A file audit and protection method based on linux security module
A security module and file technology, applied in computer security devices, computing, digital data protection, etc., can solve problems such as insufficient stability and system version compatibility, file protection cannot be achieved, etc., to achieve outstanding substantive features and reliable design principles , good stability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
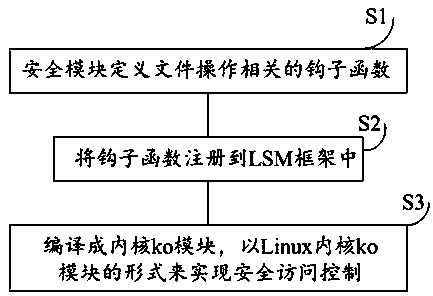
[0060] Such as Figure 1-2 Shown, a kind of file auditing, protection method based on Linux security module, comprises the steps:
[0061]S1: The security module defines hook functions related to file operations;
[0062] S2: Register the hook function into the LSM framework;
[0063] S3: Compile it into a kernel ko module, and implement security access control in the form of a Linux kernel ko module.
[0064] Step S1, including:
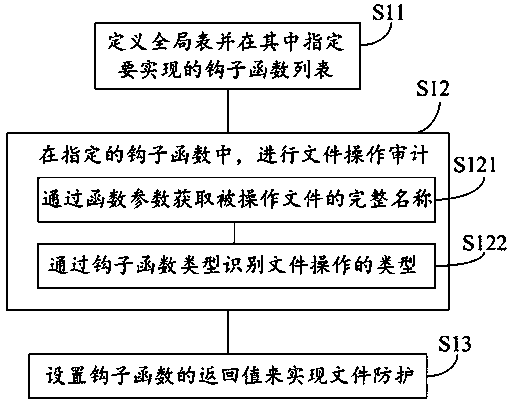
[0065] S11: define a global table and specify a list of hook functions to be implemented therein;
[0066] S12: In the specified hook function, perform file operation audit;
[0067] S13: Set the return value of the hook function to realize file protection.
[0068] In step S11, the global table of the security_operations structure is defined, and the specified hook functions include:
[0069] File copy / creation judgment function, file deletion judgment function, directory copy / creation judgment function, directory deletion judgment function, ...
Embodiment 2
[0102] A kind of file auditing, protection method based on Linux security module, comprises the steps:
[0103] (1) Define the global table of the security_operations structure, specify the list of hook functions we want to implement, including: inode_create function, inode_unlink function, inode_mkdir function, inode_rmdir function, inode_rename function, inode_setattr function, file_open function, file_permission function
[0104] In the hook function specified above, file operation audit is performed: obtain the complete name of the operated file through the function parameter, and identify the type of file operation through the hook function type. Some file operations are special and involve multiple hook functions, which need to be combined Hook function to identify.
[0105] A: The file operation type identification process is as follows:
[0106] The following two file operations are judged in the inode_create hook function:
[0107] a: file copy operation
[0108] W...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com