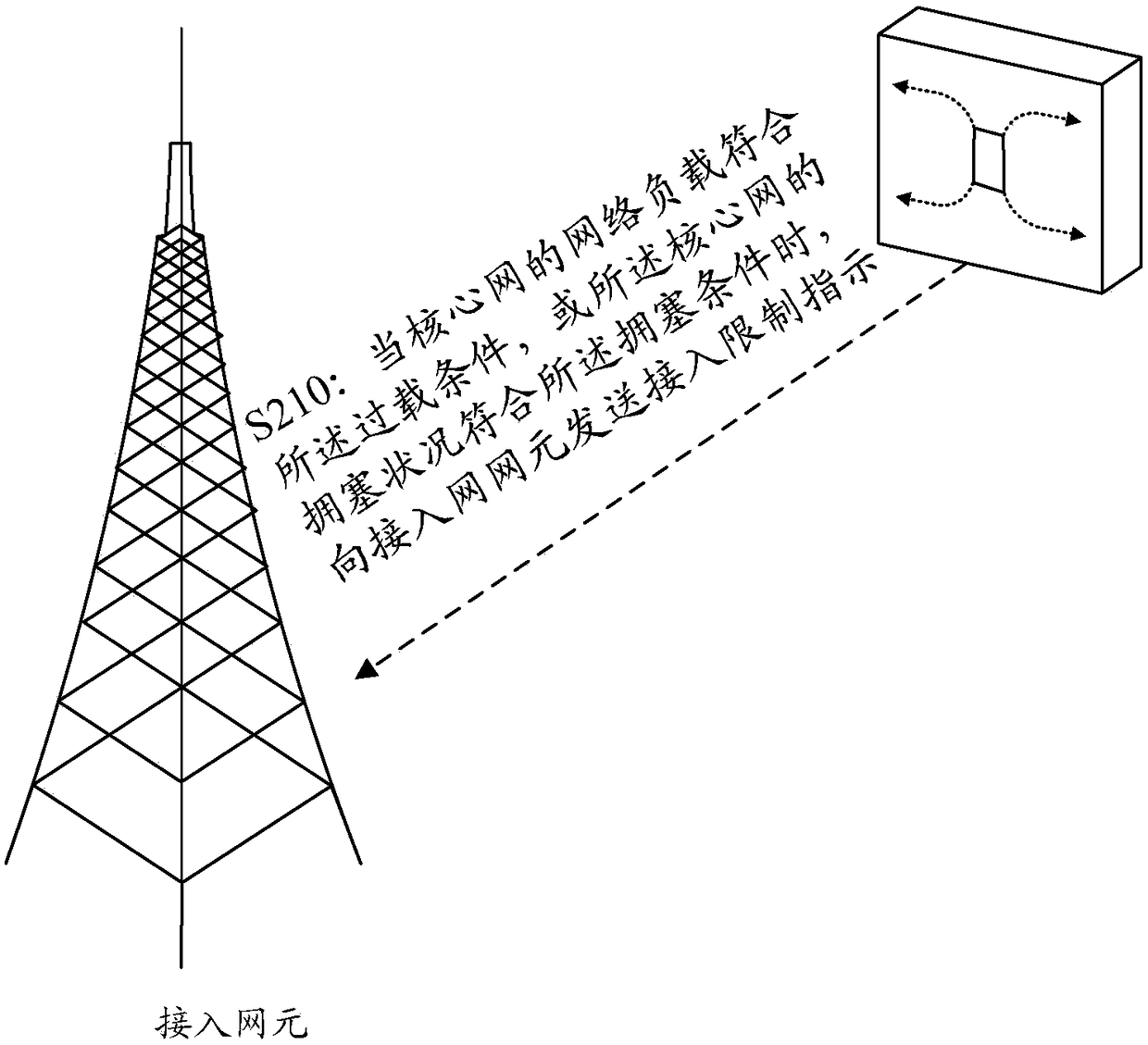
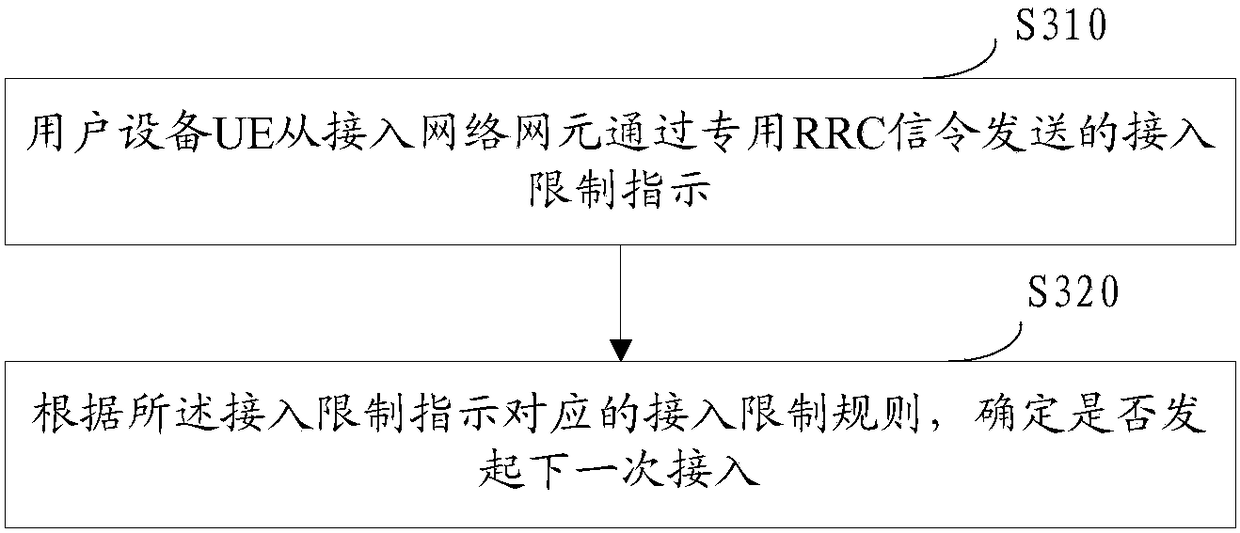
Access control method, access network element, core network element and user equipment
ActiveCN108347743ARelieve overloadReduce congestionNetwork traffic/resource managementNetwork elementRadio Resource Control
The embodiment of the invention discloses an access control method, an access network element, a core network element and user equipment. The access control method comprises the steps that when the network load of a core network or an access network accords with the overload condition or the congestion status of the core network or the access network accords with the congestion condition, the access network element sends an access limiting indication to the user equipment (UE) through a private radio resource control (RRC) signaling.
Owner:ZTE CORP
Route selection method for solving problem of wired network congestion
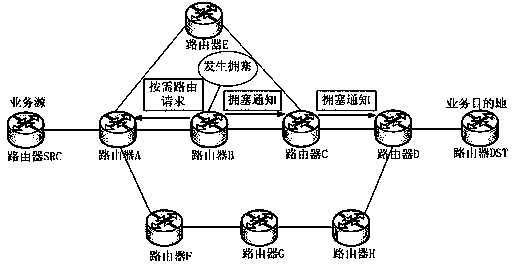
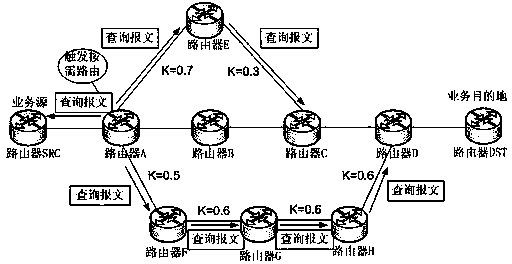
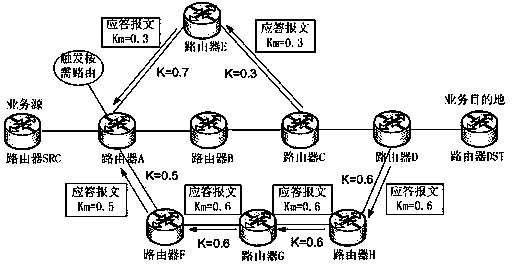
InactiveCN104038436ARelieve overloadSolve congestionData switching networksNetwork overheadOn Demand Routing
The invention discloses a route selection method for solving a problem of wired network congestion. According to the route selection method, traditional active routing networking is still used in a wide area network, on-demand routing of a preceding jump of router before a congestion point is driven through congestion monitoring, an idle link is sought in a certain range, and a congestion chain is kept off to perform business transmission. The route selection method has the advantages that the congestion chain is kept off to reasonably guide business transmission, overload of the congestion chain is relieved until the load returns to normal, and the problem of wired network congestion is solved to some extent; in specific realization, the router only needs to be simply upgraded, traditional routing protocols are not modified, intercommunication between a basic routing networking function and a traditional routing protocol is not affected, routing inquiry messages are produced within a limited scope only when congestion is generated, or network expenditure is low.
