Key management system and method
A management system and key technology, applied in the key management system and management field, can solve the problems of high investment, high cost, inapplicable application scenarios, etc., and achieve the effects of low storage consumption, simplified number of digits, and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
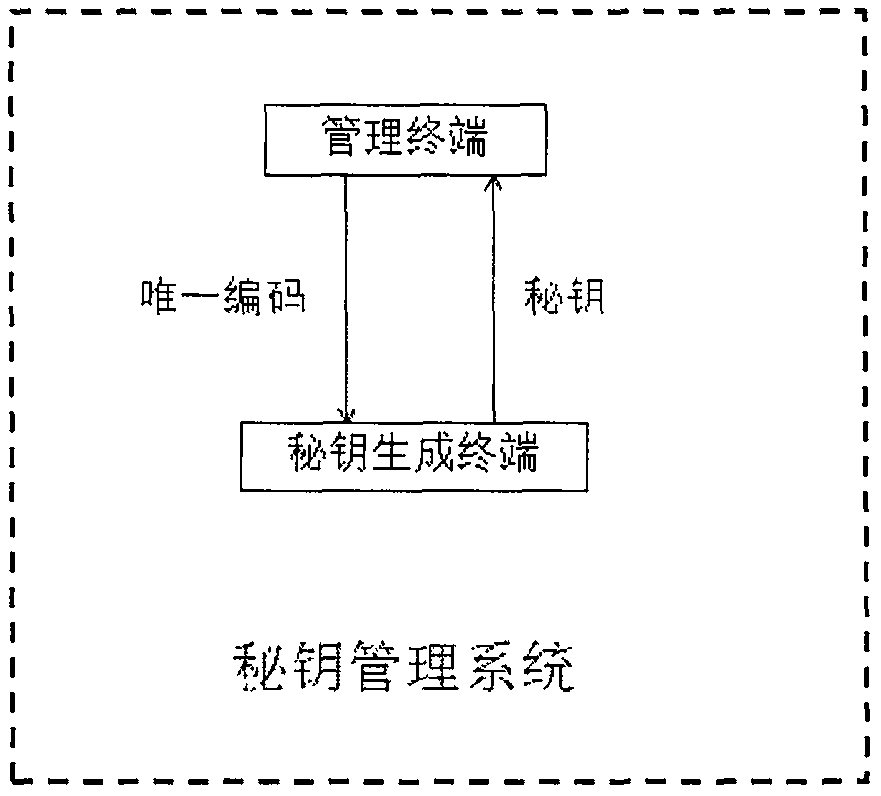
[0058] figure 1 The structure diagram of the key management system in the present invention is shown, which includes:
[0059] A management terminal, which is used to randomly generate a unique code; in this embodiment, the management terminal includes but is not limited to various access control systems, such as fingerprint locks, digital password locks, etc.;
[0060] A secret key generation terminal, which is used to receive the code, perform encryption calculation according to the code, generate a secret key and output it; in this embodiment, the secret key generation terminal may be equipped with Windows, Java, Android, or Web, etc. The operating platform of the computer, including but not limited to smart mobile terminals such as mobile phones and tablet computers, and fixed terminals such as local PCs, as long as the codes can be obtained and encrypted calculations can be performed;
[0061] After the secret key is generated, the management terminal is further configured...
