Terminal device trusted verification method and device, and terminal device
A technology of terminal equipment and authentication method, applied in secure communication devices, user identity/authority verification, digital transmission systems, etc., can solve the problems of low practicability and high cost, and achieve the effect of saving costs, improving efficiency and practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
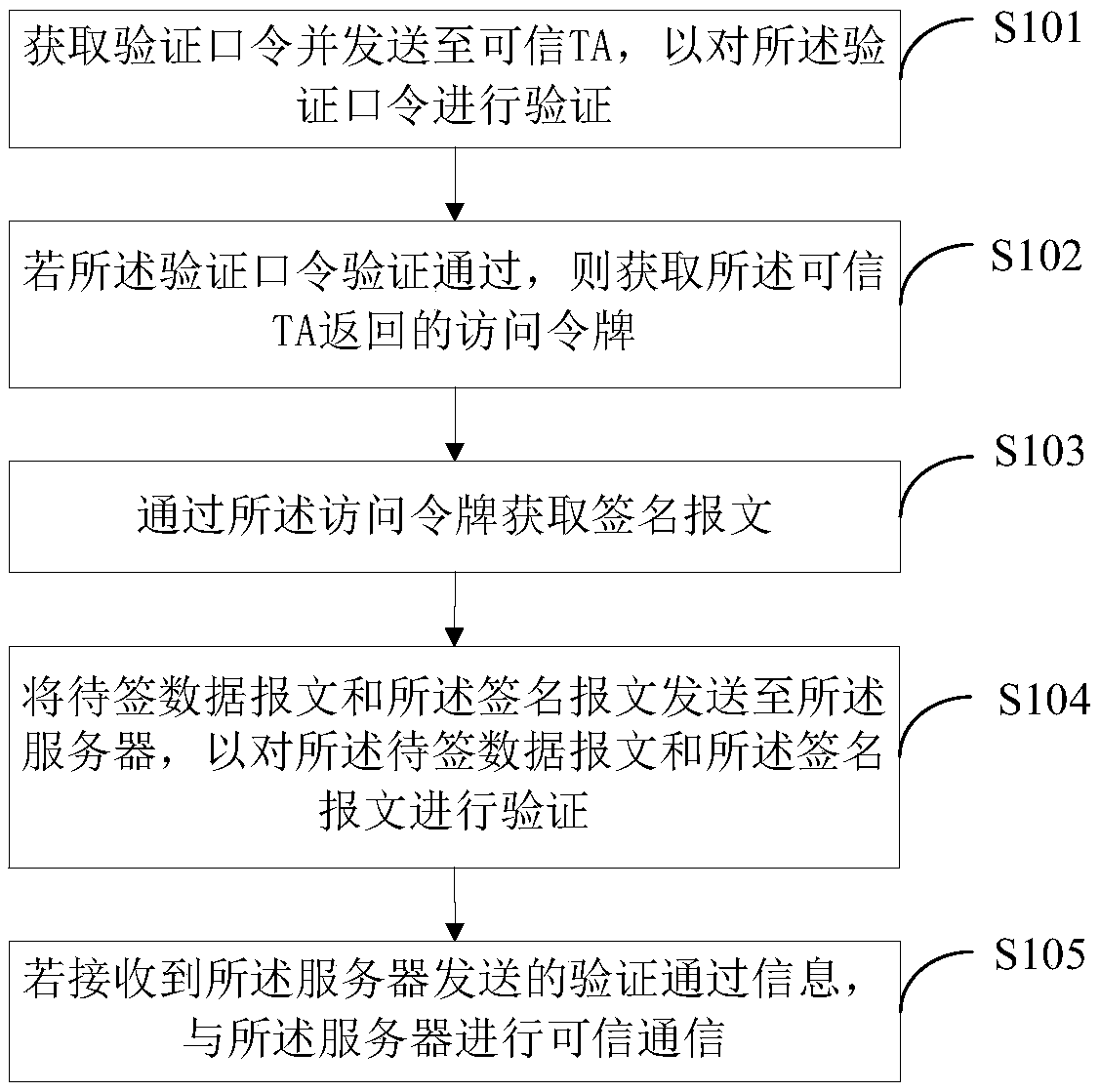
[0038] Such as figure 1 As shown, this embodiment provides a trusted authentication method for a terminal device, and the method can be applied to a terminal device using a rich operating system (Rich OS), such as a mobile phone, a PC, and a tablet computer. The trusted authentication method for terminal equipment provided in this embodiment includes:
[0039] S101. Obtain a verification password and send it to a trusted TA, so as to verify the verification password.
[0040] In a specific application, the verification password input by the user is obtained, and sent to the trusted TA in the TEE trusted execution environment for verification of the verification password.
[0041] S102. If the verification password is verified successfully, obtain the access token returned by the trusted TA.
[0042] In a specific application, if the above-mentioned verification password is verified, the user has a legal identity (the server will authorize legal access to the user), that is, ...
