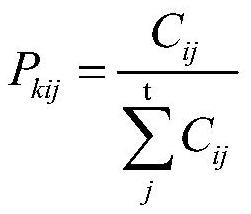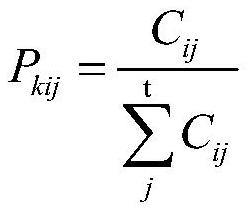Android malware detection method based on api call sequence
A technology of API call and call sequence, applied in the field of Android malware detection based on application programming interface API call sequence, can solve the problems of low detection efficiency, difficult analysis of Android application software, low recognition rate, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
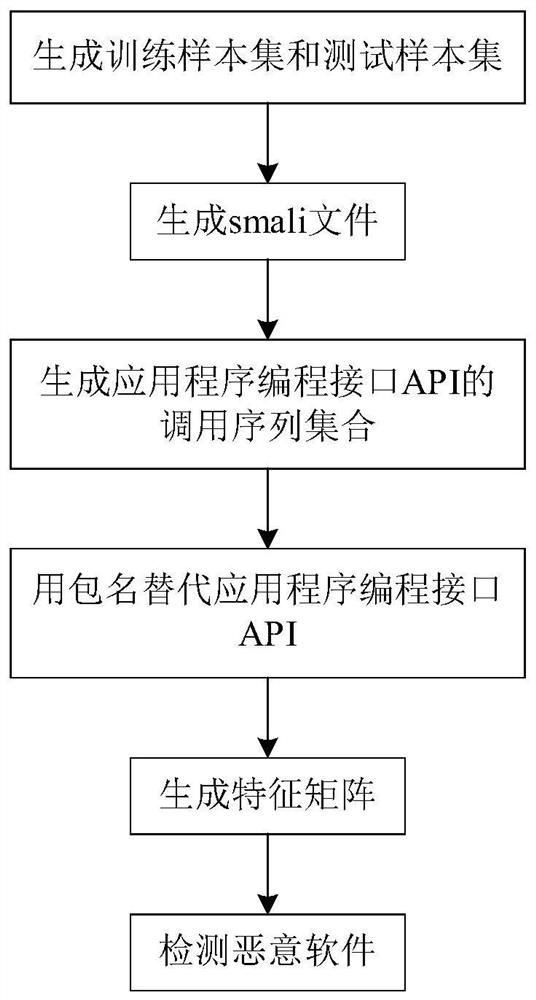
[0040] By the following figure 1 The specific steps of the invention are described below.
[0041] Step 1, generate training sample sets and test sample sets.
[0042] Extract the known 1600 Android applied software from the application software library and the known 2,400 Andrews normal applications, form a training sample set.
[0043] 700 Android applications to be tested constitute a test sample set.
[0044] Step 2, generate a smali file.
[0045] Using Android anti-compilation tools, the training sample concentration is used to confine each Android application to get the SMALI file corresponding to each Android application.
[0046] Step 3 Generate the call sequence set of the application programming interface API.
[0047] Use the depth priority algorithm DFS to generate a call sequence consisting of all application programming interface APIs in each SMALI file.
[0048] The specific steps of the depth priority overall calendar algorithm DFS are as follows.
[0049] Step 1 ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com