Data security calling method and device
A data call and data security technology, applied in the field of data processing, can solve problems such as illegal acquisition and insufficient security of data call process
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
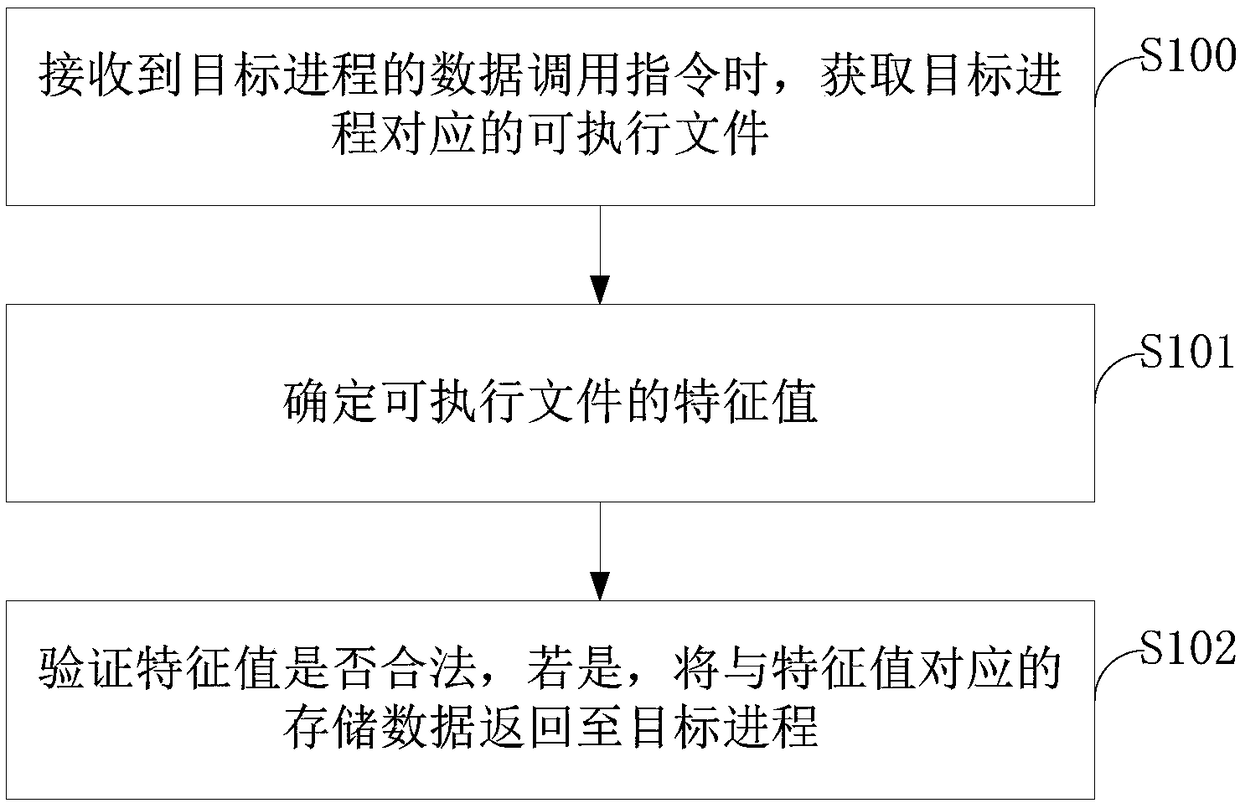
[0052] Embodiment 1 of the present application provides a data security call method, such as figure 1 As shown, the following steps S100-S102 are included:
[0053] S100. Obtain an executable file corresponding to the target process when receiving a data calling instruction of the target process.
[0054] Process (Process) is a running activity of a program in a computer on a certain data set. It is the basic unit of resource allocation and scheduling in the system and the basis of the operating system structure. When multiple programs are executed, they need to share system resources, so that As a result, each program has a mutual restriction relationship in the execution process, and the execution of the program shows the characteristics of discontinuity. These features all occur during the execution of the program, which is a dynamic process, while the traditional program itself is a set of instructions, which is a static concept and cannot describe the execution of the pr...
Embodiment 2
[0097] Embodiment 2 of the present application provides a data security calling device 600, such as Figure 6 shown, including:
[0098] The obtaining module 601 is configured to obtain an executable file corresponding to the target process when receiving a data calling instruction of the target process.
[0099] The determination module 602 is configured to determine the characteristic value of the executable file.
[0100] Returning module 603, configured to verify whether the characteristic value is legal, and if so, return the stored data corresponding to the characteristic value to the target process.
