Web application firewall system and computer storage medium
A web application and firewall technology, applied in the field of network security, can solve problems such as low efficiency, inability to exert the maximum performance of equipment, and performance redundancy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
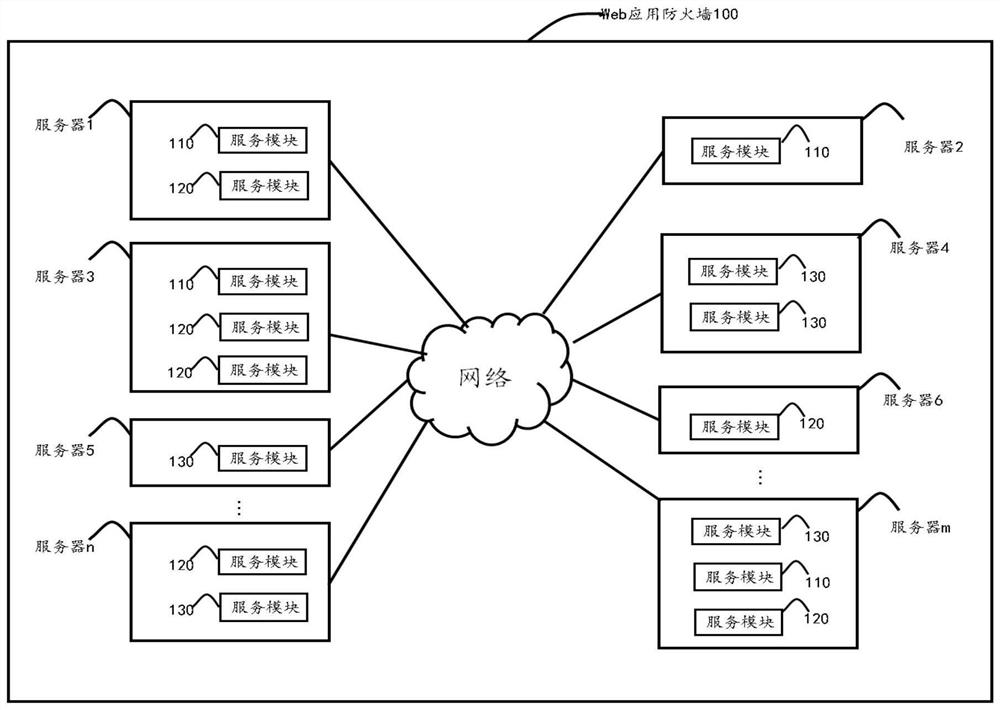
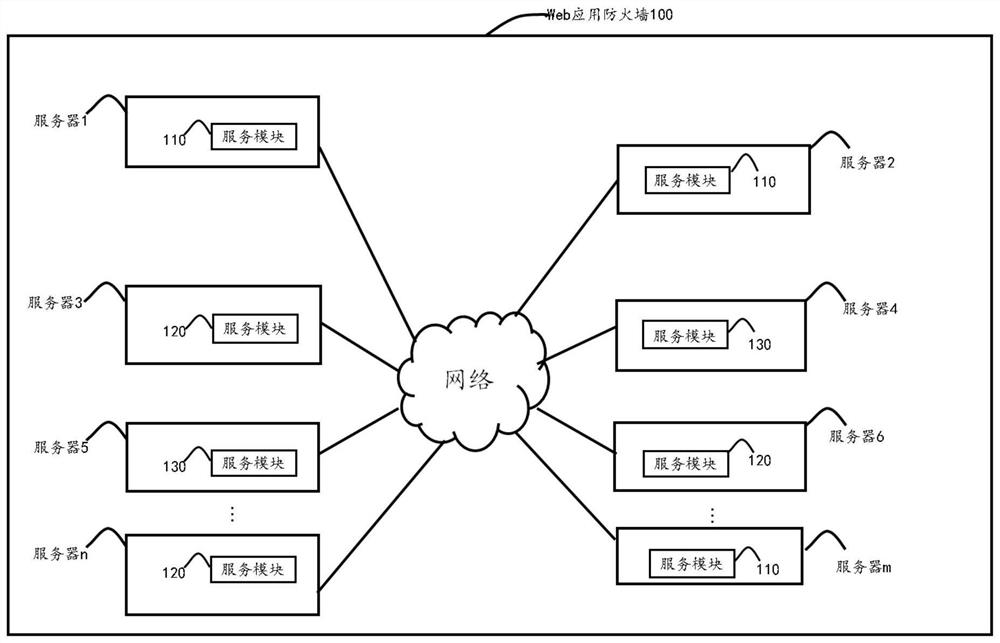
[0038] figure 1 is a schematic structural diagram of a firewall system according to an embodiment of the present invention, such as figure 1 As shown, the WAF system may include, but not limited to: a service module 110 for traffic forwarding, a service module 120 for traffic detection, and a service module 130 for traffic analysis.
