Network Information Propagation Method Based on Length Constraint and Non-repeated Path
A network information and length-constrained technology, applied in the direction of data exchange network, transmission system, digital transmission system, etc., can solve the problems of inaccurately describing the trust relationship between nodes, increasing the uncertainty of the relationship between nodes, and destroying the network topology. Achieve the effects of increasing uncertainty, improving usability, and ensuring structural properties
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
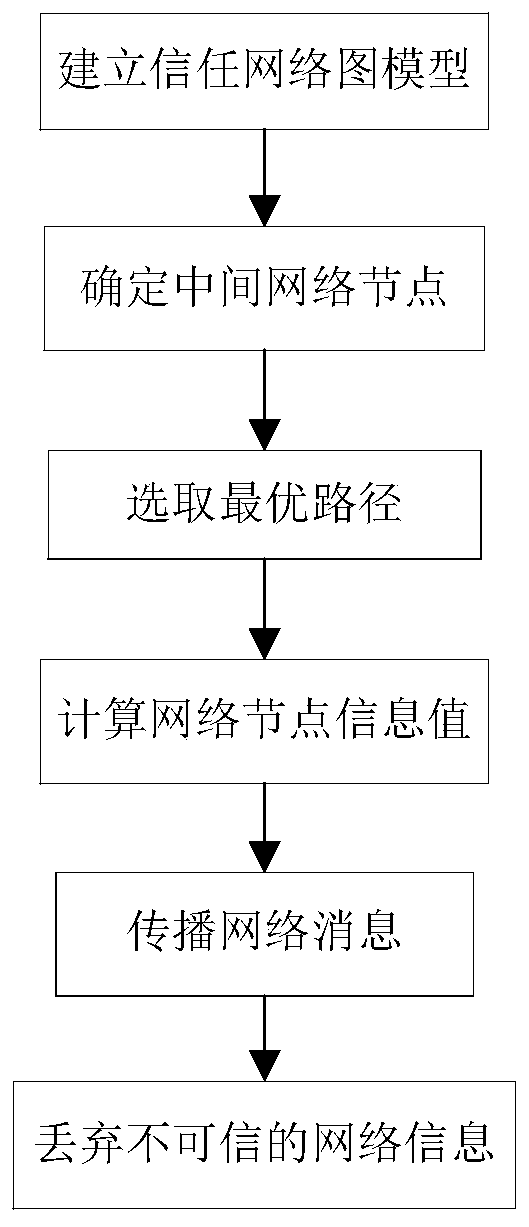
[0053] The present invention will be further described below in conjunction with the accompanying drawings.
[0054] refer to figure 1 , to further describe in detail the specific steps for realizing the present invention.
[0055] Step 1, establish a trust network graph model.
[0056] Read in a dataset with at least 300 network nodes.
[0057] Abstract the data read into the dataset into a directed graph.
[0058] The directed graph is G 1 =(Y,E), where Y represents the directed graph G 1 A collection of all network nodes in , each network node represents a user in the network, E represents a directed graph G 1 The set of edges of the network nodes in the network, each edge represents the connection relationship between any two network nodes in the network.
[0059] The network adjacency matrix generation method is adopted to generate the adjacency matrix corresponding to the directed graph.
[0060] The steps of the method for generating the network adjacency matrix ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com