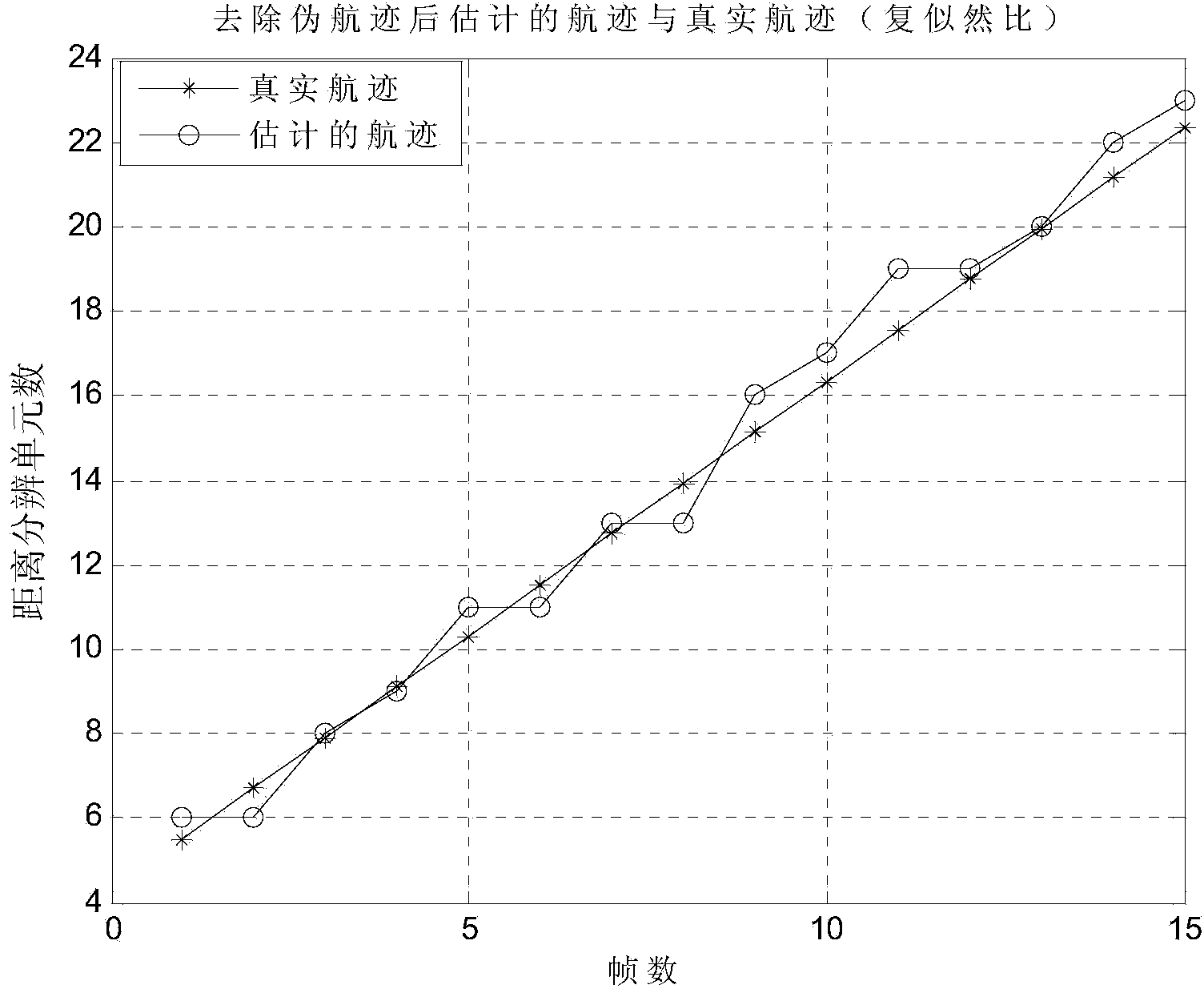Patents
Literature
242results about How to "Avoid performance loss" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
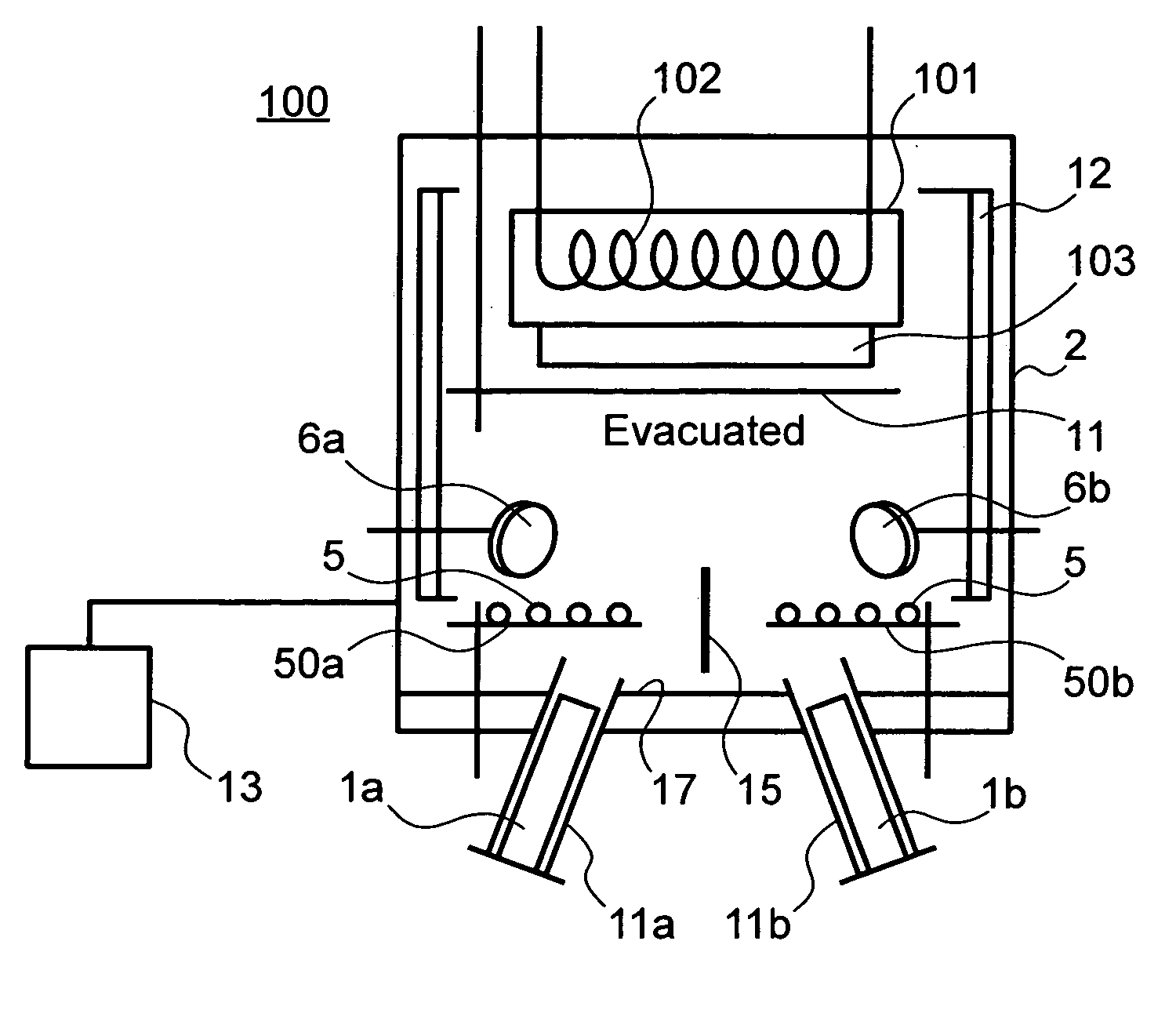
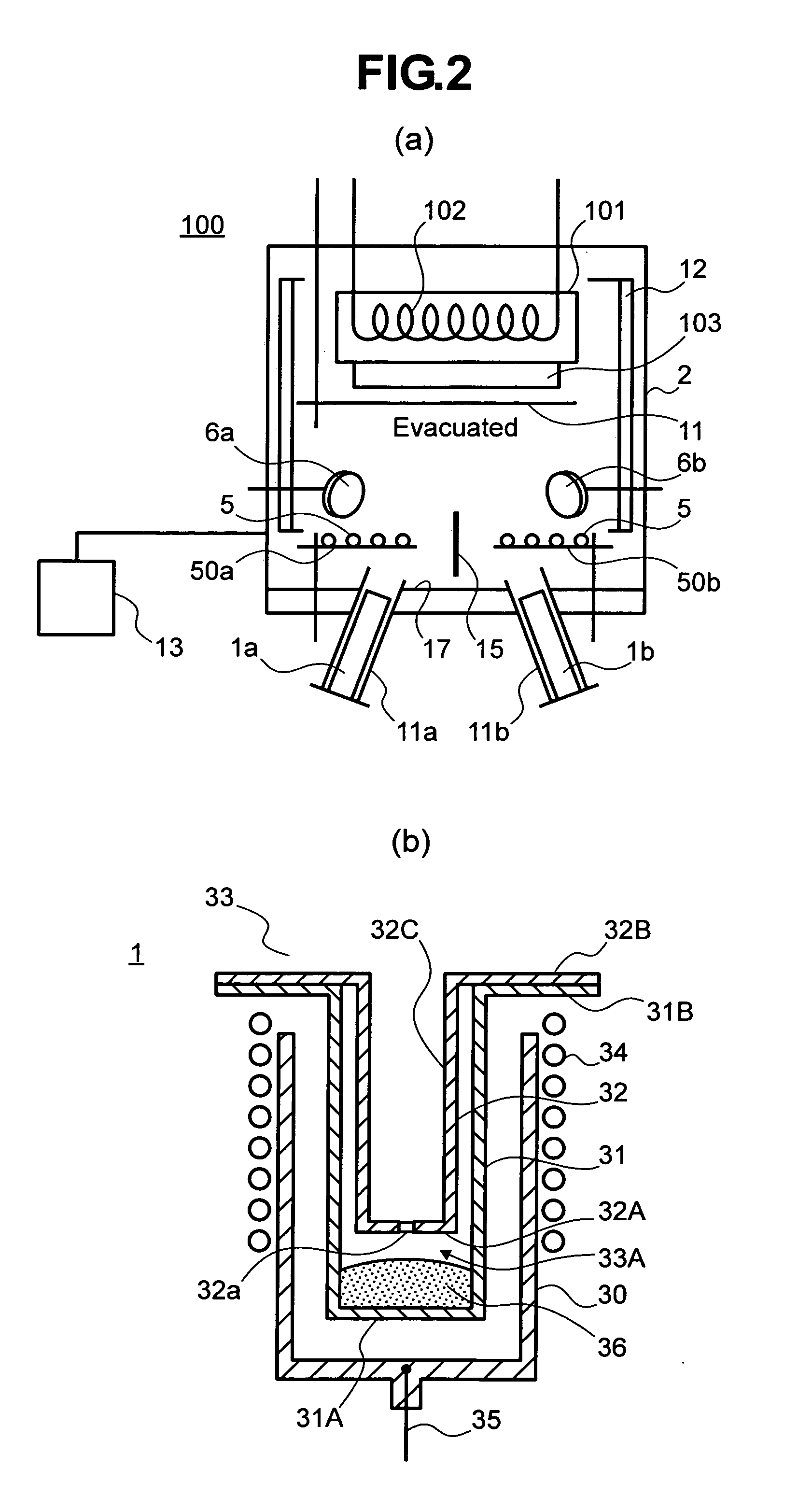
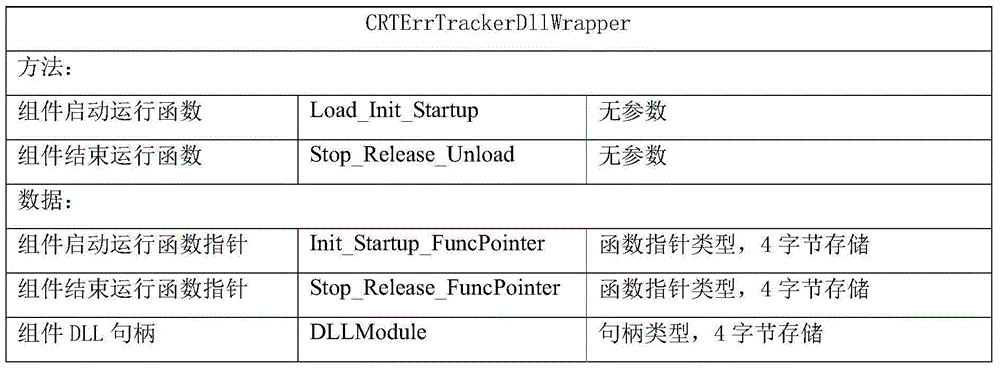
Vapor deposition crucible, thin-film forming apparatus comprising the same, and method of producing display device
InactiveUS20070178225A1Material is facilitatedPrevent solidificationSolid-state devicesVacuum evaporation coatingVena contracta diameterGas phase
For lasting stable vapor deposition of a material for a long term, the present invention provides the vapor deposition crucible comprising an evaporation chamber defined by a container part of the material and an orifice plate controlling vapor pressure of the material evaporated therein, and a pressure-controlling chamber defined in a space between the orifice plate and a discharge plate through which the material is discharged to the exterior of the vapor deposition crucible. A protrusion extending outwardly from the pressure-controlling chamber and having a second opening on its distal end may be provided on the upper surface of the discharge plate, and a heater may be provided on the side surface of the protrusion to oppose the side surface of the protrusion with an insulation mechanism provided at a position higher than the heater but lower than the second opening. In the vapor deposition crucible, temperature of the pressure-controlling chamber may be kept higher than that of the evaporation chamber by the other heaters.
