Method and device for selecting one client to generate a key for multiple clients and multiple servers
A multi-server, multi-client technology, applied in the field of information security, can solve the problems of increasing the burden of the key server, low flexibility, and no solution, and achieve the effect of improving security and flexibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
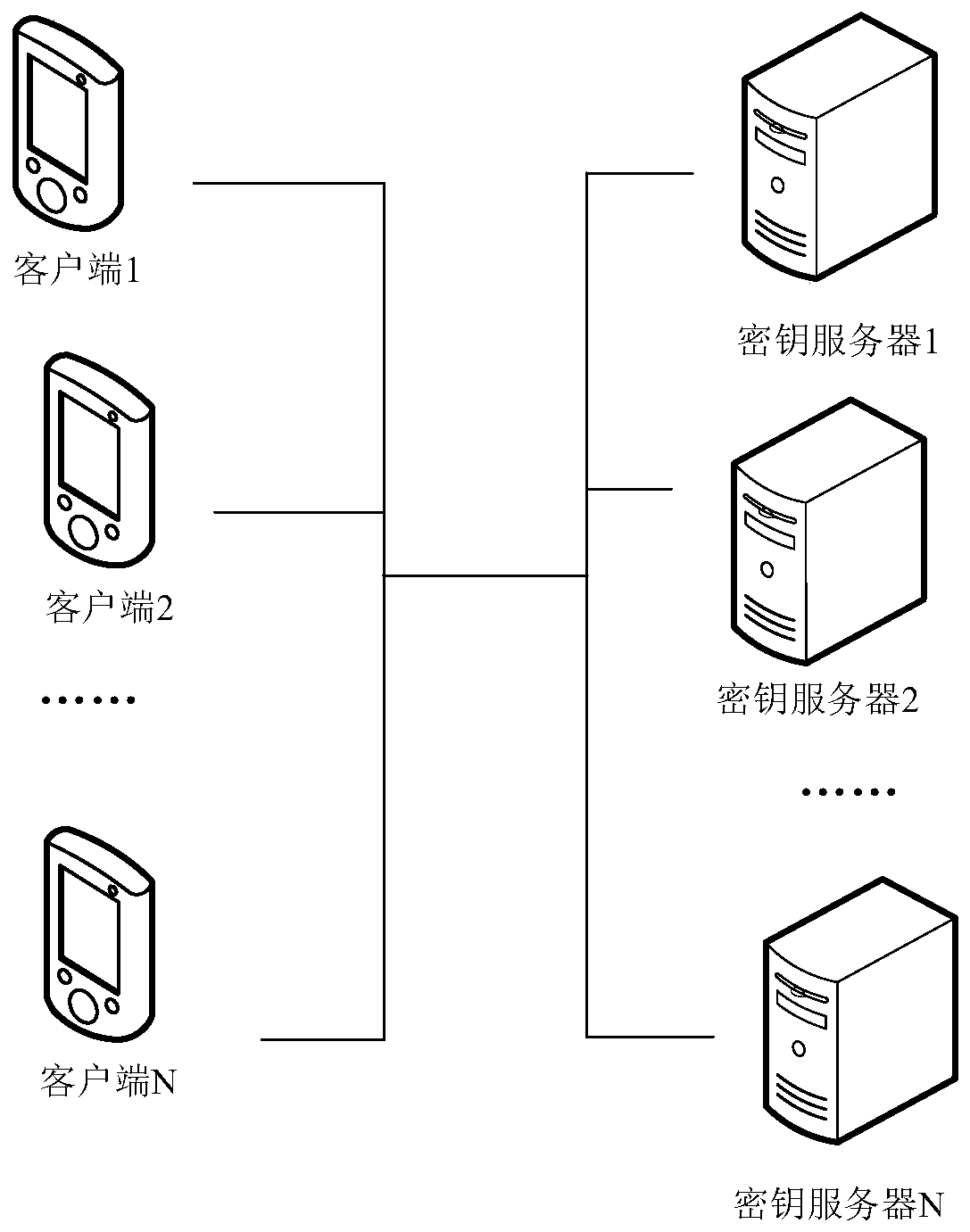
[0107] In this example, a key management method is provided based on secure two-party computing that generates keys through the client and is kept by multiple servers, that is, a single client generates a private key and splits it into multiple components for delivery. To multiple servers and multiple clients, use multiple servers and multiple clients to calculate signatures through two-party MPC; refresh multiple server and multiple client components through backup private keys, and refresh multiple Server and multiple client components.
