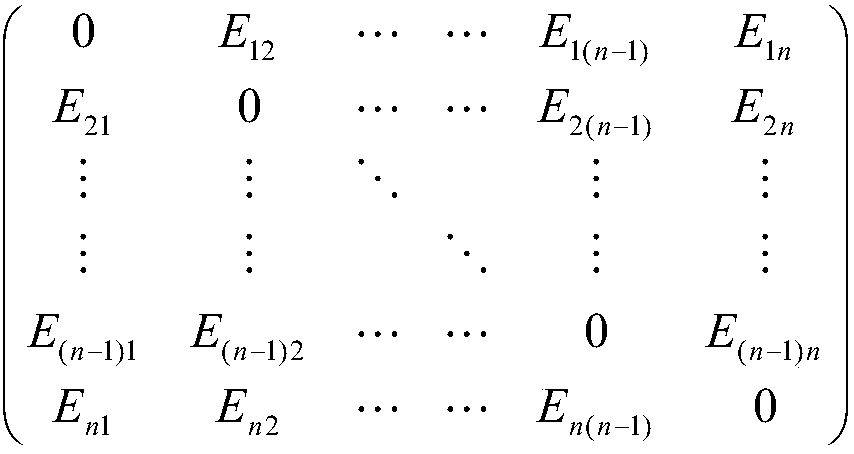Information security risk propagation control method and apparatus based on infectious disease model
A technology of information security and control methods, applied in computational models, biological models, instruments, etc., can solve the problem of inability to accurately and quickly determine the scale of node failures, and achieve the effect of ensuring safe and stable operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] Embodiments of the present invention will be described below in conjunction with the accompanying drawings.
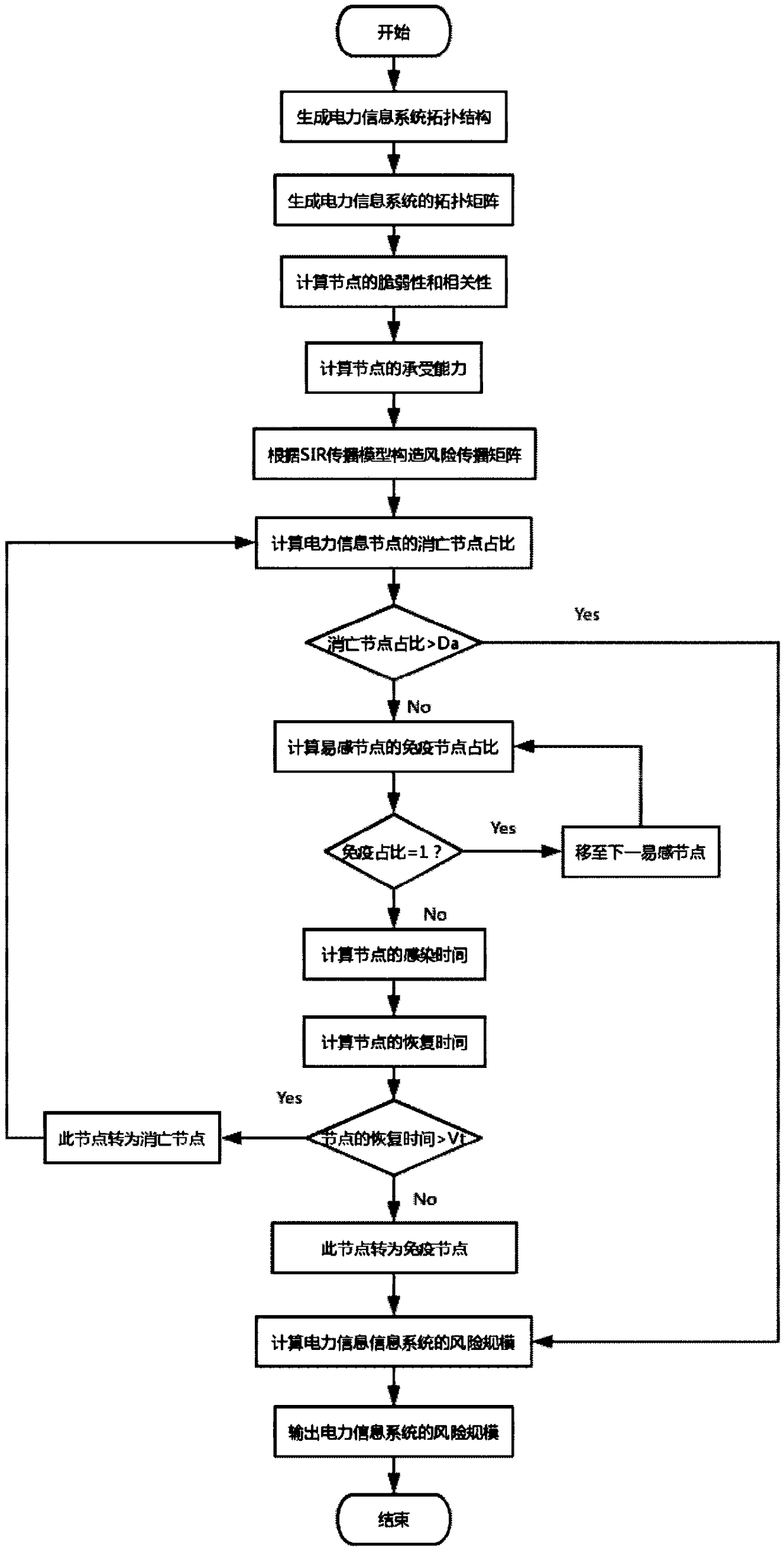
[0033] Such as figure 1 As shown, the present invention designs a method for controlling information security risk propagation based on an infectious disease model, which specifically includes the following steps:
[0034] Step 1: Number each node in the power cyber-physical system as 1, 2, 3,..., N, generate an undirected weighted topological network structure of the power information fusion system, and use the nodes of the power cyber-physical system topology It is represented by an undirected weighted sparse adjacency matrix H of Z edges of order N×N, where N is the total number of nodes, and Z is the total number of edges; go to step 2;
[0035] Step 2: According to Calculate the vulnerability of node i, where i, j ∈ 1, 2, 3, ..., N; E ij is the closeness between node i and its connected nodes, M i Denotes the combination of all neighbors of node i, G ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com