Owner:HITACHI DISPLAYS
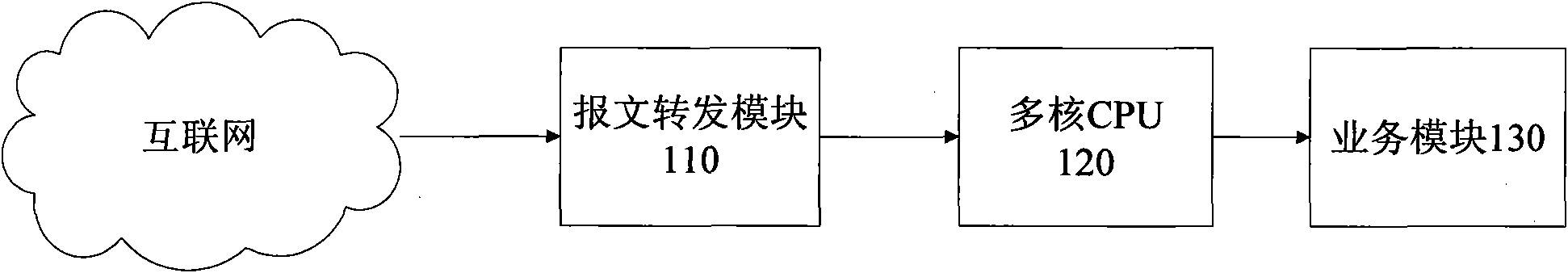
Message retransmission method and system based on multi-core architecture
InactiveCN101964749AImplement independent featuresIncrease profitData switching networksComputer hardwareNetwork packet
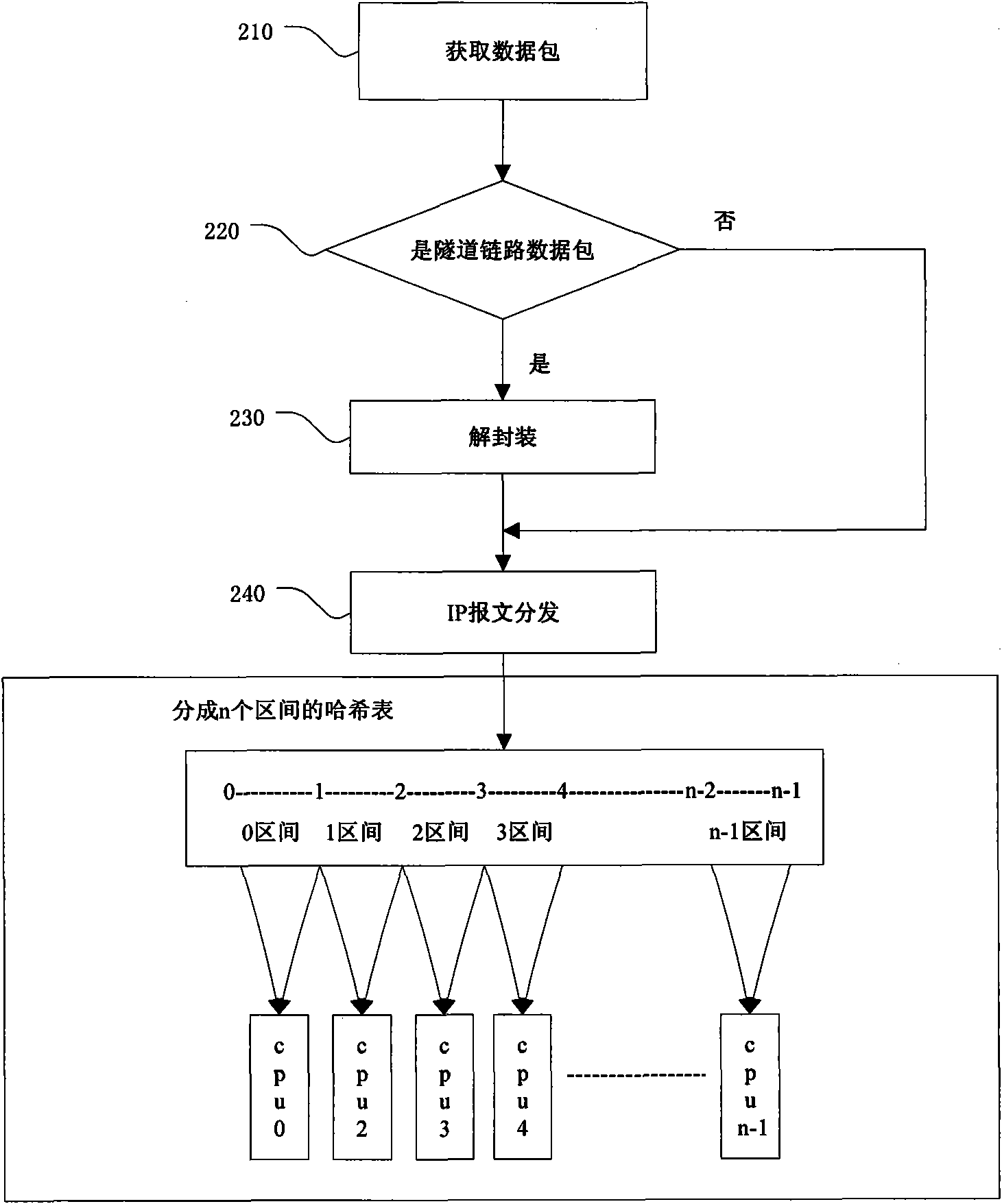
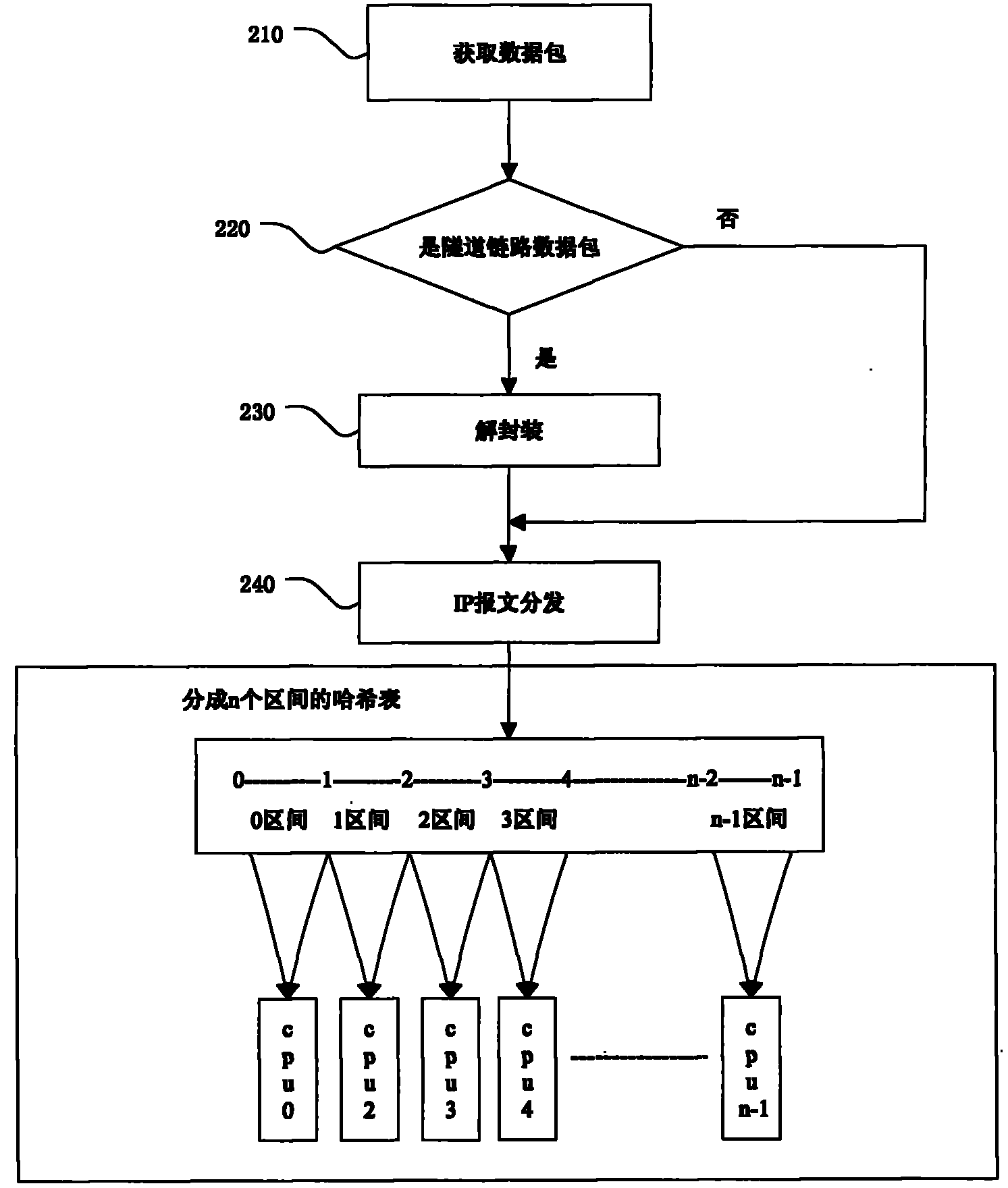
The invention relates to a message retransmission method and a system based on a multi-core architecture. The method comprises the following steps: acquiring a data packet in the Internet; when the data packet is a tunnel link data packet, decapsulating the data packet to obtain an IP data packet; and carrying out Hash operation on the quintuple of the IP data packet, computing according to the obtained Hash value and Hash table size thereof and the number of CPUs in the multi-core CPU to obtain the corresponding CPU, labeling the Hash value into the IP data packet, and transmitting the labeled IP data packet to the CPU. The invention increases the utilization rate of fixed network equipment in the wireless Internet, realizes lock-free design of shared resources, and is applicable to the wireless Internet.
Owner:BEIJINGNETENTSEC
Intelligent resource optimization method of container cloud platform based on load prediction
ActiveCN108829494AReduce overheadReduce performanceResource allocationTransmissionLoad forecastingResource utilization
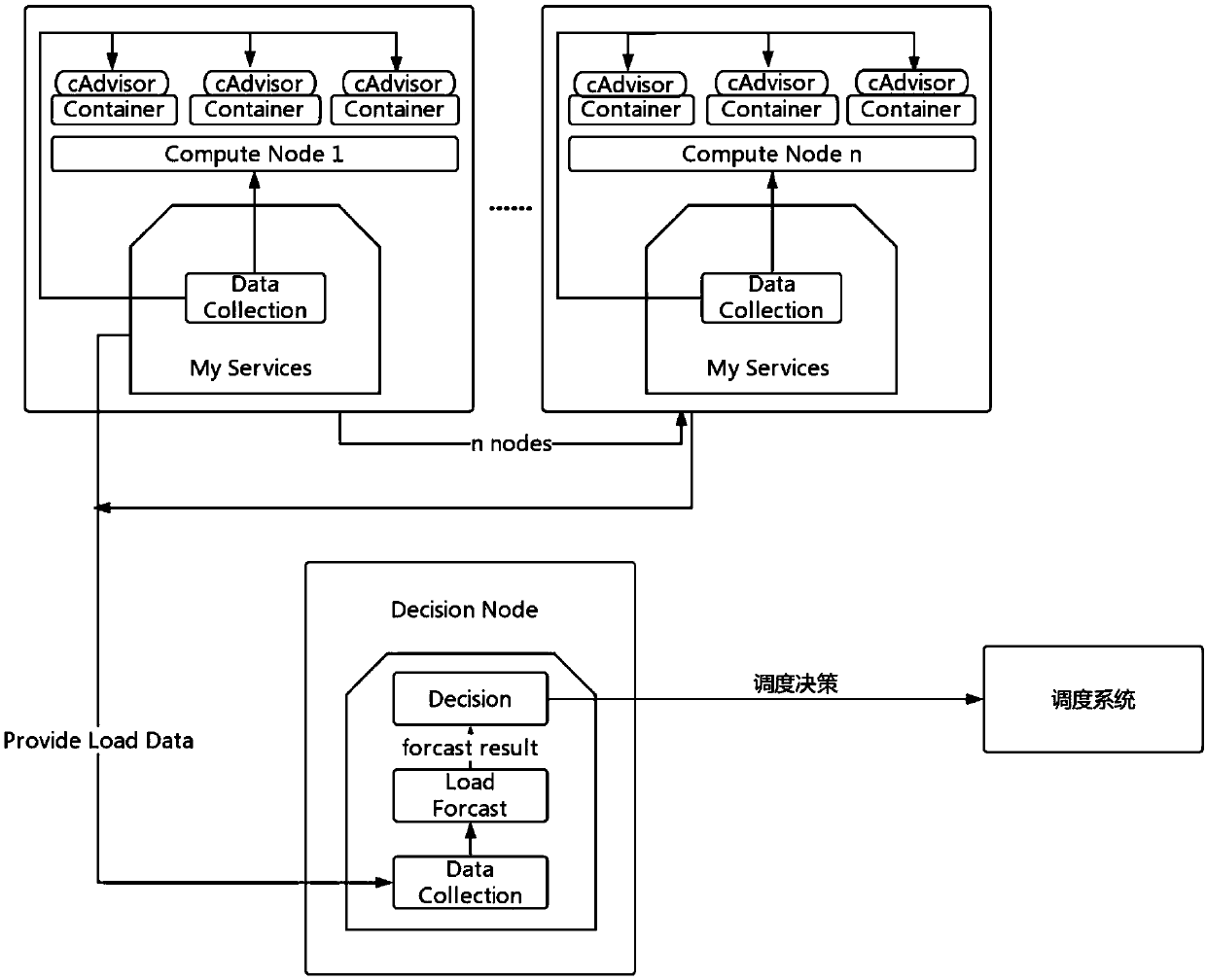
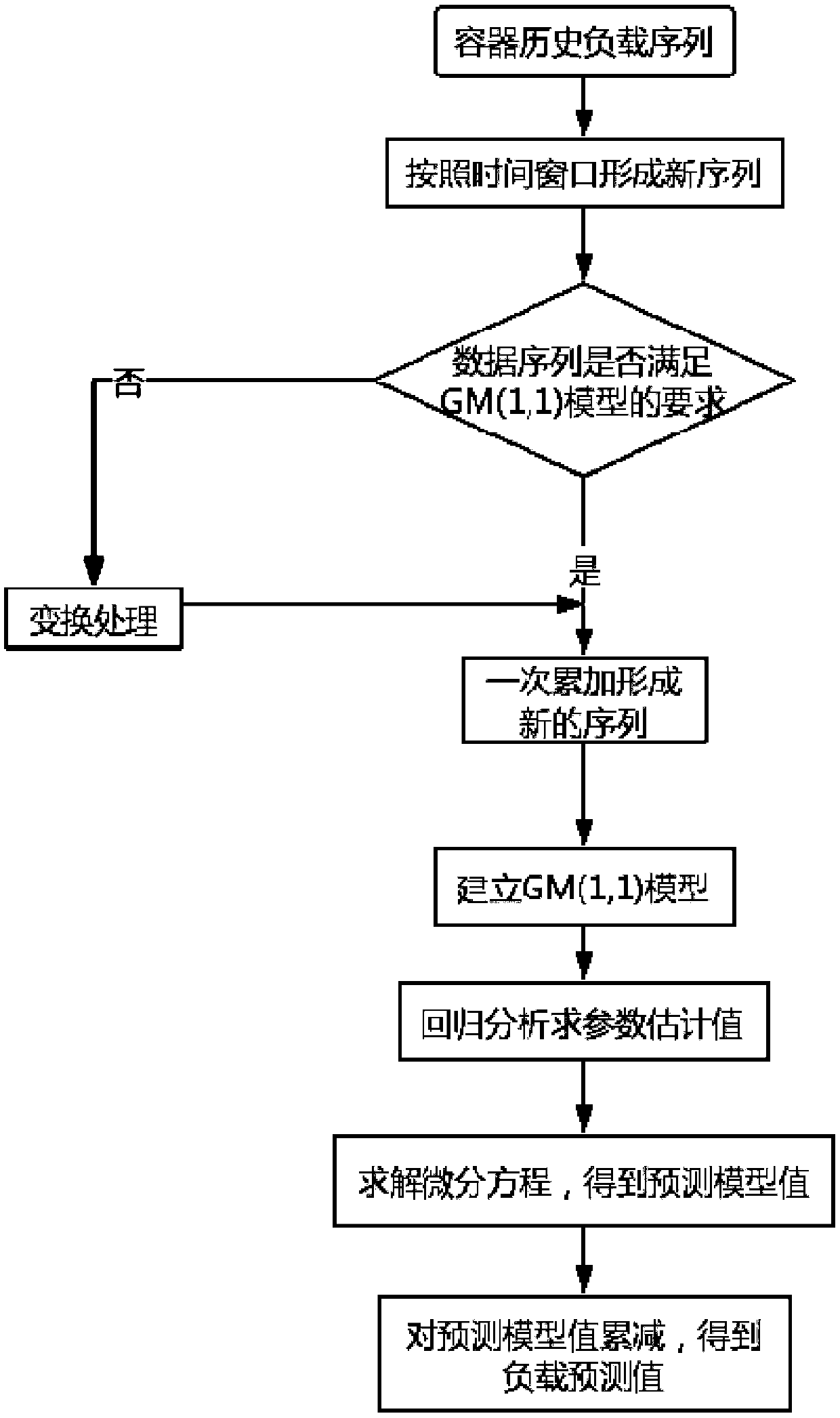
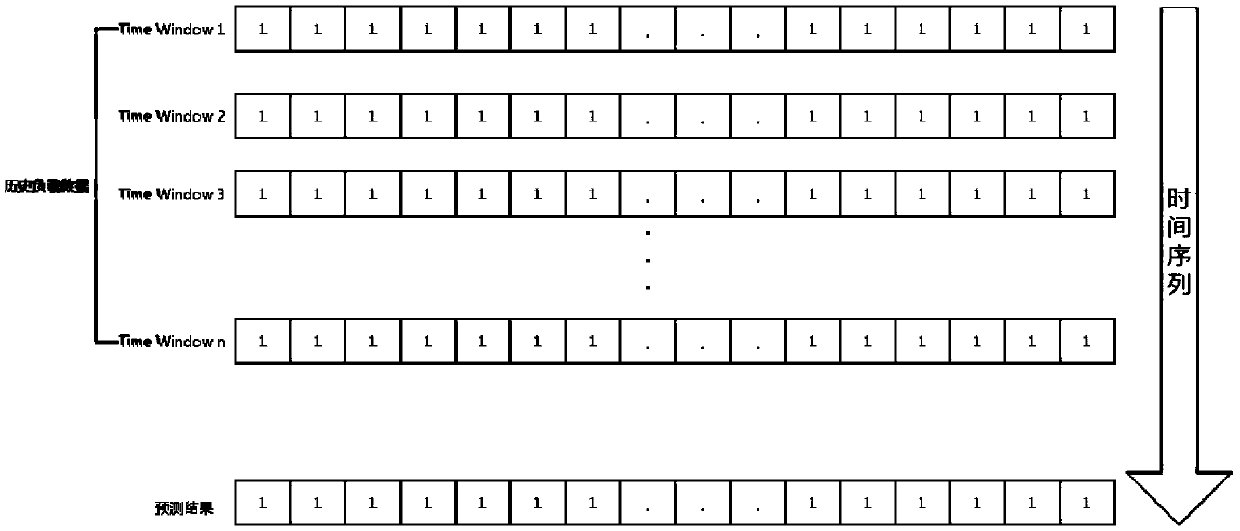
The invention discloses an intelligent resource optimization method of a container cloud platform based on load prediction, and belongs to the field of container cloud platforms. The method comprisesthe following steps of: based on a grayscale model, predicting the load condition of the next time window of each container instance according to the historical load of the container instance; judgingwhether