Embodiment 2
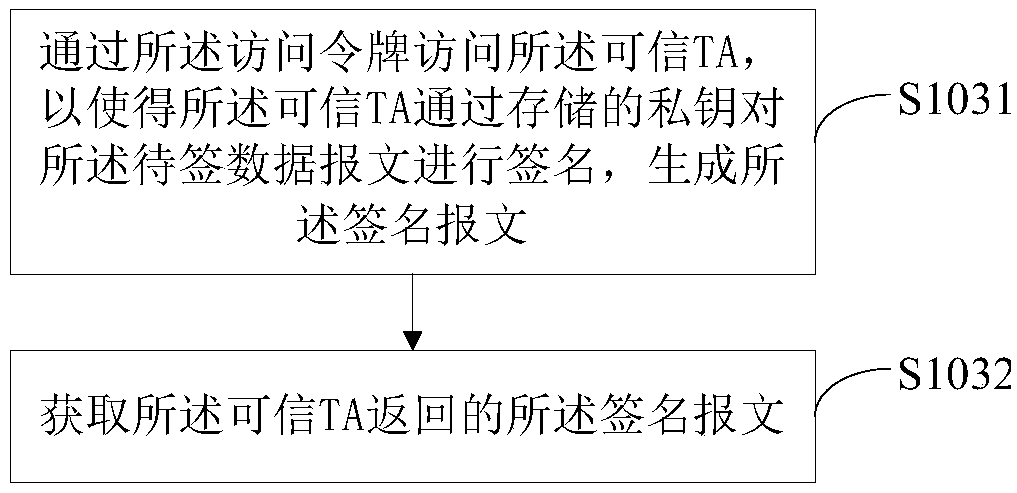
[0055] Such as figure 2 As shown, this embodiment is a further description of the method steps in the first embodiment. In this embodiment, the third acquisition module 103 includes:
[0056] S1031. Access the trusted TA through the access token, so that the trusted TA signs the data message to be signed by using the stored private key to generate the signed message.
[0057] In a specific application, the trusted TA provided for signature calculation in the TEE trusted operating environment is accessed through the above-mentioned access token and the data message to be signed, so that the trusted TA can sign the data message to be signed with its stored private key, Generate a signed message.
[0058] S1032. Obtain the signed message returned by the trusted TA.
[0059] In a specific application, the signed message returned by the above-mentioned trusted TA is obtained, and sent to the server for verification.
[0060] In one embodiment, step S104 includes:
[0061] Sen...
Embodiment 3
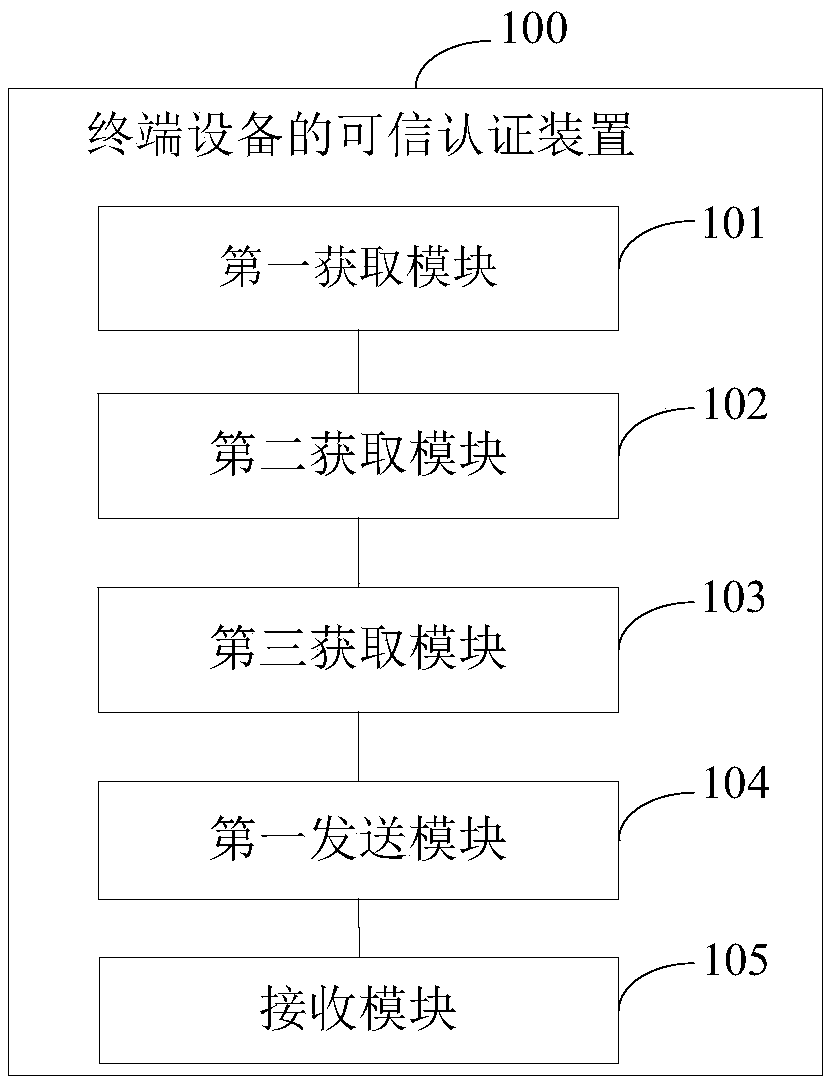
[0065] Such as image 3 As shown, this embodiment provides a trusted authentication apparatus 100 for terminal equipment, which is used to execute the method steps in Embodiment 1. The trusted authentication device 100 for terminal equipment provided in this embodiment includes:
[0066] The first acquiring module 101 is configured to acquire a verification password and send it to a trusted TA to verify the verification password;
[0067] The second obtaining module 102 is configured to obtain the access token returned by the trusted TA if the verification password is verified;
[0068] A third obtaining module 103, configured to obtain a signed message through the access token;
[0069] The first sending module 104 is configured to send the data message to be signed and the signed message to the server, so as to verify the data message to be signed and the signed message;
[0070] The receiving module 105 is configured to perform credible communication with the server if t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com