Cookie-based secure single sign-on method and unified authentication service system thereof
An authentication service and single sign-on technology, which is applied in the computer field, can solve problems such as increased difficulty of system integration, different ways of site connection, low security, stability and usability, to facilitate system integration, improve security, and stability sex high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] Embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings.
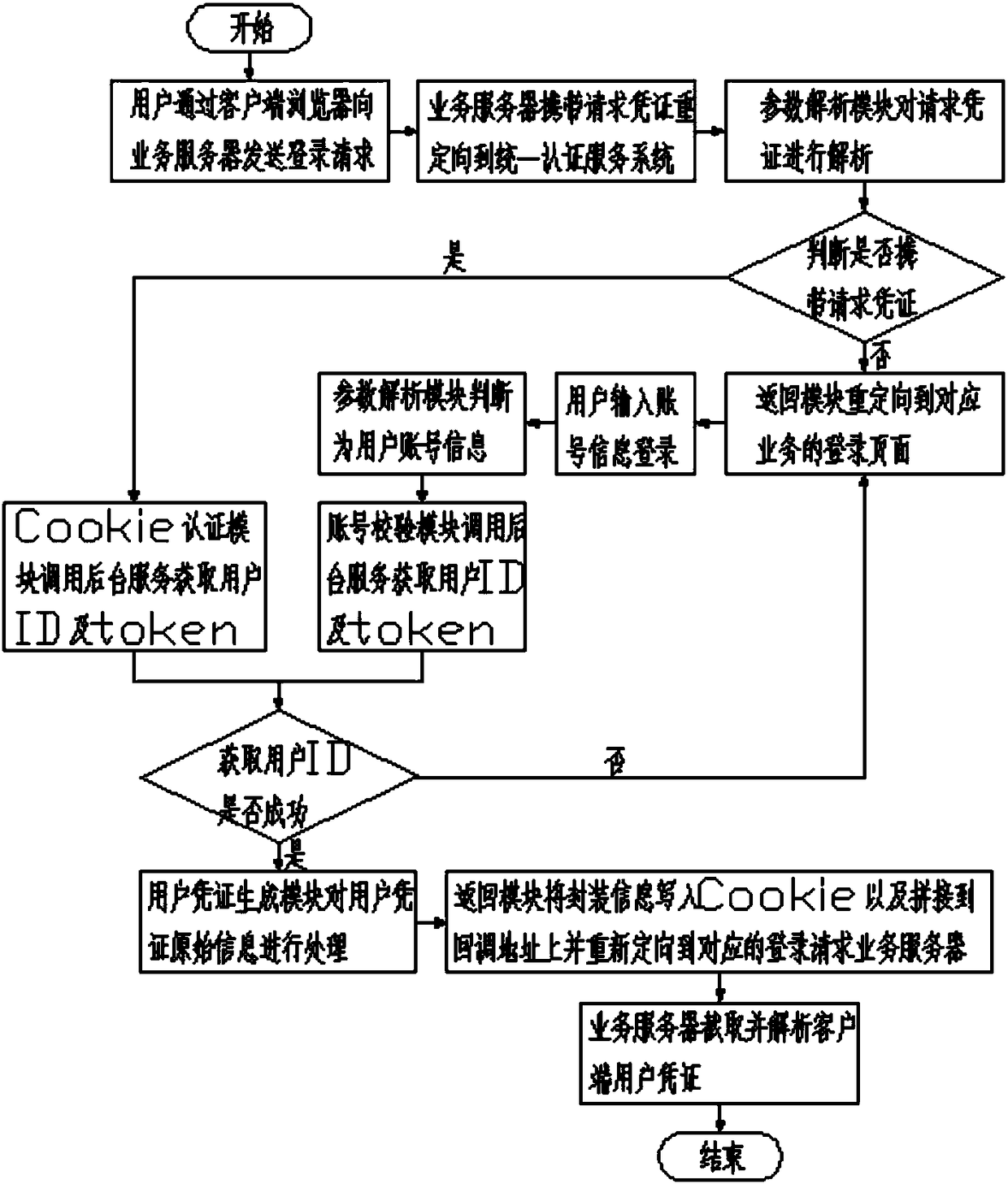
[0028] A unified authentication service system based on Cookie single sign-on, the unified authentication service system includes a parameter analysis module, an account verification module, a Cookie authentication module, a user credential generation module and a return module;
[0029] Among them, the parameter parsing module is used for parsing the request parameter when the unified authentication service system receives the login request sent by the client browser or the business server, and judging whether the request parameter is empty, and calling the return module if the request parameter is empty; If the request parameter is not empty, when the request parameter contains user account information, the account verification module is invoked; when the request parameter contains relevant Cookie information, the Cookie authentication module is invok...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com