Abnormal behavior monitoring method and system
A technology for abnormal monitoring and behavior, which is applied in special data processing applications, instruments, unstructured text data retrieval, etc., and can solve the problems of unconcealment, high risk, and monitoring of the log audit system
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
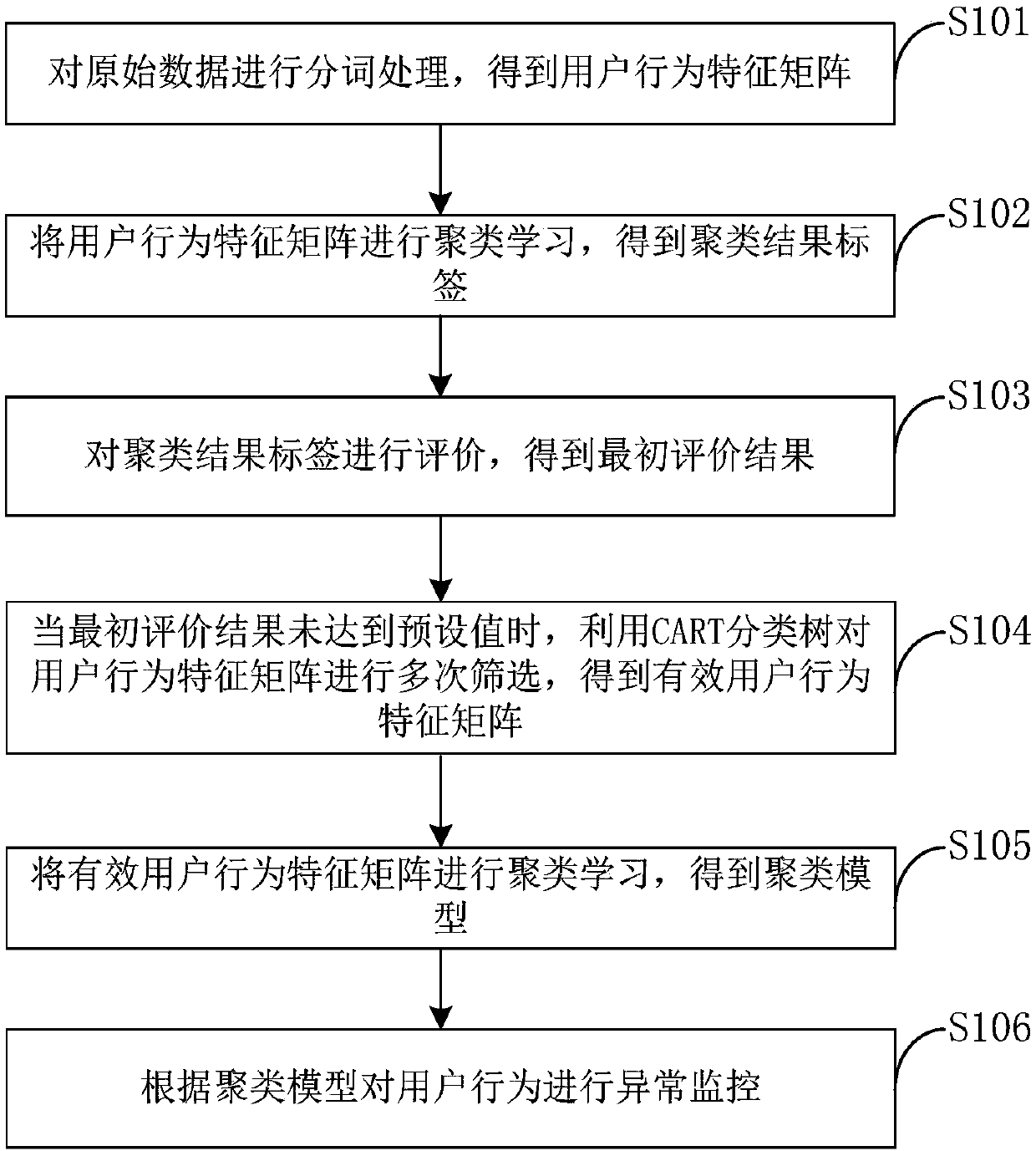
[0064] figure 1 A flowchart of the abnormal behavior monitoring method provided by the embodiment of the present invention is shown.
[0065] like figure 1 As shown, a method for monitoring abnormal behavior provided by this embodiment includes the following steps:
[0066] Step S101, performing word segmentation processing on the original data to obtain a user behavior feature matrix;
[0067] Specifically, the raw data refers to the behavior operation data in the audit log, for example, all the operation data performed by the user logging in to the bastion host. Perform word segmentation on the original data, extract keywords, and use the extracted keywords as user behavior characteristics; matrix. This standardizes the data and eliminates the influence of dimensions. The user behavior characteristic matrix can well describe the user behavior characteristics involved in the corresponding audit log. Among them, tf-idf is a commonly used weighting technique for informati...
