An industrial control system vulnerability trend analysis and early warning method and system
A trend analysis, industrial control system technology, applied in transmission systems, digital transmission systems, data exchange networks, etc., can solve problems such as inability to produce synergies, attack losses, lack of network security situational awareness and linkage early warning, etc. The effect of changing and reducing the timeliness and avoiding production accidents
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0035] The present invention will be further described below in conjunction with the accompanying drawings and specific embodiments, so that those skilled in the art can better understand the present invention and implement it, but the examples given are not intended to limit the present invention.
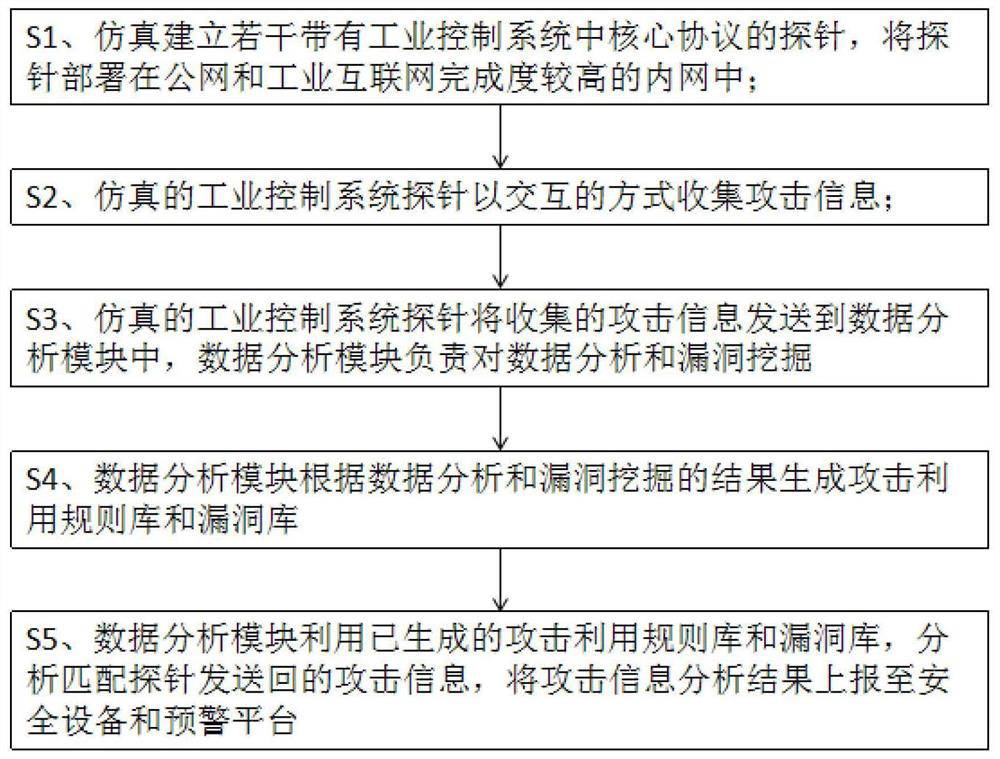
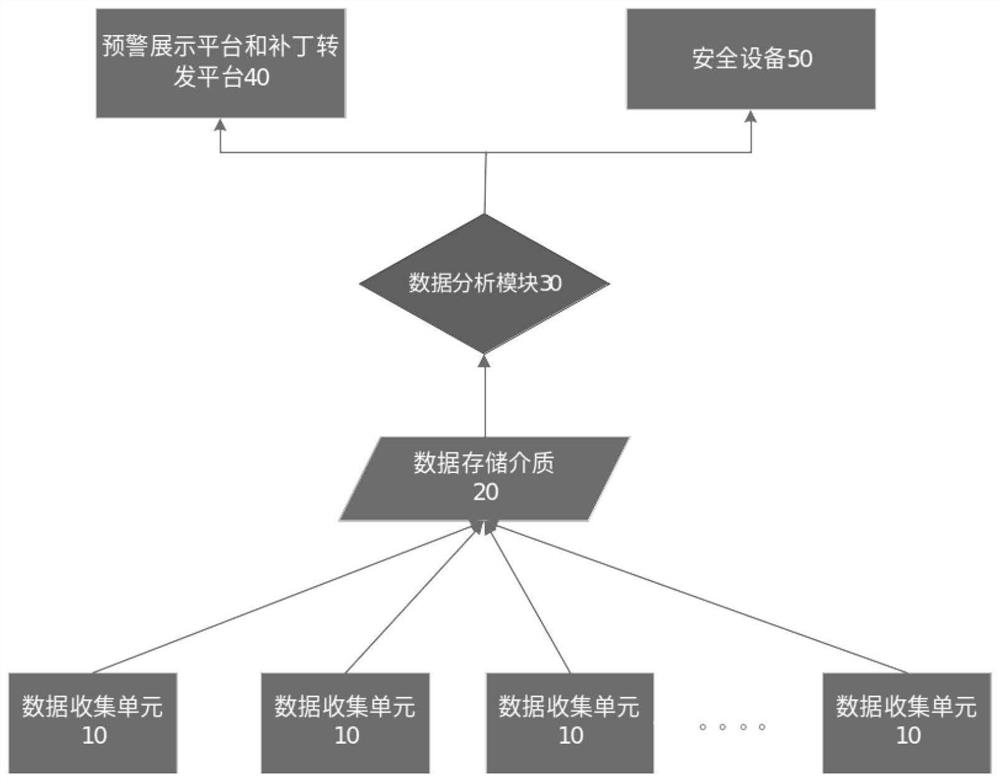
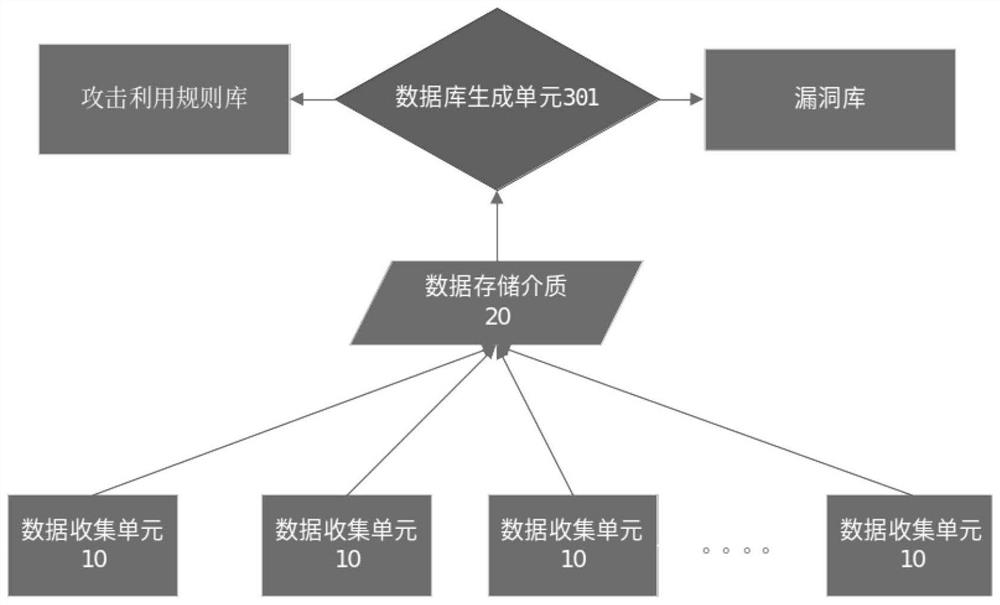
[0036] refer to figure 1 As shown, an embodiment of the vulnerability trend analysis and early warning method of the industrial control system of the present invention simulates and establishes a number of probes with core protocols in the industrial control system, and deploys the probes on the public network or in an internal network with a high degree of completion of the industrial Internet. network; the simulated industrial control system probe collects attack information interactively; the simulated industrial control system probe sends the collected attack information to the data analysis module, which is responsible for data analysis and vulnerability mining; data analysis ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com