[0108] Operations such as key generation, use, storage, backup, recovery, and refresh in this situation are explained as follows:
[0109] 1) generate:
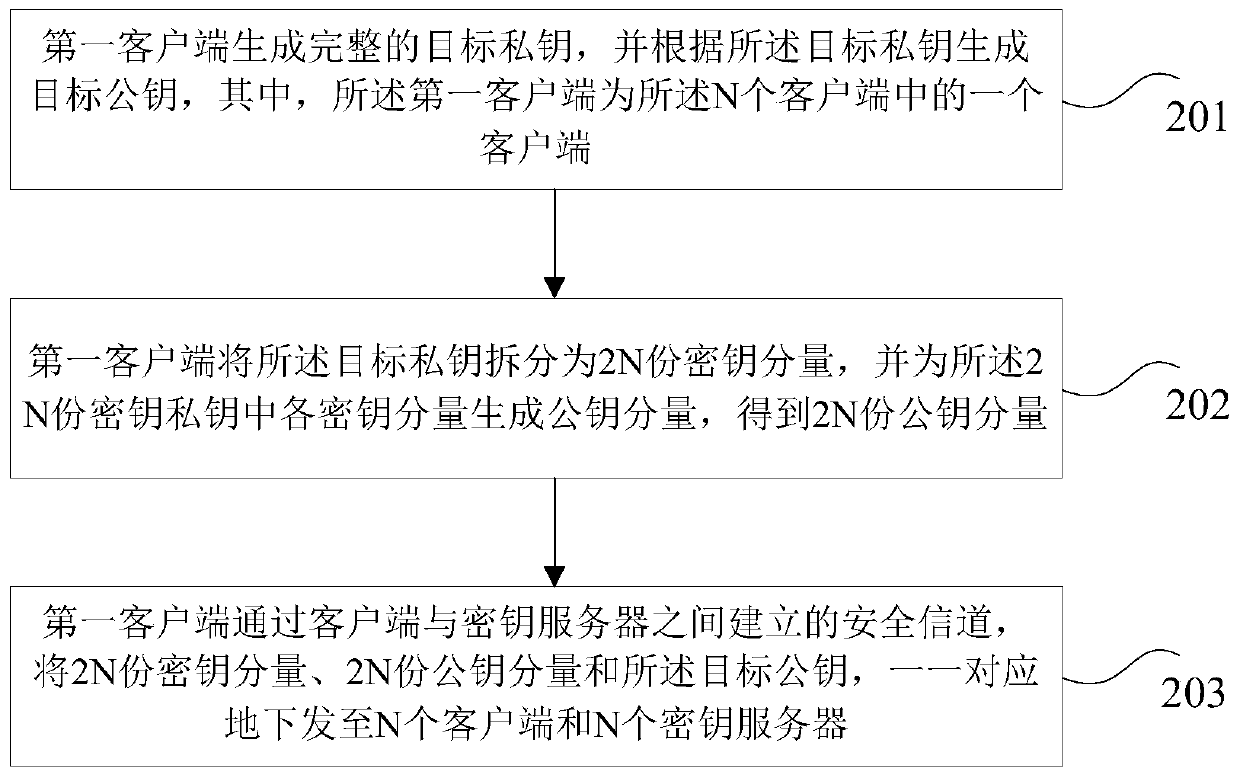
[0110] Such as image 3 As shown, the following steps may be included:
[0111] S1: The client and the key server complete two-way authentication through KYC, and issue authentication materials to complete the registration process;
[0112] S2: Client 1 generates a complete private key...
example 2
[0143] In this example, a key management method based on secure multi-party computing is provided that generates keys through the client and is kept by multiple servers. Multiple clients and multiple key servers, use multiple clients and multiple key servers to calculate signatures through MPC, refresh multiple clients and multiple key server components by backing up private keys, refresh multiple clients through MPC with multiple key server components.