the load of a node is too high or too low according to the load prediction value of all containers on each physical node; then executing the corresponding scheduling algorithm, migrating somecontainers on the node with over high load to other nodes, so that the load of the node is in a normal range; migrating all container instances on the node with over low load to other nodes so that the node is empty. According to the invention, aiming at the problem that the resource utilization is not balanced and the resource scheduling is delayed in a prior data center, load forecasting analysis is introduced, the load of the data center is scheduled and optimized in advance, the performance loss caused by the over high load of the node and the low resource utilization rate caused by the over low load are avoided, thereby improving the resource utilization efficiency of the platform.
Owner:杭州谐云科技有限公司
Management method and device of operation systems in embedded system
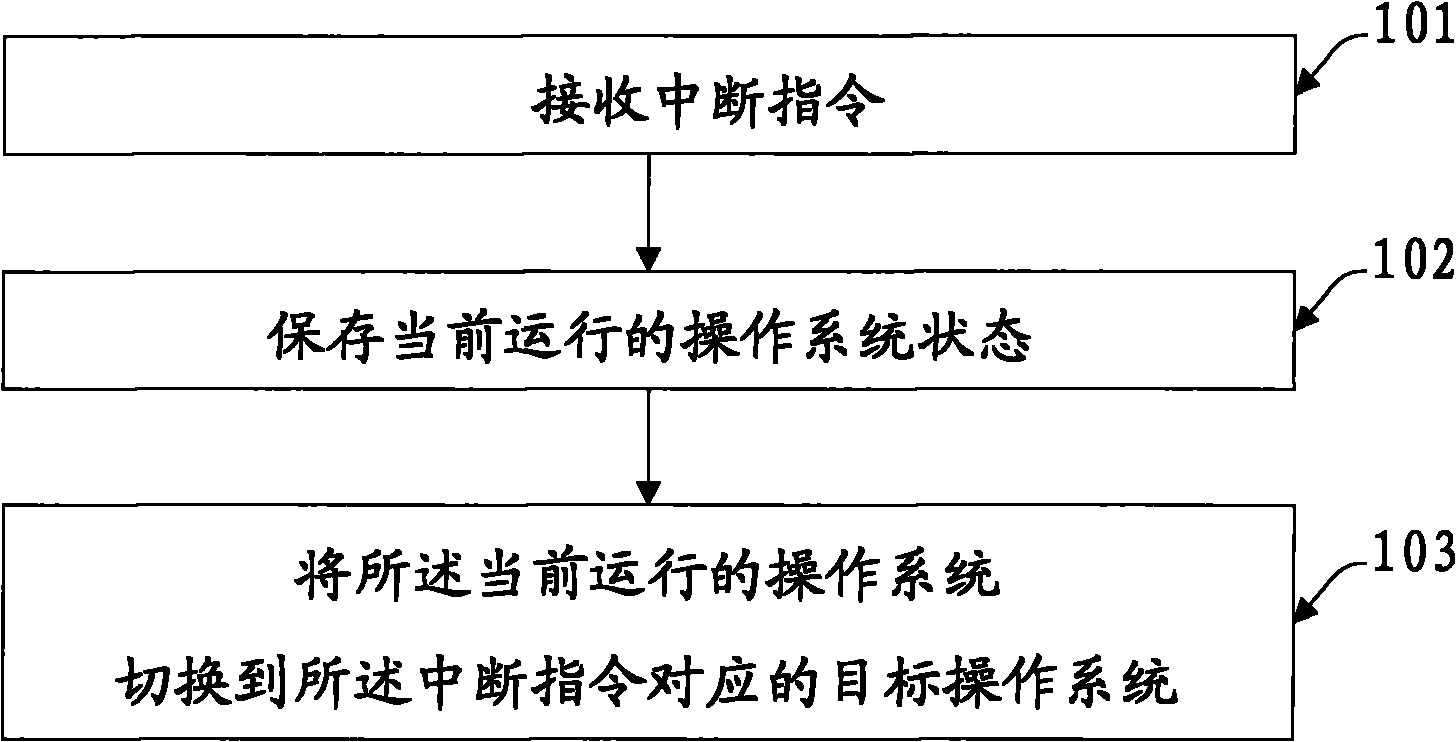
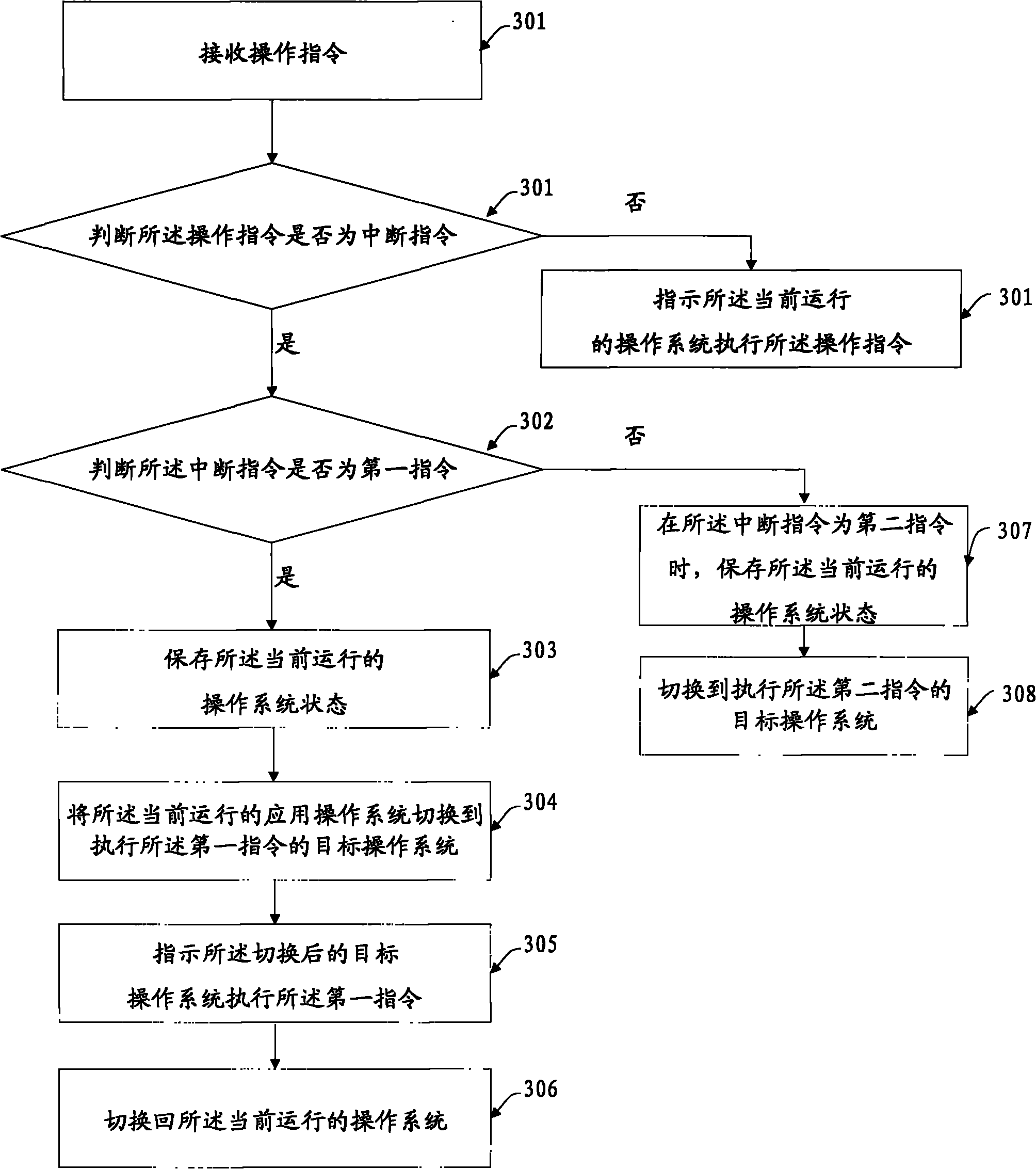
InactiveCN101782861AHigh complexityReduce complexityProgram initiation/switchingOperational systemEmbedded system
The invention discloses a management method and a device of operation systems in an embedded system, which relate to the field of mobile communication and solve the problems of larger performance loss and higher product complexity caused when a plurality of operation systems run on a single CPU in the prior art. The embedded system in the embodiment comprises at least two operation systems. The method comprises the following steps of: receiving an interrupt instruction; storing the states of the operation systems which run currently; and switching the operation systems which run currently to target operation systems corresponding to the interrupt instruction. The method is mainly applied to the field of the mobile communication.
