Database self-adaptive encryption method
An encryption method and database technology, applied in the field of database adaptive encryption, can solve the problems of low encryption pertinence, low comprehensiveness of data types, insufficient ability to obtain data types, etc., and achieve the convenience of encryption process and maintain high efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
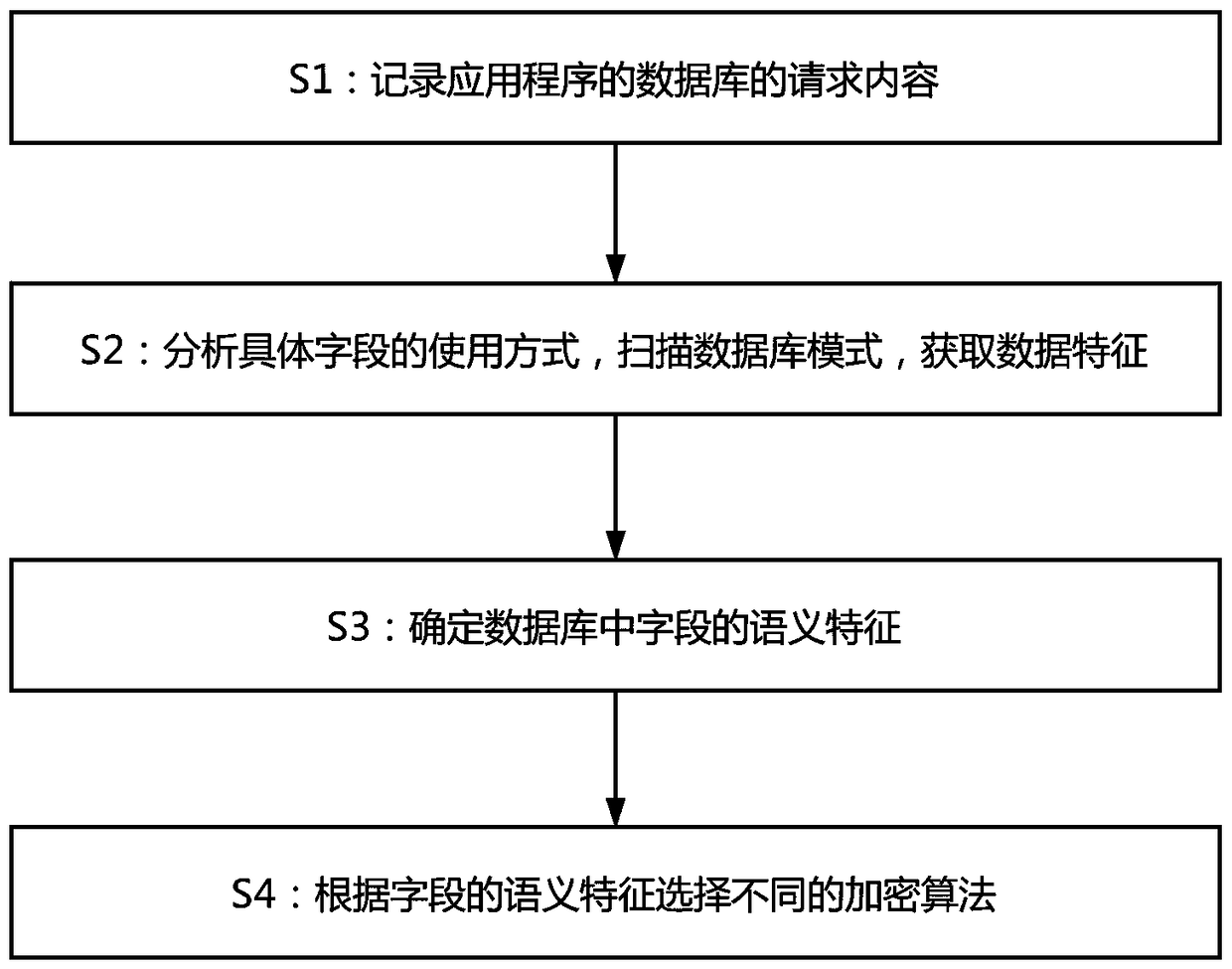
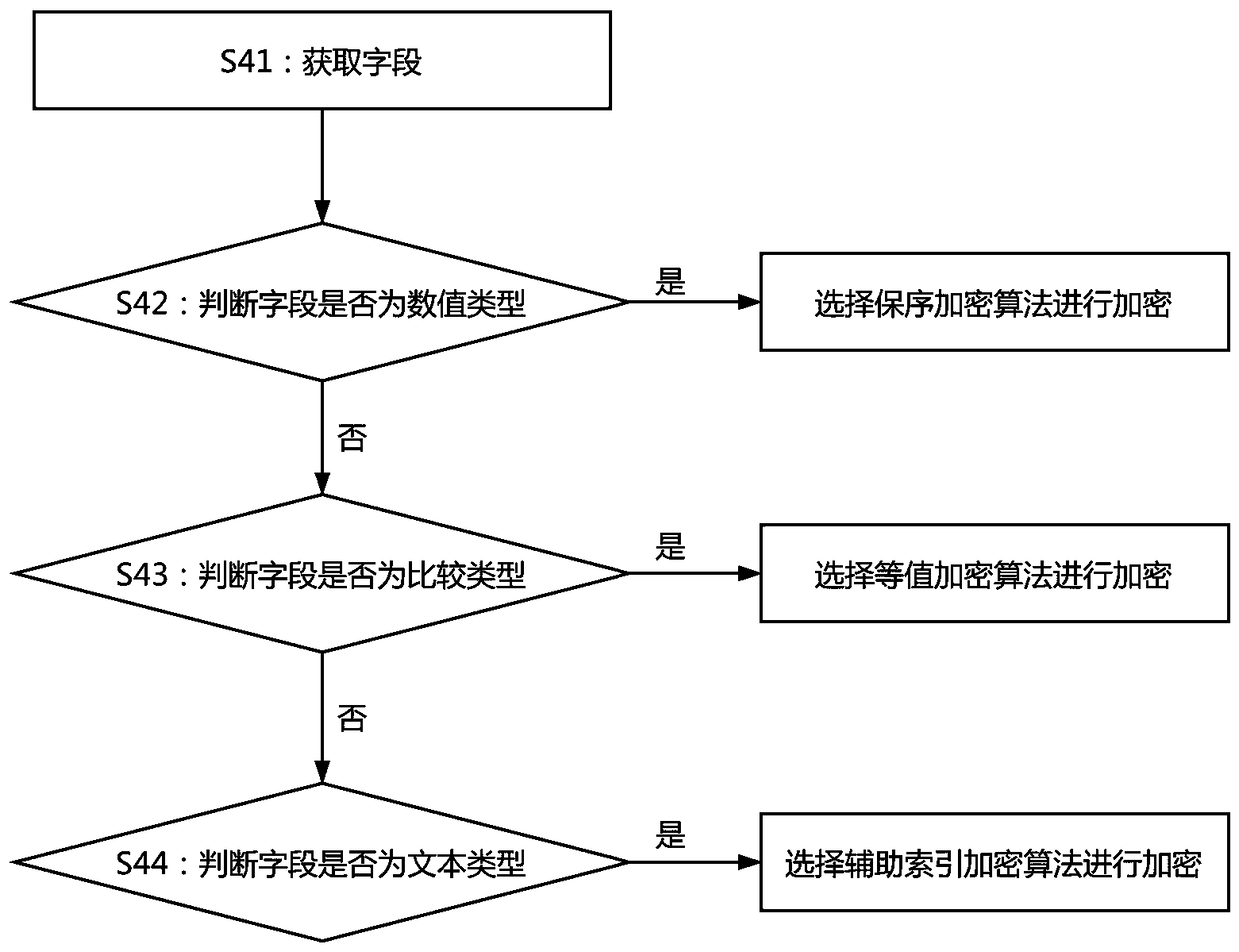
[0043] Example 1: The following combination Figure 1 to 3 What is shown is only one of the embodiments of the present invention. In order to solve the above-mentioned problems, the present invention adopts the following technical solutions to achieve: a database adaptive encryption method, including the following steps:
[0044] S1: Record the requested content of the application's database;
[0045] To encrypt data, first obtain the data, obtain the database request content in the database, and analyze and encrypt the data based on the content.
[0046] Modern Web application systems have relatively fixed usage patterns for databases, and specific encryption methods can be selected according to the specific characteristics and usage of the data to avoid efficiency problems caused by encryption and achieve a better balance between confidentiality and availability.
[0047] S2: Analyze the usage of specific fields, scan the database mode, and obtain data characteristics;
[0048] Under...
