Safety education application method and system
An application method and safe technology, applied in the field of communication, can solve problems such as large safety hazards and difficult management after school, so as to improve management level, reduce the probability of encountering dangerous situations, and improve management efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
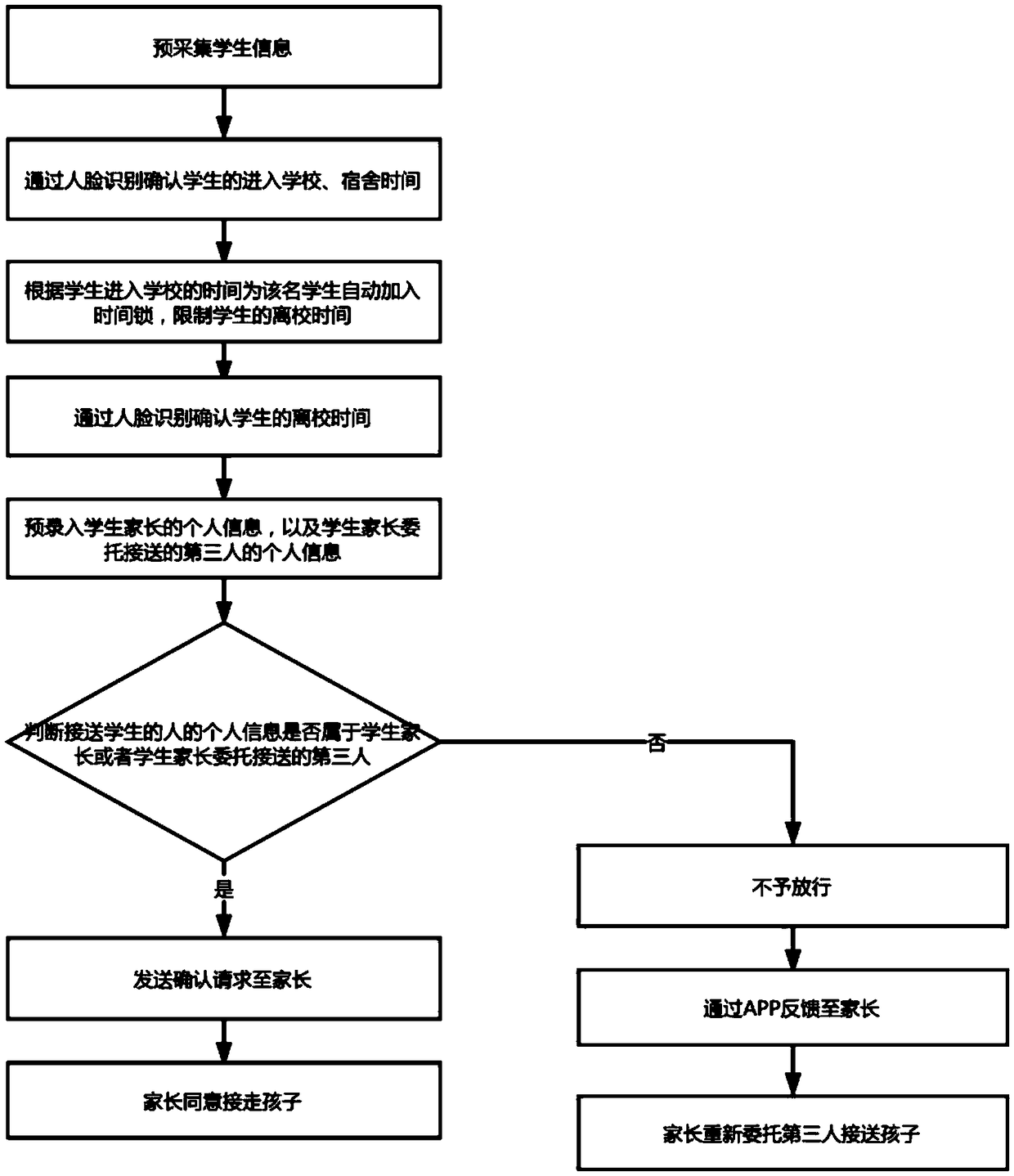
[0033] A safety education application method disclosed in this embodiment is applied to a face recognition access control system installed in a school. The hardware devices used in the access control system include but are not limited to cameras, servers, mobile phones, tablet computers, personal computers, smart bracelets, For smart wearable devices, the software used includes but is not limited to mobile APPs applied to personal mobile phones and tablet computers, and software installed on personal computers and servers. For the convenience of description, this embodiment is described for the server side, see figure 1 , including the following steps:
[0034] S1 The server side pre-collects student information. The student information should at least include face information and fingerprint information. When collecting face information, a camera can be used to collect face images in advance; the collected content should at least include student identity information. Collect...