Owner:HUAWEI DEVICE CO LTD
Method and device suitable for screen direction switching in video call
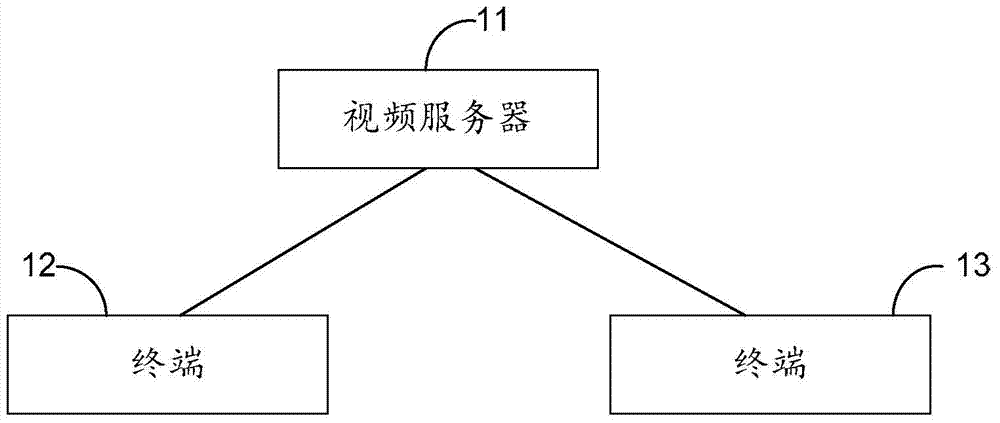
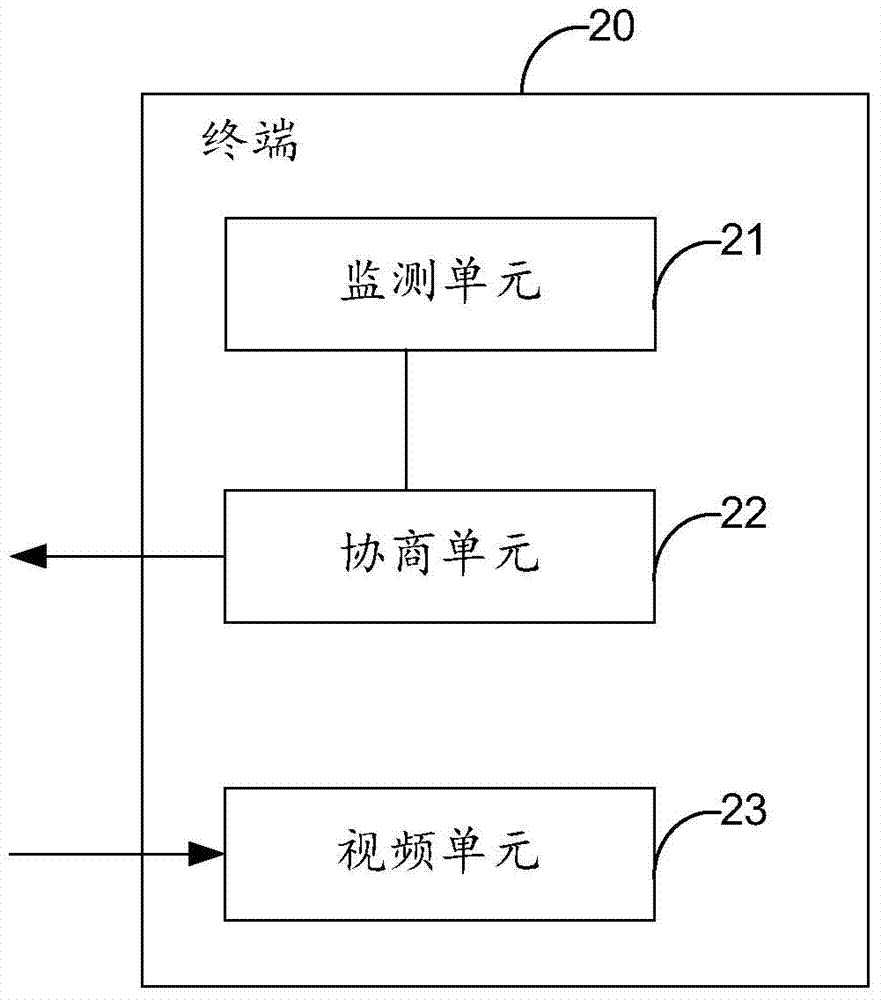
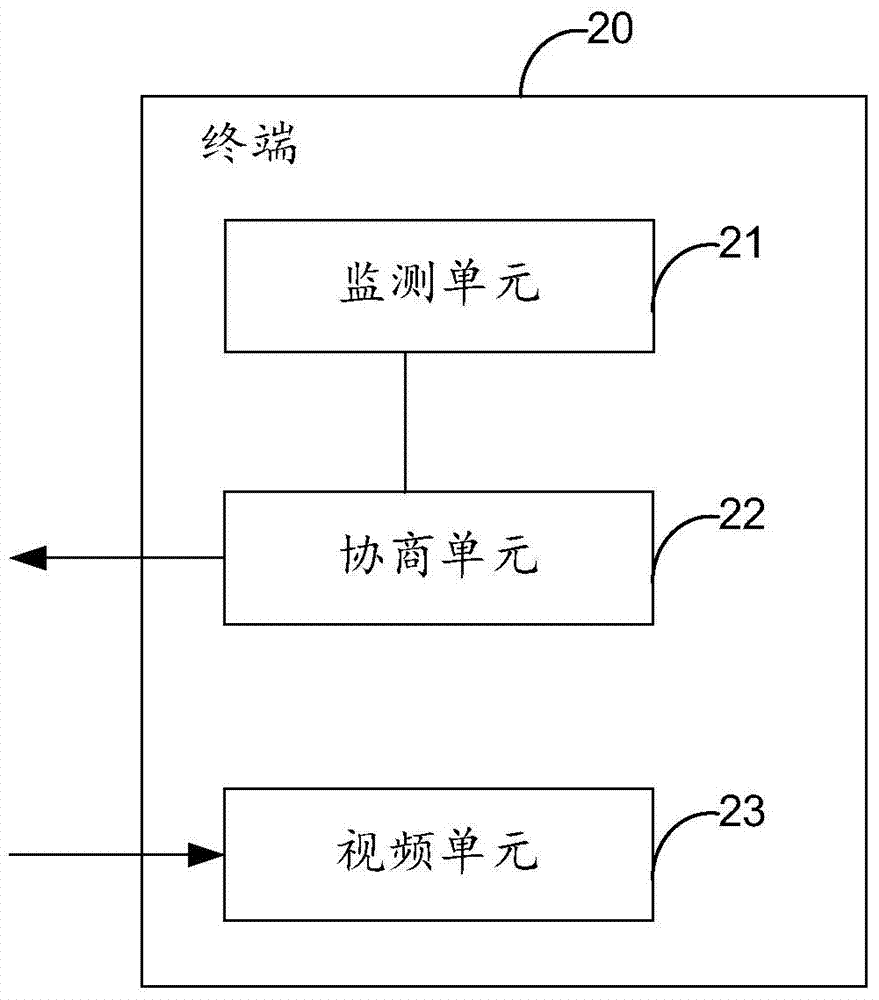
InactiveCN103763505AImprove call qualityAvoid performance lossTelevision conference systemsDevices with sensorComputer terminalVideo quality
The embodiment of the invention provides a method and device suitable for screen direction switching in a video call. The method includes the steps that in the process that a first terminal and a second terminal have the video call, and the first terminal monitors screen direction switching of the first terminal; after screen direction switching of the first terminal is monitored, a screen direction after being switched is sent to the second terminal; video stream sent by the second terminal according to video requirements corresponding to the screen direction is received. By means of the method and device, video quality can automatically adapt to screen direction switching of a terminal.
Owner:HUAWEI TECH CO LTD
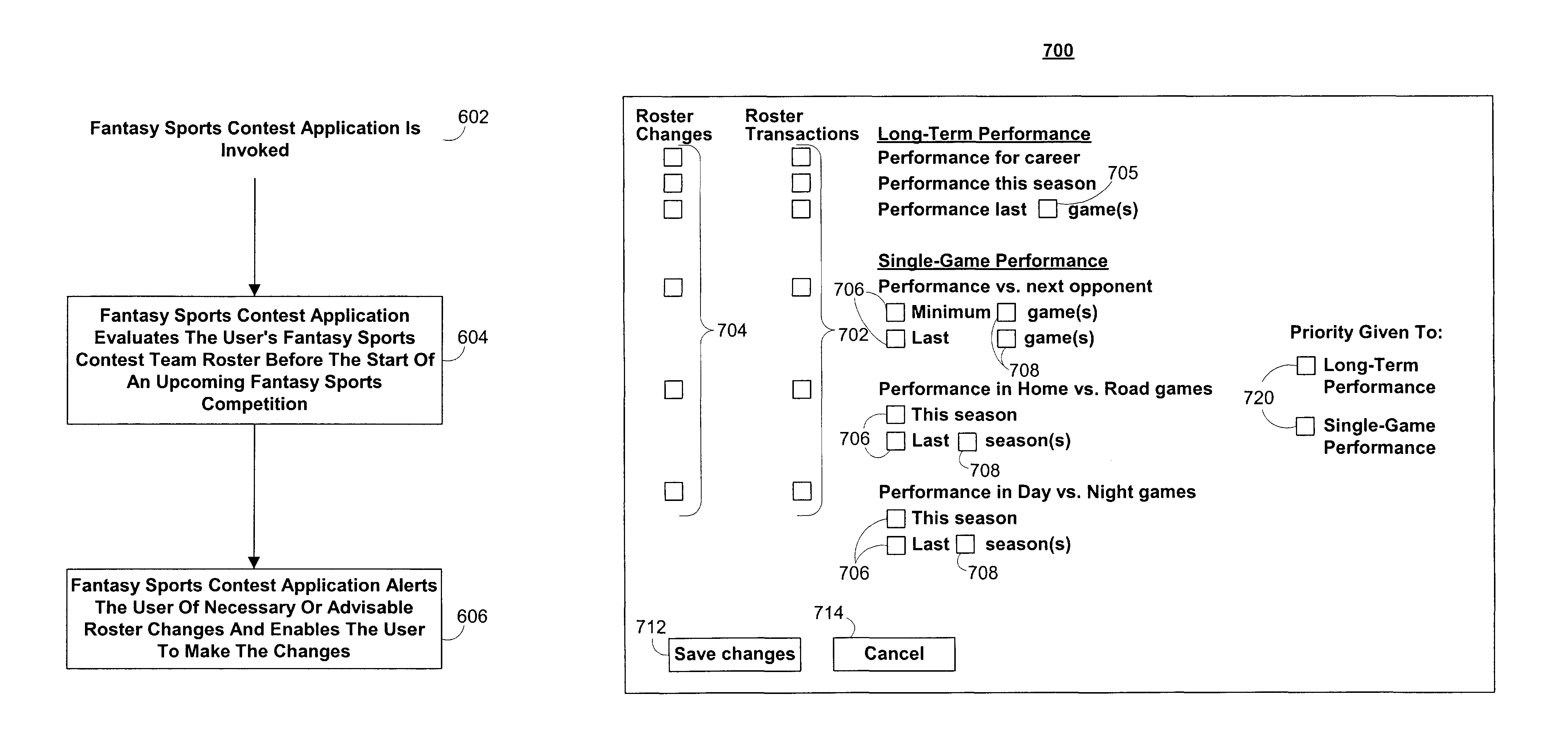
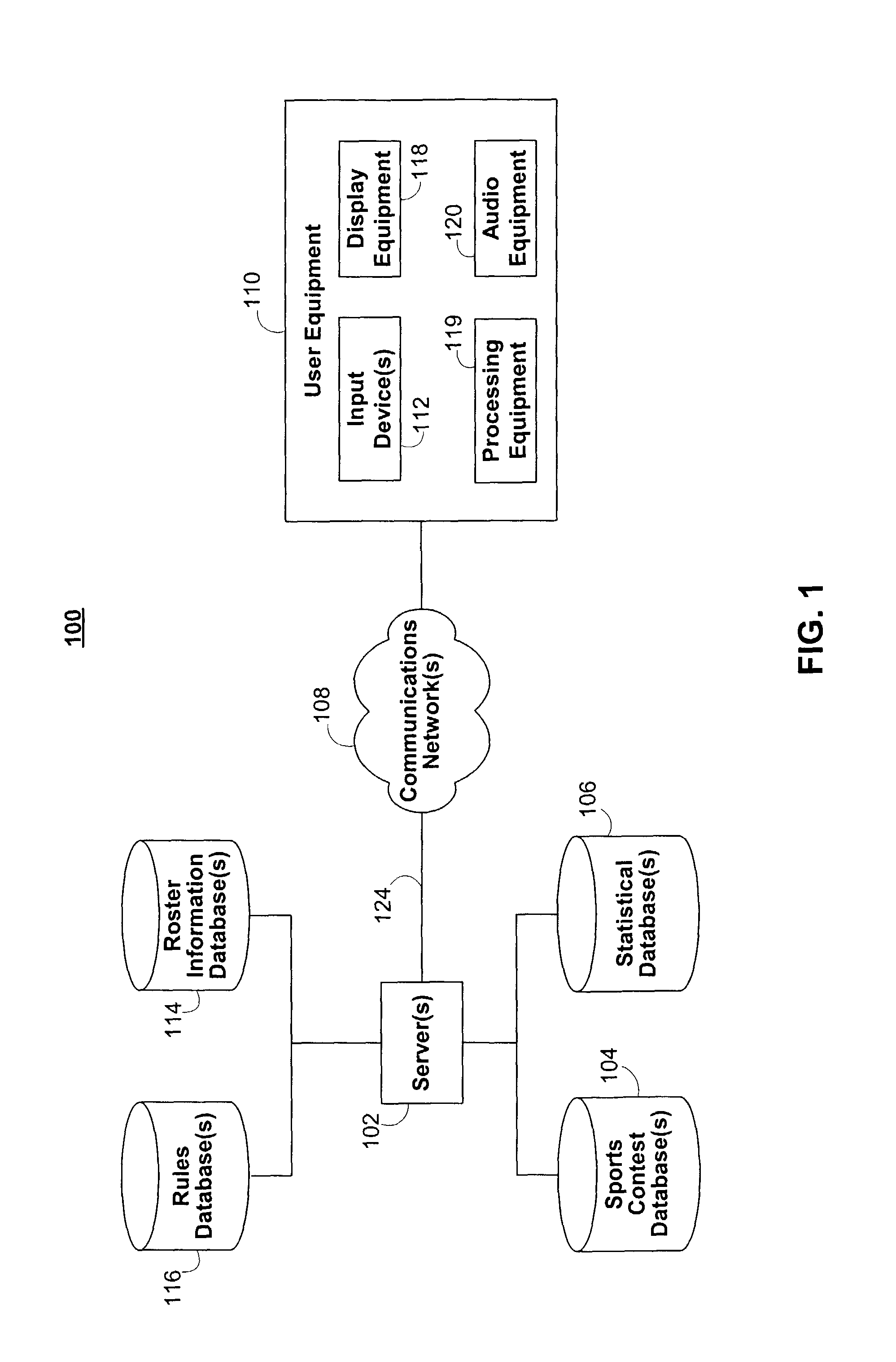
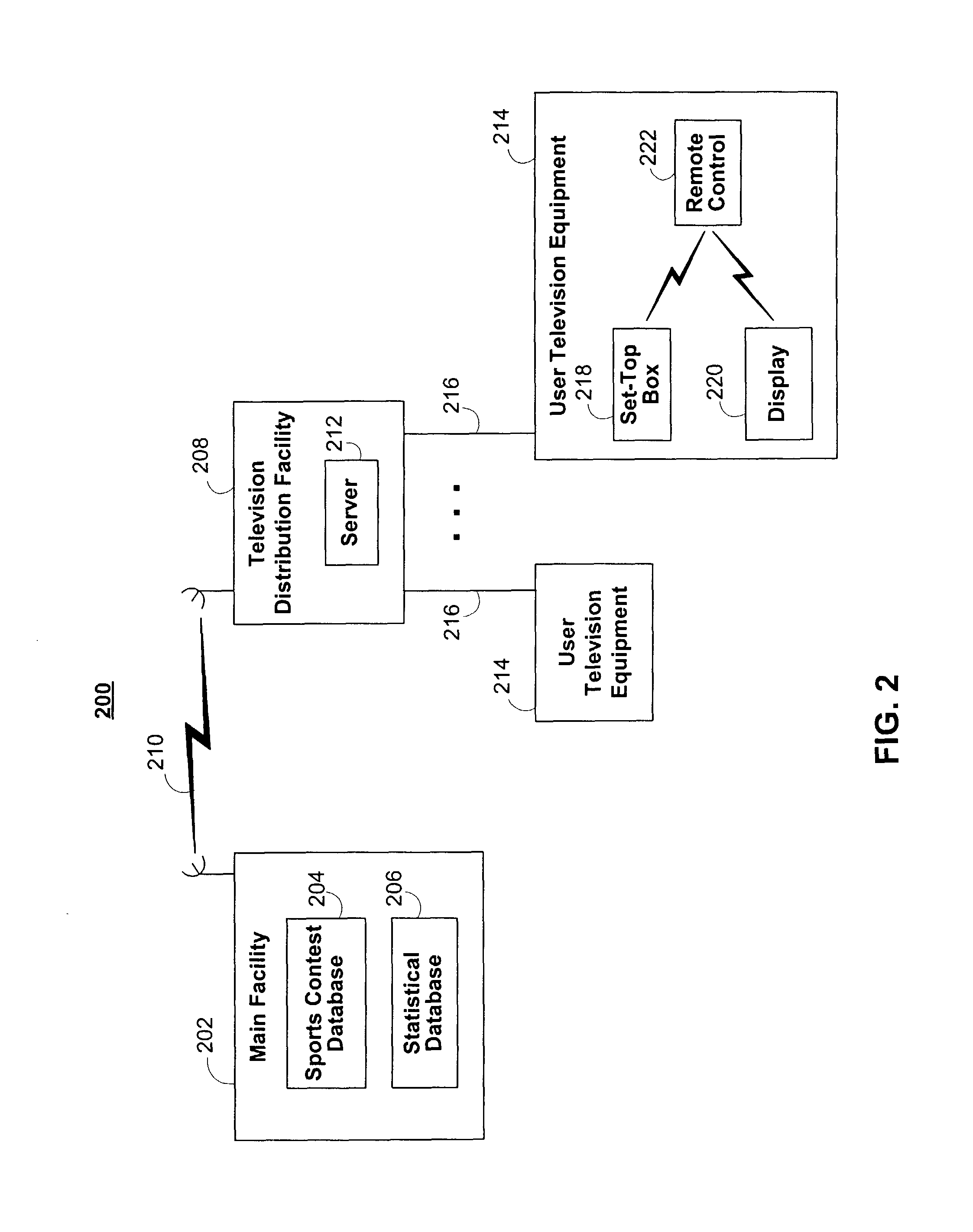
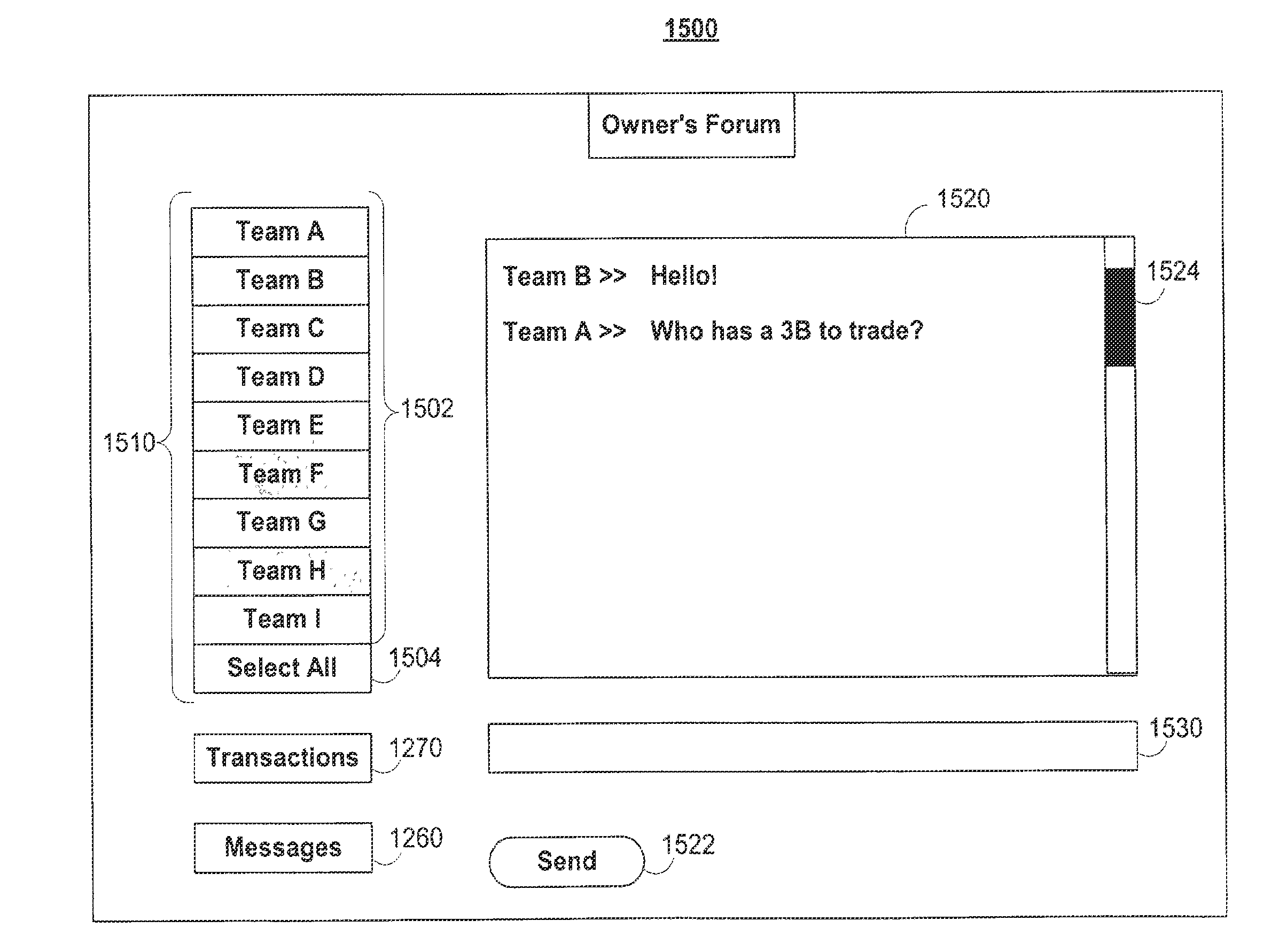
Systems and methods for roster management in fantasy sports contest applications
ActiveUS8509929B1Improved roster management featureAdd featureApparatus for meter-controlled dispensingVideo gamesEngineeringTeam Roster
The fantasy sports contest application of the present invention alerts the user of necessary roster changes before an upcoming fantasy sports competition. The fantasy sports contest application may evaluate the user's team roster before an upcoming fantasy sports competition to ensure that all roster spots on the team roster are filled with athletes available for real-life competitions. The fantasy sports contest application may also identify roster changes and roster transactions that may be beneficial to a user's fantasy sports contest team roster.The fantasy sports contest application may recommend roster changes and roster transactions to the user by evaluating the performance of athletes using performance criteria. The performance criteria can be based on the past performance of athletes, either overall, or for certain situations. The performance criteria may be predefined by the system, user-editable, or any suitable combination thereof.
