Attack method of location anonymization algorithm under continuous LBS requests
An anonymous algorithm and location information technology, applied in the field of cryptography, can solve user concerns about location privacy, achieve the effect of protecting track privacy, reducing the risk of leakage, and narrowing the scope of anonymity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention is described in further detail below in conjunction with accompanying drawing:
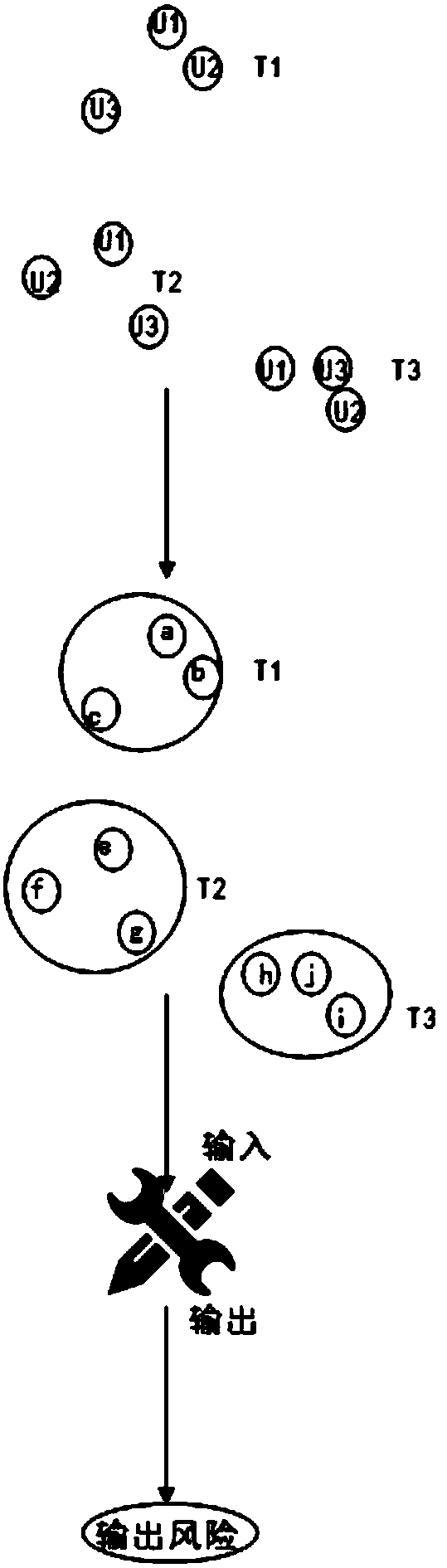
[0017] refer to figure 1 , the attack method of position anonymity algorithm under continuous LBS request of the present invention comprises the following steps:
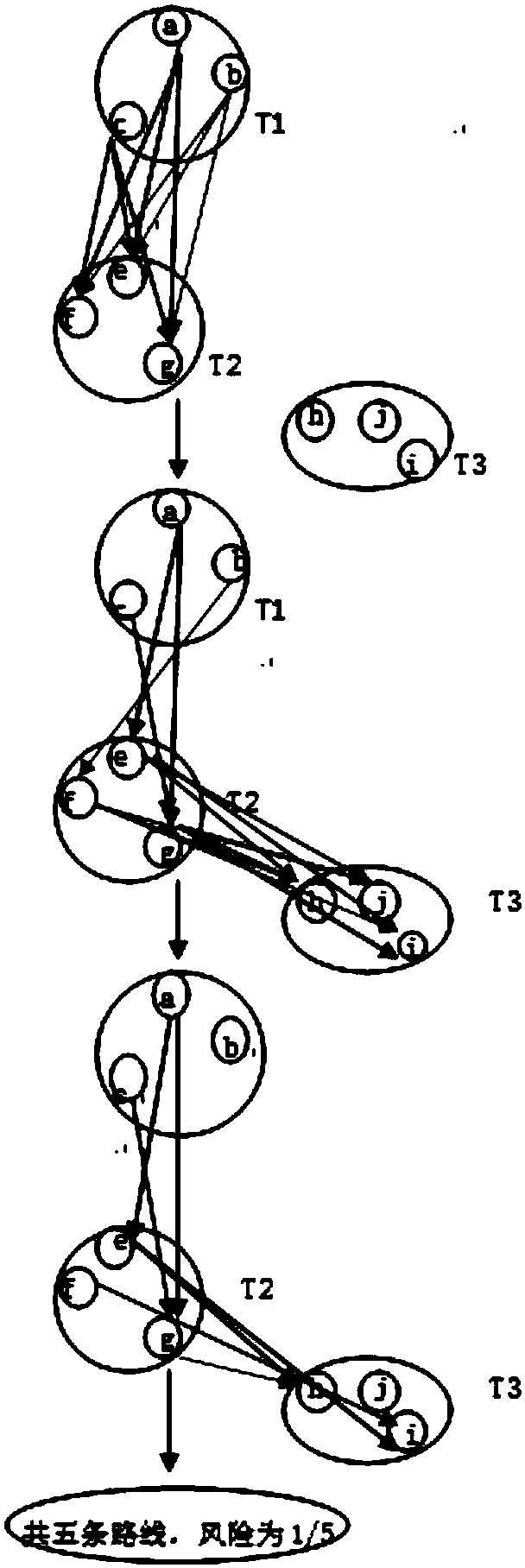
[0018] 1) Assuming that there are users {a, b, c} and users {e, f, g} in the adjacent anonymous areas R and R' respectively, the attack system pairs the users in the adjacent anonymous areas R and R', and obtains 9 position pairs, an anonymous trajectory is formed between two positions in a position pair;
[0019] 2) Set the format of each location information in the anonymous trajectory as {longitude, latitude, query time}, apply for the key of BaiDu MapAPI, and use RouteMatrix v2 to find the driving time, riding time and walking time between each location pair time;
[0020] 3) Set the time difference T between adjacent anonymous locations, and judge whether the driving time, cycling time, and walking t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com