Single Linux core and multiple Android systems-based network virtualization method
A system network and virtualization technology, which is applied in the field of network virtualization based on a single Linux kernel and multiple Android systems to reduce management costs and economic costs and ensure security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
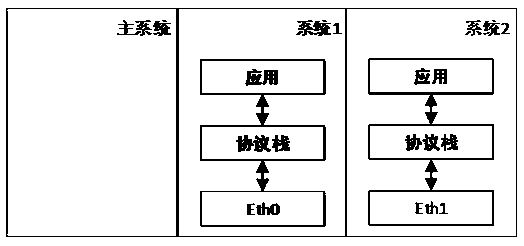
[0020] Such as figure 1 Shown, a kind of network virtualization method based on multiple Android systems of single Linux kernel, three containers are set, and described container refers to the container that realizes by the namespace technology of Linux kernel; The main system is set in one of the containers, all the other containers are set with The virtual Android systems with independent network protocol stacks are independent and isolated from each other; the virtual Android systems include various versions of Android.
[0021] The main system assigns a physical network adapter to each virtual Android system, and the virtual Android system directly communicates with the external network through the network protocol stack and the physical network adapter.
[0022] Furthermore, each container is set with an independent APN and VPN, so as to realize the function of independently accessing a specific network. For many users who need to access a specific internal network, need...
Embodiment 2
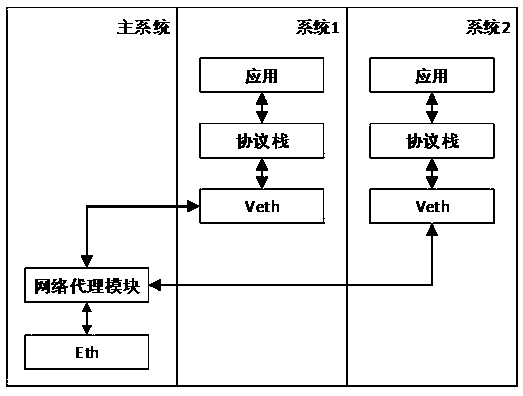
[0024] The difference between this embodiment and embodiment 1 is: as figure 2 As shown, a physical network adapter and a network proxy forwarding module are set in the main system, a virtual network adapter is set in each virtual Android system, and a plurality of virtual network adapters are respectively connected with the network proxy forwarding module;
[0025] The data of the virtual Android system is sent to the outside world sequentially through the network protocol stack, the virtual network adapter, the network agent forwarding module and the physical network adapter; meanwhile, the physical network adapter will receive The received network packet is forwarded by the virtual network adapter to the corresponding virtual Android system, thereby realizing the network access of the virtual Android system.
Embodiment 3
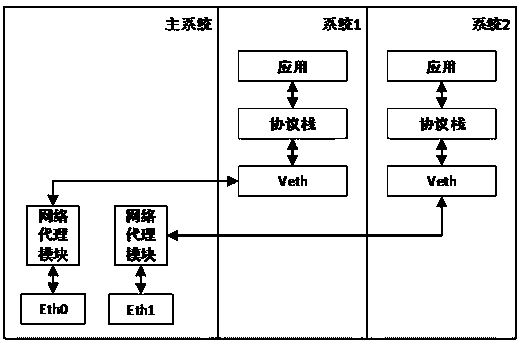
[0027] The difference between this embodiment and embodiment 1 is: as image 3 As shown, a plurality of physical network adapters and a plurality of network agent forwarding modules are set in the main system, a virtual network adapter is set in each virtual Android system, and each network agent forwarding module is respectively connected with a physical network adapter and A virtual network adapter is associated.
[0028] The data of described virtual Android system is sent to by the network protocol stack, described virtual network adapter, the network agent forwarding module associated with described virtual network adapter and the physical network adapter associated with described network agent forwarding module successively outside world. At the same time, the physical network adapter sends the received data sequentially through the network proxy forwarding module associated with the physical network adapter, the virtual network adapter associated with the network proxy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com