Method, device and system for identifying mobile generators
A generator and technology to be identified, applied in the field of network security, can solve problems such as the inability to determine the vehicle information of a mobile generator
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
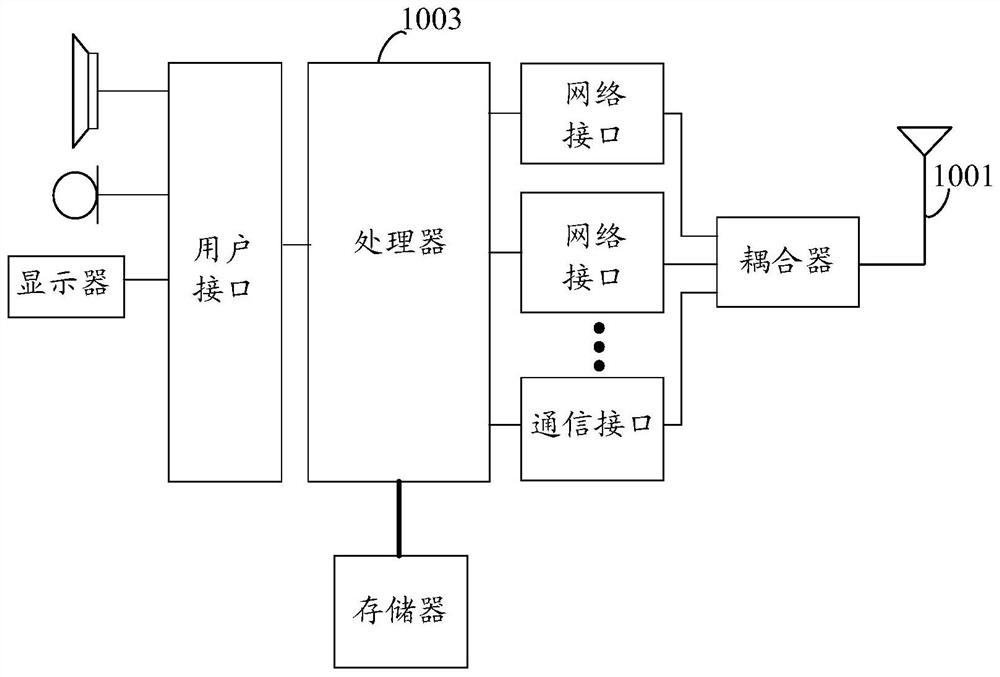
[0048] Before describing further details of the various embodiments of the present application, reference will be made to figure 1 to describe one suitable server that can be used to implement the principles of the present application.
[0049] The server provided by Embodiment 1 of the present application can be widely applied to network security. With the rapid development of modern science and technology, the Internet has been widely used in people's daily life, and people's life, work, and study are inseparable from the Internet. However, it is precisely because of the continuous popularization of Internet technology applications that criminals have begun to spread bad information to people or obtain people’s private information through network channels. After this link, criminals will obtain the user's information, such as the user's bank card password. In order to ensure the safety of people using the network and purify the network environment, it is necessary to funda...
Embodiment 2
[0074] According to an embodiment of the present invention, an embodiment of a method for identifying a mobile generator is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawings can be executed in a computer system such as a set of computer-executable instructions, Also, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
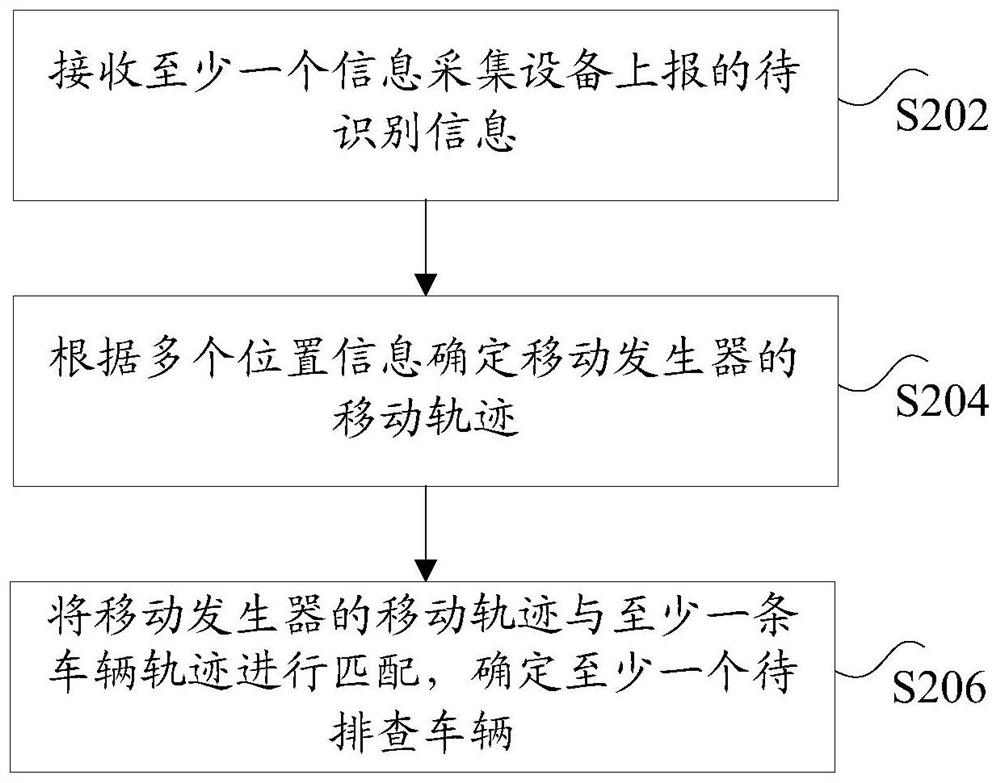
[0075] The present application provides an embodiment of a method for identifying mobile generators, figure 2 is a flowchart of a method for identifying mobile generators according to Embodiment 2 of the present invention, such as figure 2 As shown, the method includes the following steps:
[0076] Step S202, receiving information to be identified reported by at least one information collection device, wherein the information to be identified includes: a plurality of location information, ...
