Electronic device based security management background
An electronic device, security technology, applied in the direction of security devices, electrical digital data processing, computer security devices, etc., can solve the problem that users cannot access the device as a whole
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
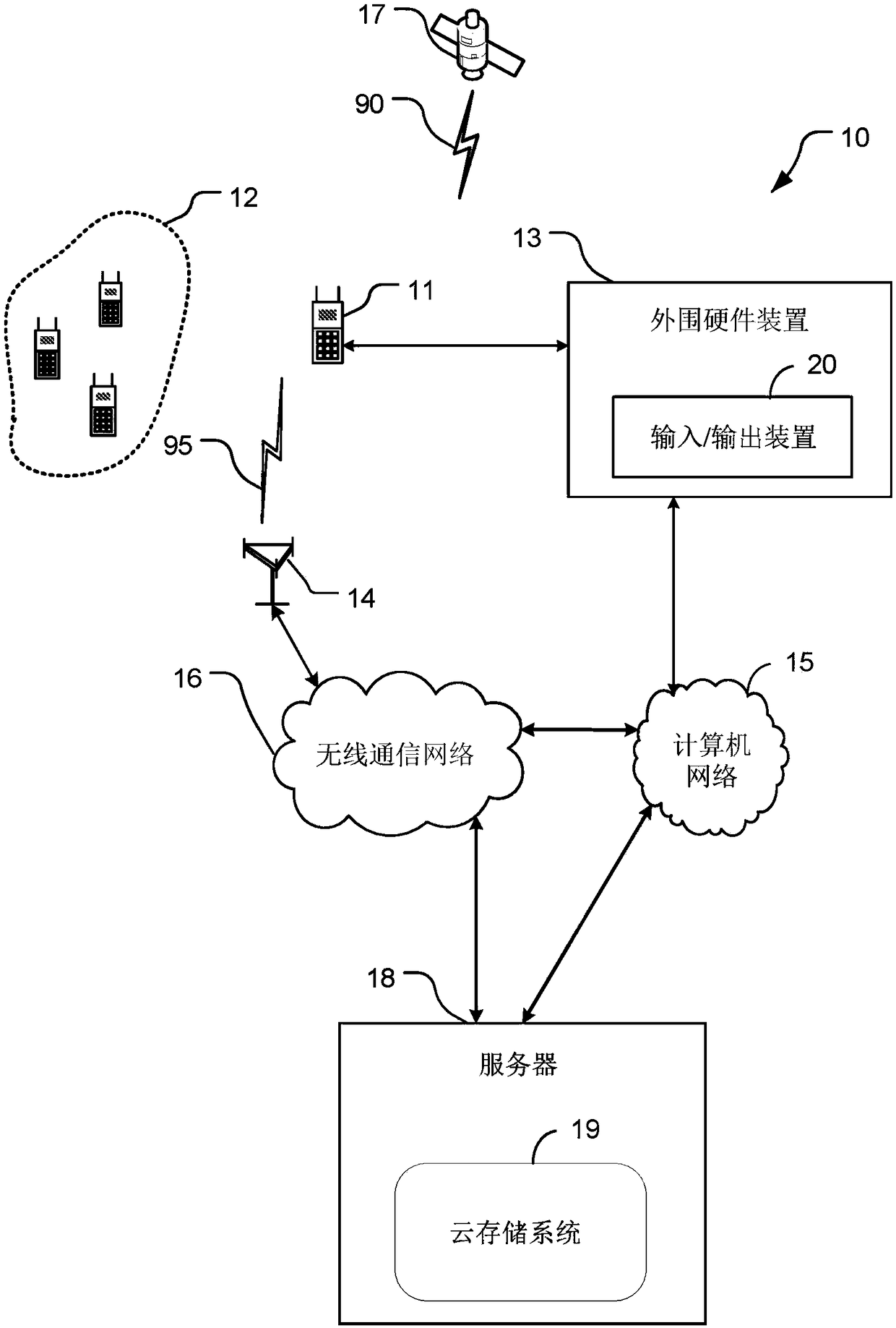
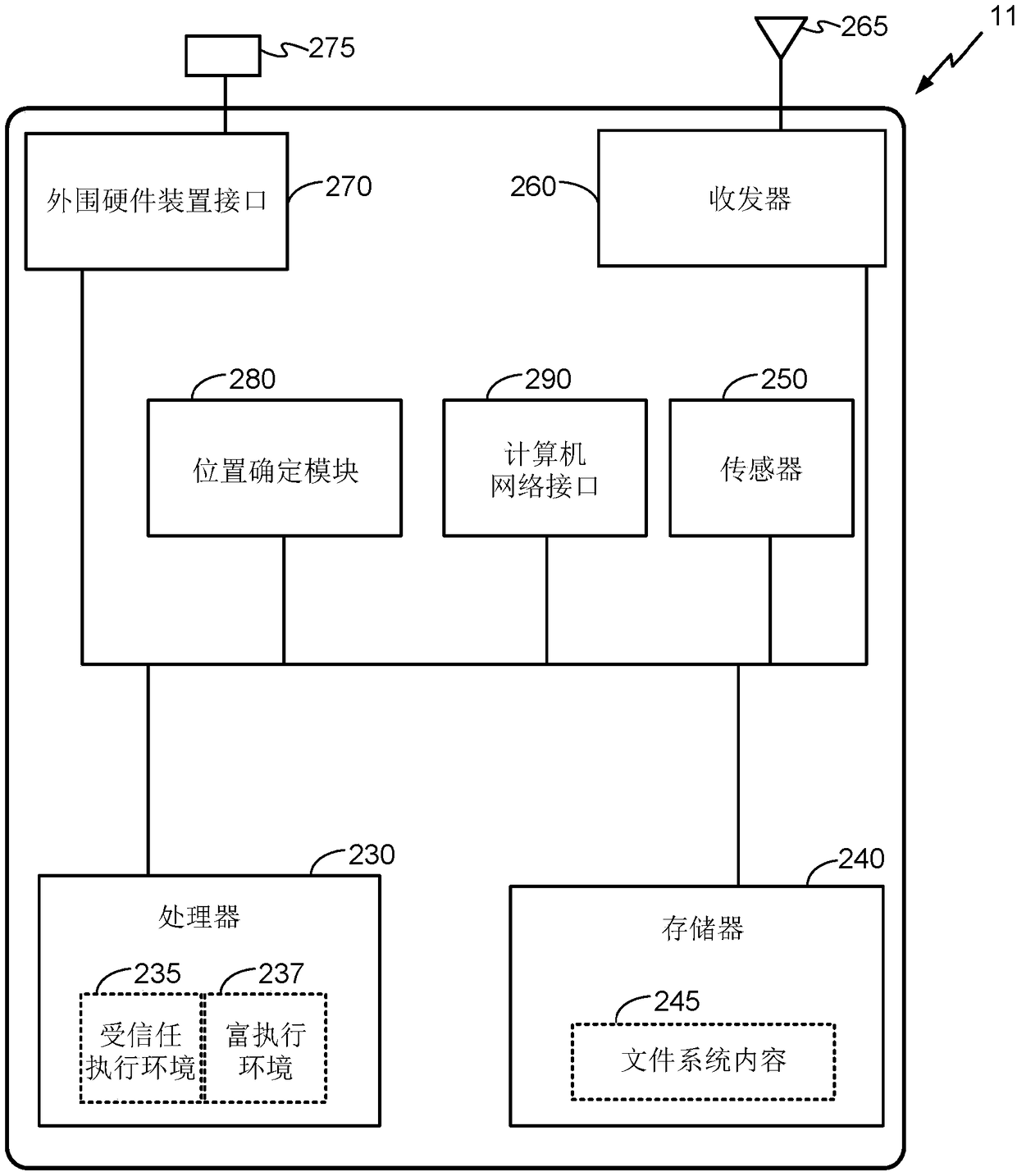
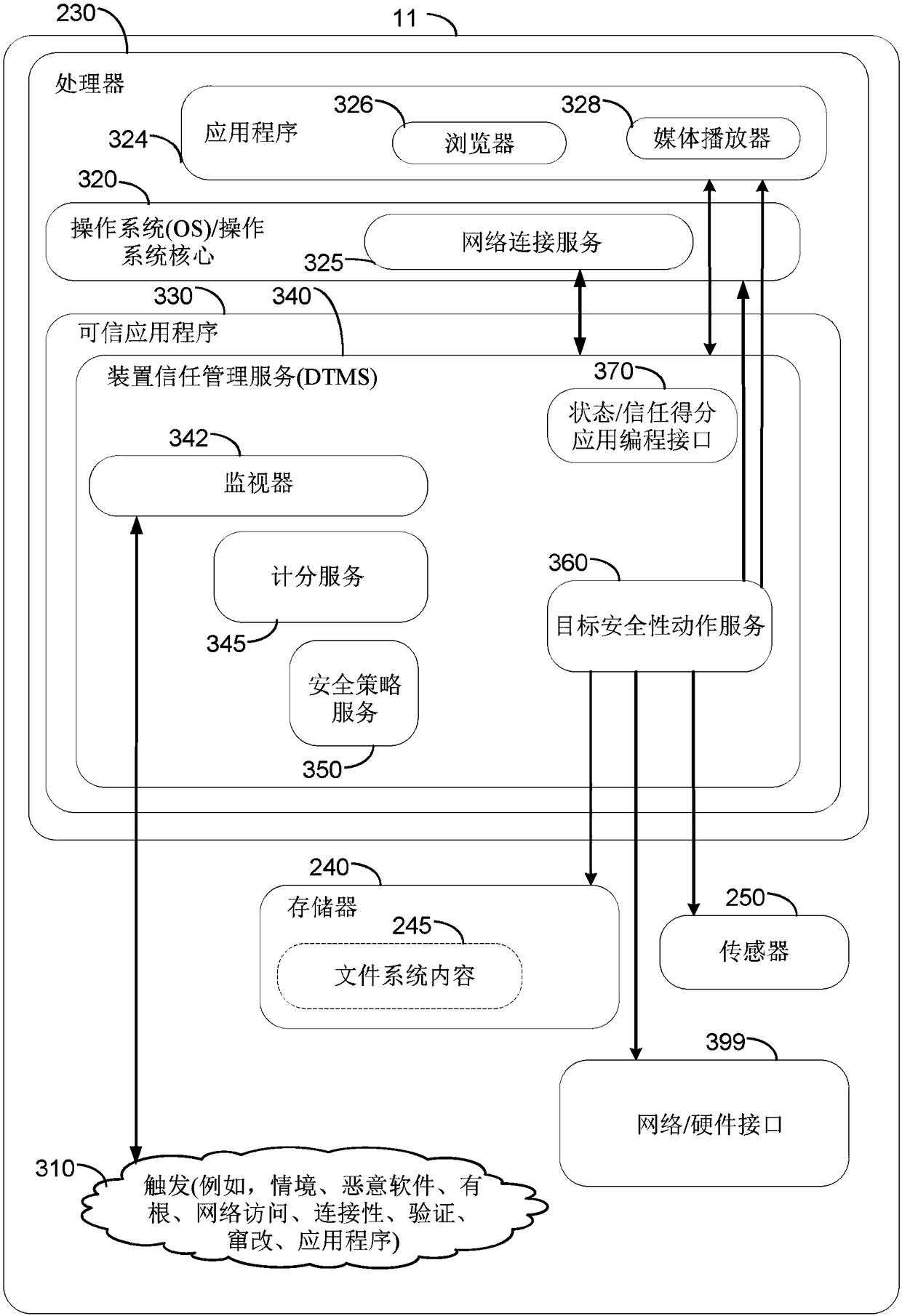
[0016] This disclosure presents techniques for providing security for electronic devices. The electronic device monitors the status of the electronic device for one or more threats to the security of the electronic device. The state may include the operation and / or configuration of the electronic device. The operation of the electronic device includes operating system and / or application program operation. The configuration of the electronic device includes software, firmware and hardware configuration. The electronic device detects one or more threats based on the monitored state and based on one or more security policies associated with the electronic device. In response to a detected threat, the electronic device self-enforces one or more security policies. The electronic device self-enforces one or more security policies by implementing one or more targeted security actions according to these policies. The targeted security actions may selectively alter operation and / or...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com