Binding authentication method of fingerprint algorithm library and fingerprint sensor and fingerprint recognition system
A technology of fingerprint sensor and fingerprint algorithm, which is applied in the field of fingerprint identification, can solve problems such as embezzlement of fingerprint algorithm library, and achieve the effect of avoiding embezzlement and increasing security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
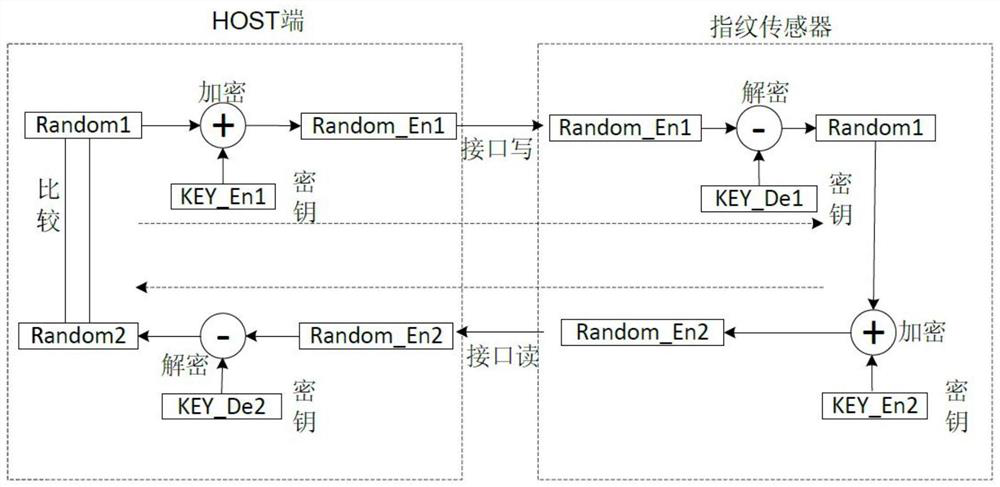
[0052] see image 3 and Figure 4 ,in image 3 It is a schematic diagram of the first embodiment of a binding authentication method between a fingerprint algorithm library and a fingerprint sensor provided by the present invention, Figure 4 Yes image 3 A schematic flow chart of the binding authentication method shown. The binding authentication method of the fingerprint algorithm library and the fingerprint sensor comprises the following steps:
[0053] S11, the HOST side generates random data Random1 every time authentication is performed. The random data Random1 can be generated according to parameters such as time, which is not limited in this embodiment;
[0054] S12. The HOST uses the first encryption key KEY_En1 to encrypt the random data Random1 to obtain the first encrypted data Random_En1;
[0055] Specifically, the fingerprint algorithm library at the HOST side can perform the first encryption process on the random data Random1 generated in step S11 through i...
Embodiment 2
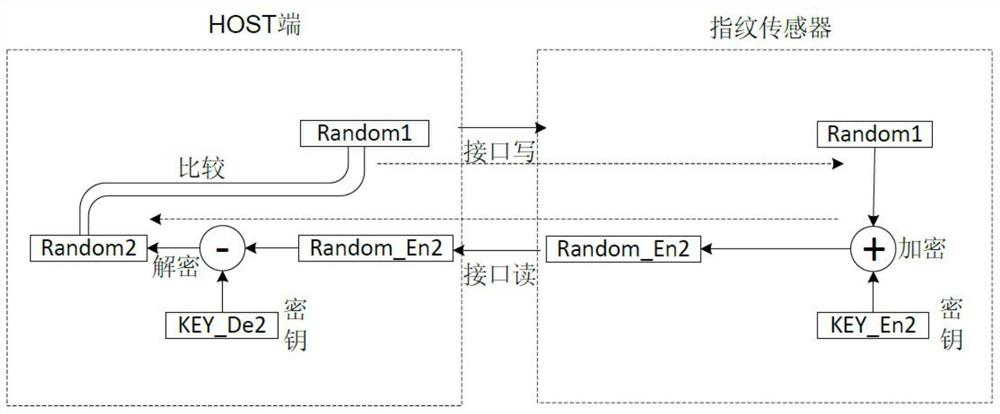
[0074] see Figure 5 and Image 6 ,in Figure 5 It is a schematic diagram of the second embodiment of a binding authentication method of a fingerprint algorithm library and a fingerprint sensor provided by the present invention, Image 6 Yes Figure 5 A schematic flow chart of the binding authentication method shown. Compared with Embodiment 1, the main difference of Embodiment 2 is that the HOST end directly provides the random data Random1 generated by it to the fingerprint sensor, without performing the first encryption process on the random data Random1 data, that is, the HOST end is connected with the fingerprint sensor The data written on the data interface between them is plain text. like Figure 7 and Figure 8 As shown, the binding authentication method of the fingerprint algorithm library and the fingerprint sensor provided in this embodiment includes the following steps:
[0075] S21. During each authentication, the HOST end generates random data Random1.
