Method and system for security management and control of mobile storage device
A mobile storage device, security management and control technology, applied in the direction of internal/peripheral computer component protection, digital data authentication, etc., can solve the problems of mobile storage device abuse, potential safety hazards, mobile storage device infection and computer virus transmission, etc., to achieve structural Simple, safe, easy to use and popularize
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
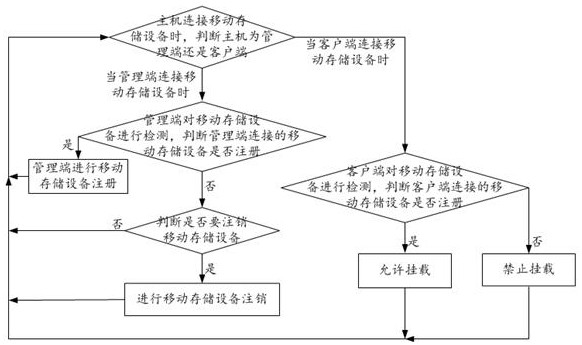
[0102] Example 1 as figure 1 As shown, the present invention provides a mobile storage device security management and control method, including the following steps:
[0103] Step S1. When the host is connected to the mobile storage device, it is determined whether the host is a management terminal or a client;
[0104] Step S2. When the management terminal is connected to the mobile storage device;
[0105] The management terminal detects the mobile storage device, and judges whether the mobile storage device connected to the management terminal is registered;
[0106] Step S3. If not registered, the management terminal registers the mobile storage device; return to step S1;
[0107] Step S4. If it has been registered, it is judged whether to cancel the mobile storage device;
[0108] If so, log out the mobile storage device;
[0109] If not, no operation is performed;
[0110] Return to step S1;
[0111] Step S5. When the client connects to the mobile storage device;
...
Embodiment 2
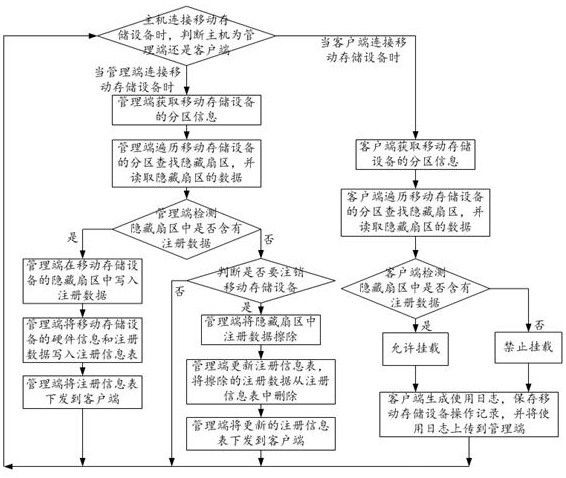
[0117] Example 2 as figure 2 As shown, a mobile storage device security management and control method includes the following steps:
[0118] Step S1. When the host is connected to the mobile storage device, it is determined whether the host is a management terminal or a client;
[0119] Step S2. When the management terminal is connected to the mobile storage device;
[0120] The management terminal detects the mobile storage device, and judges whether the mobile storage device connected to the management terminal is registered;
[0121] Step S21. The management terminal obtains the partition information of the mobile storage device;
[0122] Step S22. The management terminal traverses the partitions of the mobile storage device to find hidden sectors, and reads the data of the hidden sectors;
[0123] Step S23. The management terminal detects whether the hidden sector contains registration data;
[0124] Step S231. The management terminal traverses the hidden sectors of t...
Embodiment 3
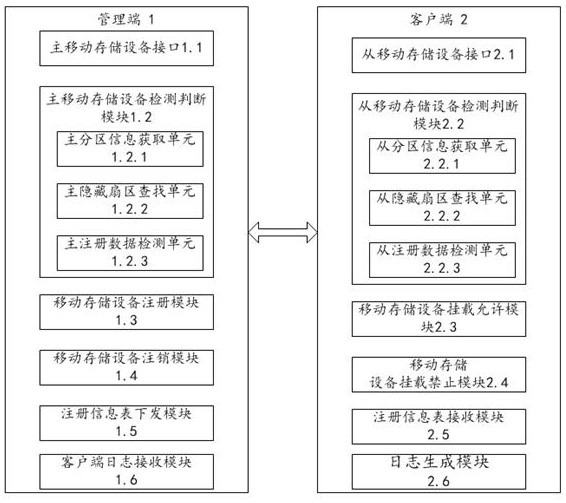
[0155] Example 3 as image 3 As shown, a mobile storage device security management and control system includes a management terminal 1 and a client 2, and the management terminal 1 is connected to the client 2;
[0156] The management terminal 1 includes a main mobile storage device interface 1.1, a main mobile storage device detection and judgment module 1.2, a mobile storage device registration module 1.3, a mobile storage device cancellation module 1.4, a registration information table issuing module 1.5 and a client log receiving module 1.6 ;
[0157] The main mobile storage device interface 1.1 is used to connect the management terminal to the mobile storage device;
[0158] The main mobile storage device detection and judgment module 1.2 is used for the management terminal to detect the mobile storage device and judge whether the mobile storage device connected to the management terminal is registered;
[0159] The mobile storage device registration module 1.3 is used ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com