Embodiment 2
[0123] like Figure 4 As shown, this embodiment provides an abnormal behavior monitoring system, including a processing module 10, a first cluster learning module 20, an evaluation module 30, a feature screening module 40, a second cluster learning module 50, and a monitoring module 60;
[0124] The processing module 10 is used to perform word segmentation processing on the original data to obtain a user behavior characteristic matrix;
[0125] The first clustering learning module 20 is used to perform clustering learning on the user behavior feature matrix to obtain a clustering result label;
[0126] The evaluation module 30 is used to evaluate the clustering result label to obtain the initial evaluation result;
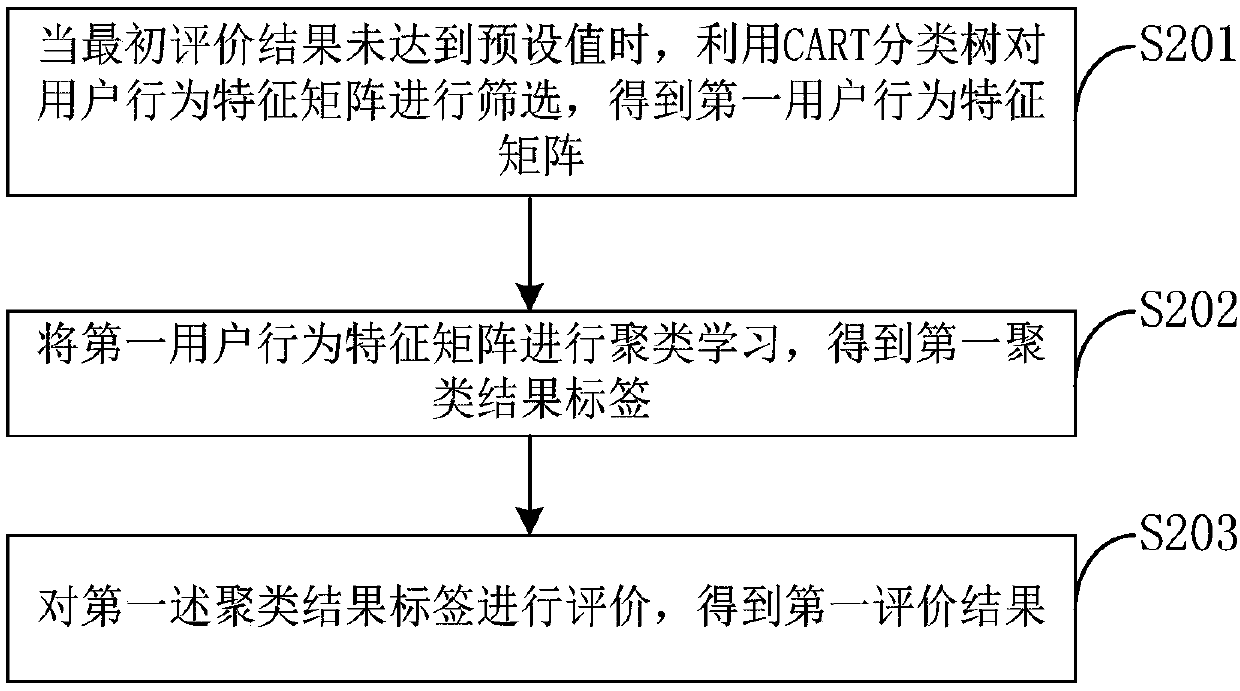
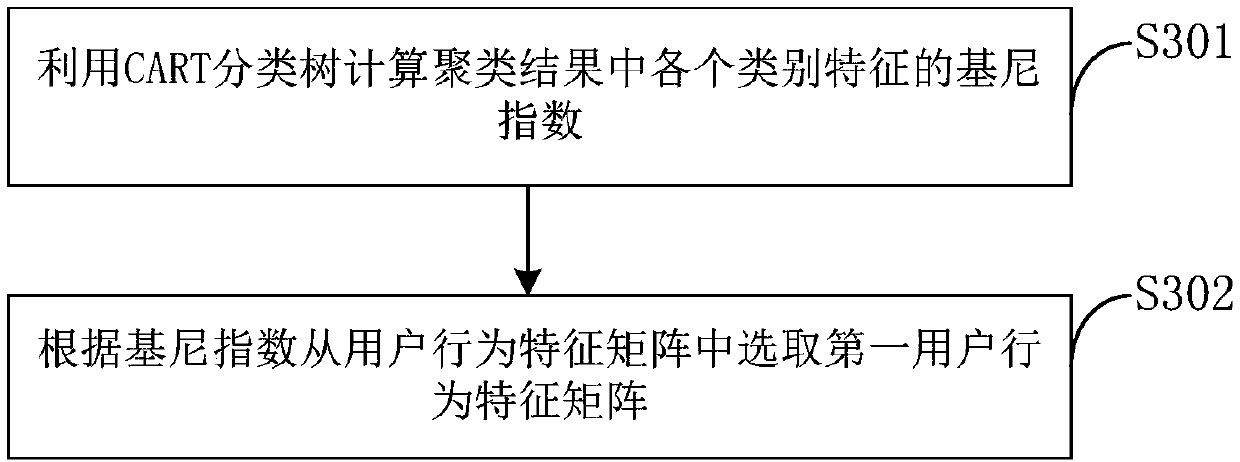
[0127] The feature screening module 40 is used to screen the user behavior feature matrix multiple times by using the CART classification tree to obtain an effective user behavior feature matrix when the initial evaluation result does not reach the preset value; ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com