Owner:ROVI TECH CORP
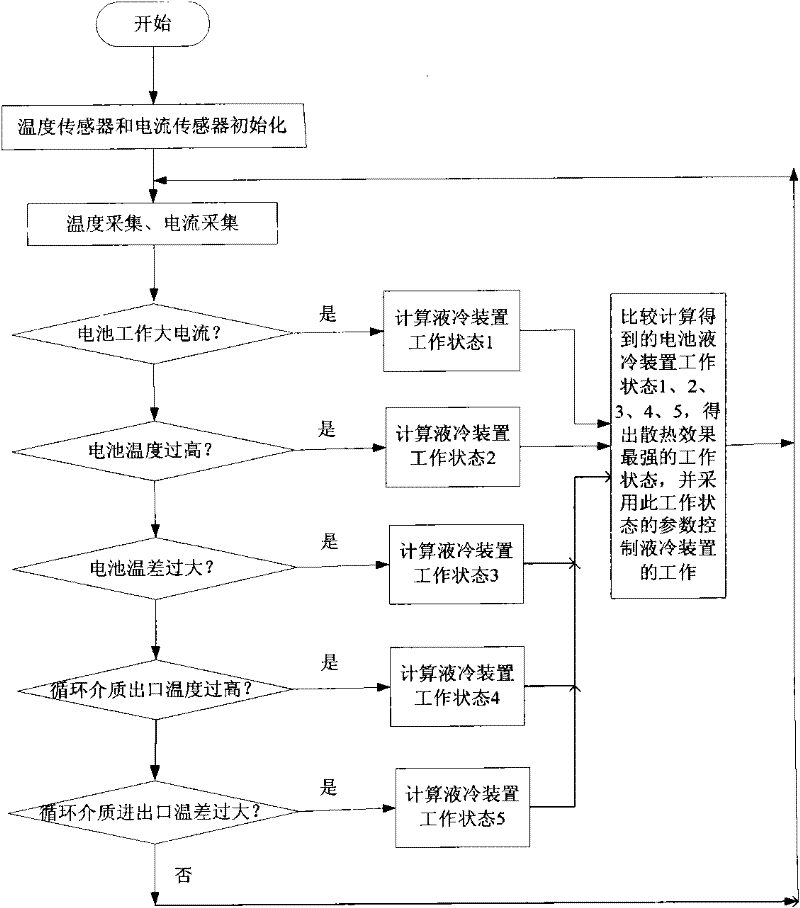
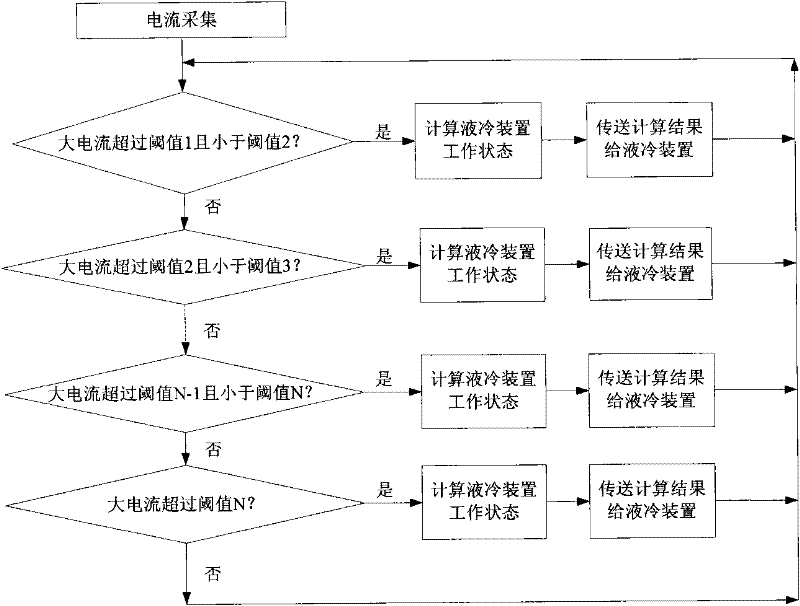
Liquid cooling temperature control and management method of power lithium ion battery
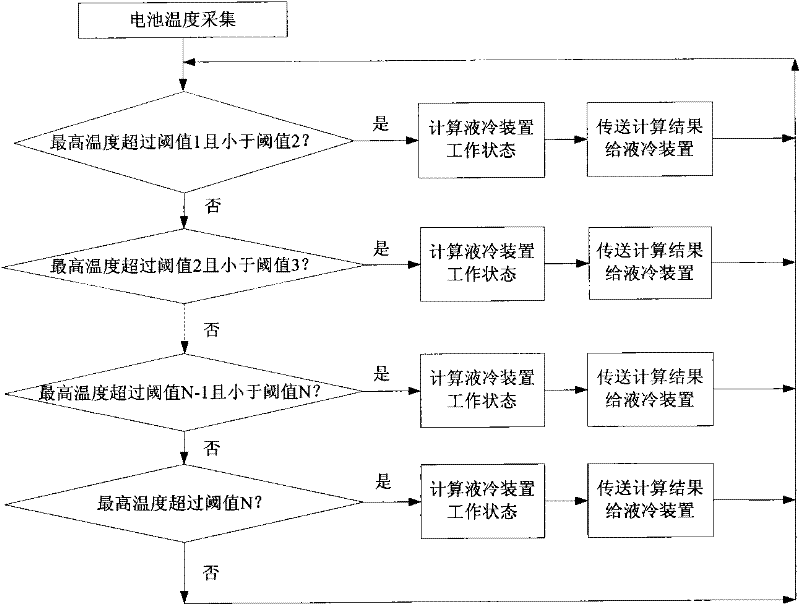
InactiveCN102544618AAvoid heat dissipationAvoid performance lossCell temperature controlTemperature controlPower flow
The invention discloses a liquid cooling temperature control and management method of a power lithium ion battery. The liquid cooling temperature control and management method comprises the steps of: 1) acquiring temperature and current; 2) obtaining a highest temperature value, a lowest temperature value, greatest temperature difference and liquid cooling system inlet and outlet temperature difference; 3) judging whether the current is large or not and computing a working state 1; 4) judging whether the temperature of the battery is high or not, computing a working state 2; 5) judging whether temperature difference of the battery is too great or not and computing a working state 3; 6) judging whether the outlet temperature of a battery pack is too high or not and computing a working state 4; 7) judging whether the temperature difference of circulating medium at the inlet and outlet of the battery pack is too great or not and computing a working state 5; and 8) comparing the computed working state 1, the working state 2, the working state 3, the working state 4 and the working state 5 to obtain a working state with the best heat dissipation effect for setting. The liquid cooling temperature control and management method of the power lithium ion battery solves the problems that the temperature of the battery is too high and the local temperature difference is too great, and has the beneficial effects that the performance of the battery is improved and the service life of battery is prolonged.
