Big data information security processing method and system of variable-length key RSA encryption algorithm
An encryption algorithm and information security technology, applied in the direction of digital transmission system, transmission system, secure communication device, etc., can solve the problem of unguaranteed security, and achieve the effect of simple means of security encoding and decoding and key distribution.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
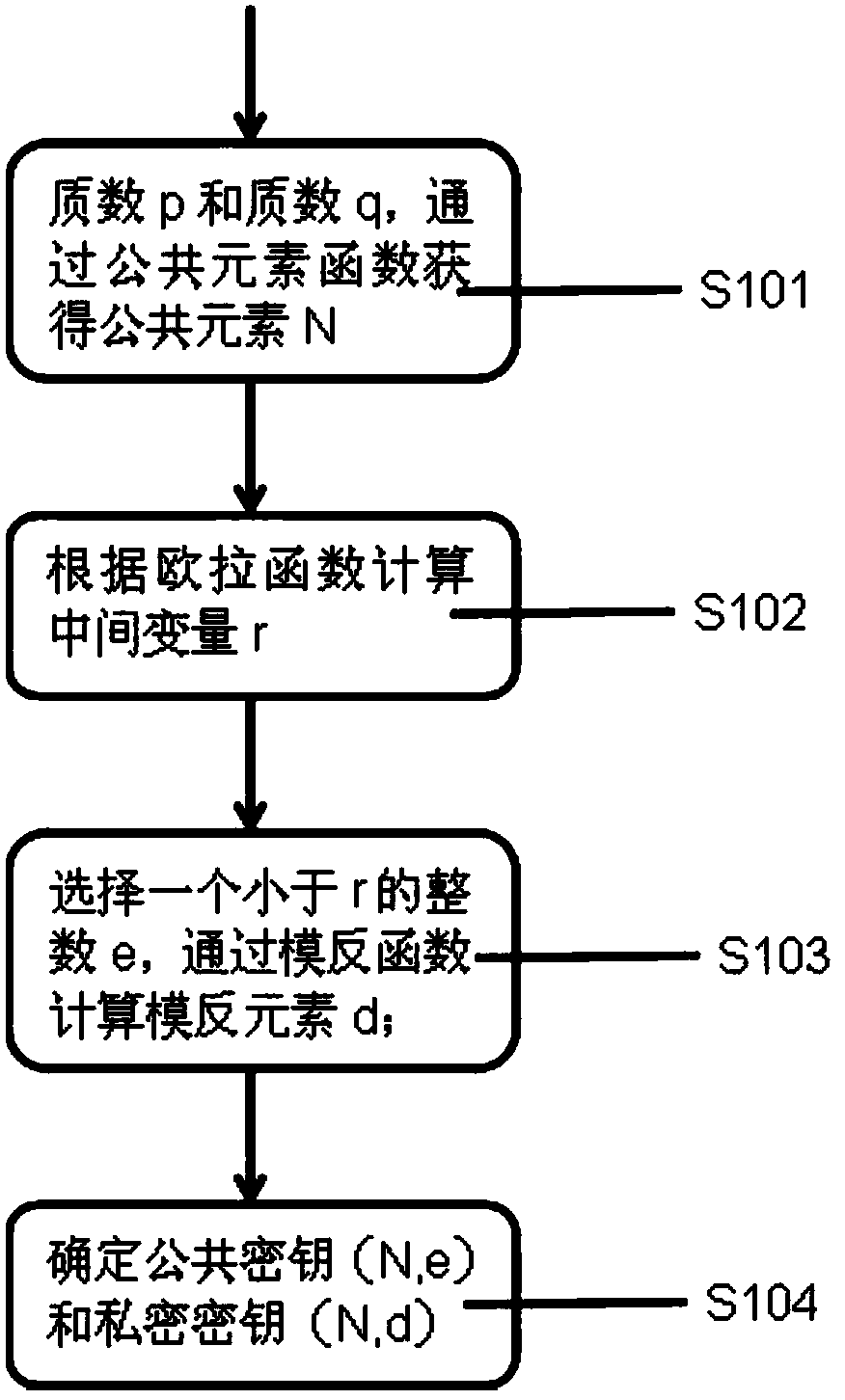
[0093] This embodiment: as figure 1 As shown, a large data information security processing method of the variable-length key RSA encryption algorithm, including:
[0094] Key generation: prime number p and prime number q, obtain the public element NS101 through the public element function;
[0095] The public element function is
[0096] Calculate the intermediate variable rS102 according to the Euler function;
[0097] The Euler function is r=(p-1)x(q-1);
[0098] Select an integer e smaller than r, and calculate the modulus element dS103 through the modulus function;
[0099] The modulo inverse function is
[0100] Determine public key (N, e) and private key (N, d) S104.
