Identity authentication method for a content request user in an information center network
An information center network and content request technology, applied to key distribution, can solve the problems of unable to contain IFA from the root, PIT entry discarding, PIT table resource exhaustion, etc., and achieve the effect of avoiding the leakage of sensitive information
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The preferred embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
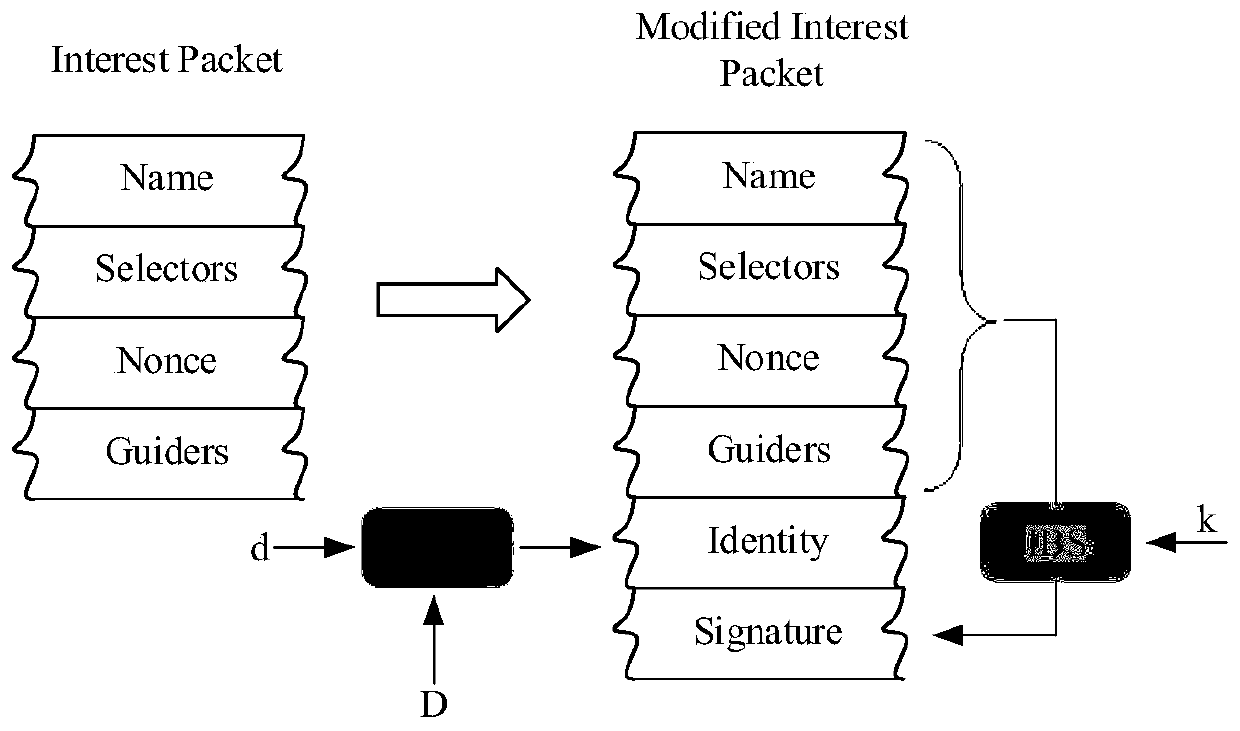
[0033] refer to figure 1 , an identity authentication method for content requesting users in an information center network. The extended Interest packet structure adds two fields to the original Interest packet structure: the encrypted identity and the requested user signature, which are used to store the encrypted user identity respectively. And the signature information of the user who initiates the interest request. The content requests the user to embed the IBE-encrypted identity and IBS signature information in each interest packet sent.
