Analytic method for multi-root peer-to-peer identity of internet of things
A technology of IoT identification and analysis methods, applied in user identity/authority verification, data exchange through path configuration, electrical components, etc., can solve the problem of equality, intercommunication and information sharing without the basic resource services of the Internet of Things, and the independence of item analysis cannot be guaranteed. rights, failure to achieve peer-to-peer analysis, etc., to achieve the effect of ensuring legitimacy and security, improving single point of failure, and maintaining political authority
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The following describes the present invention in detail through specific embodiments and accompanying drawings.
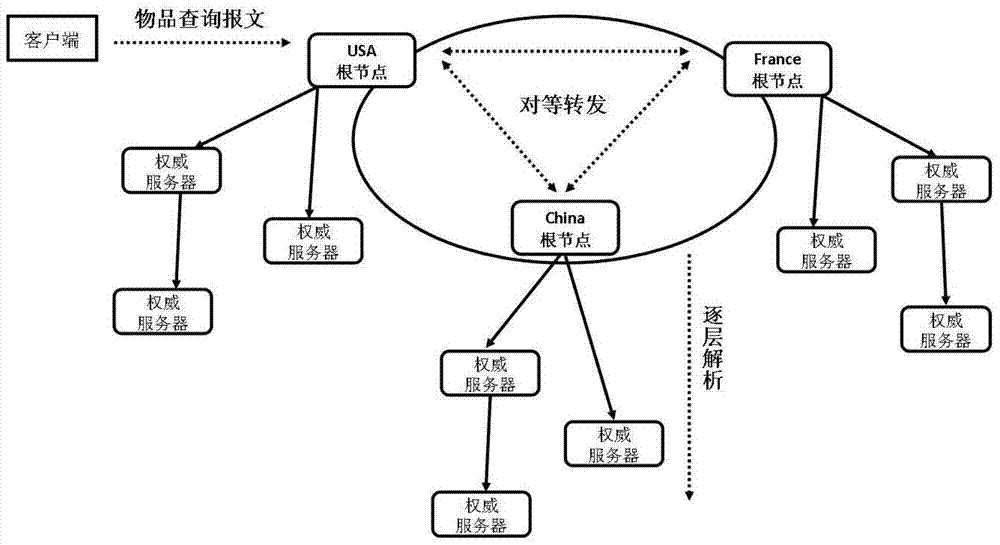
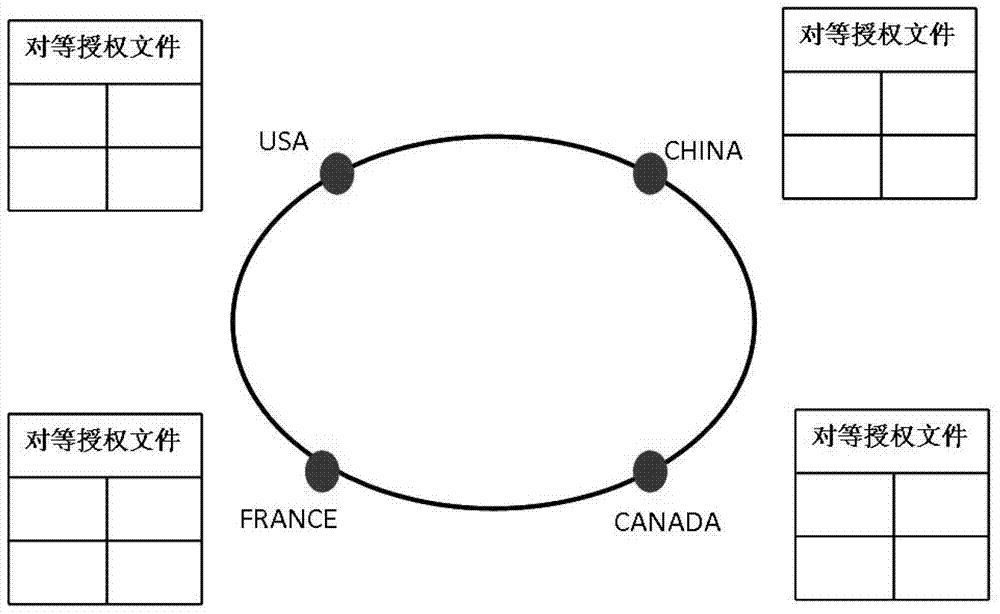
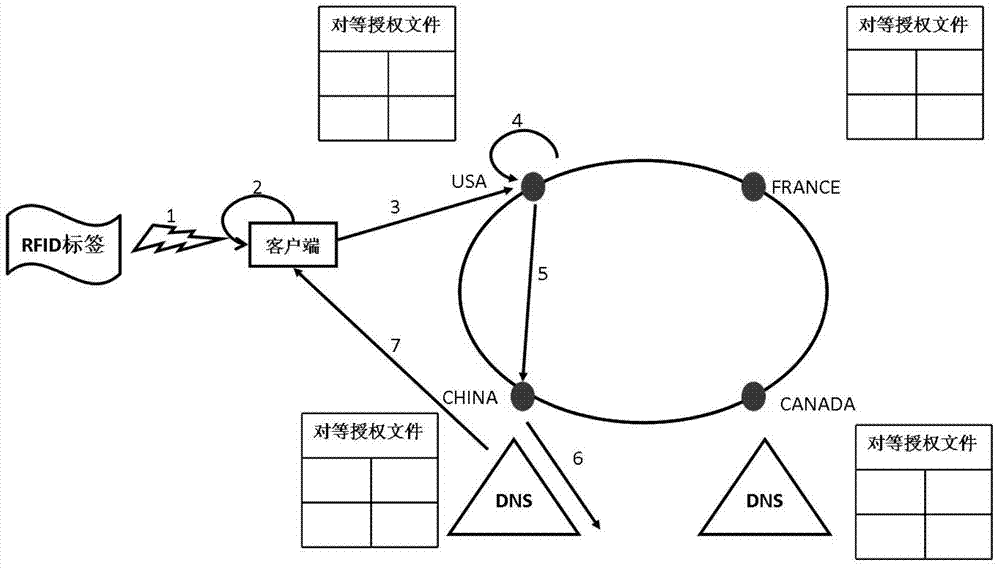
[0036] The Internet of Things identification peer-to-peer analysis architecture proposed in the present invention transforms a single root node into multiple peer root nodes with equal status, consistent functions, and mutual cooperation at the top level of the analysis system. These root nodes are respectively managed and controlled by the corresponding country or organization, and jointly process item object identification query requests on the basis of ensuring that each root node has the resolution autonomy. The specific implementation content is described below.
[0037] 1. System Architecture
[0038] 1) As attached figure 1 As shown, the client that initiates the Internet of Things identification resolution request is the resolver, which is responsible for receiving RFID encoding and other object identifications and converting them into FQDN (Fully Qualifie...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com