Secure revocable multi-center large attribute domain attribute-based encryption method in fog computing
An attribute-based encryption and fog computing technology, applied in computer security devices, computing, instruments, etc., can solve problems such as reducing fog efficiency and increasing equipment energy consumption, achieving security against selected ciphertext attacks, flexible and fine-grained access control , to achieve the effect of efficient cancellation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
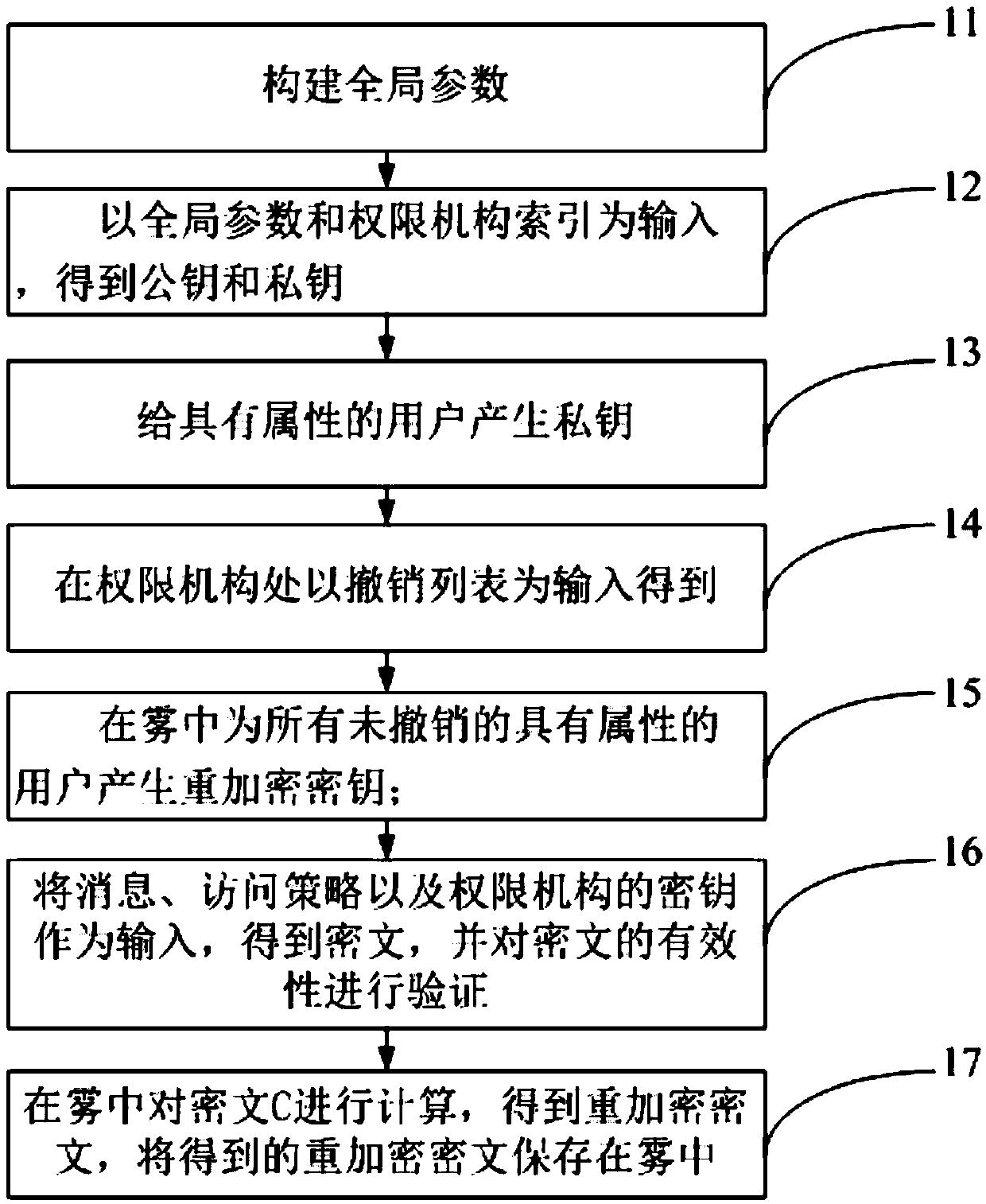
[0029] The present invention provides a secure revocable multi-center large-attribute domain attribute-based encryption method in fog computing. For the revocable multi-center large-attribute domain CP-ABE, it defines the impossibility of permission selection, access strategy and static adaptive selected ciphertext attack. Differentiation (IND-sAA-sCCA2). Use Π={GSetup, ASetup, KeyUp, KeyUp, RKGen, Enc, ReEnc, Dec} to represent this system.
[0030] In this security model, the attacker can query the secret key associated with any access policy and the decryption of any ciphertext it chooses, but it cannot query the decryption of the challenge code if it queries the secret key associated with its specific access policy. key, it can only do this in Phase 1, and must immediately revoke one of its selected properties.
[0031] Such as figure 1 As shown, the attribute-based encryption method includes:
[0032] 11. Construct the global parameter Param;
[0033] 12. Take the glob...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com