A Quorum Searchable Encryption Method
An encryption method and indexing technology, which is applied in the fields of secure data storage and information search, can solve the problems of not considering data encryption, not considering outsourcing decryption, and aggravating the computing tasks of data owners.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0109] Hereinafter, the preferred embodiments of the present invention will be described in detail with reference to the accompanying drawings.
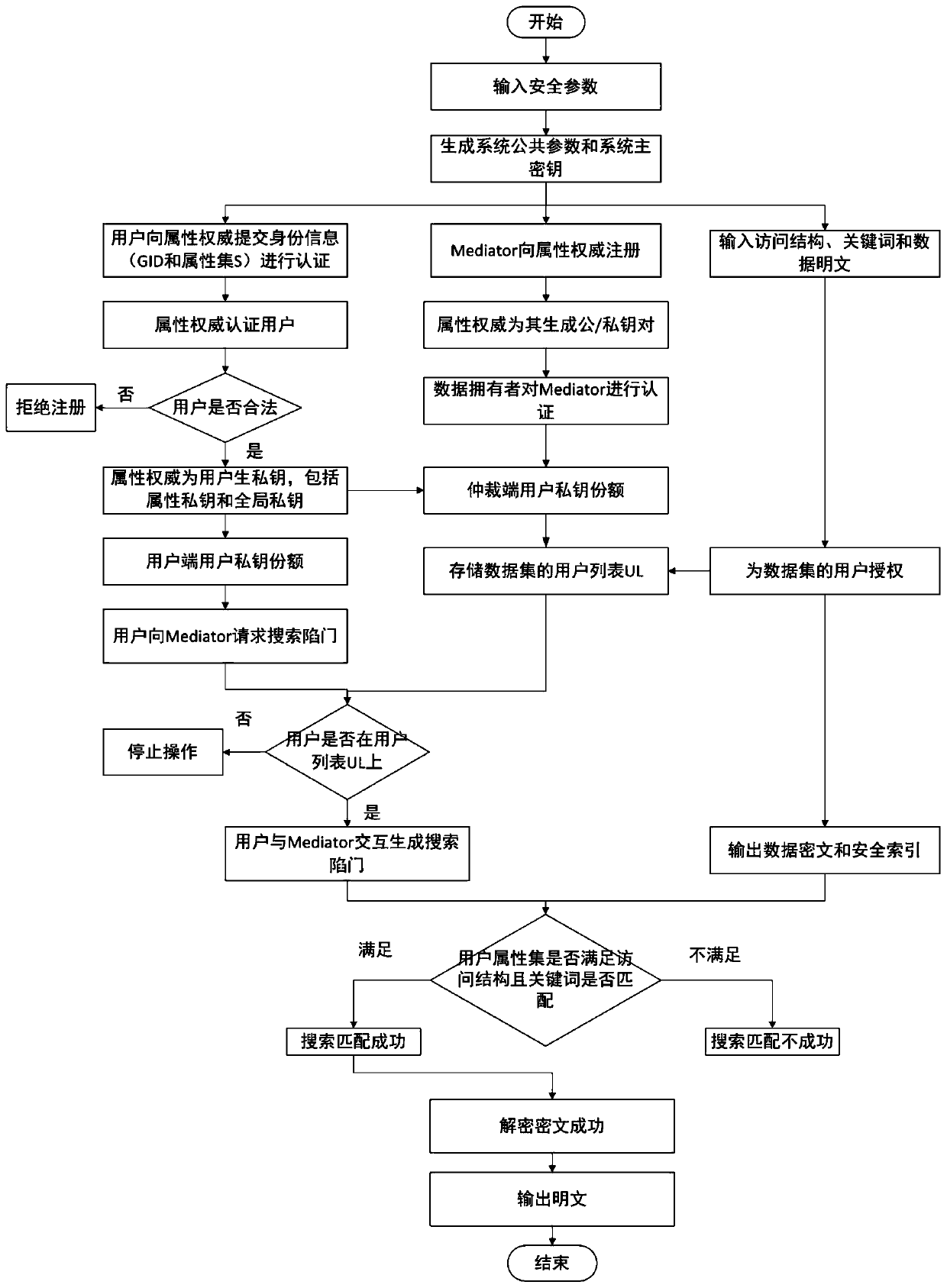
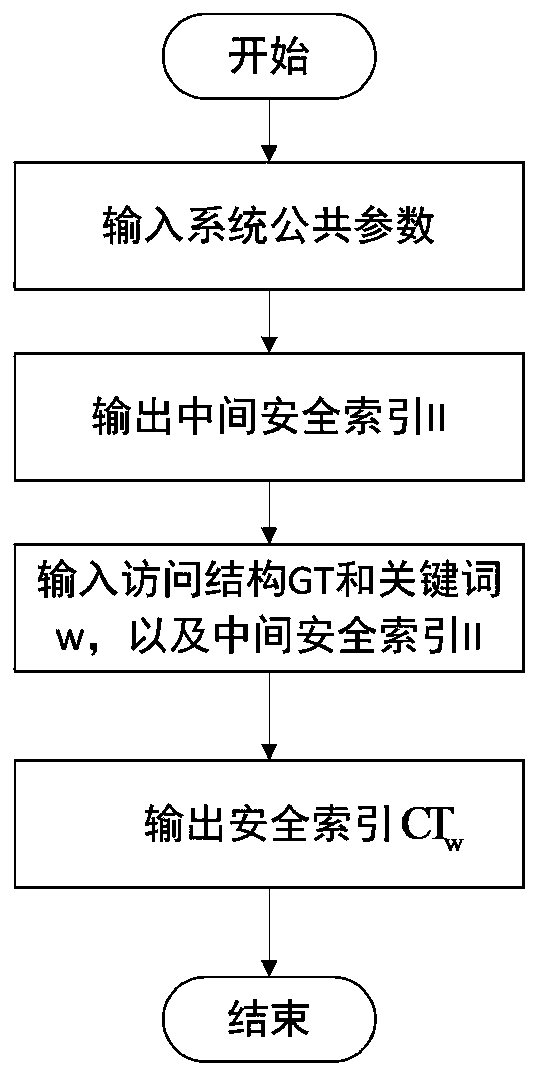
[0110] The online and offline searchable encryption mechanism based on arbitration attributes provided by the present invention includes the following steps, see figure 1 :