Owner:CHONGQING JINMEI COMM
A multi-root peer-to-peer IoT identification analysis method
ActiveCN103248726BConducive to maintaining political authorityImprove leakageUser identity/authority verificationData switching by path configurationThe InternetClient-side
Owner:COMP NETWORK INFORMATION CENT CHINESE ACADEMY OF SCI
Overload protection method, device and server
ActiveCN103685336BRelieve overloadThe effect of mitigating overloadTransmissionInternet communicationReal-time computing
Owner:TENCENT TECH (SHENZHEN) CO LTD
Forward supplement channel speed assignment method and device and base station
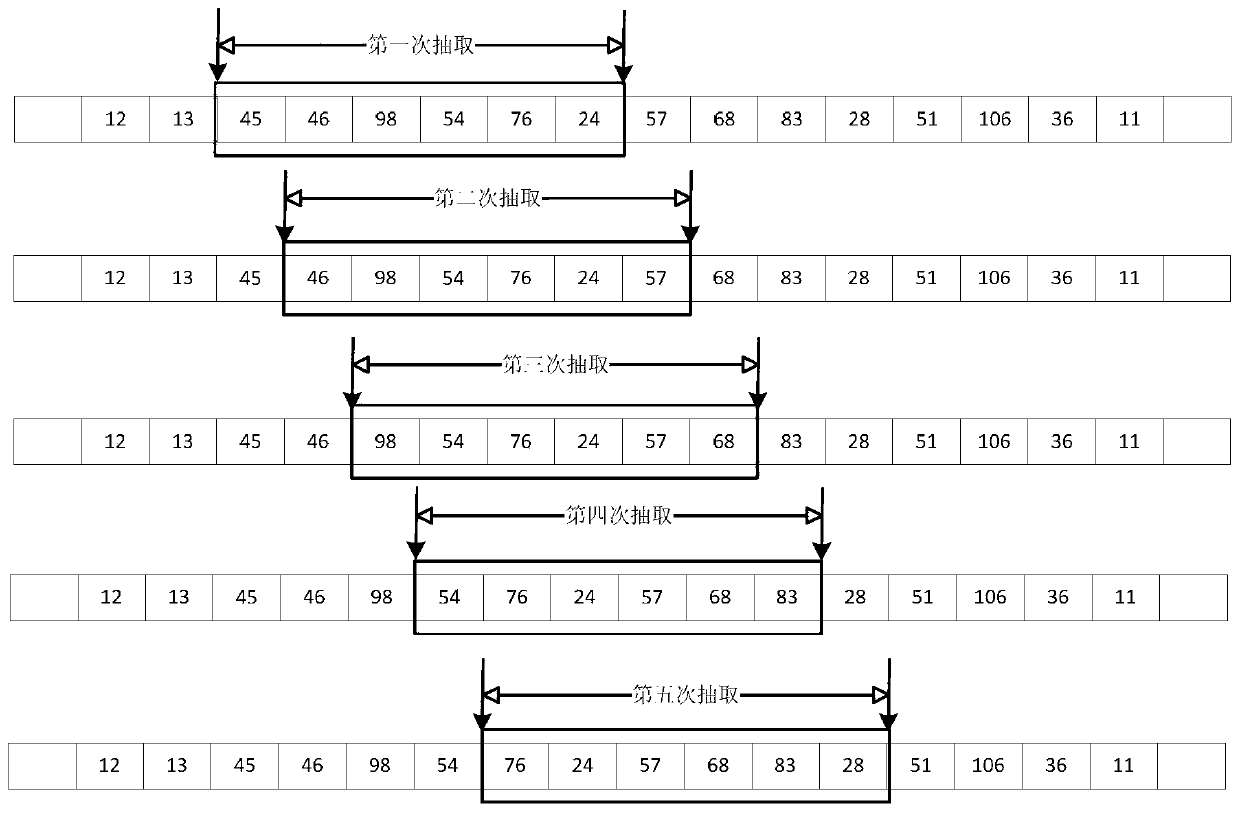
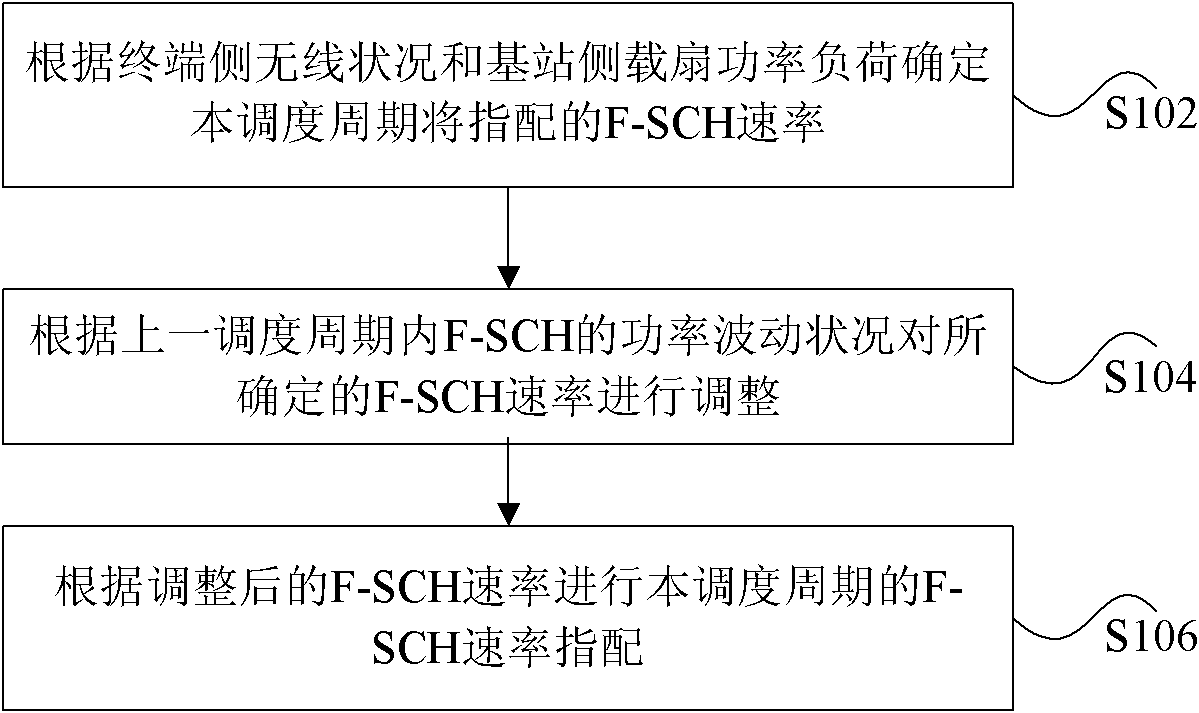
ActiveCN101990259ARelieve overloadAvoid unreasonable rate assignmentPower managementEnergy efficient ICTAssignment methodsPower load
The invention provides a forward supplement channel speed assignment method, a forward supplement channel speed assignment device and a base station. The forward supplement channel speed assignment method comprises the following steps of: determining forward supplement channel (F-SCH) speed to be assigned in the dispatching cycle according to the wireless condition of a terminal and the power load of a load fan of a base station; adjusting the determined F-SCH speed according to the power fluctuation condition of the F-SCH in the last dispatching cycle; and assigning the F-SCH speed of the dispatching cycle according to the adjusted F-SCH speed. In the invention, the speed is assigned for the terminal according to the instantaneous wireless condition of a user and the power condition of the load fan, and extra speed reduction processing is performed on the terminal with serious fluctuation by evaluating the historical power fluctuation condition of the F-SCH of the terminal, so that unreasonable speed assignment caused by instantaneous sampling is avoided, and power overload of the load fan caused by the improvement on the transmission power of the F-SCH is relieved.