Owner:SHANGHAI AEROSPACE POWER TECH
Self-sealing mattress structure
InactiveUS6839929B2Avoid loss of performanceEliminate needStuffed mattressesSpring mattressesMechanical engineeringEngineering
A mattress for a bed having a frame for supporting the mattress and side rails, includes a non-puncture resistant cover with an interior surface, and a core disposed adjacent the interior surface. The core includes a body defining a plurality of mounting locations, and further includes a plurality of self sealing gas containers that are respectively disposed within the plurality of mounting locations. Accordingly, the overall height of the mattress may be used by the gas containers since a puncture resistant foam layer is not necessary.
Owner:HILL ROM SERVICES
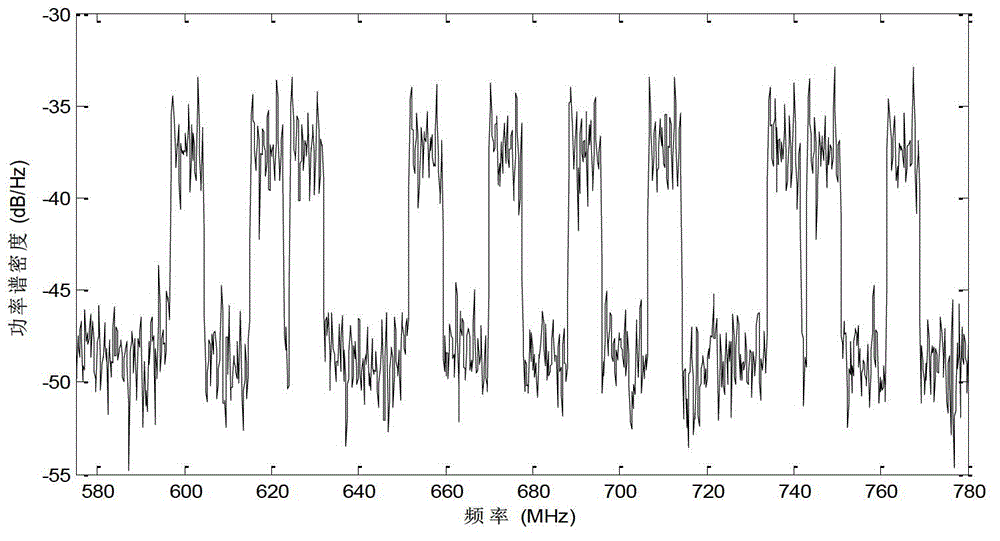
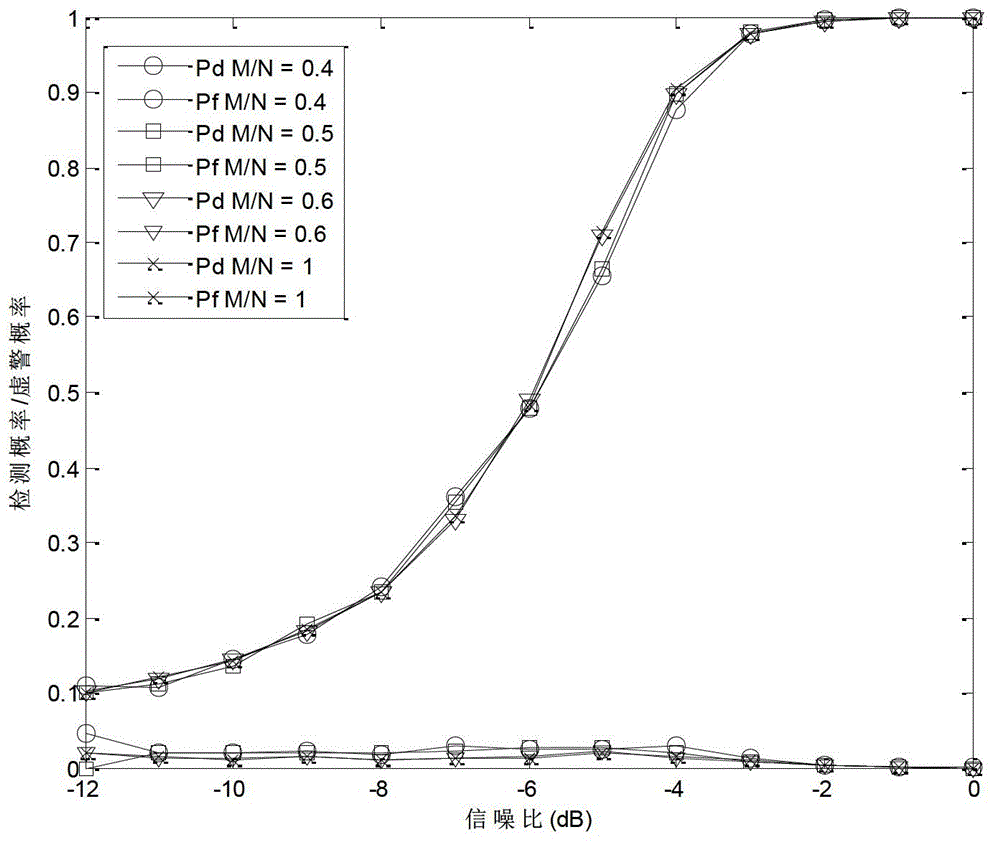
Compressed spectrum sensing method based on autocorrelation matrix reconstitution
InactiveCN102946288ADownsamplingSave storage spaceTransmission monitoringFrequency spectrumSignal classification
The invention provides a compressed spectrum sensing method based on autocorrelation matrix reconstitution and mainly solves the problem that an existing sensing algorithm is high in sampling speed and large computation overhead. The compressed spectrum sensing method comprises that a secondary user obtains an observation sequence of a frequency spectrum environment through compressed sensing and obtains an autocorrelation matrix estimated value of Nyquist sampling by utilizing autocorrelation vector quantity of a autocorrelation matrix reconstitution Nyquist sample sequence of the observation sequence; a multi-signal classification MUSIC algorithm is adopted to obtain an estimated value of occupied channel number according to a characteristic value of the autocorrelation matrix estimated value; a characteristic spectrum is constructed according to the characteristic value and the estimated value of the occupied channel number, spectral amplitude values corresponding to characteristics of channels are added to obtain a sum, and mark numbers of the occupied channels are judged. By means of the compressed spectrum sensing method, the sampling speed of a secondary user receiving machine can be reduced, algorithm complexity at the reconstitution end is low, and spectral amplitude occupying situation in a cognitive radio system can be judged quickly.
Owner:XIDIAN UNIV
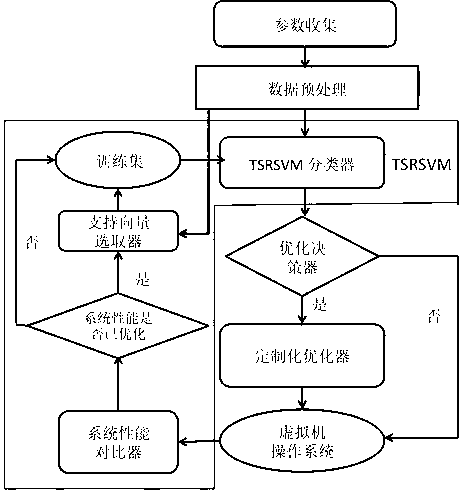
Method for classifying operated load in virtual machine under cloud computing environment
ActiveCN103279392AHigh load classification accuracyExclude the effects of misclassificationResource allocationTransmissionOperational systemParallel computing
The invention discloses a method for classifying operated load in a virtual machine under cloud computing environment. The method includes firstly acquiring monitoring parameters in 5 minutes of load operation and subjecting the monitored parameters to normalization processing; classifying load monitored into four categories such as CPU (central processing unit)-intensive load, memory intensive load, I / O (input / output) intensive load and network intensive load by means of TSRSVM (training sets refresh SVM); providing corresponding customized optimizing strategies for operation systems which running the four categories of intensive loads, and monitoring operating state of the systems through a performance comparison device; indicating that classification strategies are correct if performance of the systems is improved, otherwise, indicating that the classification strategies are incorrect. By the method, accuracy of load classification is high and system performance loss is low.
Owner:ZHEJIANG UNIV
Transaction execution method and device, computer equipment and storage medium
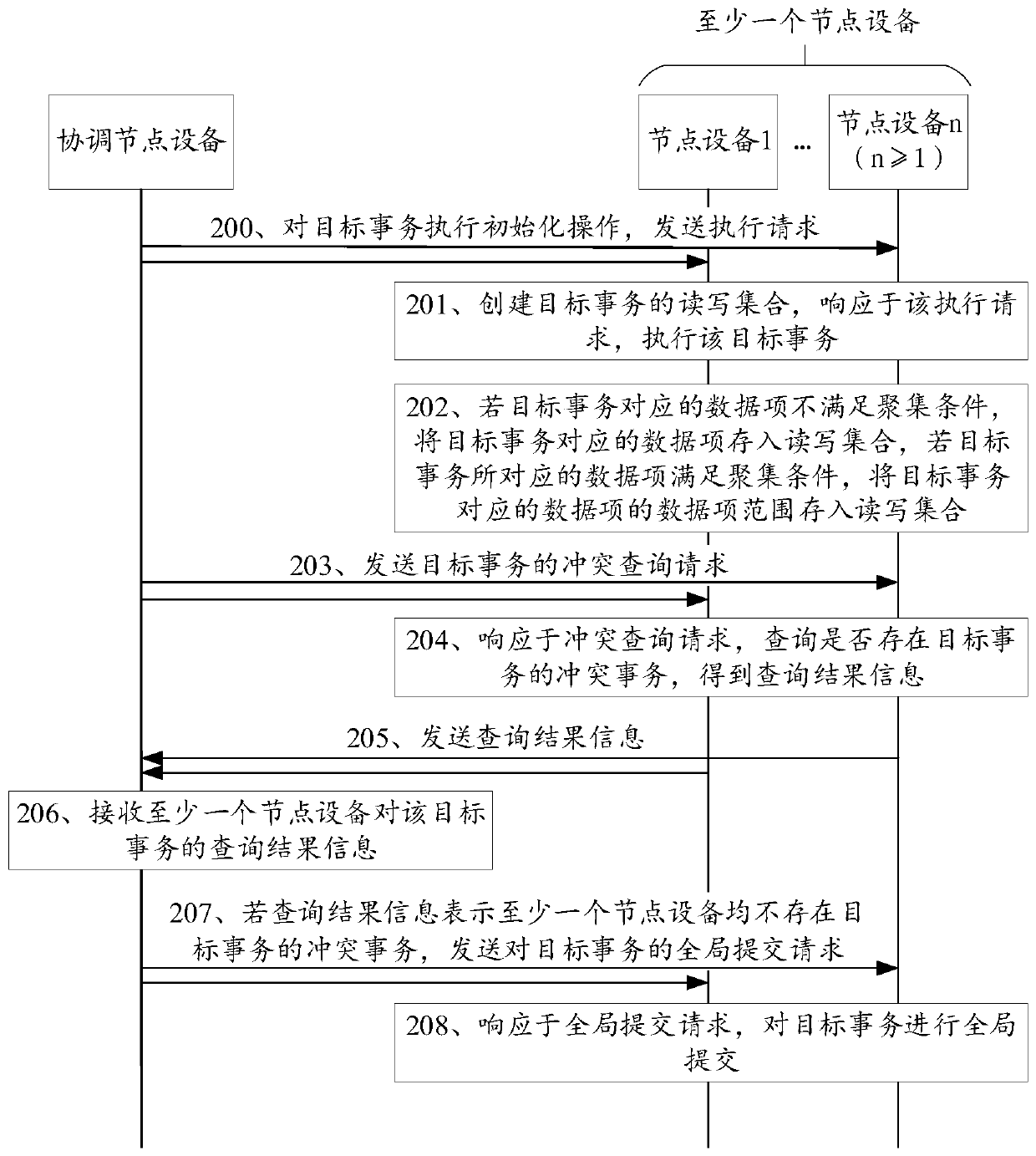
ActiveCN111159252AImprove transaction execution efficiencyAvoid performance lossDatabase distribution/replicationSpecial data processing applicationsConcurrency control algorithmsConcurrency control
The invention discloses a transaction execution method and device, computer equipment and a storage medium, and belongs to the technical field of databases. According to the invention, node equipmentresponds to the conflict query request of coordination node equipment for the target transaction; whether a conflict transaction of the target transaction exists in the node equipment or not is inquired to obtain query result information, wherein the operation objects of the conflict transaction and the target transaction comprise the same data item; and the query result information is sent to coordination node equipment, responding to a global submission request for the target transaction sent by the coordination node equipment under a target condition, the target transaction is subjected toglobal submission; and the target condition is used for representing that the conflict transaction of the target transaction does not exist in the database system, so that the concurrency control algorithm does not need to depend on distributed deadlock, the performance loss caused by the distributed deadlock is avoided, and the transaction execution efficiency of the database system is improved.