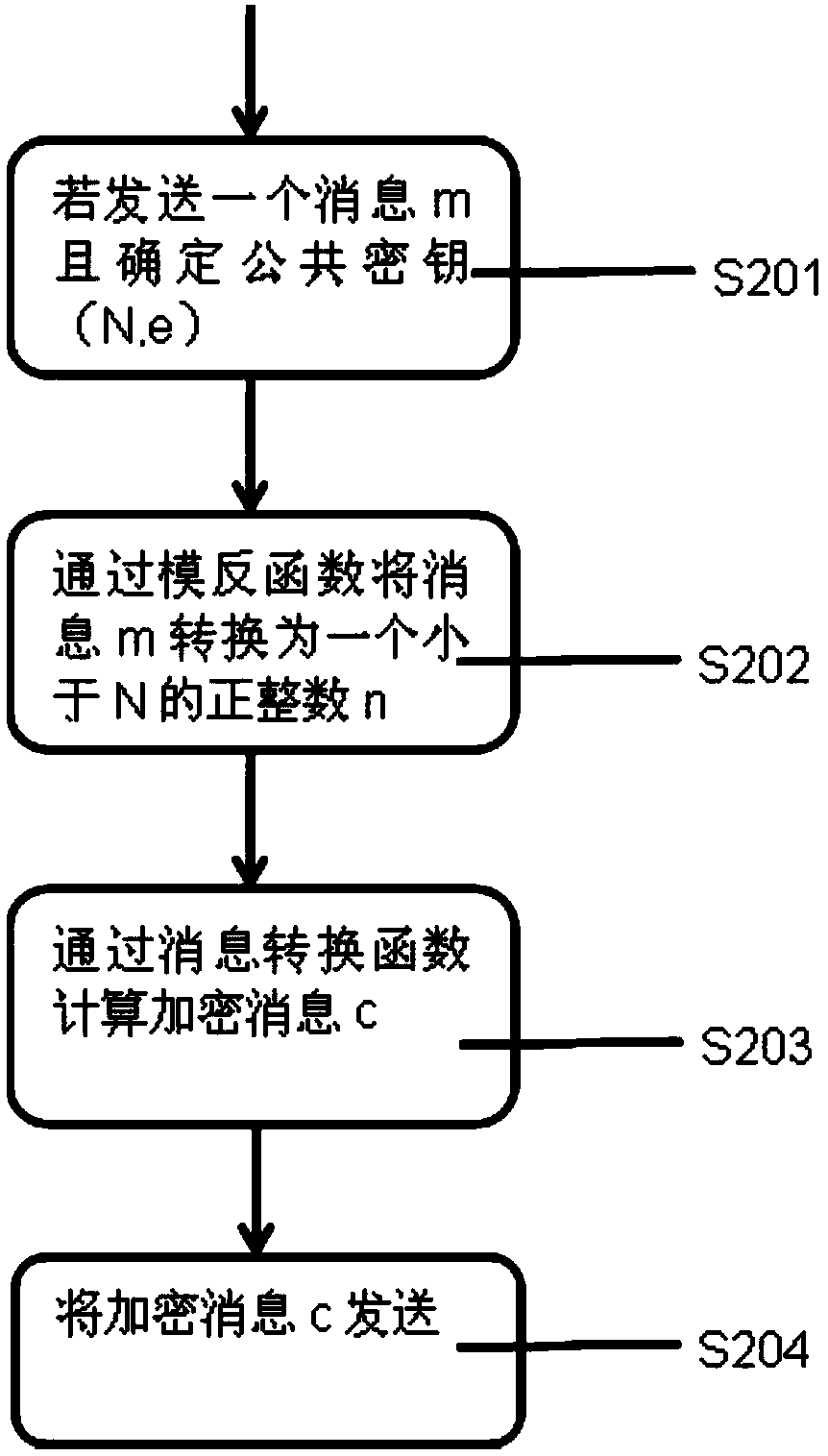
[0101] like figure 2 As shown, message encryption: if a message m is sent and the public key (N, e) S201 is determined, then the message m is converted into a positive integer nS202 smaller than N through the modulo inverse function;
[0102] Then calculate the encrypted message cS203 through t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com