A malicious URL detection system and method based on automatic feature extraction
A feature extraction and detection system technology, applied in transmission systems, special data processing applications, instruments, etc., can solve problems such as the lack of popular URL detection software, improve the scope of application and accuracy, avoid manual errors, and improve adaptability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0041] Hereinafter, a number of preferred embodiments of the present invention will be introduced with reference to the accompanying drawings in the specification to make the technical content clearer and easier to understand. The present invention can be embodied by many different forms of embodiments, and the protection scope of the present invention is not limited to the embodiments mentioned in the text.
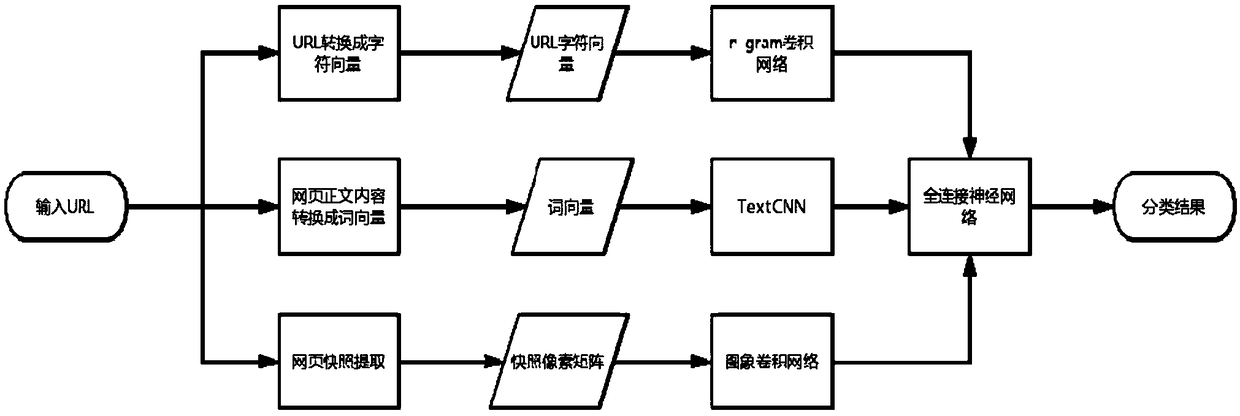
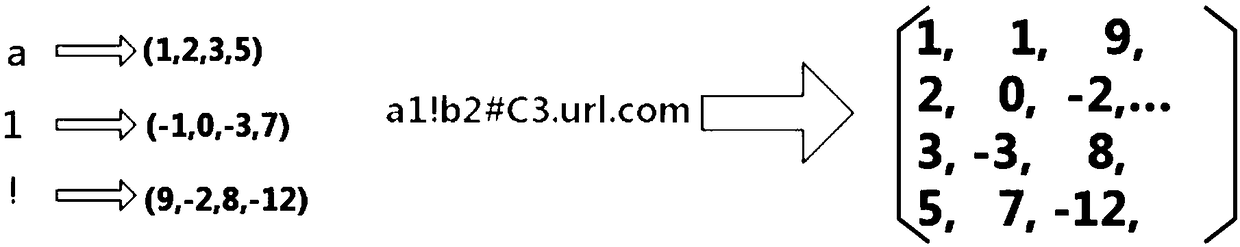
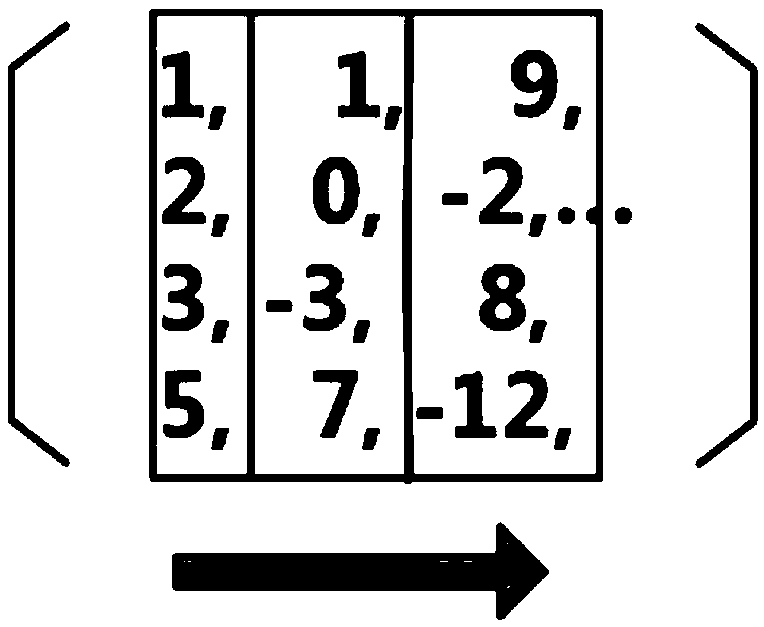
[0042] figure 1 It shows a schematic structural diagram of a malicious URL detection system based on automatic feature extraction in an embodiment of the present invention. This embodiment provides a malicious URL detection system based on automatic feature extraction. The system is composed of a preprocessing module, a parallel learning module, and a detection classification module. For the input URL, the system will determine whether it is a malicious URL and give Its category. In the present invention, the preprocessing module converts different types of data sources su...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com