Owner:TENCENT TECH (SHENZHEN) CO LTD +1
Intelligent charging pile peak-hour-avoiding charging method and intelligent charging pile system
ActiveCN110126665AReduce the burden onReduce charging costsCircuit monitoring/indicationCharging stationsStart timeElectricity price
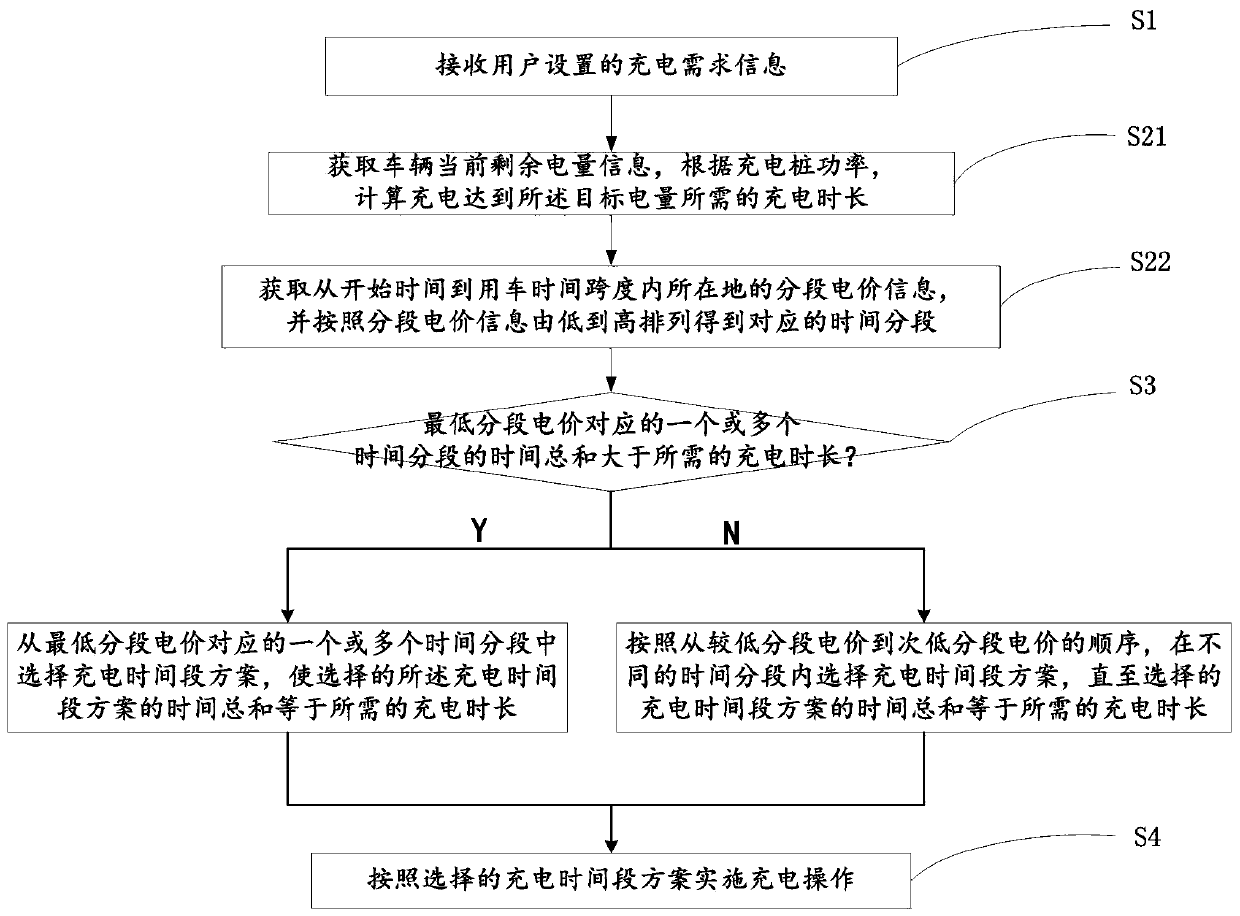
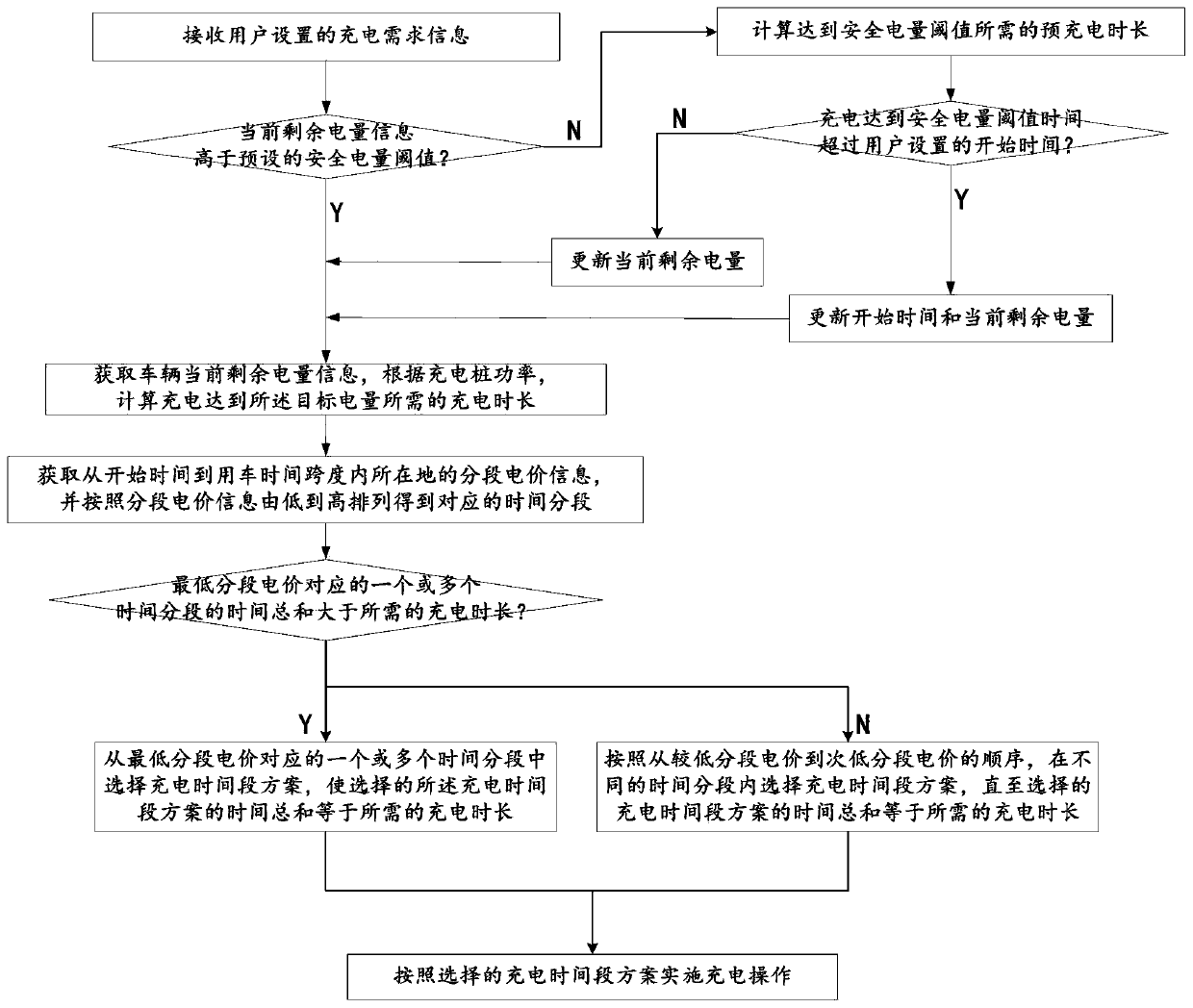
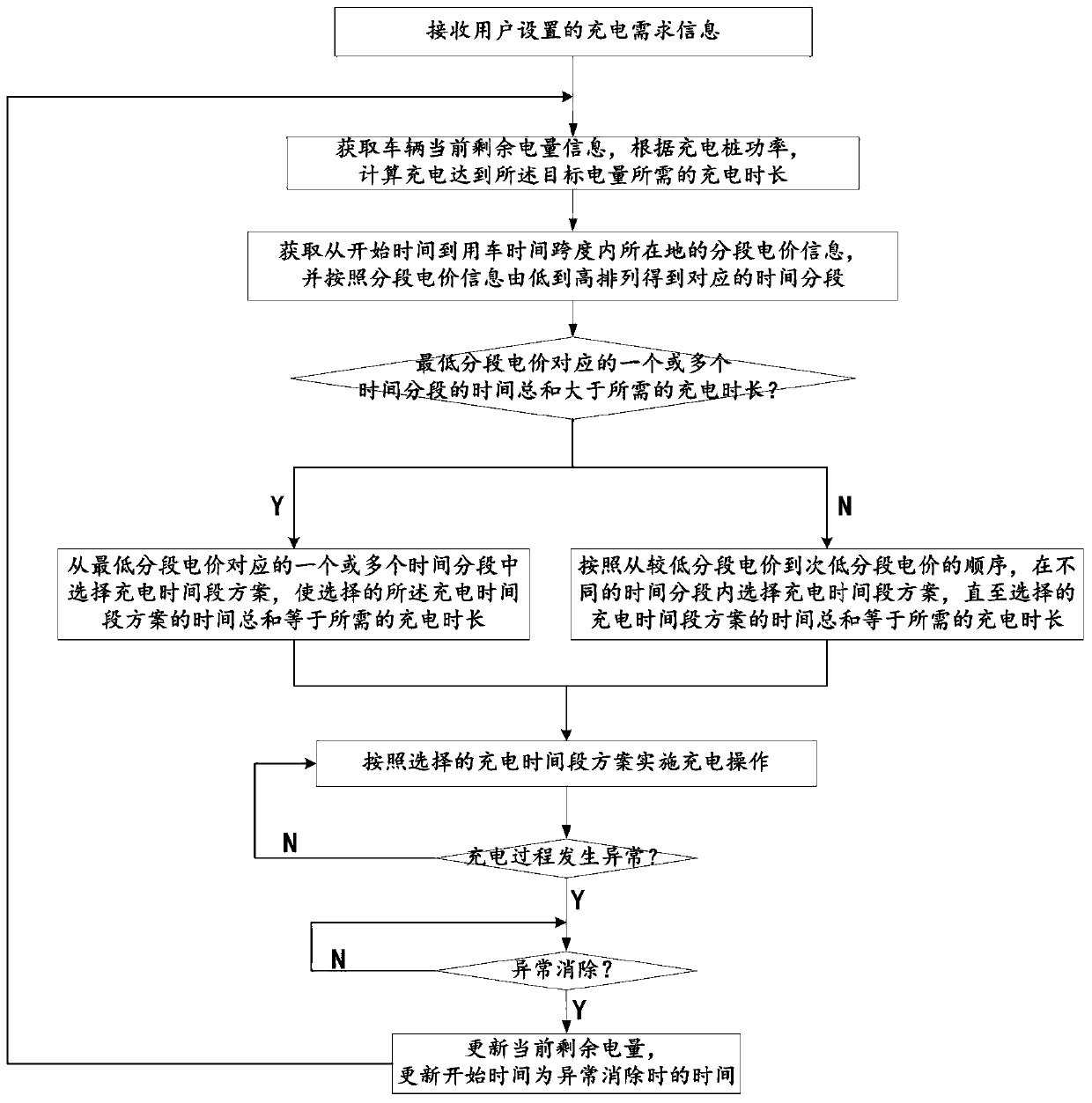
The invention discloses an intelligent charging pile peak-hour-avoiding charging method and an intelligent charging pile system. The intelligent charging pile peak-hour-avoiding charging method comprises the following steps that S1, charging demand information set by a user is received, wherein the charging demand information comprises vehicle use time, target electric quantity and start time; S2,the current remaining electric quantity information of a vehicle is acquired, and the charging time required for charging is calculated to reach the target electric quantity according to the chargingpile power; and segmented electricity price information of the location of the time span from the starting time to the vehicle using time, and the segmented electricity price information is arrangedfrom low to high to obtain corresponding time segments; S3, a charging time period scheme is selected according to the sequence from the lower segment price to the next lower segment price until the total time of the selected charging time period scheme is equal to the required charging time period; and S4, charging operation is implemented according to the selected charging time period scheme. According to the set charging conditions, the intelligent charging pile peak-hour-avoiding charging method automatically plans a peak-hour-avoiding charging time period scheme, the power grid burden ofpeak power consumption is reduced, and the charging cost of the user is reduced.
