Random sub-domain name DDoS attack detection method
An attack detection and randomizer technology, applied in the field of network security, can solve problems such as low efficiency and traffic impact, achieve the effect of simple and efficient model, avoid false positive rate increase, and simple and robust classifier
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
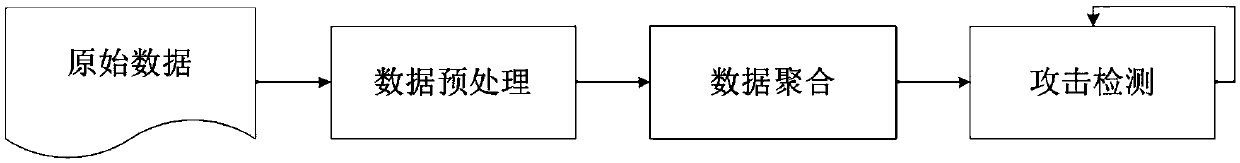
Method used
Image
Examples
Embodiment 1
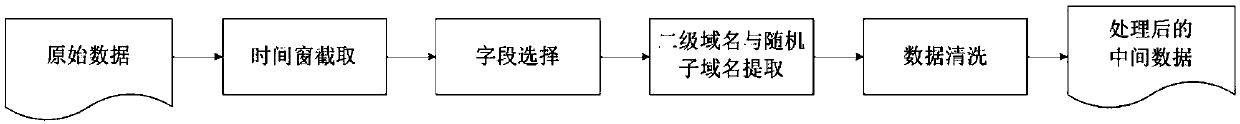
[0065] Embodiment 1. The input data in this embodiment of the present invention comes from DNS data collected by a certain gateway. The data is real data and has been desensitized. The following 10 DNS log records are used for explanation.
[0066] The data after field extraction is:
[0067]
[0068]
[0069] After data preprocessing, filtering data, parsing and extracting the second-level domain name of the domain name, it is converted into a key-value pair data format, and the data is:
[0070]
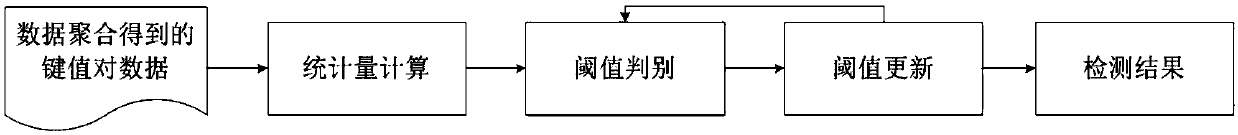
[0071] Perform data aggregation steps on the preprocessed data:
[0072]
[0073]
[0074] After the data aggregation is completed, the statistics calculation step is performed, and the following results are obtained:
[0075]
[0076] Then perform threshold discrimination. From the above example, it can be seen that the selected two statistical features have a strong distinction between attack traffic and normal traffic. In the above example, it is assumed that ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com