Multi-diffusion image encryption and decryption method based on chaotic segmentation
An encryption and decryption and chaotic technology, applied in the field of multi-diffusion image encryption and decryption, can solve problems such as hidden dangers of multimedia data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
specific Embodiment approach 1
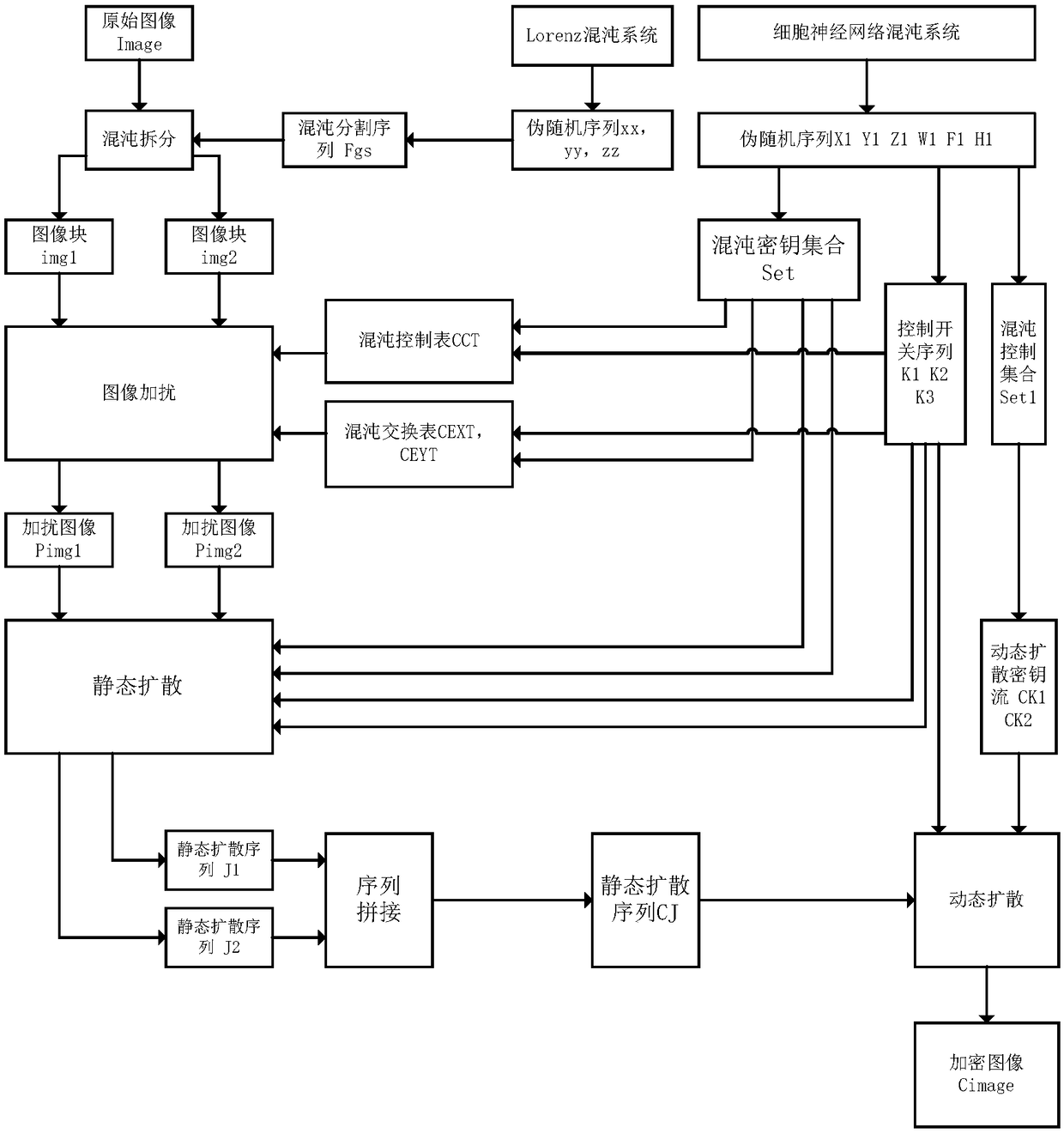
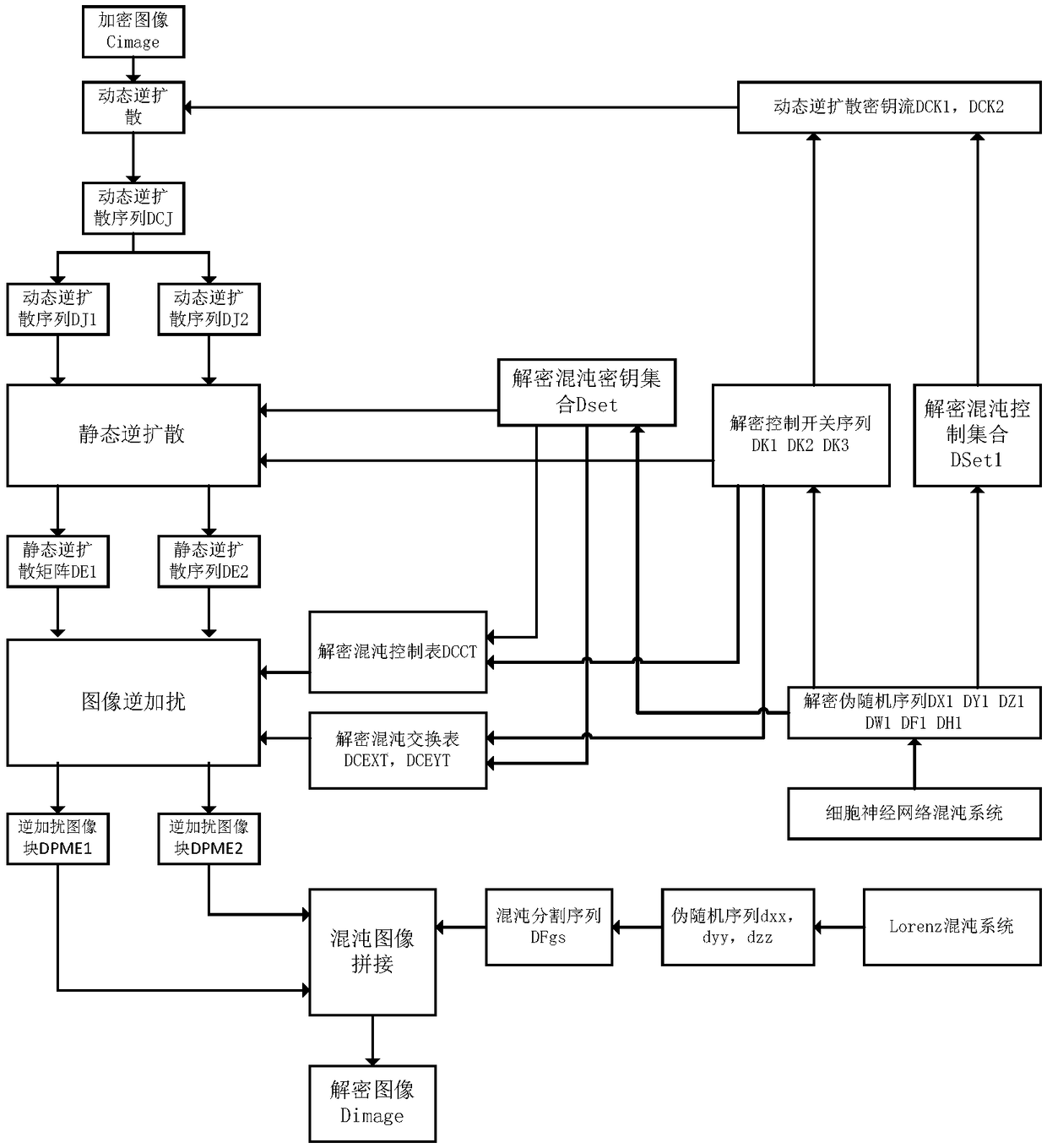
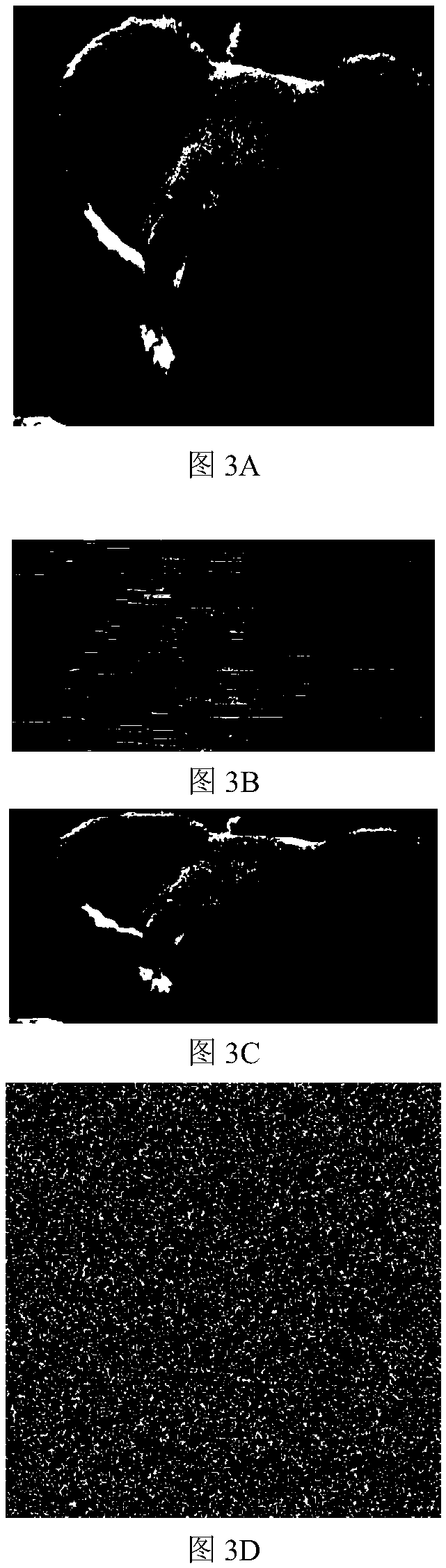
[0080] Specific implementation mode 1. Combination Figure 1 to Figure 4 Illustrate this embodiment, based on the multi-diffusion image encryption and decryption method of chaotic segmentation, comprise image encryption process and image decryption process, it is characterized in that, encryption process and decryption process are realized by the following steps:
[0081] Set the user's encryption key as: the initial value of the cellular neural network and the number of iterations, and the control parameter ku of the chaotic key matrix 1 , ku 2 , the control parameter ku of the chaos control matrix 3 , ku 4 , the control parameter ku of the chaos control table 5 , the control parameter ku of the chaotic exchange table 6 , the control parameter ku of the chaotic dynamic diffusion key stream 7 , ku 8 , the dynamic encryption control parameter ku 9 ;
[0082] The image encryption process is:
[0083] Step 1. Take the "koala" image with a size of 256×256 as the original ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com