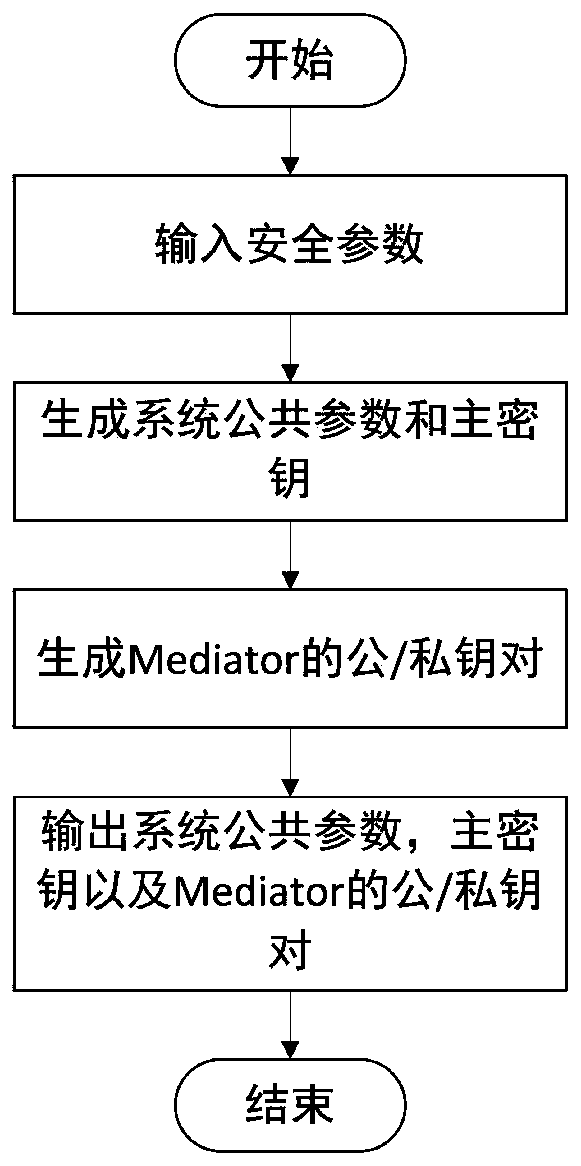
[0111] S1: System initialization, generating system public parameters (including public / private key pairs for each attribute) and Mediator public / private key pairs, see figure 2 ;
[0112] Further, the step S1 includes the following steps:
[0113] S11: System initialization, input security parameter λ, generate system public parameters, system master key, where system public parameters include two bilinear groups G and G of order p T , The generator g in G and the bilinear mapping e: G×G→G T , Hash function H: {0,1} * →Z p , And the public / private key pair of each attribute, let i denote the attribute, and choose a random number t 1 ,...,t 3n ∈ Z p , Calculate Where ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com