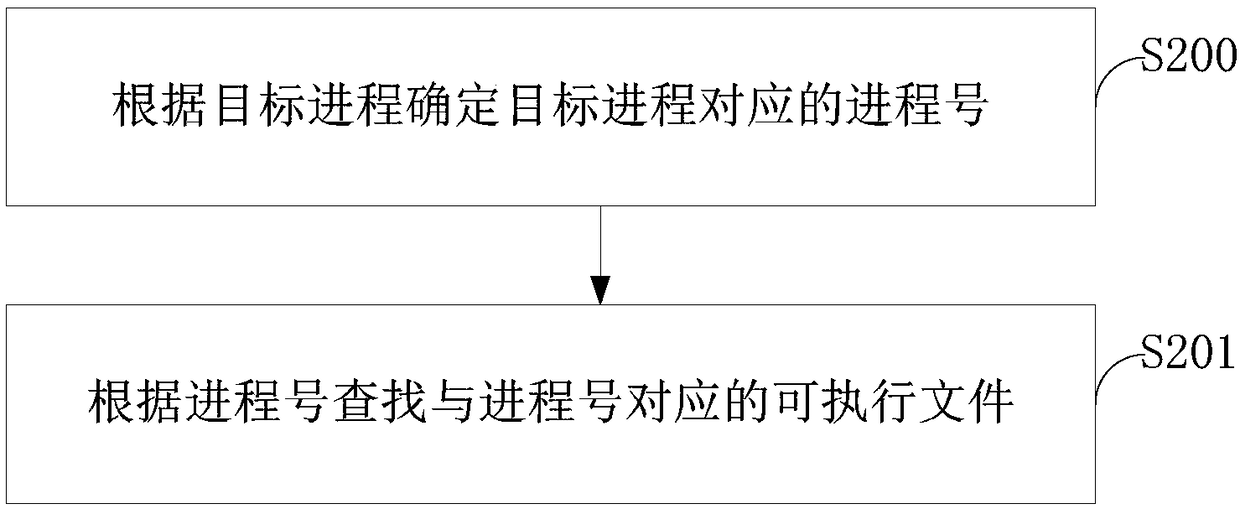
[0101] Optionally, the obtaining module 601 is specifically configured to:
[0102] A process number corresponding to the target process is determined according to the target process.
[0103] Find the executable file corresponding to the process number according to the process number.
[0104] Optionally, the determination module 602 is specifically configured to:
...
Embodiment 3
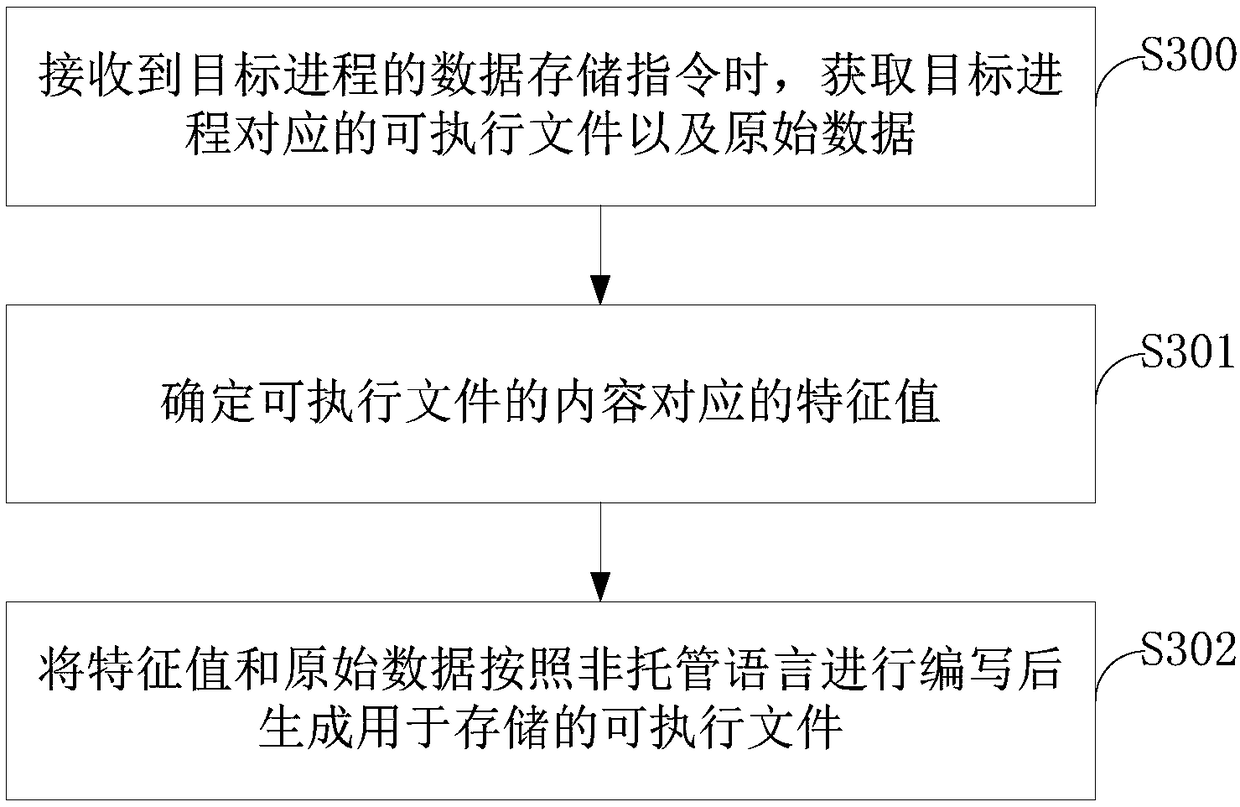
[0122] Embodiment 3 of the present application also provides an electronic device 700, such as Figure 7 As shown, it includes: a processor 701, a memory 702, and a bus 703. The memory 702 stores machine-readable instructions executable by the processor 701. When the electronic device is running, the processor 701 communicates with the memory 702 through the bus. The processor 701 executes the following machine-readable instructions stored in memory 702:
[0123] When the data calling instruction of the target process is received, the executable file corresponding to the target process is obtained.
[0124] Determine the characteristic value of the executable file.
[0125] Verify whether the characteristic value is legal, and if so, return the stored data corresponding to the characteristic value to the target process.
[0126] Optionally, the execution instructions executed by the processor 701 specifically include:
[0127] A process number corresponding to the target pr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com