DDOS (Distributed Denial of Service) effect evaluation method based on BP (Back Propagation) neural network
A BP neural network and DDOS technology, applied in biological neural network models, data exchange networks, digital transmission systems, etc., can solve the problem of low evaluation accuracy and achieve accurate evaluation results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
[0025] Specific implementation mode one: the specific process of a kind of DDOS effect evaluation method based on BP neural network in this embodiment mode is:
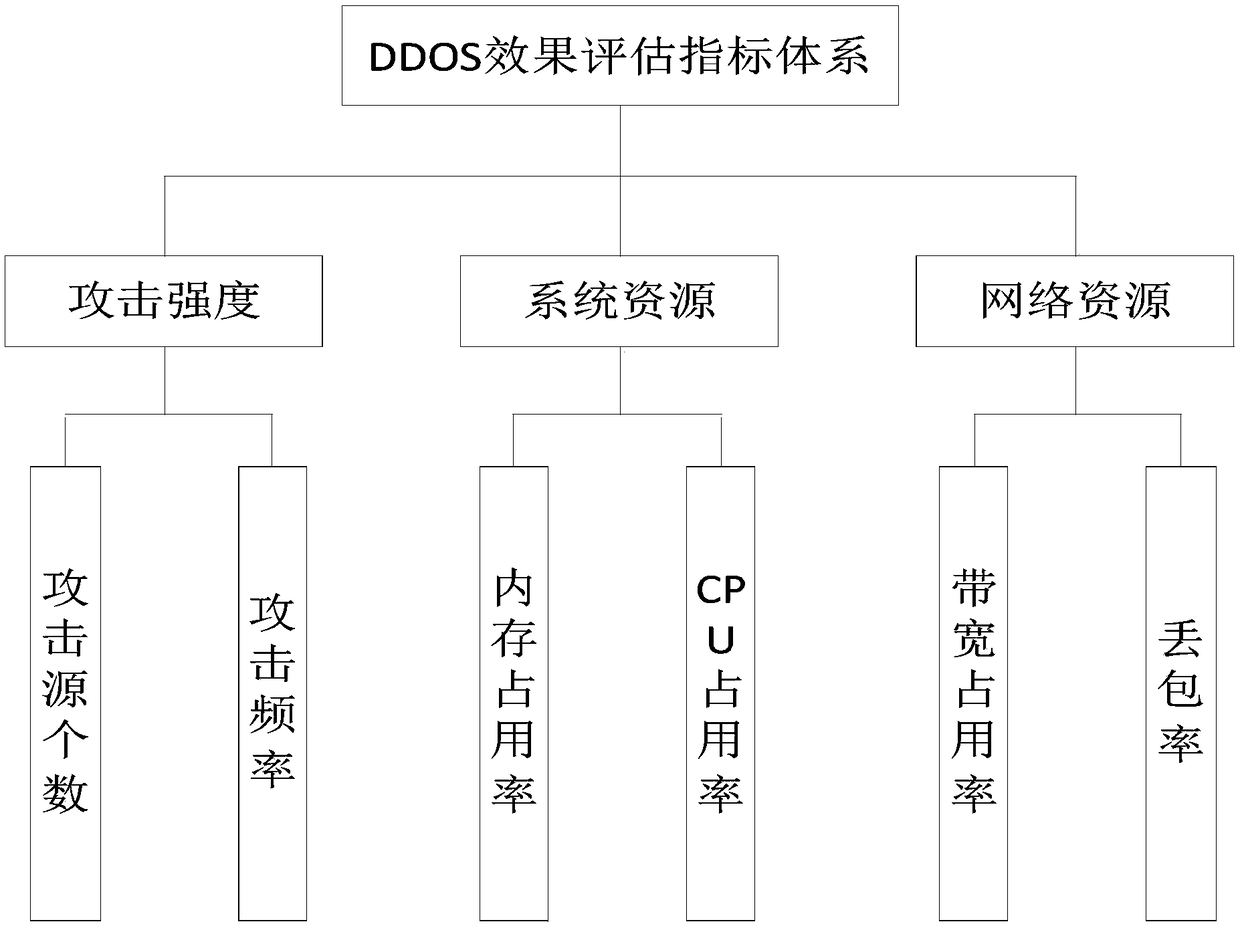
[0026] Step 1. Establish a DDOS effect evaluation index system;
[0027] The DDOS effect evaluation index system includes attack strength, system resources and network resources;
[0028] Attack intensity includes the number of attack sources of DDOS attack aircraft and the attack frequency (attack interval time) of DDOS attack aircraft;
[0029] System resources include the memory usage of the destination host and the CPU usage of the destination host;
[0030] Network resources include bandwidth occupancy rate and packet loss rate;
[0031] In view of the diversified characteristics of the factors involved in the evaluation of denial of service attack effects, and each factor has different impacts on the attack and defense effects at different levels and dimensions, it is necessary to deeply study the characterist...
