Security and protection identity recognition method and system, and computer readable storage medium
A technology for identification and security, applied in transmission systems, short-distance communication services, electrical components, etc., can solve problems such as low security encryption and inconvenient use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
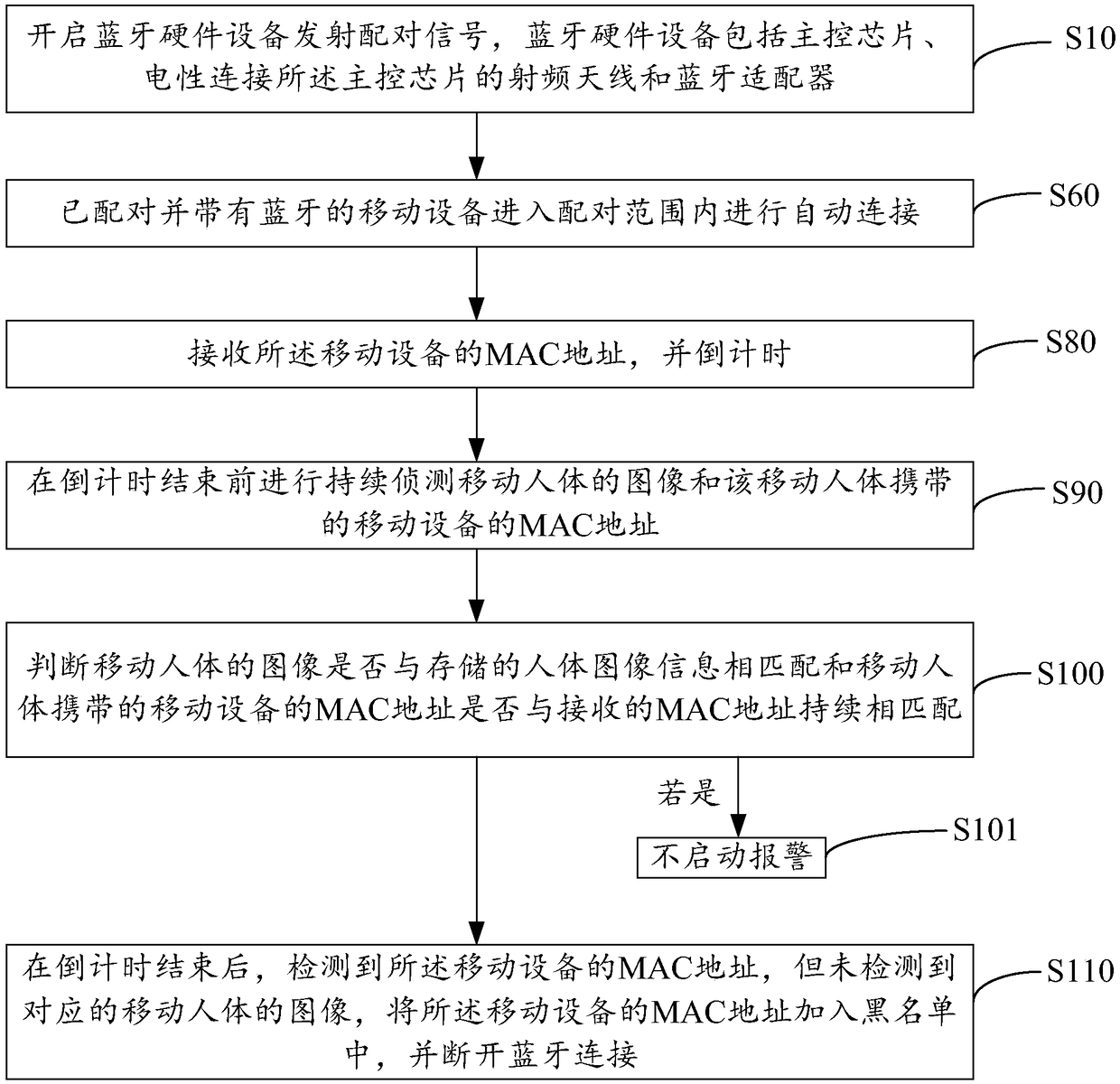
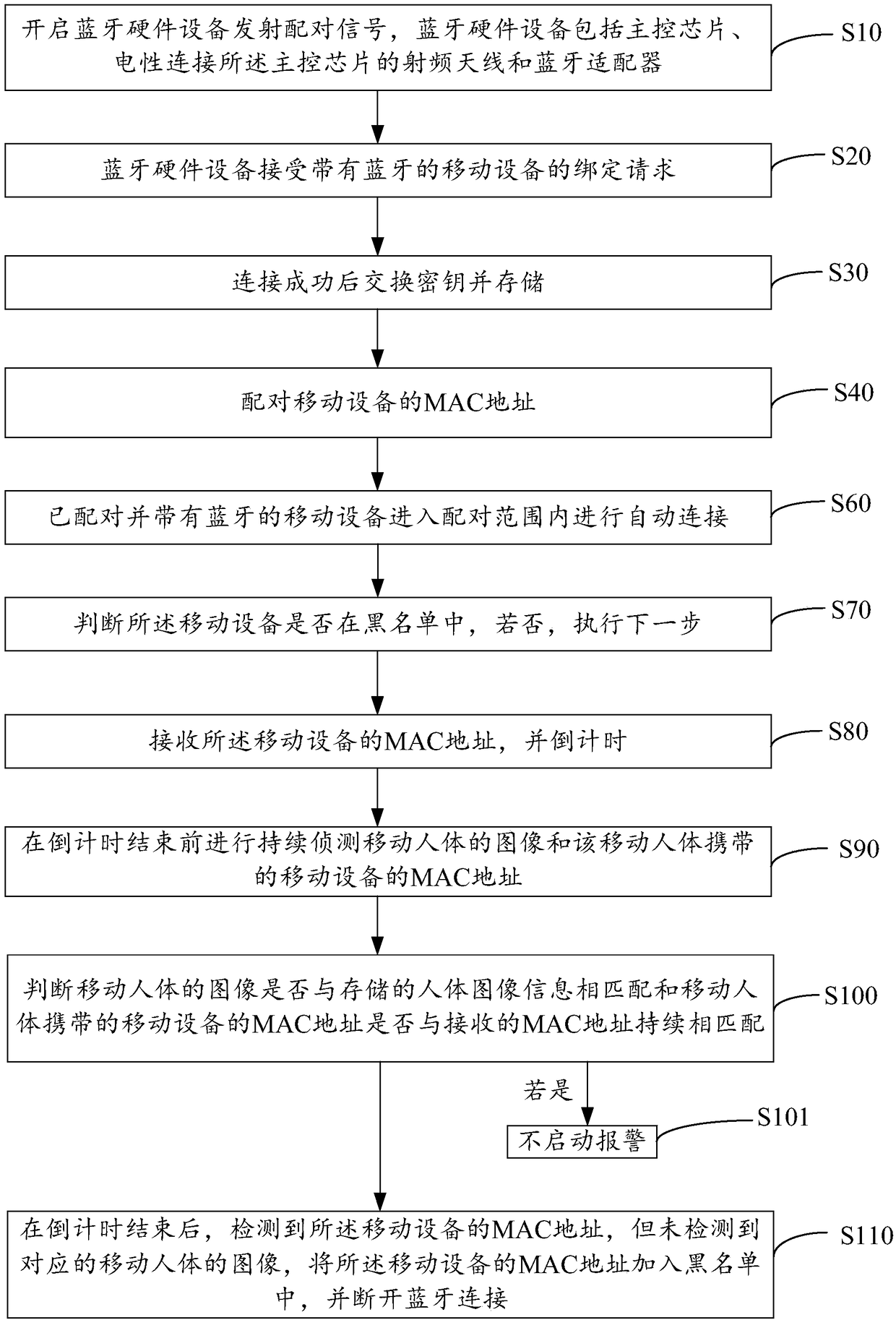
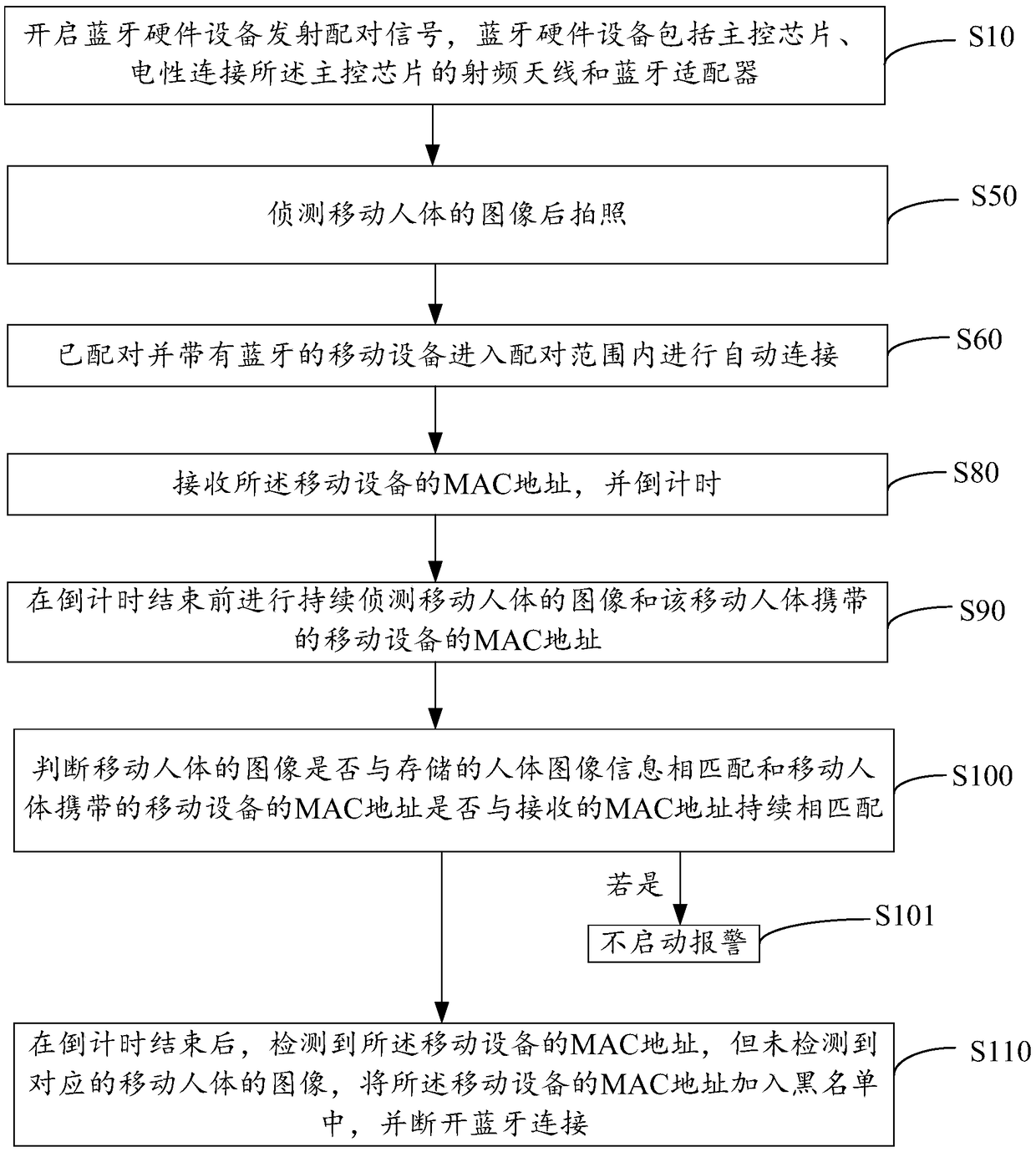
[0063] The first stage
[0064] Bluetooth hardware device 30: continue to wait for the Bluetooth connection of the paired mobile phone;
[0065] Family mobile phone: within the directional range, the Bluetooth signal of the family mobile phone appears;
[0066] Bluetooth hardware device 30: connect to the family’s mobile phone, judge whether there is this mobile phone connected to in the blacklist, if it does not appear in the blacklist, then continue;
[0067] Bluetooth hardware device 30: after the connection is successful, send the MAC address of the mobile phone to the main control chip 31, and the main control chip 31 is an IPC main control chip;
[0068] Main control chip 31: After receiving the MAC address, write "alarm stop" as "true", start the 30s countdown, that is, within 30s, do not respond to any alarm event, and the camera 40 continues to detect images of moving human bodies; 30s of them The time can be adjusted as needed.
[0069] When the main control chip ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com