Owner:ZTE CORP
Server load balancing system and method thereof
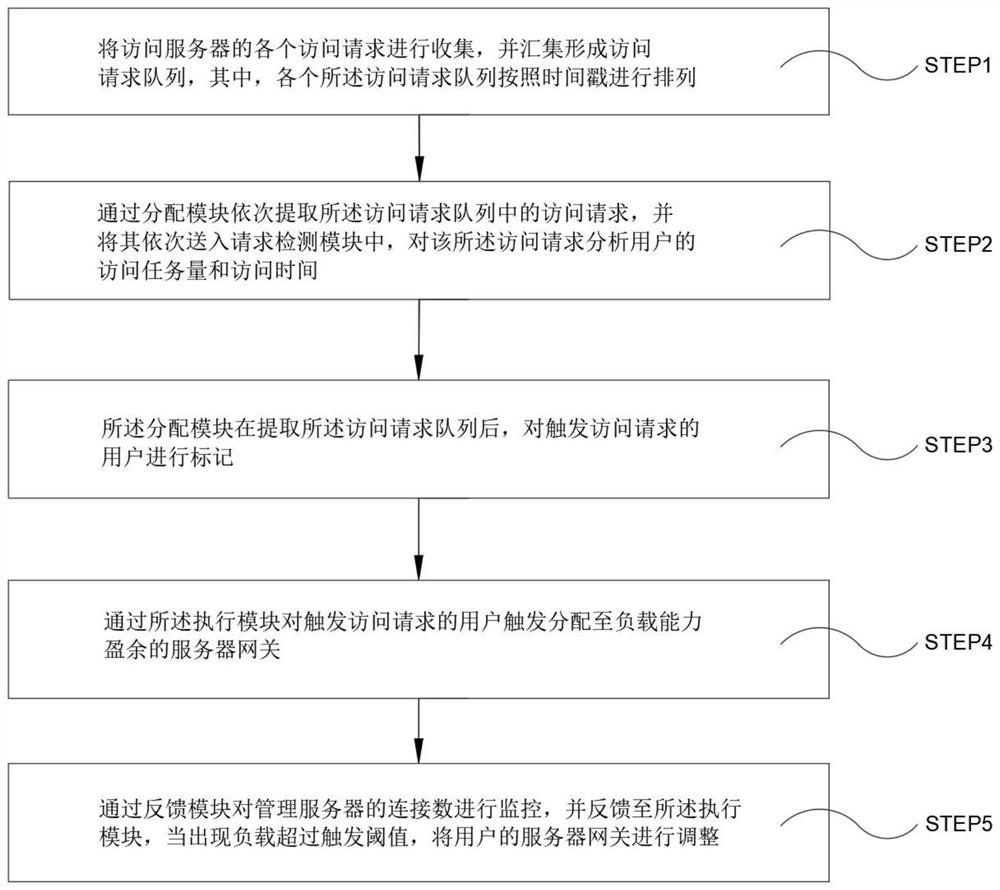
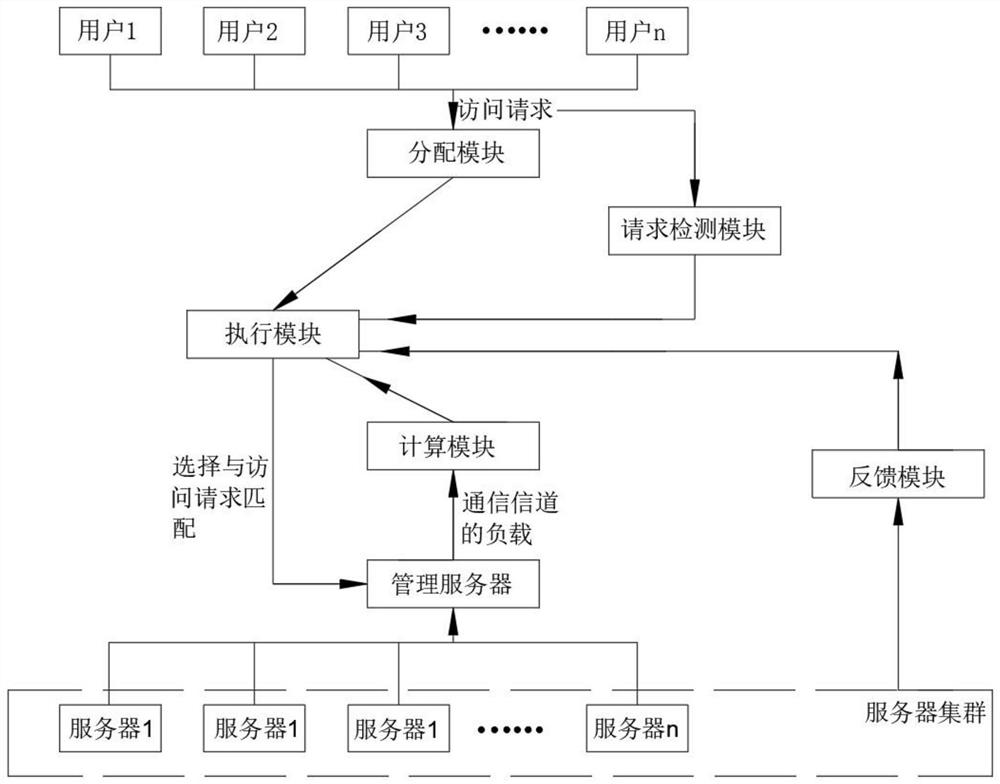
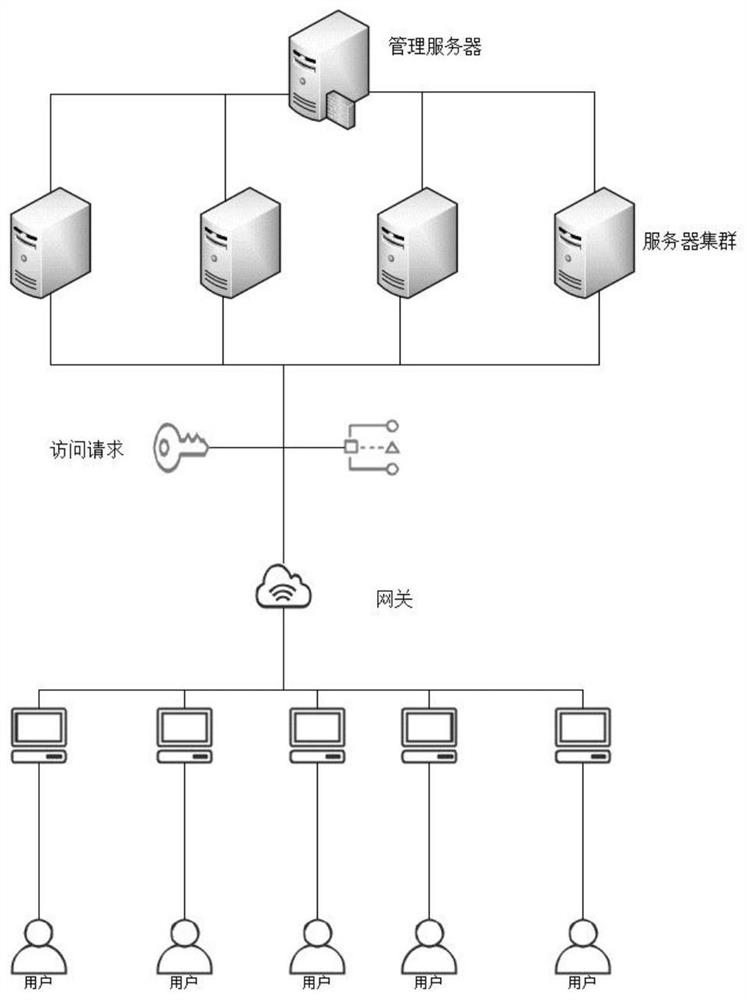
PendingCN114422517ALoad balancingImprove stabilityResource allocationTransmissionCompletion timeEngineering
The invention provides a server load balancing system, which comprises a management server and a server cluster, and is characterized in that the server cluster processes user access requests distributed by the management server, calculates load indexes of the server cluster in real time and feeds the load indexes back to the management server; the management server comprises a request detection module, a feedback module, a calculation module, a distribution module and an execution module; the calculation module calculates the load of the communication channel of the management server, and detects whether the overloaded nodes of the server cluster are lower than a preset performance level or not; the distribution module receives an access request of a user, takes out the access request from the request queue, and submits the access request to the request detection module to estimate the task load and the expected completion time of the access request; and the feedback module receives a feedback result of the server cluster. The load of the server can be ensured to be more balanced by redistributing the server through the execution module, and the stability and the reliability of managing the server are improved.