[0144] Operations such as key generation, use, storage, backup, recovery, and refresh in this situation are explained as follows:
[0145]1) generate:
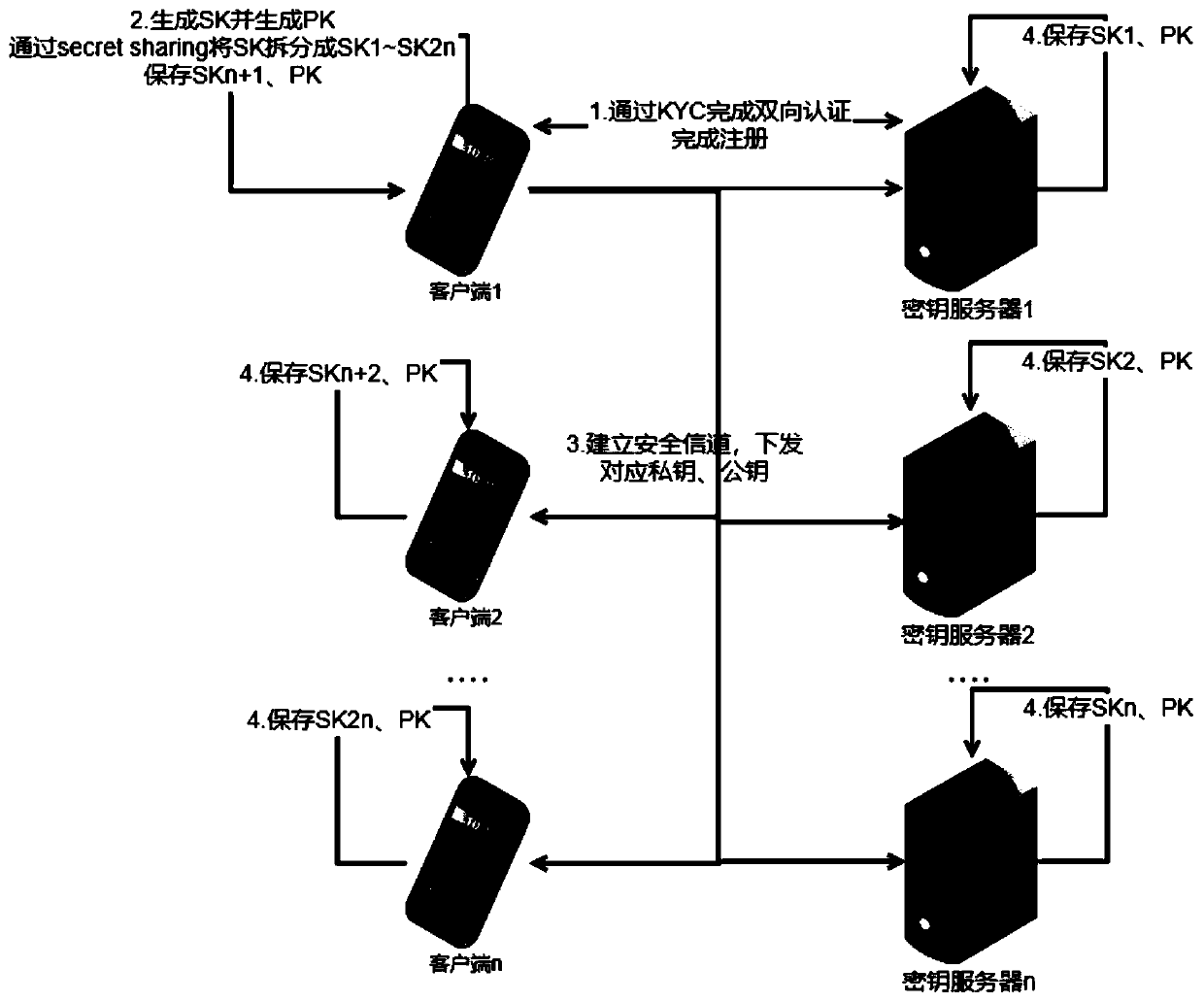
[0146] Such as Figure 8 As shown, the following steps may be included:
[0147] S1: The client and the key server complete two-way authentication through KYC, and issue authentication materials to complete the registration process;
[0148] S2: Client 1 generates a complete private key SK, and generates a related public key PK based on the private key SK. Split the priv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com