Cross-link pass exchange method based on permission and computer readable medium
A chain exchange and token technology, applied in the information field, can solve the problems of not realizing cross-chain asset transfer, inability to realize cross-chain contracts, and no collection attributes.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0033] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings to further illustrate the present invention.
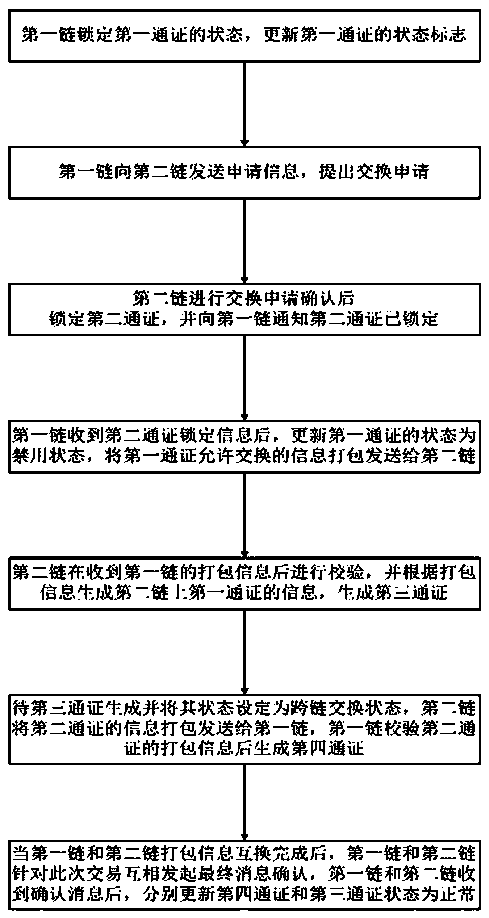
[0034] First, combine figure 1 A permission-based cross-chain token exchange method according to an embodiment of the present invention is described.
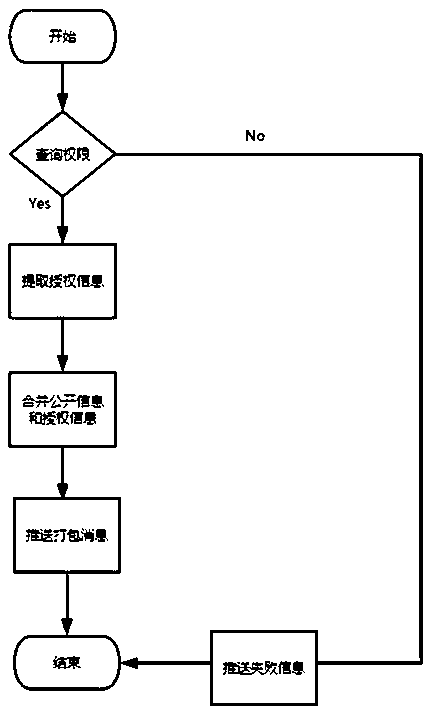
[0035] figure 1 It is a method flowchart illustrating a permission-based cross-chain token exchange method according to an embodiment of the present invention. The basic authority of the token includes public data and authorization data, and the status identifier of the token data includes three states: normal, exchanged, and disabled. The default is the normal state. Further, when the third token is exchanged back to the first When the fourth token is exchanged back to the second chain, the original authorization information of the third token or the fourth token can be retrieved. In this embodiment, the basic information identity number of the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com