Owner:广东三合电子实业有限公司
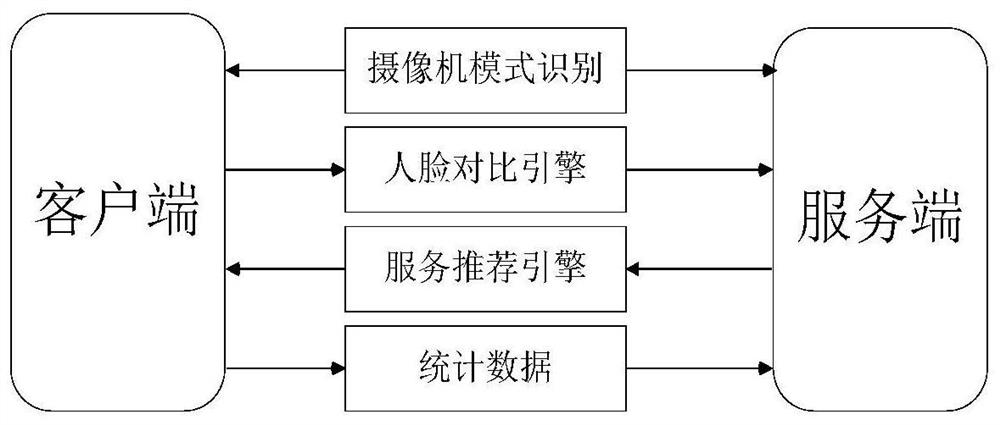
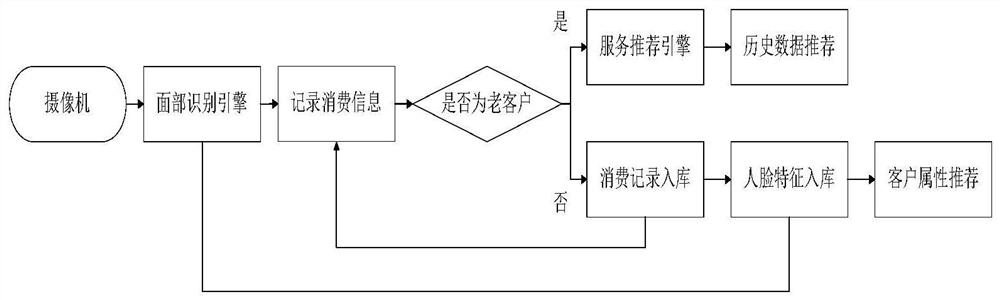
Personalized commodity recommendation method based on machine vision and improved neural network
PendingCN113435983ARelieve overloadIncrease profitDigital data information retrievalCharacter and pattern recognitionPersonalizationFeature vector
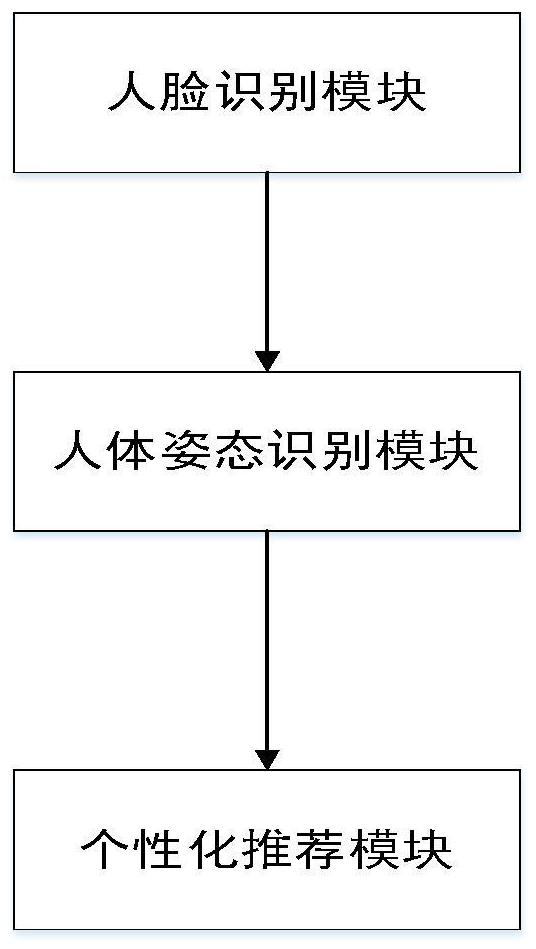
The invention discloses a personalized commodity recommendation method based on machine vision and an improved neural network, and the method comprises the steps: firstly obtaining a face image through a camera, training a face recognition model through a deep neural network according to the obtained image, and carrying out the recognition of a customer IP through the trained model; secondly, capturing behavior data of customers in the shopping process through a camera and a human body posture recognition technology, obtaining interests and hobbies of the customers, and combining personal attribute information of the customers to serve as feature vectors of the customers; finally, inputting the feature vectors of the customers and the features of the commodities into a personalized recommendation system. The requirements of quickly and accurately recommending the commodities meeting the preferences of the customers to the customers can be met, and the labor cost is reduced.
Owner:SHAANXI UNIV OF SCI & TECH
Method and system for obtaining user requirements based on the context of home work
ActiveCN105224681BImprove experienceAdvancing the business modelSpecial data processing applicationsWeb data retrieval using information identifiersCyber operationsUser needs
The invention provides a method and a system for obtaining a user demand based on a context environment of a household workplace. The method comprises the steps of obtaining mobile user network usage information based on a dataset of a mobile network operator; performing data cleaning to remove abnormal user Internet-surfing records; extracting and remaining attributes related to user interests from the user Internet-surfing records; discovering user interest space; discovering the position of the household workplace by utilizing a squeezing principle; performing data integration and data dimension reduction; and performing model training by utilizing a random forest and classifying. According to the method and the system for obtaining the user demand based on the context environment of the household workplace, a new technical scheme is provided for mining user demands and interests conveniently and efficiently by utilizing the dataset which is composed of the user network usage detailed information and comes from a mobile network operator and based on the position discovery of the household workplace and the context environment thereof.
Owner:WUHAN UNIV
A breaking method of a high-voltage superconducting current-limiting DC circuit breaker
InactiveCN103633631BReduce weightReduce volumeEmergency protective circuit arrangementsSuperconductor elements usageElectronic switchFault current limiter
The invention provides a method for breaking a high-voltage (HV) superconducting current-limiting direct current (DC) circuit breaker. The method comprises the following steps: when a HVDC side is in short-circuit fault and current / current rising steepness rises rapidly and reaches a critical value of a current limiter, a superconducting material quenches immediately, impedance rises steeply, short-circuit current is limited within set values, and meanwhile, an instruction is sent to an ultra-quick mechanical switch; the ultra-quick mechanical switch acts immediately, enables contacts to separate at an ultrahigh rigid separating speed so as to form a physical gap and generate electric arcs, and immediately sends a breaking instruction to a power electronic switch; the power electronic switch quickly breaks the short-circuit current and enables the electric arcs between the contacts to be extinguished, so as to form an isolated fracture; when the contacts are separated to final open positions and current in a lightning arrester is attenuated to zero, the HV superconducting current-limiting DC circuit breaker completes a whole breaking process, and a HVDC transmission power grid is isolated from a faulty line. The method has the advantages that the cost performances of different components are taken into account comprehensively, so that the cooperation is optimized; the number of components and devices is reduced as much as possible, so that the size is reduced, the weight is reduced, and the reliability is improved.