Embodiment 2
[0078] Figure 4-5 Shown is a flow chart of the steps of the key management method of the present invention, which includes:
[0079] S1. Randomly generate a unique code through the management terminal;
[0080] S2, encrypting and calculating the code through a secret key generation terminal, generating a secret key and outputting;
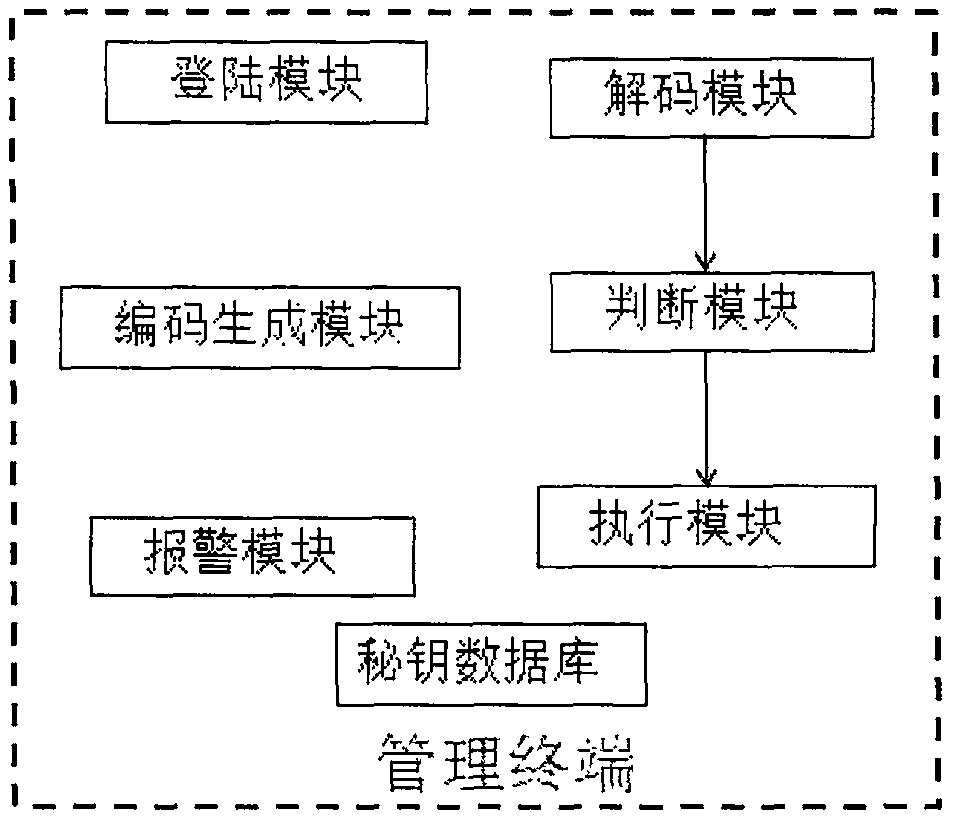
[0081] S3. After the secret key is generated, the management terminal parses the secret key information, and performs an unlocking / locking operation according to the parsing result.
[0082] Specifically, the step S1 includes the following steps:
[0083] S11, the user inputs login information, enters the management interface of the management terminal, and inputs a user instruction;
[0084] S12. The management terminal randomly generates the code according to a user instruction.
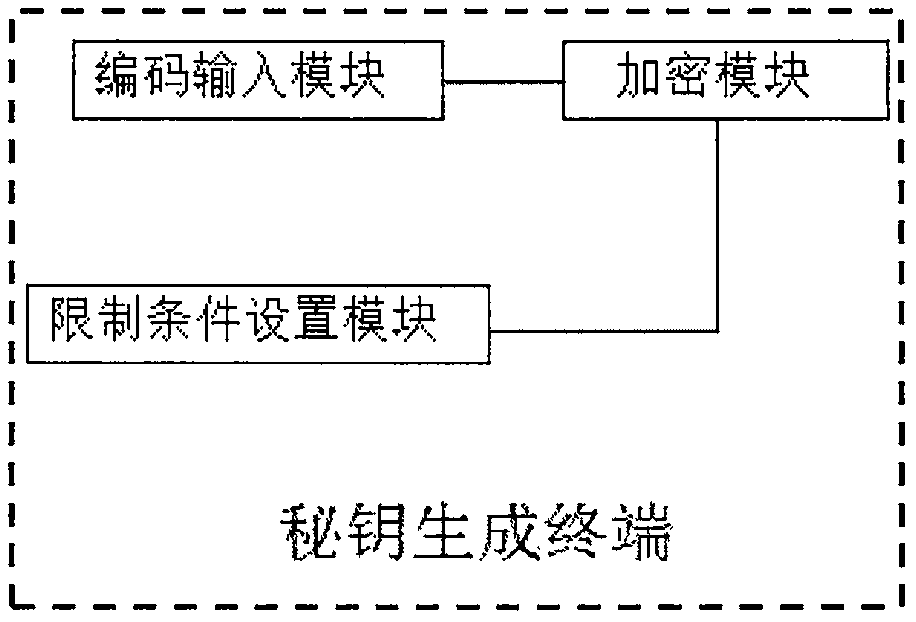
[0085] The step S2 includes the following steps:
[0086] S21, the user inputs the obtained code in the secret key generation terminal;
[0087] S22, the user se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com