A method for detecting a transaction data source in a multi-chain scenario of a superbook
A detection method and transaction data technology, which are applied in the detection field of multi-channel data sources, can solve the problems of inability to achieve data isolation, synchronization and storage of data with different degrees of sensitivity, etc., so as to avoid sensitive data leakage and ensure security. sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Benefits of technology
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described in detail below in conjunction with the accompanying drawings and specific embodiments.
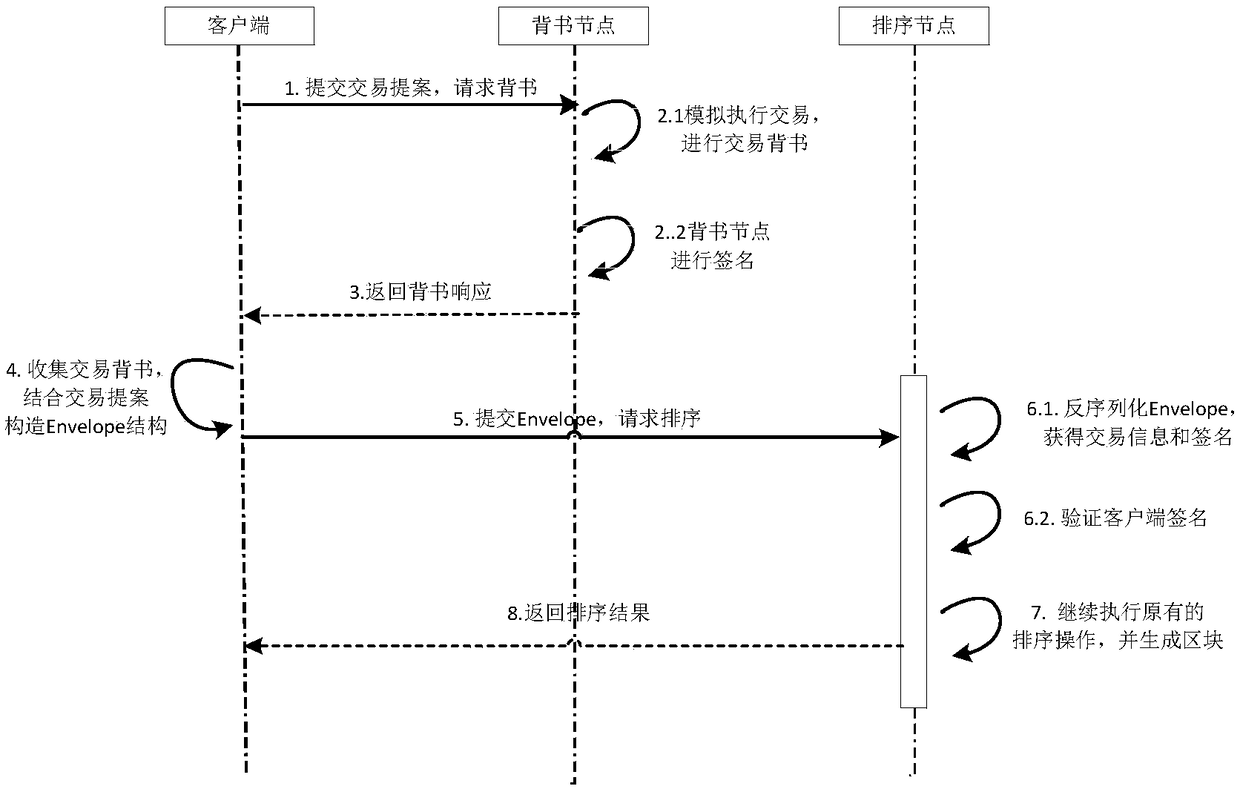
[0024] figure 1 It is the processing flow chart from transaction submission to block generation in the original Hyperledger Fabric;