Embodiment 2
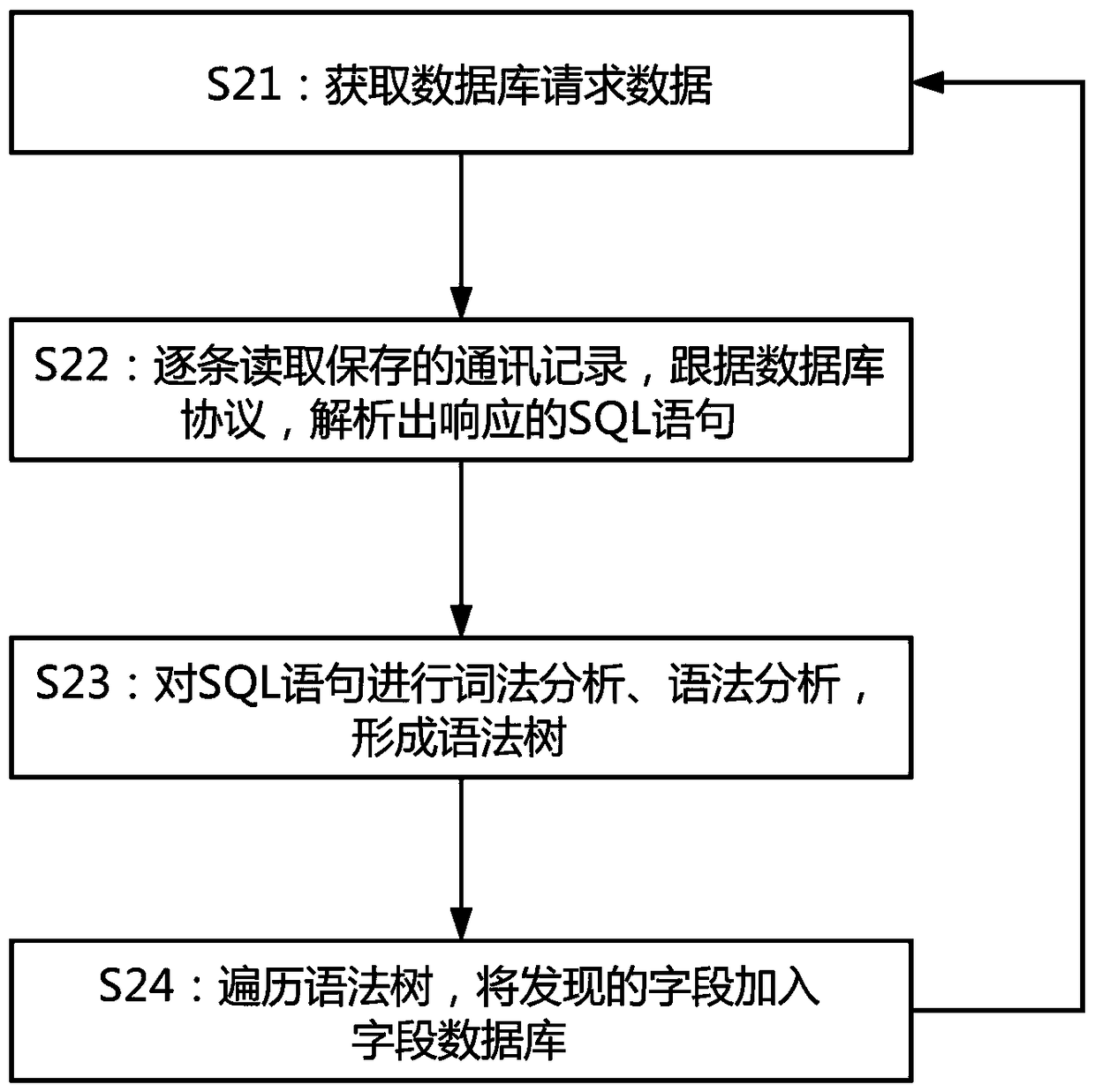
[0064] Example 2: Still combined Figure 1 to 3 What is shown is only one of the embodiments of the present invention. In order to make a database adaptive encryption method of the present invention more accurate, the encryption process is more rigorous and more convenient, there are many data processing steps in the present invention:
[0065] First, before performing step S1, a storage library for storing the recorded database request content is established.
[0066] Due to the large communication traffic of the database service, the storage library here uses a caching mechanism. First, it is stored in the form of a file on the disk and recorded for a period of time so that the data in it contains all the patterns used by the application on the database. Make the coverage of data analysis more comprehensive.
[0067] Then, step S2 is specifically:
[0068] S21: Obtain database request data;
[0069] Here is to get the database request data from the repository.
[0070] S22: Read the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com