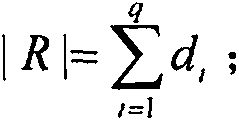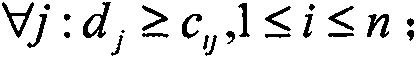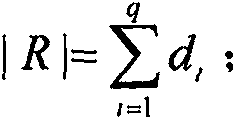Role mining optimization modeling method meeting user role-usage cardinality constraint
A modeling method and role technology, applied in data processing applications, special data processing applications, instruments, etc., can solve problems such as the lack of a unified standard for role sets, and achieve the effect of simplifying construction, concise mining results, and reducing mining costs.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The technical solutions of the present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
[0030] 1 Preliminary knowledge and problem description
[0031] From the user's point of view, a user-friendly RBAC system should assign as few roles as possible to each user. In theory, users are only willing to have a role with all the permissions required to perform tasks. In fact, many application systems are also designed in this way. A basic requirement of role mining is that the mined roles should be able to completely reconstruct the original UPA, ie integrity. In other words, for any user there exists a set of role assignments such that the user gets exactly the same set of permissions through role assignment as before the assignment, and can be described as: in is the Boolean matrix multiply operator. If a user was originally assigned a permission, the user should be assigned at least one rol...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com