Application data leakage preventing method and apparatus
An application, anti-leakage technology, applied in the application field, can solve the problems of limited security, easy to be broken, and can not meet the security requirements.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] The technical solutions of the present invention will be further described in detail below through specific embodiments.
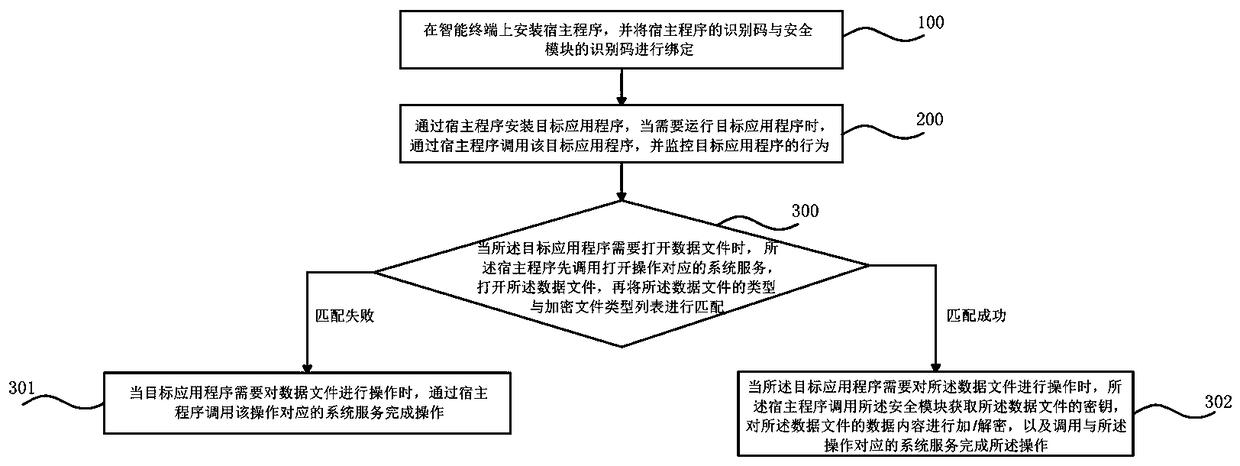
[0042] Embodiments of the present invention provide a method for preventing leakage of application data, such as figure 1 As shown, the method includes the following steps:
[0043] In step 100, a host program is installed on an intelligent terminal, the intelligent terminal has a security module embedded or externally inserted, and the identification code of the host program and the identification code of the security module are bound.
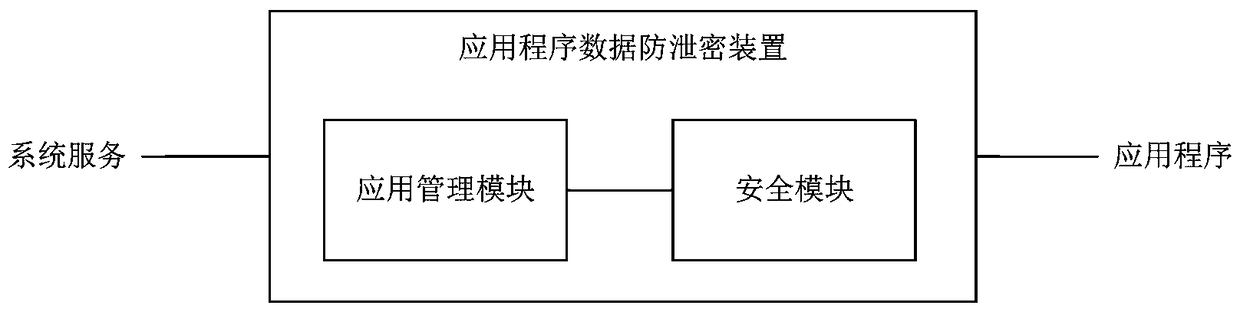
[0044] Preferably, the host program is an application management system implemented in the form of software, which is used to intercept and proxy system services on the intelligent terminal, install, call, monitor and manage target applications, and perform security checks on security The module function is called.
[0045] The security module is used for key generation, encryption and decryption, and identity ve...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com