Owner:STATE GRID CORP OF CHINA +1
Site Selection and Capacity Calculation Method of Flexible DC Access Point
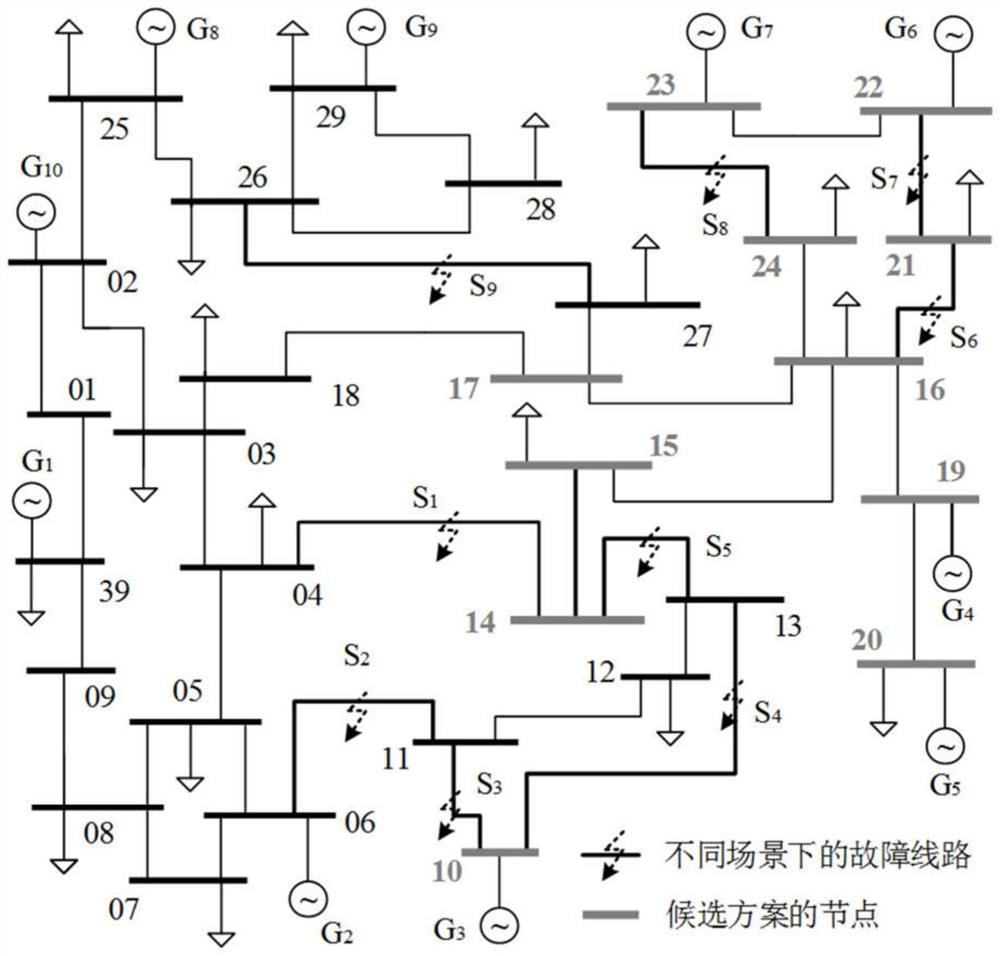
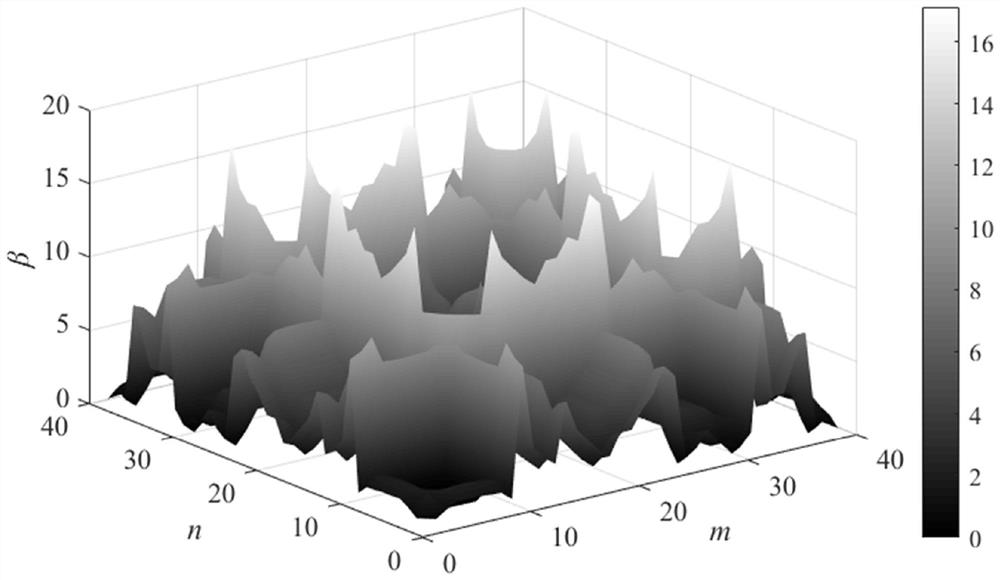
ActiveCN111953003BReduce overloadIncrease the initial screening processElectric power transfer ac networkCapacity provisioningPower grid
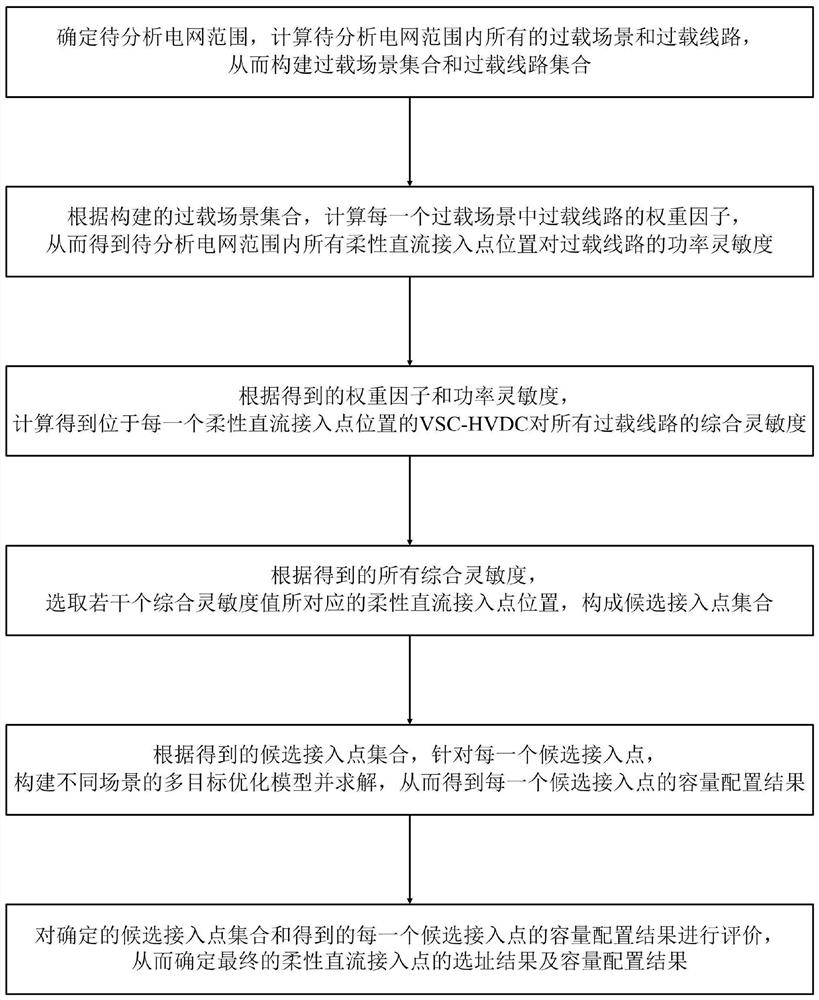
The invention discloses a site selection and capacity calculation method for a flexible DC access point, which includes determining the scope of the power grid to be analyzed and constructing an overload scene set and an overload line set; calculating the weight factor of the overload line in each overload scene to obtain all flexible The power sensitivity of the DC access point position to the overloaded line; calculate the comprehensive sensitivity of the VSC-HVDC located at each flexible DC access point to all overloaded lines; construct a candidate access point set; construct a different The multi-objective optimization model of the scene is solved to obtain the capacity configuration result of each candidate access point; the candidate access point set and the capacity configuration result of the candidate access point are evaluated to obtain the final site selection result of the flexible DC access point and capacity allocation results. The method of the invention can effectively reduce the overload problem of the AC line in the N-1 scene, and has high reliability and good effect.