specific Embodiment approach 2
[0054] Specific implementation mode two: the difference between this implementation mode and specific implementation mode one is: the specific establishment process of the cloud environment is:
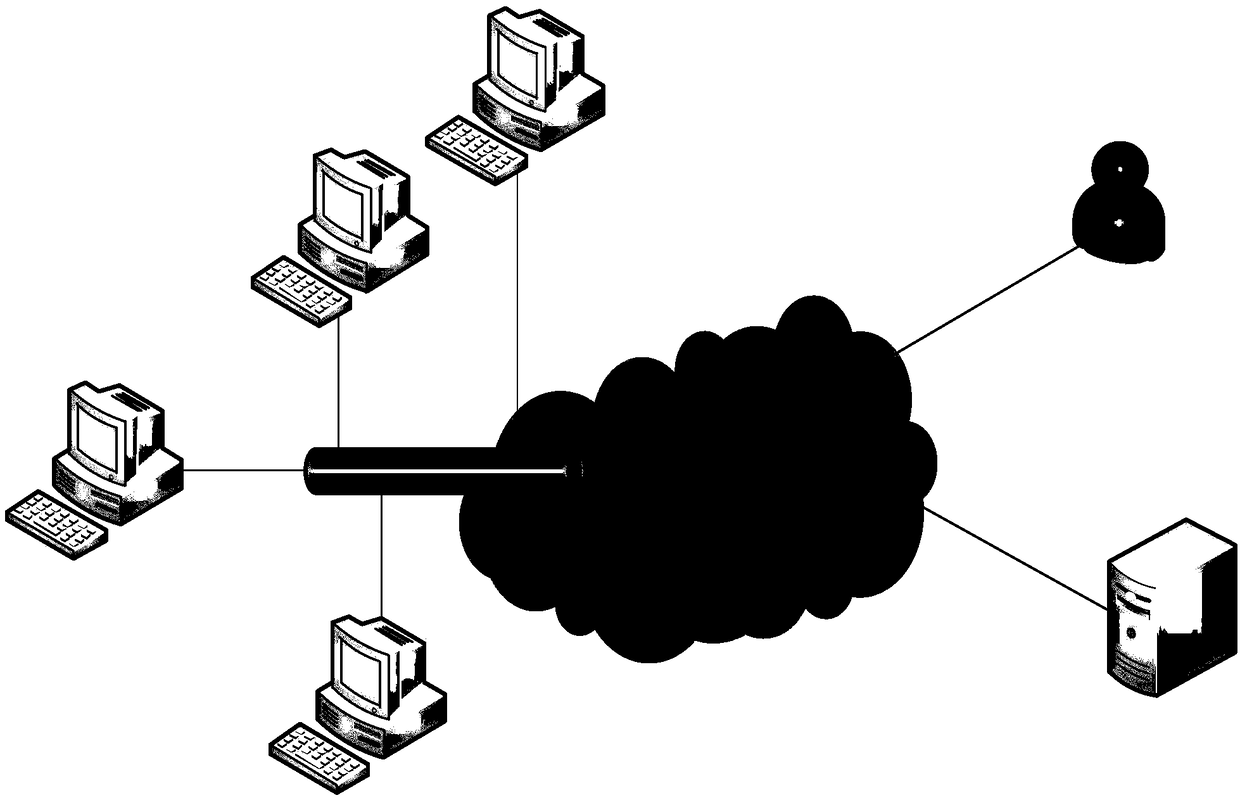
[0055] Experimental simulation network topology such as figure 2 , first build a simple cloud environment, the cloud environment is composed of three physical servers, a virtual network is established on the three physical servers, the topology of the virtual network is composed of three parts, namely N DDOS attack machines and a user virtual machine , a destination host;
[0056] The value of N is a positive integer.
[0057] figure 2 All nodes in the network are virtual nodes. The virtual machine cluster on the left side of the network is an attack proxy machine, on which an attack program is deployed for DDOS attacks. The upper right side of the network is a common user virtual machine, on which a service request program is deployed to collect Web The response of the server is...
specific Embodiment approach 3
[0059] Embodiment 3: The difference between this embodiment and Embodiment 1 or 2 is that: the specific process of establishing a virtual network on three physical servers is as follows:
[0060] Create a KVM virtual machine on each physical server and connect to the cloud network to obtain a virtual network.
[0061] Other steps and parameters are the same as those in Embodiment 1 or Embodiment 2.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com