Semi-quantum secure direct communication protocol based on Bell state
A secure direct communication, semi-quantum technology, applied in the field of semi-quantum secure direct communication methods and systems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
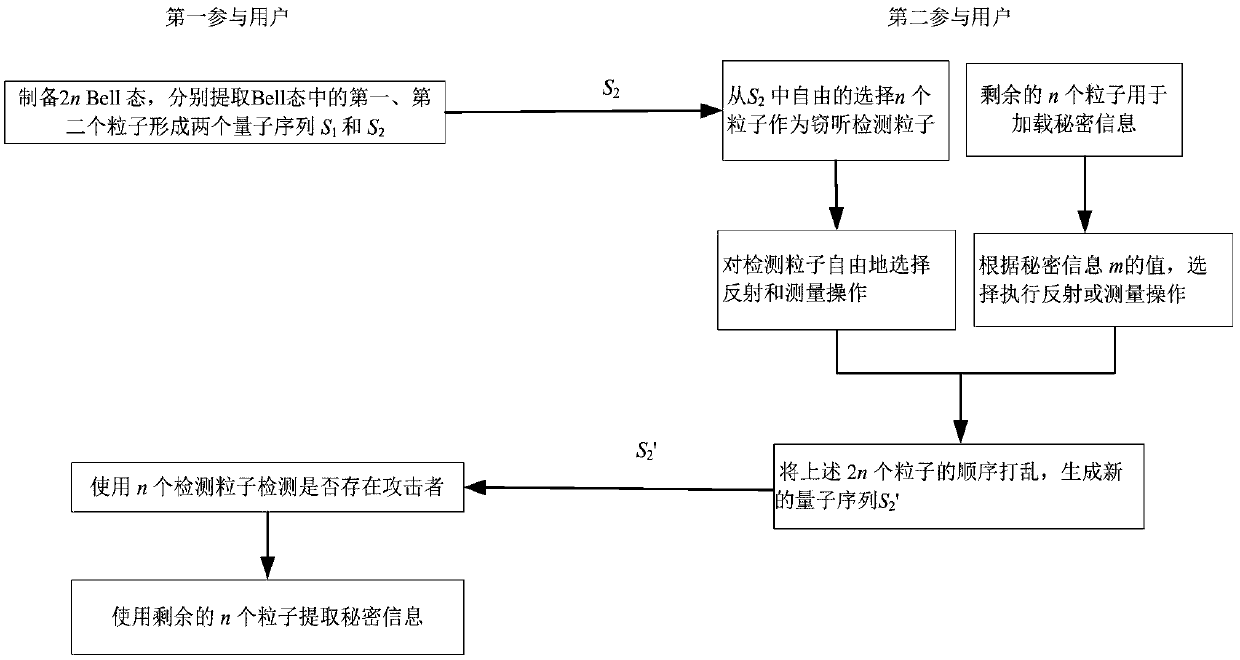
[0091] See figure 1 , this embodiment includes a first participating user with strong quantum functions and a second participating user with only basic quantum functions, and the second participating user needs to transmit secret information to the first participating user;
[0092] The first participating user Alice prepares 2n Bell states, extracts one particle in each Bell state to form a particle sequence and sends it to the second participating user Bob; after receiving the quantum, the second participating user Bob, who has basic quantum functions, randomly selects n among them n particles are used as detection particles to detect external eavesdroppers; the other n particles are used to load secret information; the second participating user performs random operations on the detection particles and uses the remaining particles to encode secret information; the second participating user performs a random operation on the generated particles Sequence, processed out of ord...
Embodiment 2
[0094] See figure 2 , the usage method of Embodiment 1, the quantum communication volume required for the protocol to realize the transmission of secret information, and compare it with related work;
Embodiment 3
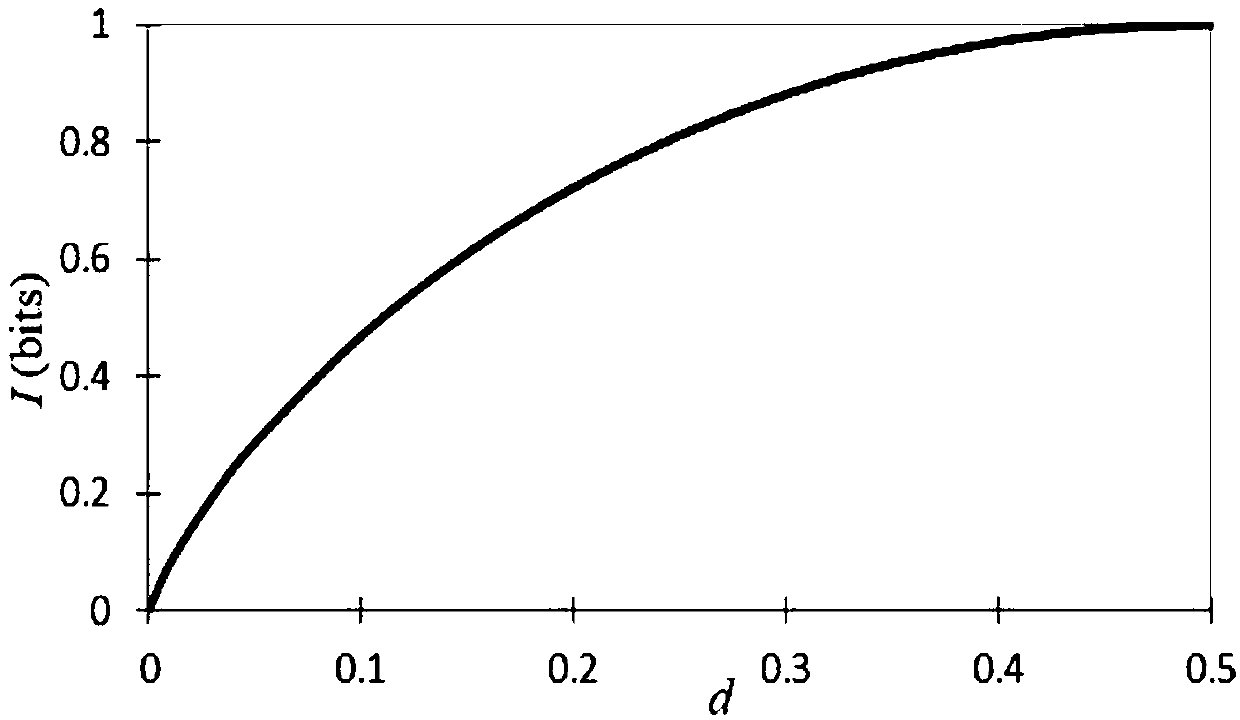
[0096] See image 3 , using the method of embodiment 1, if the attacker wants to obtain complete information, the probability of being detected is 50%;
[0097] The present invention needs to be executed in a quantum communication network environment, so the participating computers have quantum functions, and a quantum network is required for transmission;
[0098] In the above-mentioned embodiments, it can be realized in whole or in part by software, hardware, firmware or any combination thereof; when using a computer program product in whole or in part, the computer program product includes one or more ; When loading or executing the computer program instructions on the computer, all or part of the processes or functions according to the embodiments of the present invention are generated; the computer needs to be equipped with a quantum device; the computer instructions can be stored in a computer-readable storage media, or transmitted from one computer-readable storage med...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com