A multi-dimensional state-aware dynamic access control method
A dynamic access control and state-aware technology, applied in the field of cloud computing, can solve problems such as increasing the burden on security management personnel, and achieve the effect of improving access performance, accuracy, and accurate authentication results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0017] In order to make the object, technical solution and advantages of the present invention more clear and definite, the present invention will be further described in detail below with reference to the accompanying drawings and examples. It should be understood that the specific embodiments described here are only used to explain the present invention, not to limit the present invention.
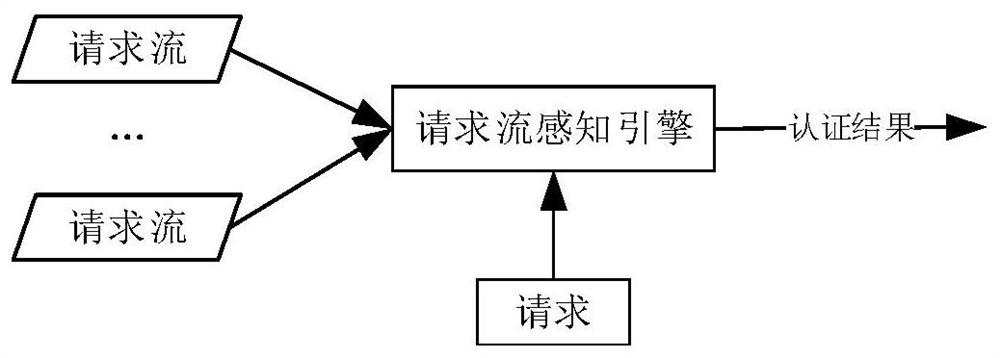
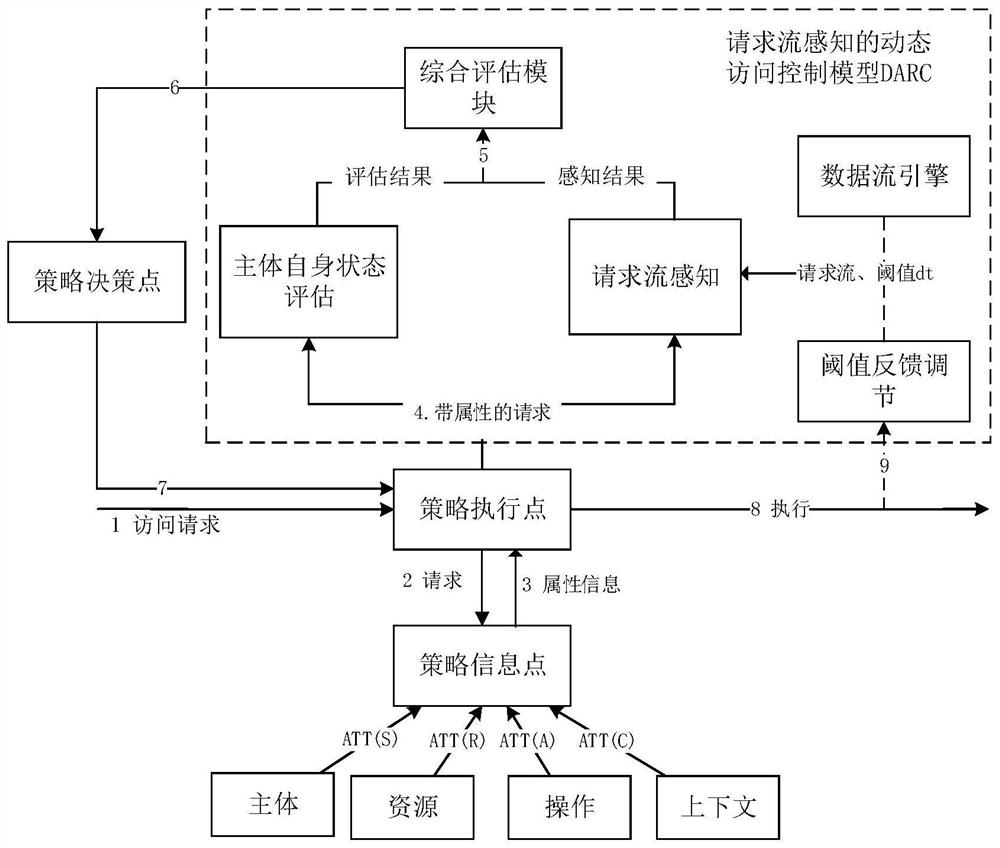
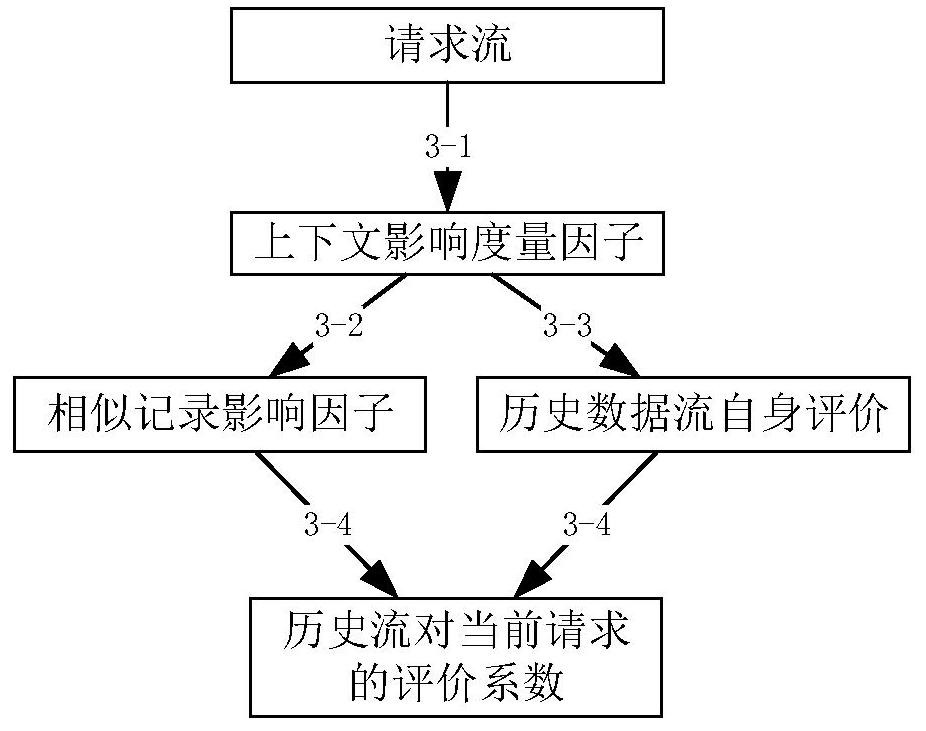
[0018] The invention is an access control method suitable for cloud computing environment. The invention proposes a dynamic access control method with request data flow awareness. The biggest difference from the existing methods is: first, it provides a completely dynamic access control technology, which no longer constrains the formulation of static rules; second, it effectively utilizes the user's historical data and provides a The method of authenticating the current request; the third is to calculate the validity of the historical data nodes, so that the authentication results of th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com