...
Embodiment 3
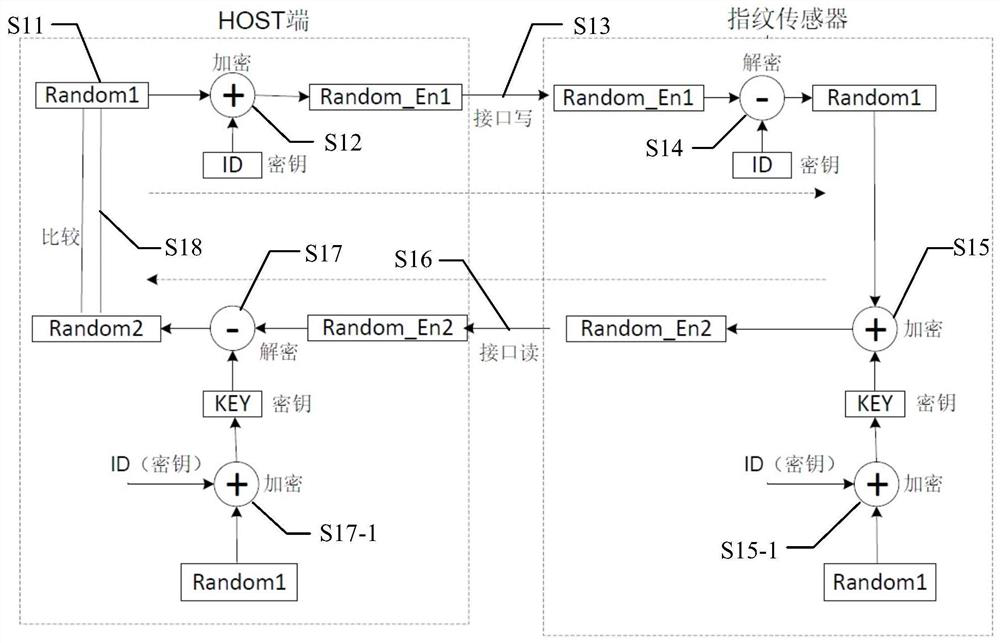
[0088] like Figure 7 As shown, this embodiment also provides a fingerprint identification system, the fingerprint identification system corresponds to Embodiment 1 of the binding authentication method between the fingerprint algorithm library and the fingerprint sensor, which includes a HOST terminal 710 and The fingerprint sensor 720, the HOST terminal 710 and the fingerprint sensor 720 are connected to each other through the data interface between them and perform data transmission. in,
[0089] The HOST terminal 710 includes:
[0090] Random number generation unit 711, which is used to generate random data Random1;
[0091] The first encryption unit 712 is used to encrypt the random data Random1 using the first encryption key KEY_En1 to obtain the first encrypted data Random_En1; wherein the first encryption unit 712 can use a preset first encryption function to The random data Random1 is encrypted.
[0092] The first communication unit 713 is configured to transmit th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com