Owner:STATE GRID HUNAN ELECTRIC POWER +2
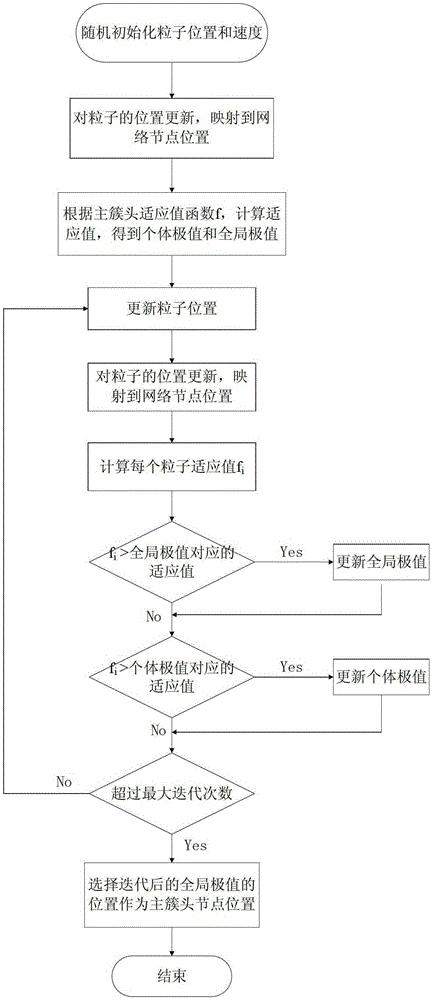
Routing method for wireless sensor network with dual cluster heads
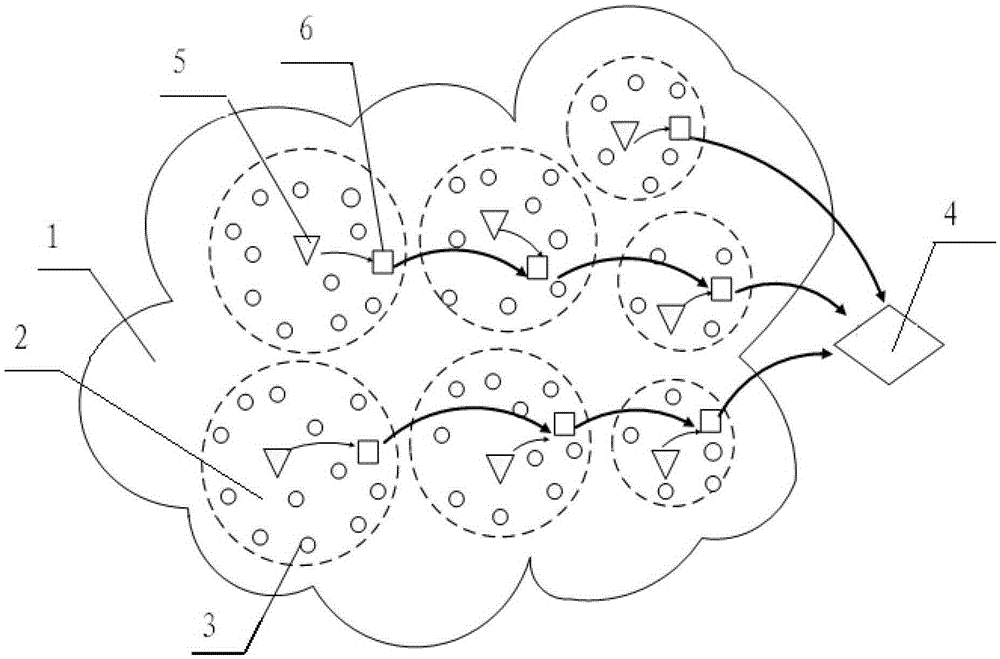
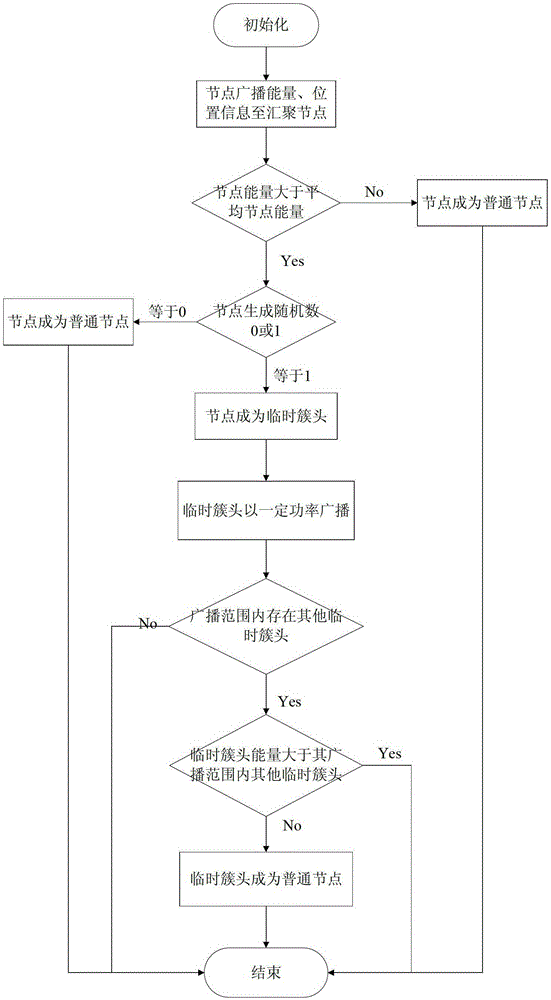
InactiveCN103269507BBalanced energy consumptionExtend the life cycleNetwork topologiesHigh level techniquesEnergy consumption minimizationWireless sensor networking
The invention discloses a routing method of a double-cluster head wireless sensor network. The method comprises the following steps: performing network initialization; performing temporary clustering, and collecting the positions and the energy information of intra-cluster ordinary nodes by selected temporary cluster head nodes; selecting out the optimal main cluster head node and the optimal secondary cluster head node by utilizing the particle swarm optimization algorithm according to the information of the intra-cluster ordinary nodes collected by the temporary cluster head nodes and the collection energy consumption and transmission energy consumption minimization criterion; selecting the next-hop node by every secondary cluster head node according to the distance from the secondary cluster head nodes to an aggregation node and the residual energy information at the data transmission stage, and transmitting data to the aggregation node by multiple hops. According to the routing method of the double-cluster head wireless sensor network disclosed by the invention, the problem that loads of cluster heads are overweight can be effectively relieved, the respective energy usage ratios of the two cluster heads are improved, the cluster heads are prevented from rapidly dying, the energy consumption of the network is balanced, and the life cycle of the whole network is prolonged.
