Authentication method of application, terminal and computer readable storage medium
An application and authentication technology, applied in the information field, can solve the problems of increasing the risk of token exposure, waste of operating costs, hidden dangers of H5, etc., to reduce the risk of exposure and capture, and avoid hidden dangers.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
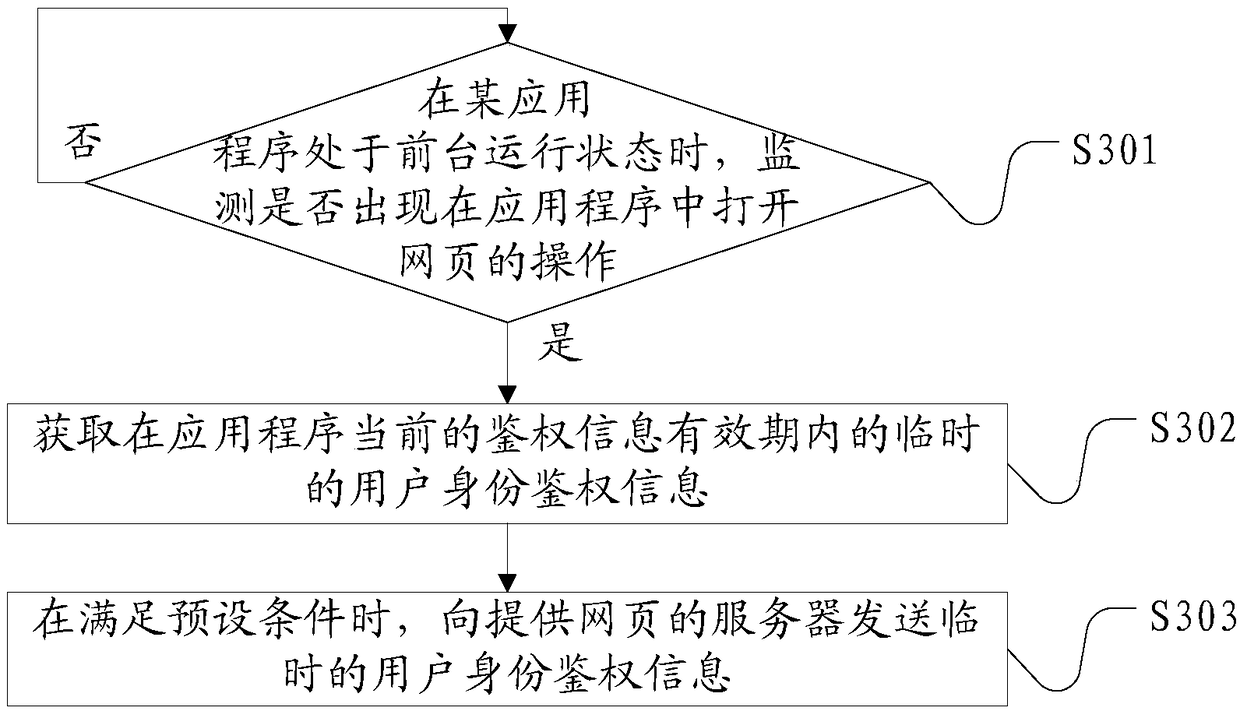
[0067] In this age of APP (Application, application program) flying around, for the entire product development team, high-speed iterations and explosive function additions have become the era label of the Internet industry, and the progress measurement in units of hours or even minutes has become the norm. In order to improve the functional richness of the APP, most of the APPs are full of web pages (such as H5 pages) or elements with a high proportion. Judging from the current mainstream non-tool and non-large-scale game applications, the use of hardware functions Some of the parts that remain unchanged throughout the year and have a high usage rate will use native apps, and other functions are almost all implemented in H5. At present, H5 pages generally send tokens to the corresponding server when authentication is required, and it is difficult to encrypt parameters transmitted by H5 pages. This approach makes token information easy to be captured. Some users can use this to...
no. 2 example
[0098] This embodiment proposes another authentication method for a web page in an application program. In this method, it is assumed that the application program is a user-centered APP, the user-center server and the server are the same terminal equipment, and the authentication information is valid for one day and time The segment is 0:00-24:00 every day, and the webpage embedded in the APP is an H5 page. The method includes the following steps:
[0099] Step A: User Center App login
[0100] The user enters the user name and password on the login interface of the APP, and the client sends the user name and password to the user center server. After passing the authentication, the user center server will generate an AccessToken (that is, the access user identity authentication in the first embodiment) Authorization information) and SecretKey (that is, the decryption key in the first embodiment) are issued and returned to the client, and the user center server will also store ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com