Embodiment 2
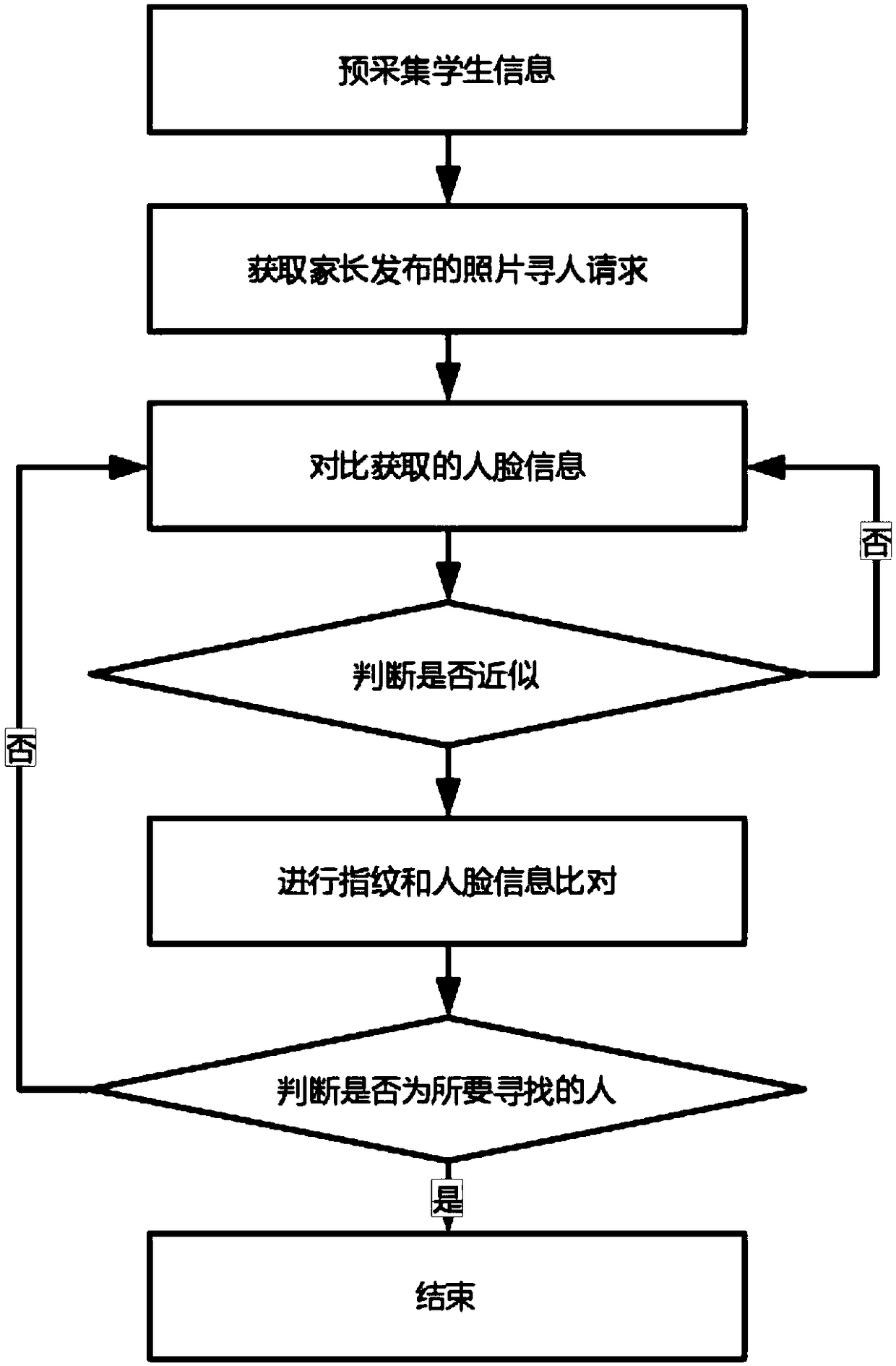
[0045] See figure 2 , the technical solution of this embodiment is basically the same as the technical solution of embodiment 1, the only difference is that the student information starts to be collected when the student is an infant, and once lost or unable to be contacted, the server can obtain the photos posted by the parents For a person-finding request, the server performs a similar comparison based on the image information collected by the camera. When a person similar to the photo is found, the fingerprint and face information are compared through the platform or the public security data center to determine whether it is the person you are looking for. If the result is yes, it is confirmed that the search is successful; if the judgment result is no, then search again.