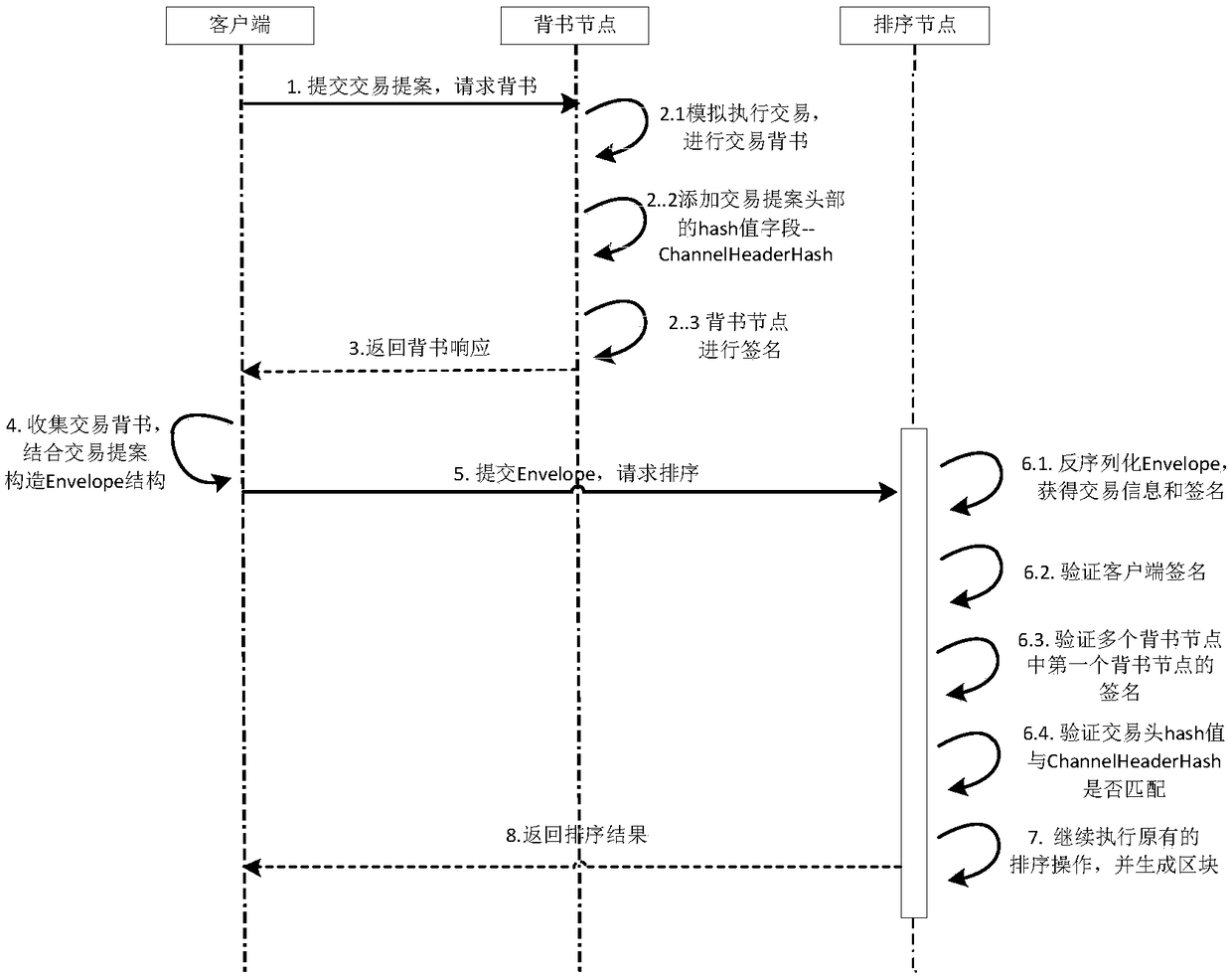
[0025] combine figure 2 (The processing flow chart of submitting transactions to generated blocks in the super ledger of this scheme), the improved complete transaction execution and sorting include the following steps (each node has been started and completed):
[0026] Step 1: The client generates a transaction proposal, signs it to obtain a SignedProposal, sends the SignedProposal to the endorsement node for endorsement, and the channel information of the transaction is included in SignedProposal.ProposalBytes.Header.ChannelHeader;
[0027] Step 2: The endorsement node simulates the execution of the transaction after receiving the proposal request, modifies the ProposalResponse data structure in t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com