[0039] Wherein, the service module 110 for traffic forwarding is used to obtain a user request, forward the request to the service module 120 for traffic detection, and perform a test according to the detection result returned by the service module 120 for traffic detection. The user request is processed. In this embodiment, the exemplary number of service modules 110 used for traffic forwarding is more than one, but the present invention is not limited thereto. According to the application environment of the firewall system, the firewall system can deploy any number of The service module 110 for traffic forwarding. In an optional implementati...
Embodiment 2
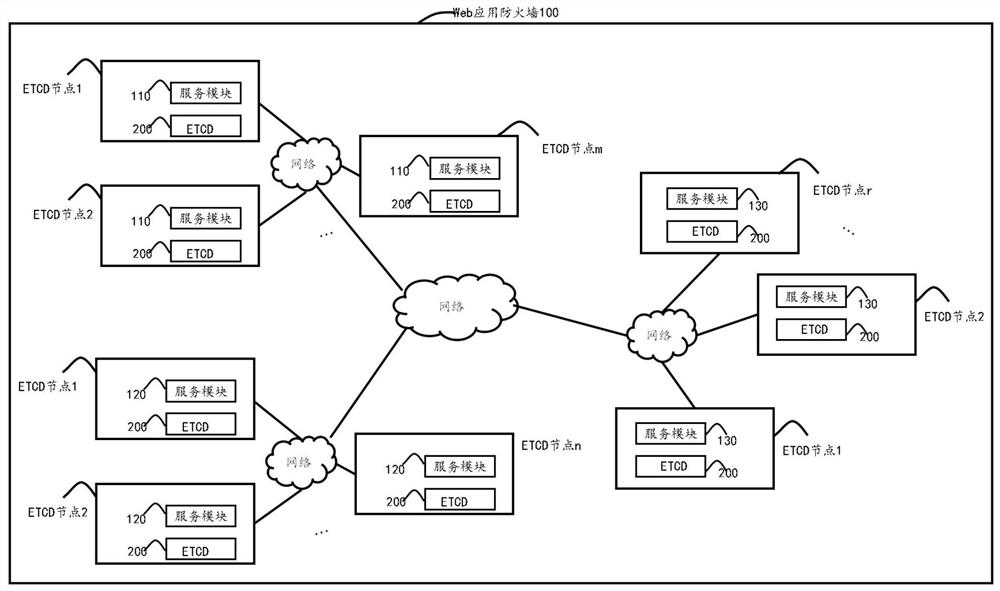
[0050] image 3 is an example of the firewall system according to the embodiment of the present invention, such as image 3 As shown, the firewall system described in the embodiments of the present invention has the architecture and modules described in the above embodiments, and also includes a distributed key-value storage system ETCD 200, which can be used to store all configuration information of the service module described above. Wherein, the configuration information of the service module may include but not limited to: node service type, node IP, node name, node ID, node information synchronization protocol channel. Among them, the node service types of the service modules with the same function are the same, and their node IPs are in the same network segment.
[0051] In this embodiment, the firewall system described in the implementation manner of the present invention performs distributed cluster management through the distributed key-value storage system ETCD. T...
Embodiment 3
[0056] Figure 4 is another example of the firewall system according to the embodiment of the present invention. Such as Figure 4 As shown, in addition to the modules and architecture described in any one of the above-mentioned embodiments, the firewall system described in the embodiment of the present invention also includes a basic platform module 300, which is used to manage the basic configuration information of the firewall system. The basic The configuration information may include configuration information of each service module stored in the distributed key-value storage system.
[0057] Optionally or further, the basic platform module 300 is also used for generating and updating service configurations of service modules. For example, generate Nginx configuration files based on site configuration.
[0058] Optionally or further, the basic platform module 300 is also used to provide high-availability support for each service module, and perform error recovery when t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com