Embodiment 3
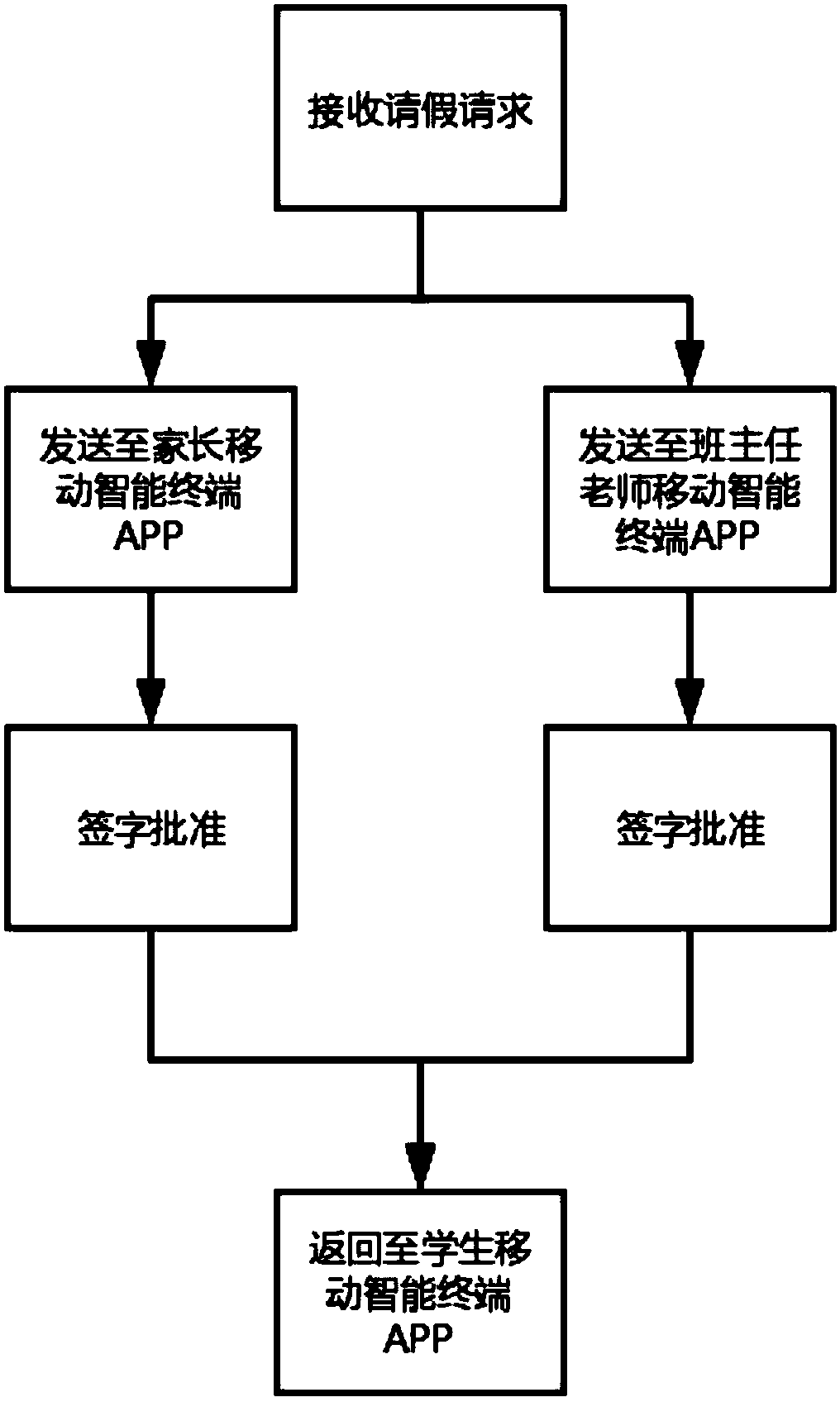
[0047] See image 3 , the technical solution of this embodiment is basically the same as the technical solution of embodiment 1, the only difference is that this embodiment adds a student leave process, which specifically includes the following types:
[0048] Type 1 students ask for leave during school, and students have mobile smart terminals
[0049] If a student needs to ask for leave to go out during the school period, for students with a mobile smart terminal, write a leave request through the mobile smart terminal APP, and the mobile smart terminal APP will send the student's leave request to the head teacher, and the leave request will also be sent to the student synchronously Parents, parents of students can approve or deny the student's leave request through one or more methods including remote electronic signature and fingerprint signature, and the teacher can also approve the student's leave slip through one or more methods including remote electronic signature and...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com