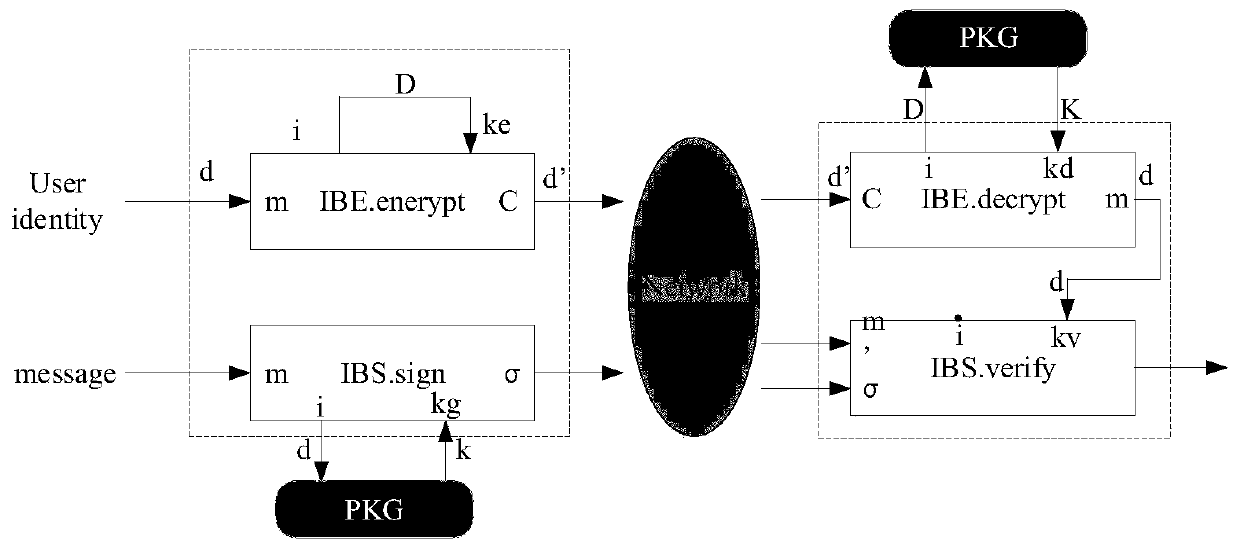
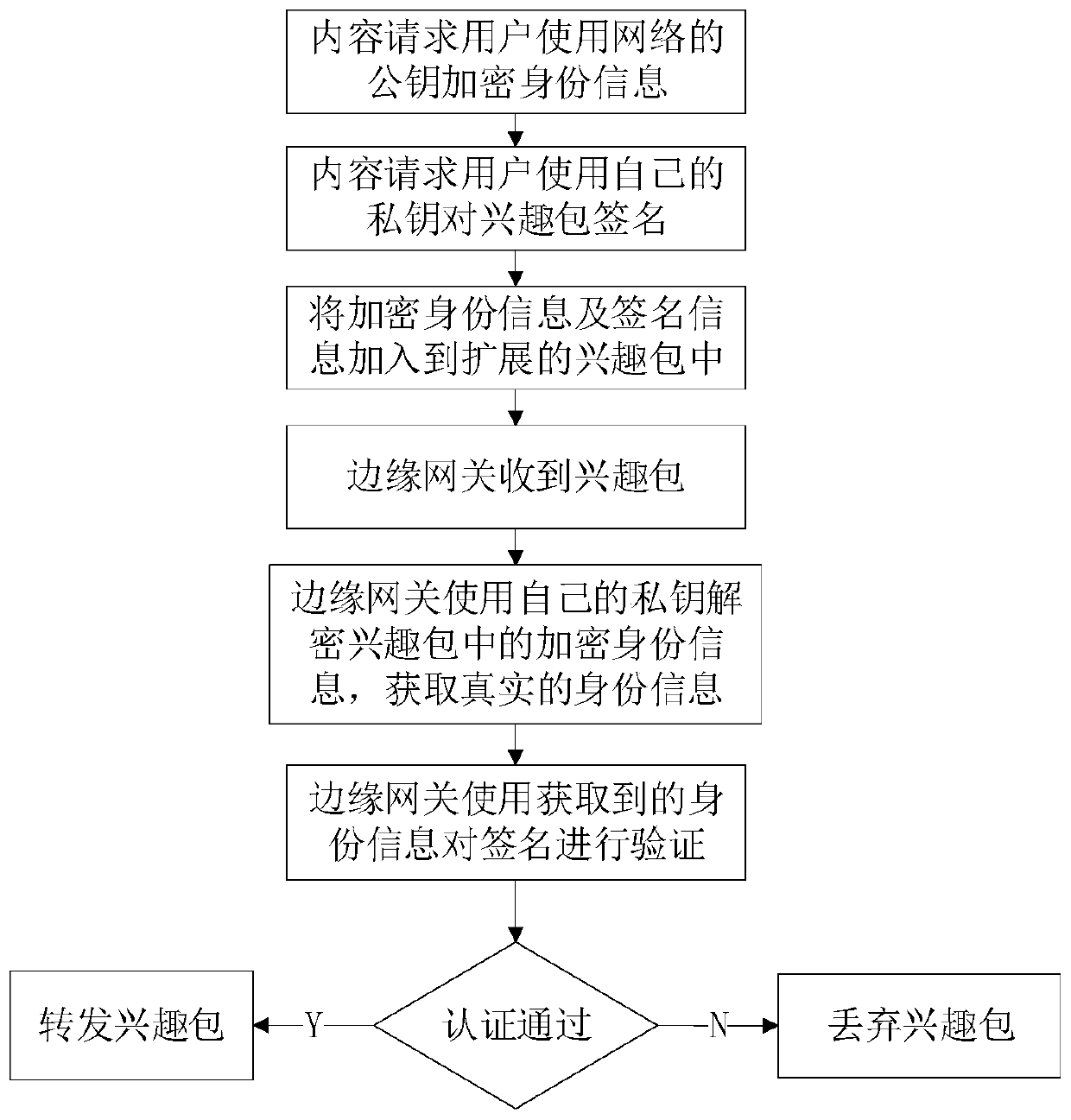
[0034] Such as figure 2 , image 3 As shown, the method also includes the following specific concrete implementation steps as follows:
[0035] Step S1: The content requests the user to use the network identity as a key to encrypt its identity with the IBE algorithm. d'=IBE.encrypt(d,D), where ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com