Owner:JIANGSU UNIV OF SCI & TECH
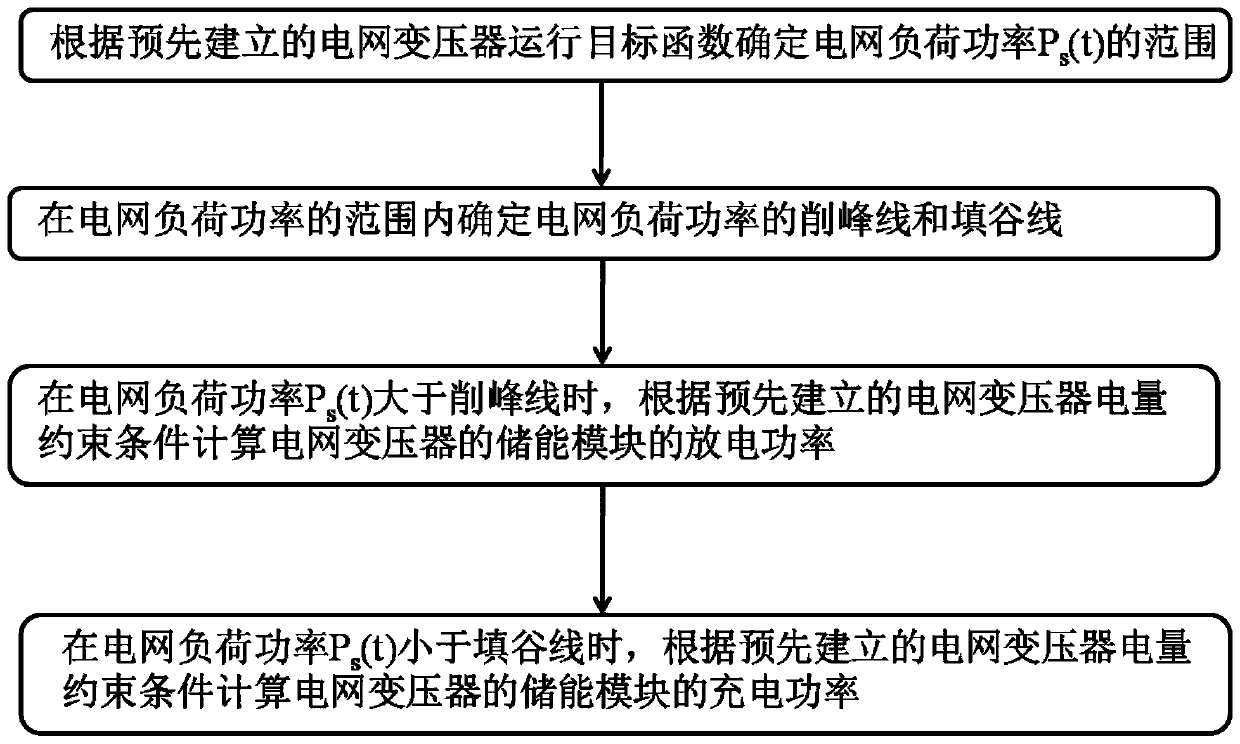
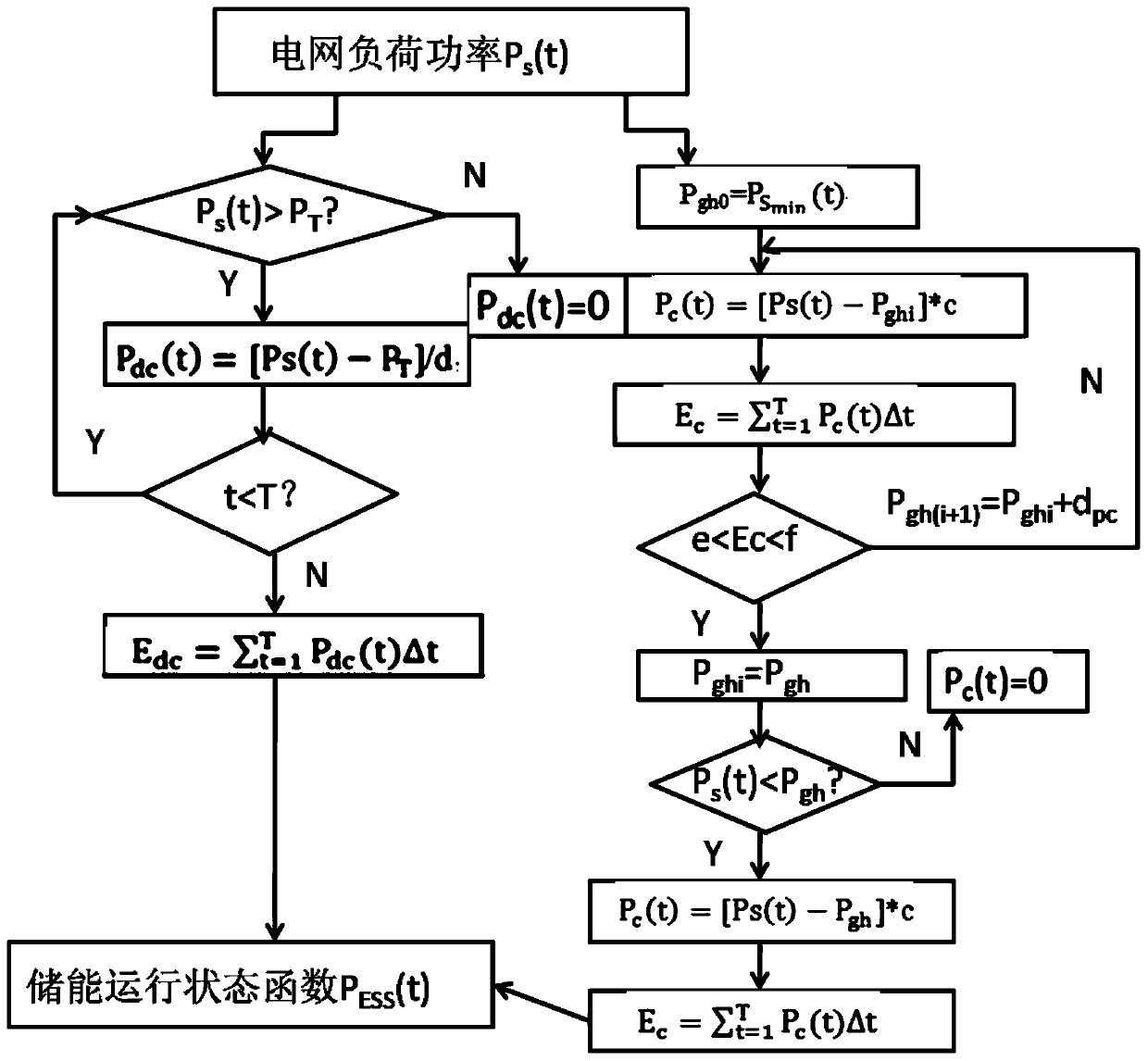
Energy storage control method and system for reducing peak-valley difference of power grid load
InactiveCN111416369AReduce the peak-valley difference of the power gridRelieve overloadAc network load balancingPower gridTransformer
The invention relates to an energy storage control method and system for reducing the peak-valley difference of a power grid load. The method comprises the following steps: determining the range of the power grid load power Ps(t) according to a pre-established power grid transformer operation target function; determining a peak clipping line and a valley filling line of the power grid load power in the range of the power grid load power; when the power grid load power Ps(t) is greater than the peak clipping line, calculating the discharge power of an energy storage module of the power grid transformer according to a pre-established power grid transformer electric quantity constraint condition; when the power grid load power Ps(t) is smaller than the valley fill line, calculating the charging power of an energy storage module of the power grid transformer according to a pre-established power grid transformer electric quantity constraint condition. Peak-valley difference of a power gridis reduced through the energy storage module, overload of a transformer is relieved, and power reverse transmission from the power grid to a main grid is reduced.
Owner:STATE GRID ECONOMIC TECH RES INST CO +3
A cooperative unmanned vehicle network computing task offloading method
ActiveCN112702714BRelieve overloadNo transmission delayNetwork traffic/resource managementParticular environment based servicesEdge computingMobile edge computing
The invention discloses an unmanned aerial vehicle cooperative computing task unloading method for the Internet of Vehicles, comprising: a mobile edge computing server receives computing tasks unloaded by the Internet of Vehicles, and if the computing task exceeds its own computing tolerance, the mobile edge computing server is determined to be an overload server , otherwise it is a non-overloaded server; the overloaded server sends a help signal to the UAV based on its own overloaded calculation amount; The original optimization problem is constructed with its own long-term energy consumption as the constraint condition, and the cooperative strategy is obtained for the overload calculation of all overloaded servers by converting and solving the original optimization problem. The present invention can alleviate the overload problem of the mobile edge computing server caused by the unbalanced distribution of unloading computation.
