Method for preventing burning data from being stolen by encrypting burning port
A data and port technology, which is applied in the field of MCU programming and data security, can solve data leakage and other problems, and achieve the effect of reducing costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
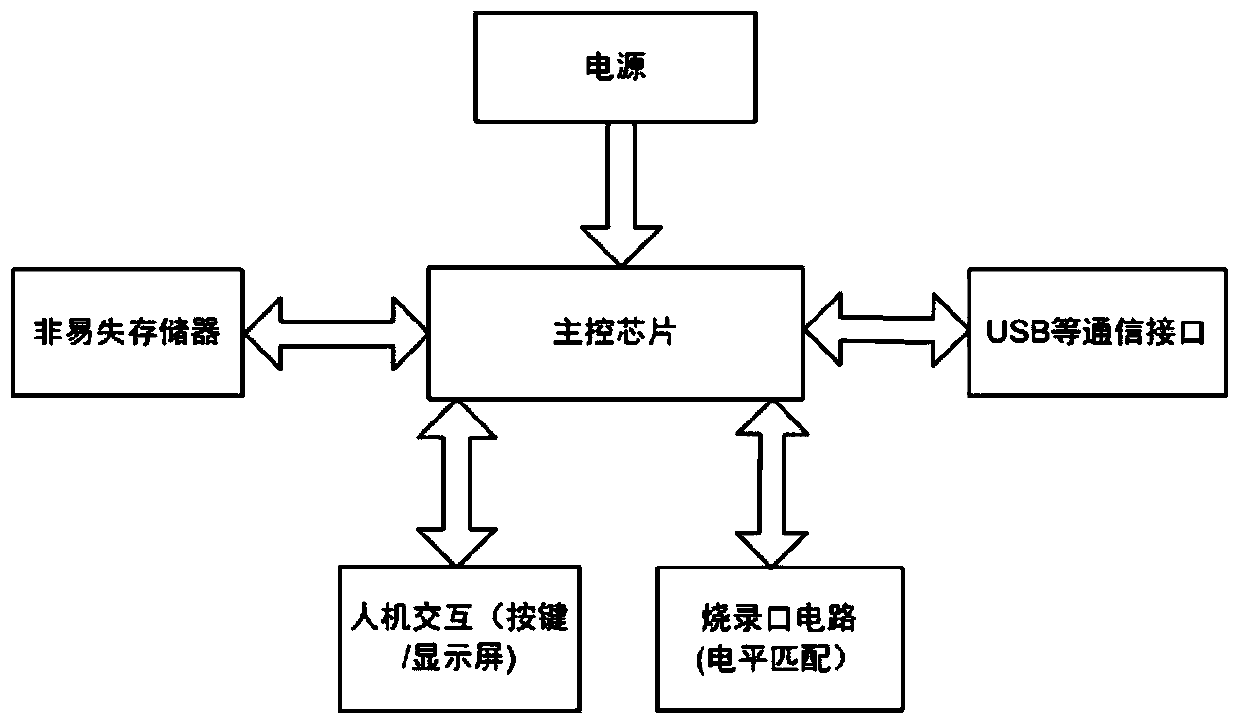
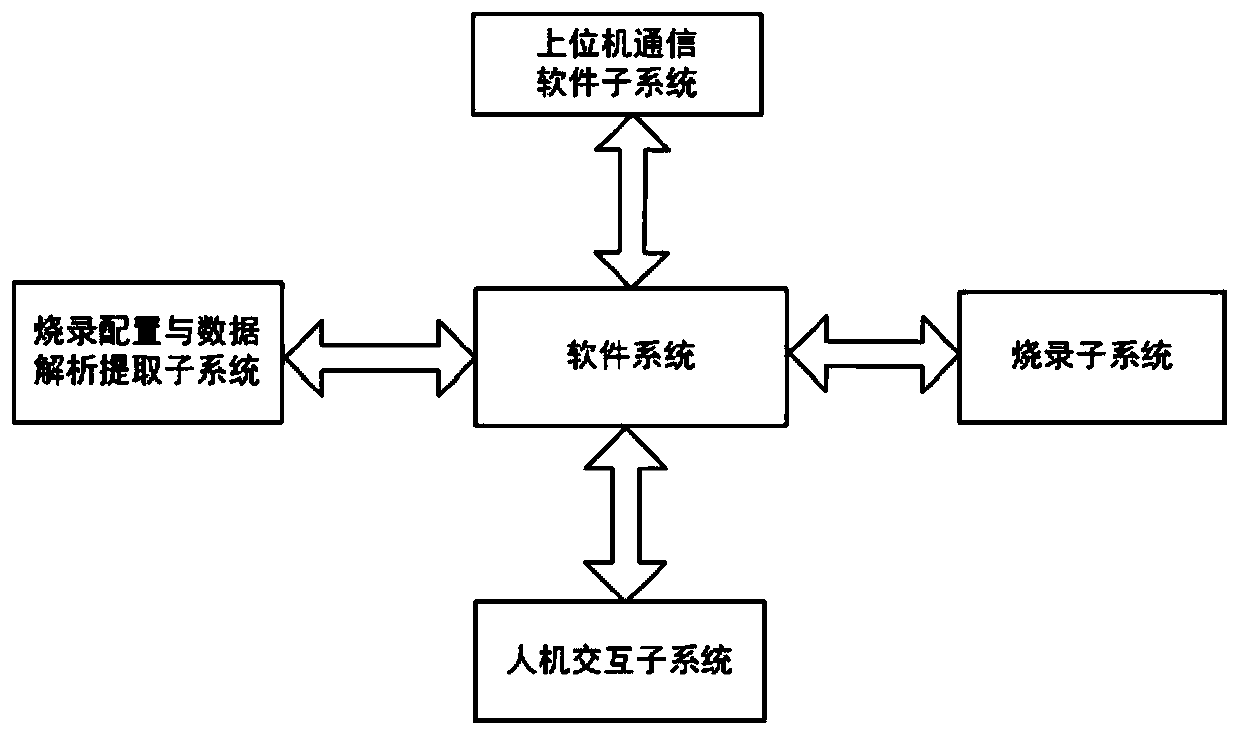
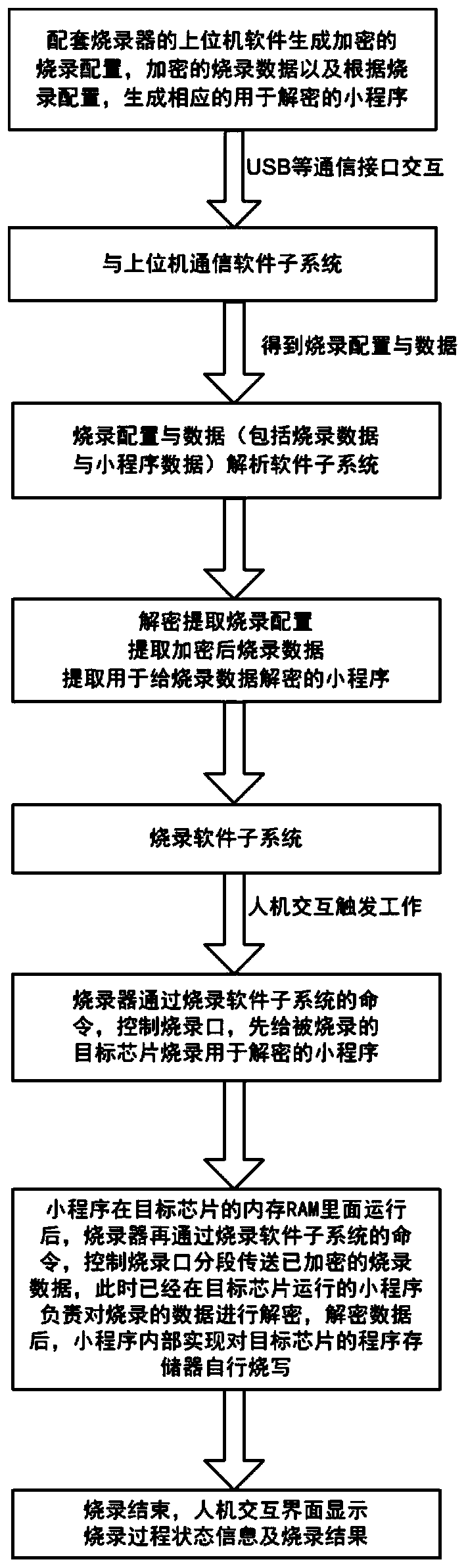
[0030] A method to prevent burning data from being eavesdropped and stolen by encrypting the burning port, the specific steps are as follows:
[0031] 1. Open the host computer software running the supporting burner in the host computer;
[0032] 2. The upper computer software used by the supporting burner generates encrypted burning configuration, encrypted burning data and generates a corresponding applet for decryption according to the burning configuration;
[0033] 3. The host computer sends the encrypted programming configuration and programming data, and the decrypted applet to the programmer through USB and other communication interfaces, and the programming configuration and data (including programming data and applet data) inside the programmer ) The analysis and extraction subsystem will correctly analyze and extract the programming configuration, programming data, and store the small program in the internal memory of the chip or the external non-volatile storage. A...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com