Embodiment 3
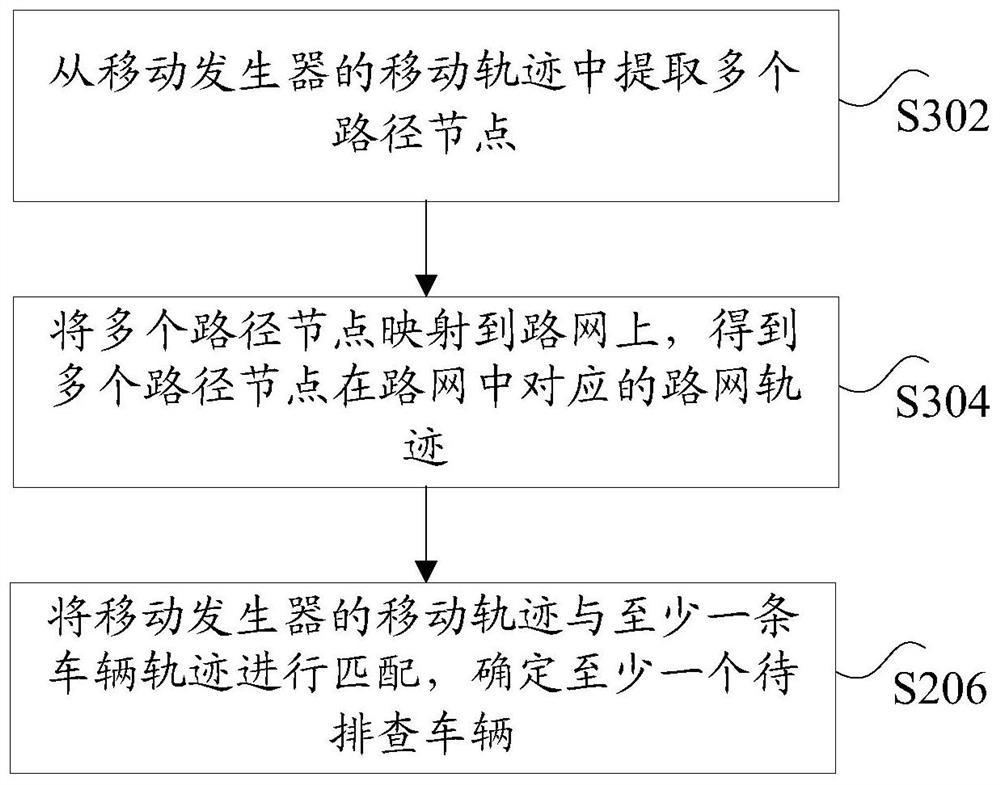
[0132] According to an embodiment of the present invention, a device for identifying a mobile generator for implementing the above method for identifying a mobile generator is also provided, such as Figure 13 A structural schematic diagram of a device for identifying a mobile generator is shown, the device includes: a receiving module 1301 , a determining module 1303 and a matching module 1305 .
[0133] The receiving module 1301 is configured to receive information to be identified reported by at least one information collection device, wherein the information to be identified includes: a plurality of location information, wherein the location information is location information of the information collection device reporting the information to be identified.
[0134] In the above-mentioned receiving module 1301, the above-mentioned at least one information collection device may be, but not limited to, a terminal device or a mobile device that can receive information or signal...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com