Owner:HUNAN UNIV
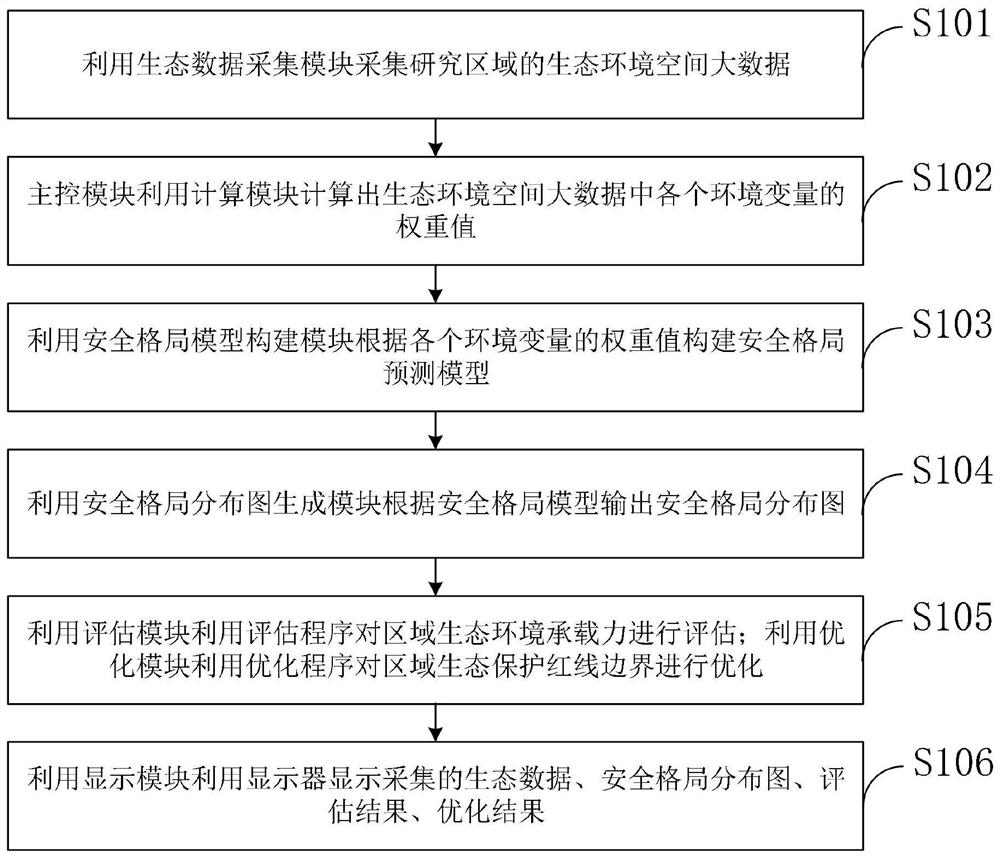
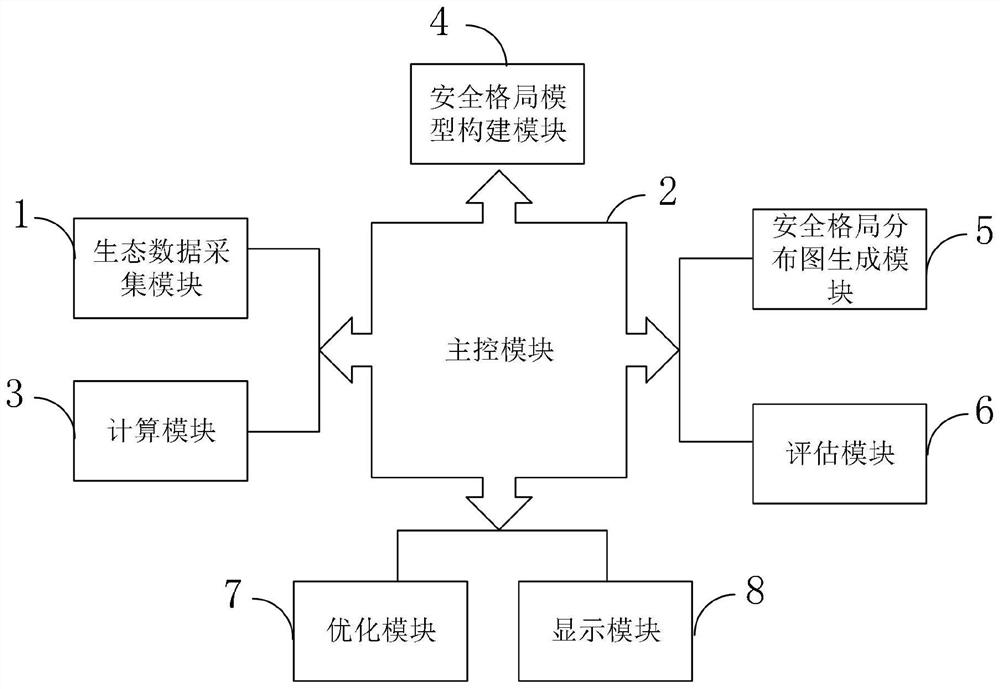
Regional ecological security pattern construction method and system based on geographic space big data
PendingCN114548698AAccurate assessmentThe assessment results are accurateImage analysisClimate change adaptationLandscape connectivityImage resolution
The invention belongs to the technical field of regional ecological security pattern construction, and discloses a regional ecological security pattern construction method and system based on geographic space big data. The regional ecological security pattern construction system based on geographic space big data comprises an ecological data acquisition module, a main control module, a calculation module, a security pattern model construction module, a security pattern distribution diagram generation module, an evaluation module, an optimization module and a display module. According to the invention, the evaluation module is utilized to determine the overload type of any one index overload or the combination of two or more index critical overload in the load result of the basic evaluation data and the load result of the special evaluation data, so that the evaluation result is more reference and more accurate; meanwhile, the resolution and accuracy of pure zoning are improved through an optimization module, an ecological protection red line electronic vector diagram which is practical, clear in boundary and good in ecological integrity and landscape connectivity is formed, reference is provided for field exploration, and the field workload is reduced.
Owner:XINJIANG INST OF ECOLOGY & GEOGRAPHY CHINESE ACAD OF SCI
Method and system for controlling instant congestion of server
The invention provides a method and a system for controlling the instant congestion of a server. In the method, controlling state comprises a first state, a second state and a third state, in each state, a data packet is processed by different methods under different conditions. The method comprises the following steps of: 1) receiving a data packet, then discarding or forwarding the data packet according to the controlling state; and 2) comparing the average request return time delay of the data packet with a detection threshold value, then changing controlling state or keeping an original state according to a comparison result, when the average request return time delay is greater than the detection threshold value, switching from the first state to the second state, or switching from the second state to the third state, and when congestion condition is improved, switching from the third state to the first state. By the method and the system, session integrity can be protected, the retransmission of massive data packets caused by the oscillation of server load can be avoided, and learning or training is not required and computation cost is low.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Method and device for determining and processing indication information and request message
InactiveCN104270725BReduce the impact of UEs in congested/overloaded areasReduce congestionNetwork traffic/resource managementComputer security arrangementsMultimedia Broadcast Multicast ServiceApplication server
The present invention discloses a method and apparatus for determining, processing and requesting information, in the above method, determining whether the user surface data carried by MBMS is congested or overloaded, configuring the first indication; The first indication is sent to GCS AS, wherein the first indication is used to provide a reference basis in the process of GCS AS requesting MCE or eNB to stop the cluster traffic hosted by MBMS due to congestion or overload of user plane data. According to the technical solution provided in the present invention, it is possible to alleviate MBMS carrying congestion / overload, thereby reducing the impact on non-congestion / overload area UE.
Owner:ZTE CORP
Automatic summary generation method and device
ActiveCN105653704BFix low-quality summariesRelieve overloadSpecial data processing applicationsAlgorithmTheoretical computer science
The invention relates to an automatic summarization generating method and device. The method comprises the steps of modeling a text to generate a sentential network diagram which comprises edge weights; computing first weights of sentences in the text according to the edge weights and initial weights of the sentences in the text; computing term weights according to frequencies of terms in the sentences and the first weights of the sentences corresponding to the terms; computing second weights of the sentences according to the frequencies of the terms in the sentences and the term weights of the terms; computing final weights of the sentences according to the first weights and the second weights; and if the difference between the final weight after nth iterations and the final weight after (n-1)th iterations is less than a preset threshold value and the difference between the term weight after nth iterations and the term weight after (n-1)th iterations is less than a preset threshold value, generating an automatic summarization. By means of the method, the problem that the quality of single long text summarizations is low is solved; the information overload is alleviated; and the summarization quality is improved.
Owner:NANJING UNIV OF FINANCE & ECONOMICS
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com