Intelligent Analysis Method of Intranet Security Threat
An intelligent analysis and security technology, applied in the direction of secure communication devices, digital transmission systems, complex mathematical operations, etc., can solve problems such as model degradation, logs are easy to be tampered, and cannot be used in combination, so as to improve security and improve analysis efficiency , the effect of improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
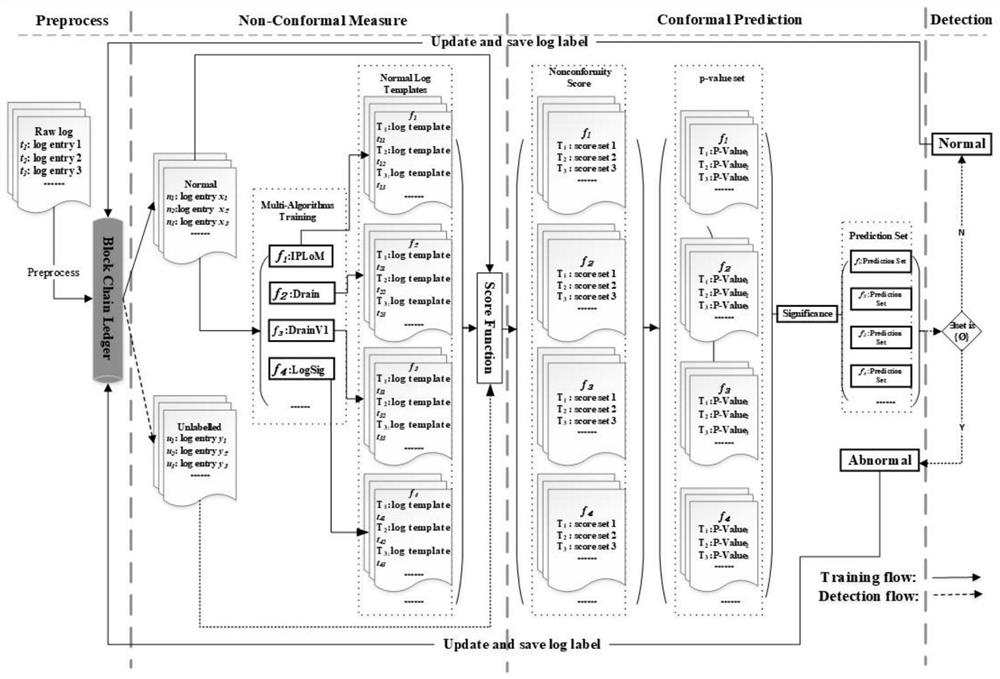
[0055] The present invention takes the detection of abnormal logs as an example for specific description. Any log parsing algorithm that obtains a log template set by inputting a set of original log streams can be used in this method, and the method flow is as follows: figure 1 In this embodiment, four log parsing algorithms, IPLoM, Drain, DrainV1, and LogSig, are used as examples, and the specific introduction is as follows:
[0056] IPLoM is a log parsing algorithm. This algorithm is divided into four steps when parsing logs, and all logs are input at the beginning. The first step is to divide all original logs into different groups according to the length; the second step is to continue grouping the original logs in groups with the same log length. Count all words in the same position of all log records, find the position with the least unique words, and classify according to these unique words. Group raw logs with the same unique word into a group. The third step will o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com