Network security efficiency evaluation method based on attack and defense association matrix
A network security and correlation matrix technology, applied in the field of information security, can solve the problems of inaccurate calculation results, focus on measuring the effect of attacks, ignore defense and other problems, and achieve the effect of scientific and objective results
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] In order to make the purpose, content, and advantages of the present invention clearer, the specific implementation manners of the present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
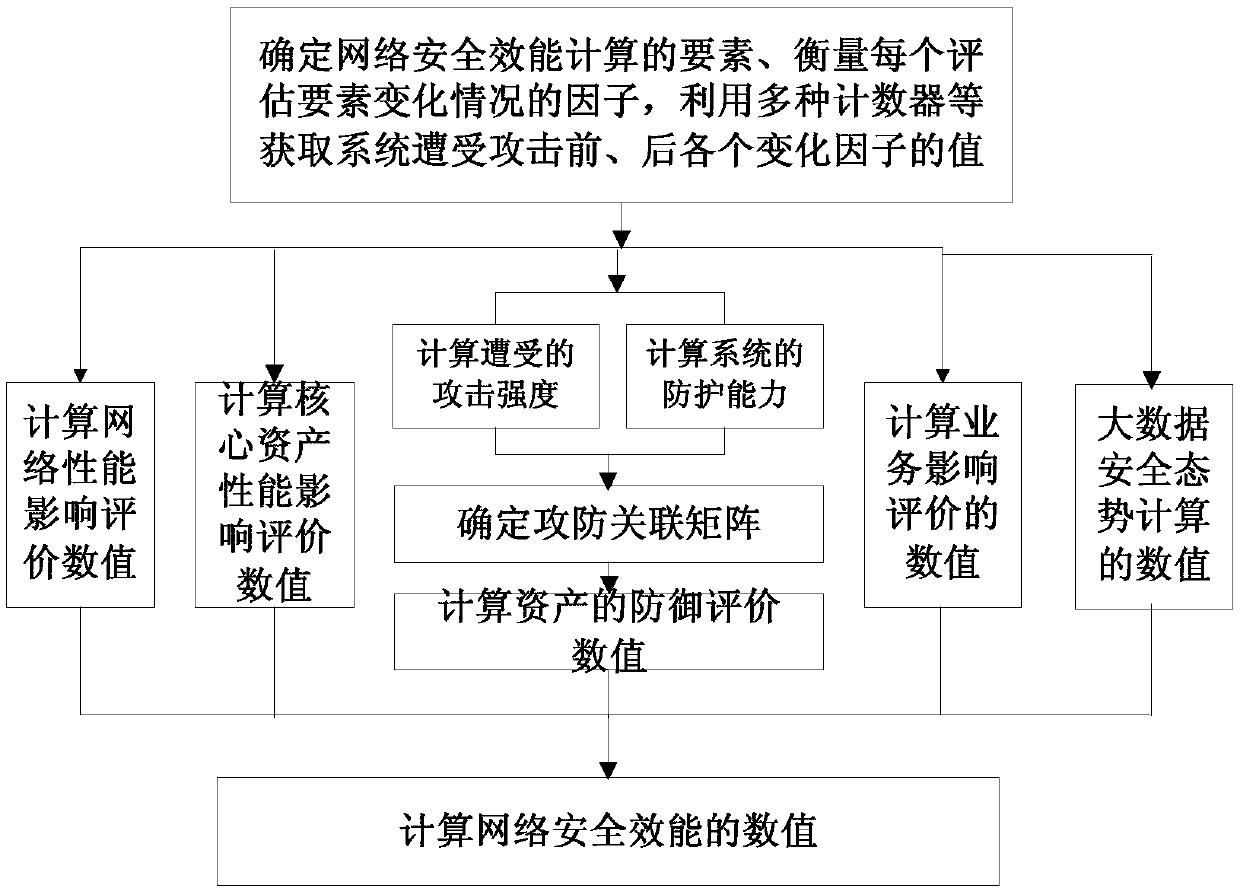
[0035] The present invention firstly determines the elements of network security efficiency calculation, and the factors to measure the change of each calculation element; Obtain the values of each calculation element factor before and after the attack, and preprocess the collected raw data to eliminate redundancy; finally, calculate the value of network security effectiveness evaluation by calculating the value of each calculation element separately.
[0036] In the present invention, the network security efficiency calculation elements are divided into: {network damage effect, asset damage effect, business damage effect, attack intensity, system protection capability, big data security situation}.
[0037] The calc...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com