Method for capturing network worm based on honeypot technology
A honeypot technology and worm technology, applied in the field of catching network viruses, can solve problems such as network congestion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in detail below in conjunction with examples.
[0023] 1. Feature extraction method
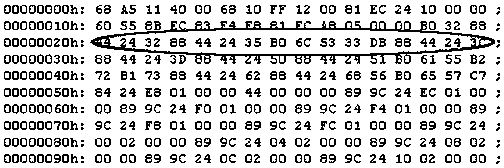
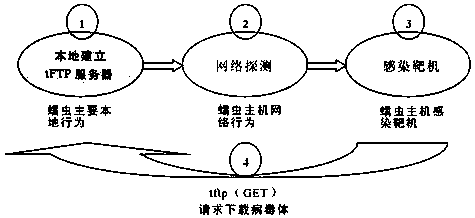
[0024] The worm execution body first detects the host with the vulnerable service in the network. If a host that meets the requirements is detected, the virus body program will be transmitted to the host with the vulnerable service through the network, and the virus body program will be started and some settings will be made. Protective measures, such as setting it to run automatically at startup. After the virus body program runs, it will continue to detect vulnerabilities and replicate itself, and perform work with a certain purpose. The characteristics of the worm program can be extracted through the infected file, and the specific process is as follows:
[0025] (1) Start the service program with a certain vulnerability, and check the service port of the vulnerability to confirm that the service program with a certain vulnerability is runni...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com