Mthod for verifying the login of BIOS user through mobile phone two-dimensional code
A technology of two-dimensional codes and mobile phones, applied in the field of BIOS security, can solve troubles and other problems, and achieve the effect of a wide range of applicable environments
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
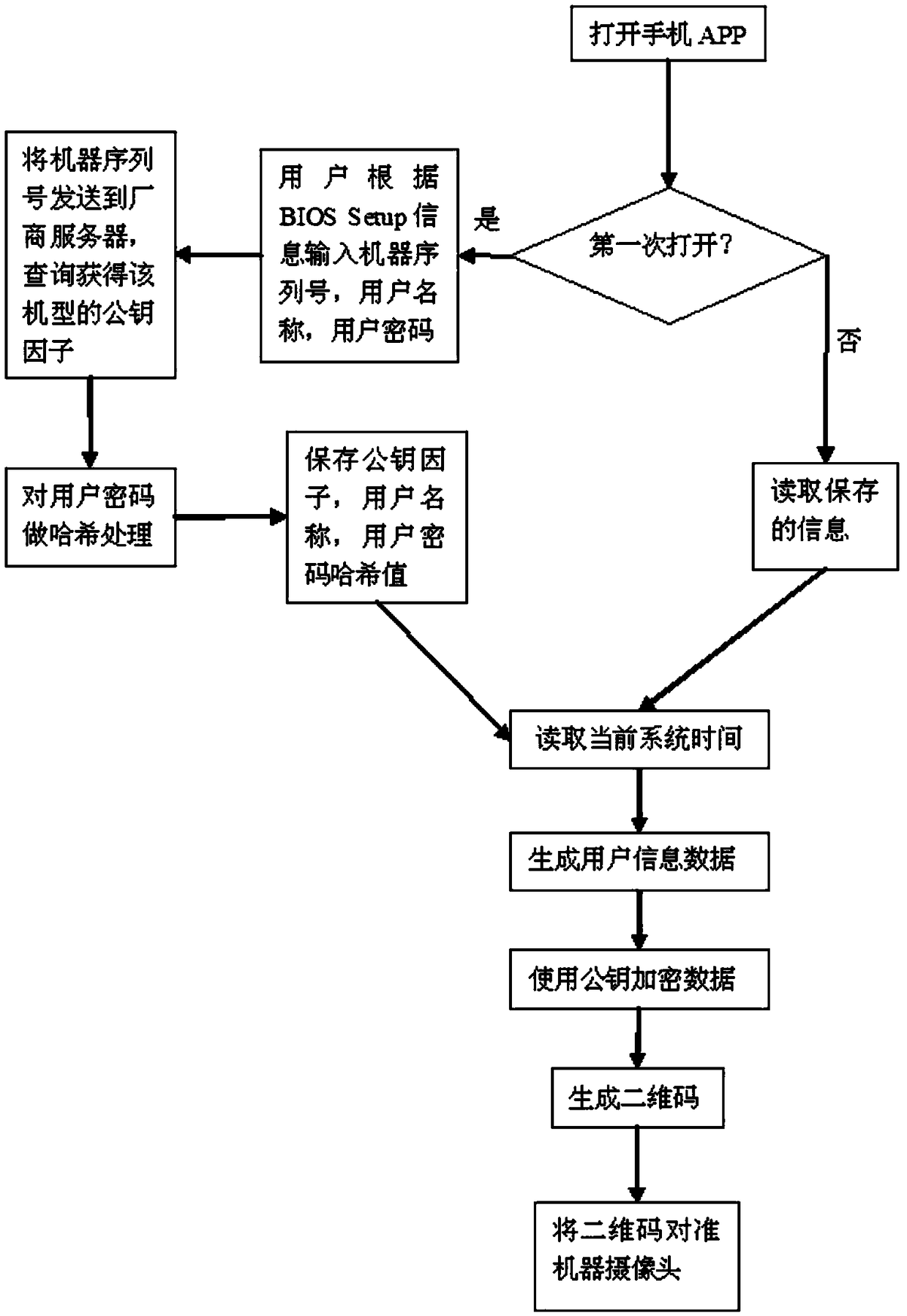
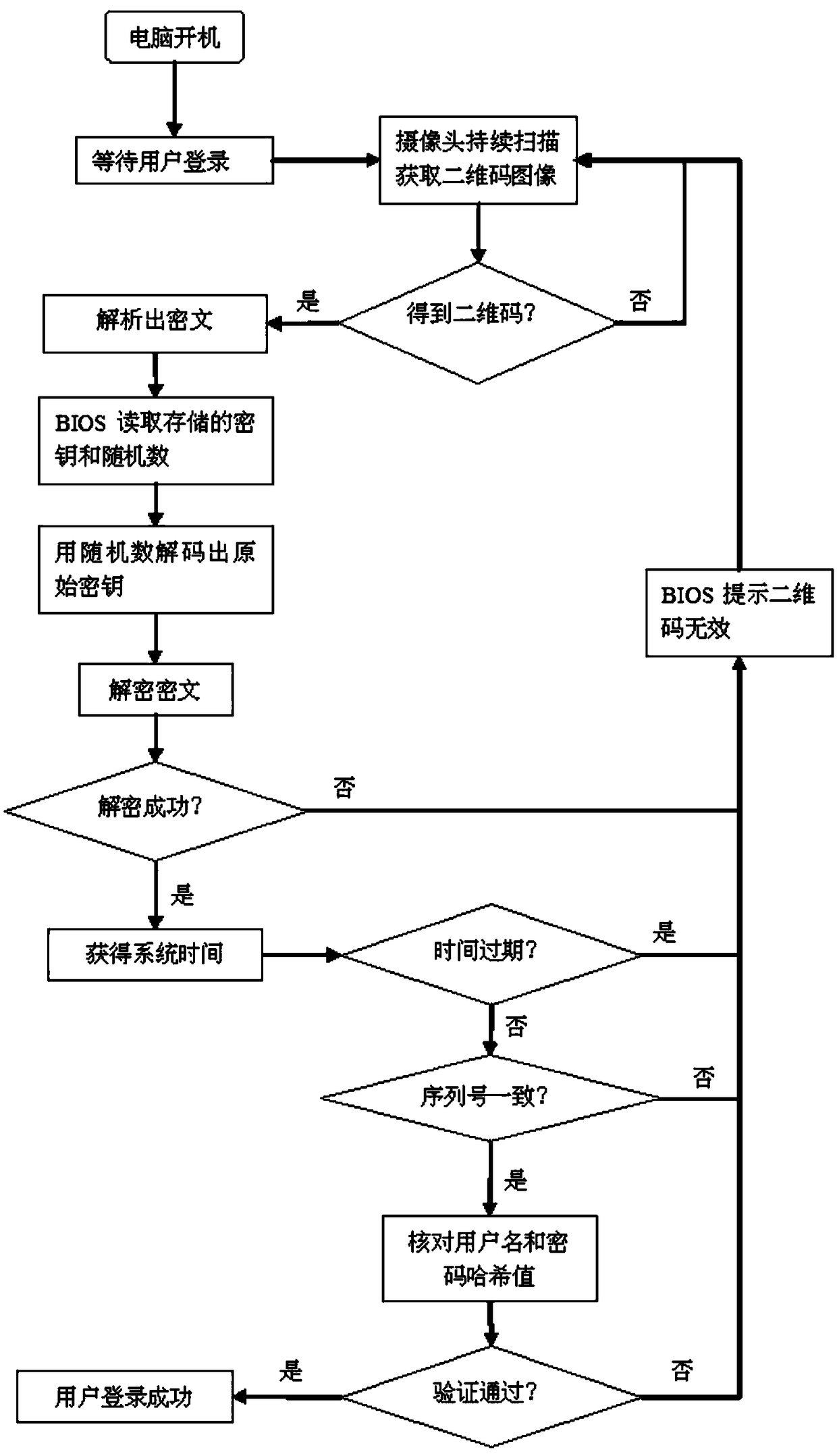
[0026] Such as figure 2 As shown, a method for verifying BIOS user login through a mobile phone two-dimensional code includes the following steps:
[0027] (1) The operation library for camera driver and analysis of two-dimensional code images is added to the BIOS program;
[0028] (2) Use the open source tool openssl to generate a pair of asymmetric encryption and decryption passwords. Using the RSA2048 algorithm, the generated key contains three factors: N, e, d, where N and e are public keys that can be known by others, and N and d are private keys that need to be kept properly and cannot be known by others. The private key is put into the BIOS storage space and protected to a certain extent. Use mathematical XOR operation (XOR) to protect the key. First, use a tool to generate a string of random numbers and store them. Before putting the key into the BIOS, use the random number to perform an XOR operation on the key, so that the key will not will appear in plaintext. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com