Owner:SHANGHAI POWERSHARE TECH LTD
Maintaining PEM fuel cell performance with sub-freezing boot strap starts
InactiveUS20040247965A1Poor end-cell performanceMitigate and eliminate performance lossFuel cell heat exchangeFuel cell controlFuel cellsElectric heating
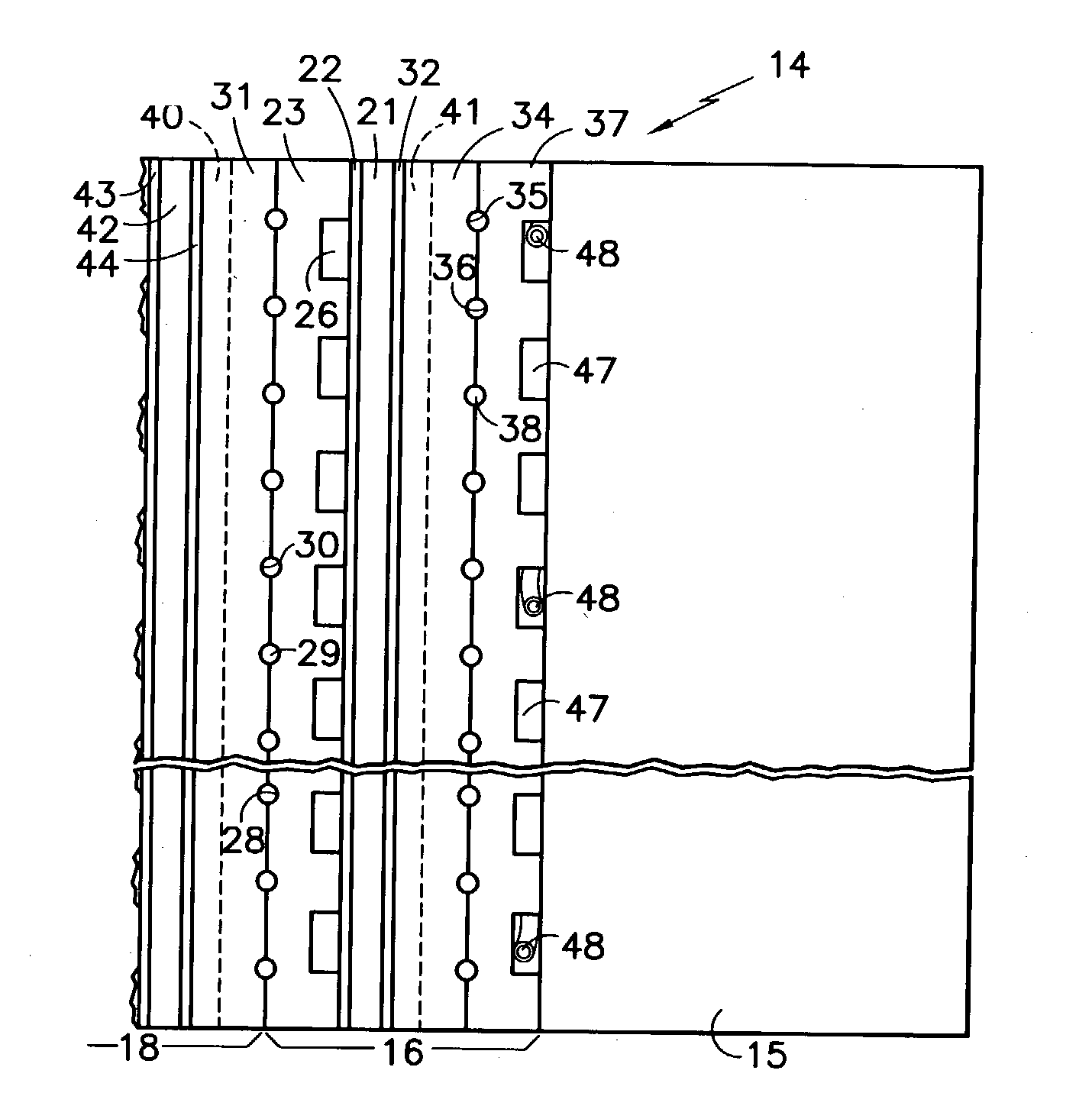
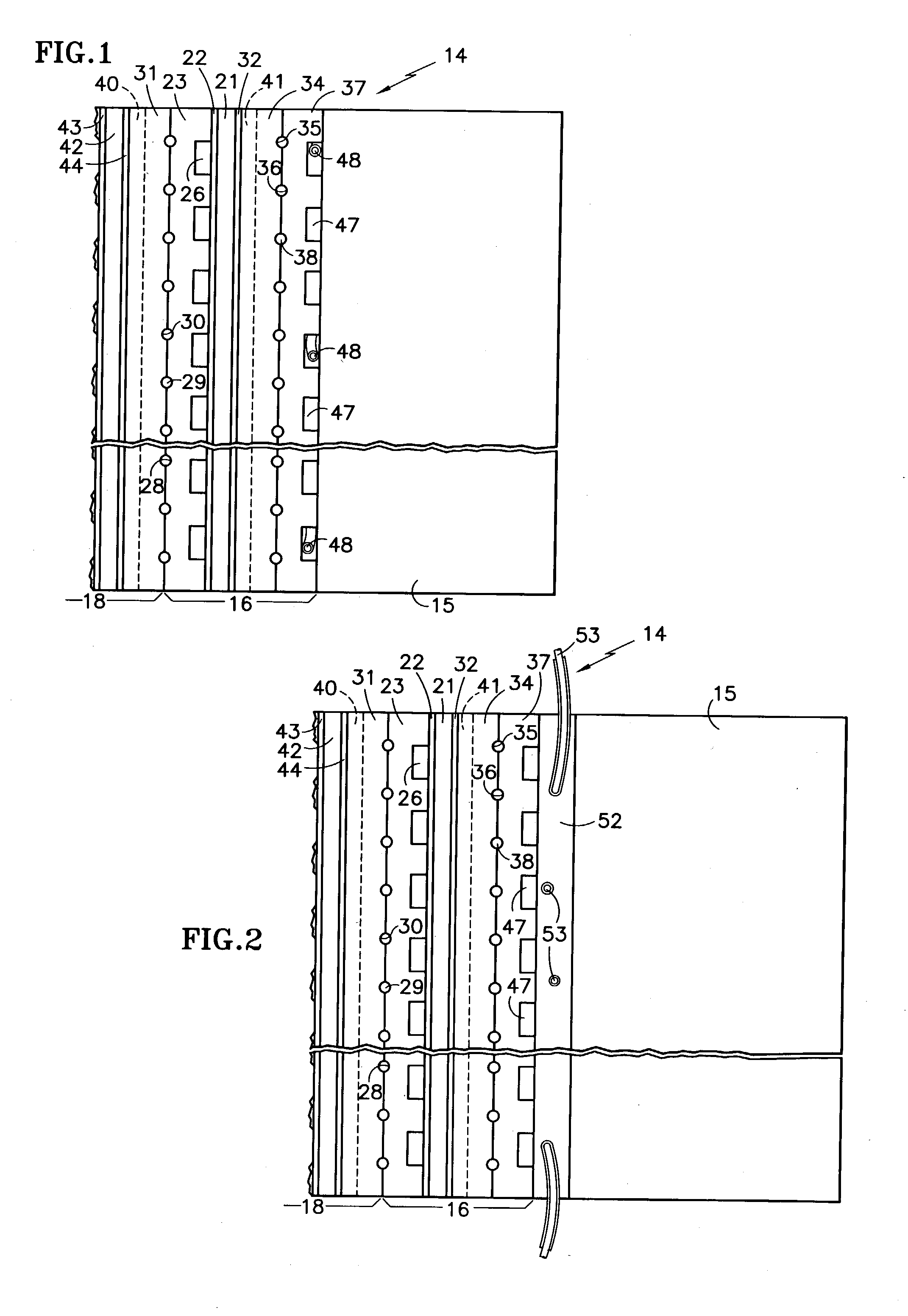
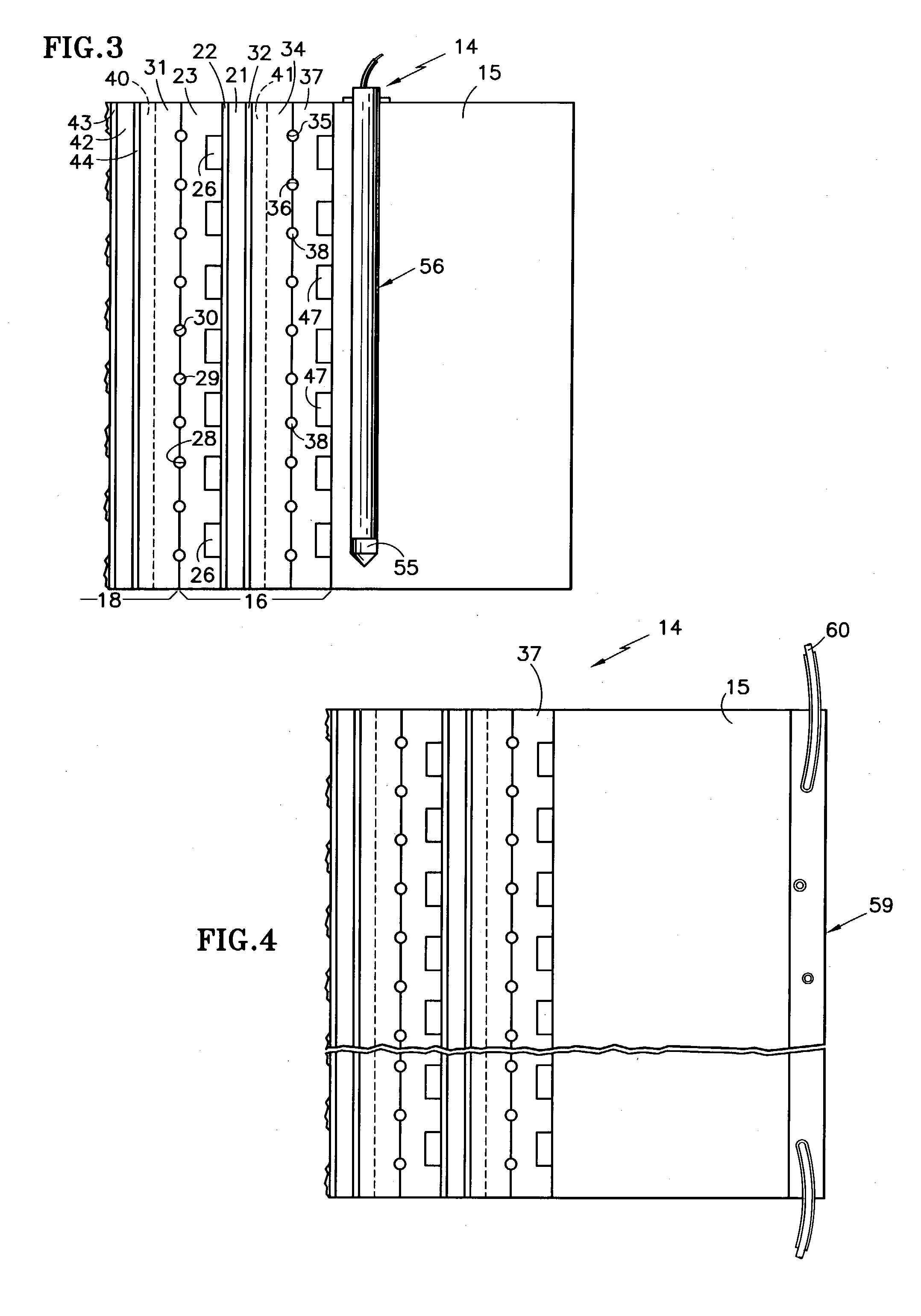
The fuel cells (16, 18) adjacent or near the end plate (15) of a fuel cell stack (14) are warmed either by (a) a heater wire (48) within the fuel cell (16) adjacent to the end plate, (b) heater wires (53) are disposed in a heater element (52) located between the end plate and the fuel cell closest to the end plate (15), (c) one or more heaters (56) are disposed in holes (55) within the end plate (15), (d) electric heating elements (59) on a surface of the end plate (15), or (e) a catalytic heater (61) disposed on the surface of the end plate. The fuel cells (16, 18) may be heated before or during operation at sub-freezing temperatures to prevent loss of fuel cell performance, or may be heated after operation at sub-freezing temperatures to restore fuel cell performance.
Owner:INT FUEL CELLS
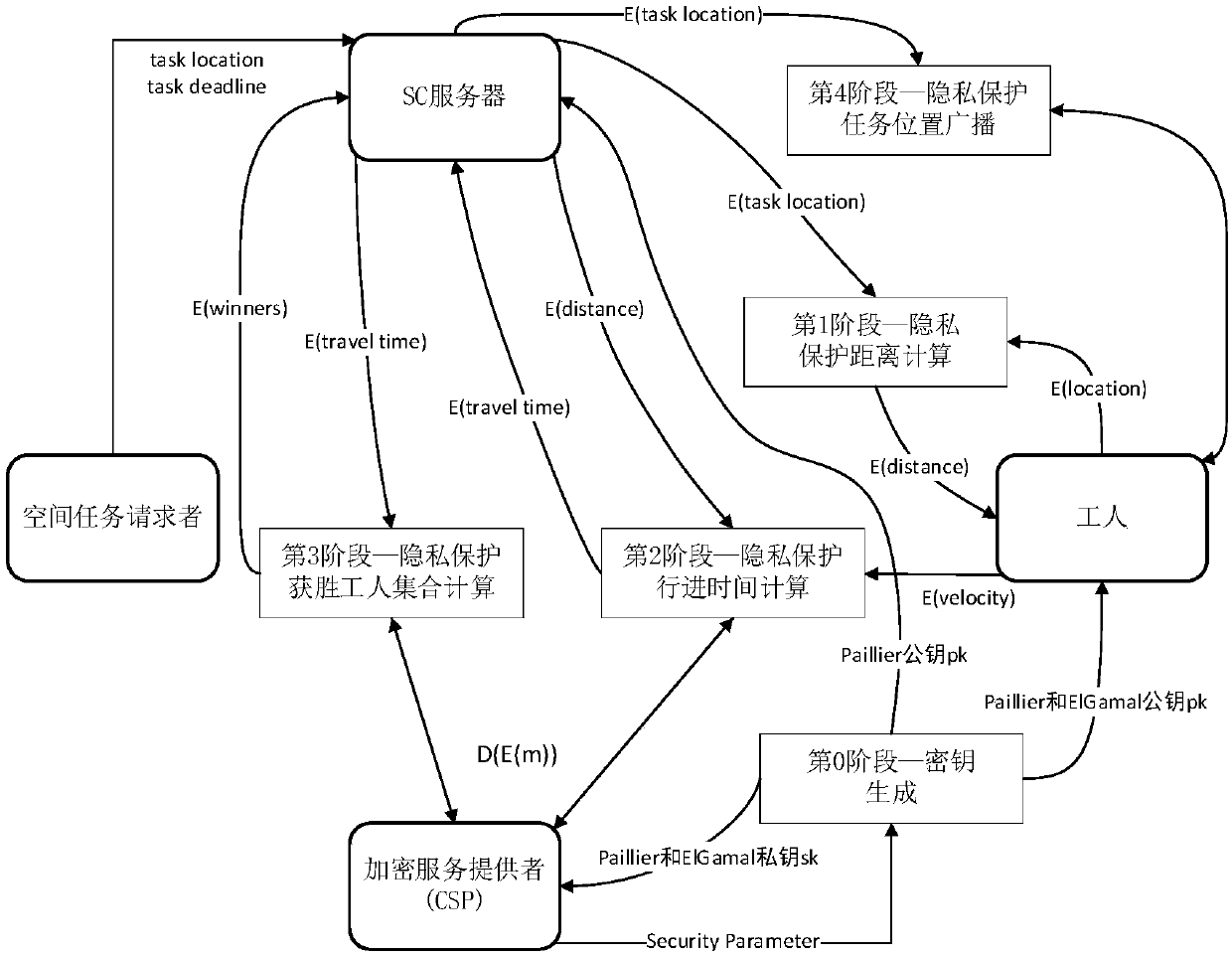
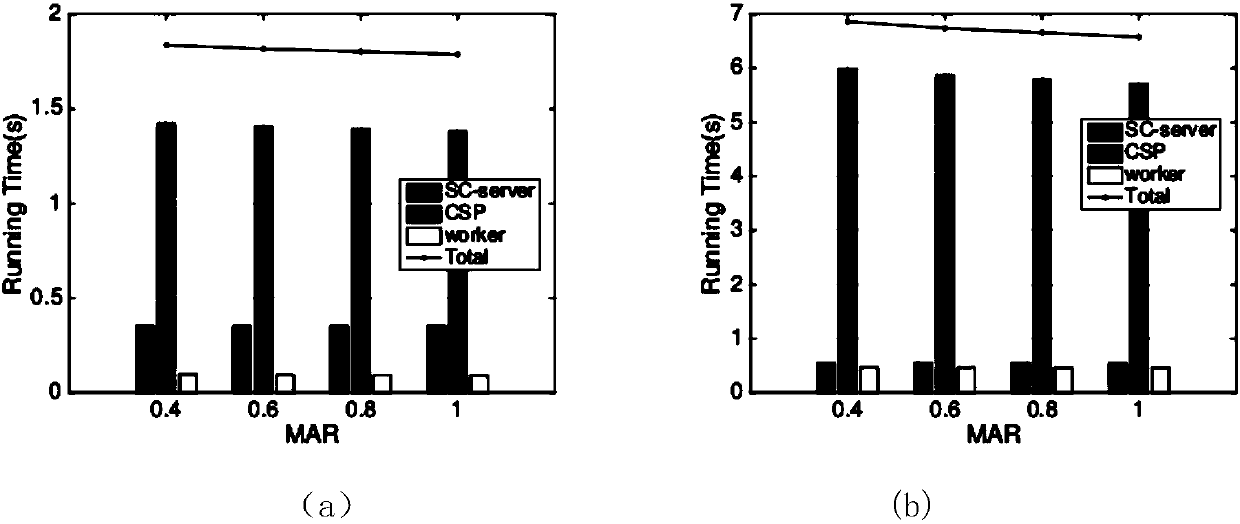
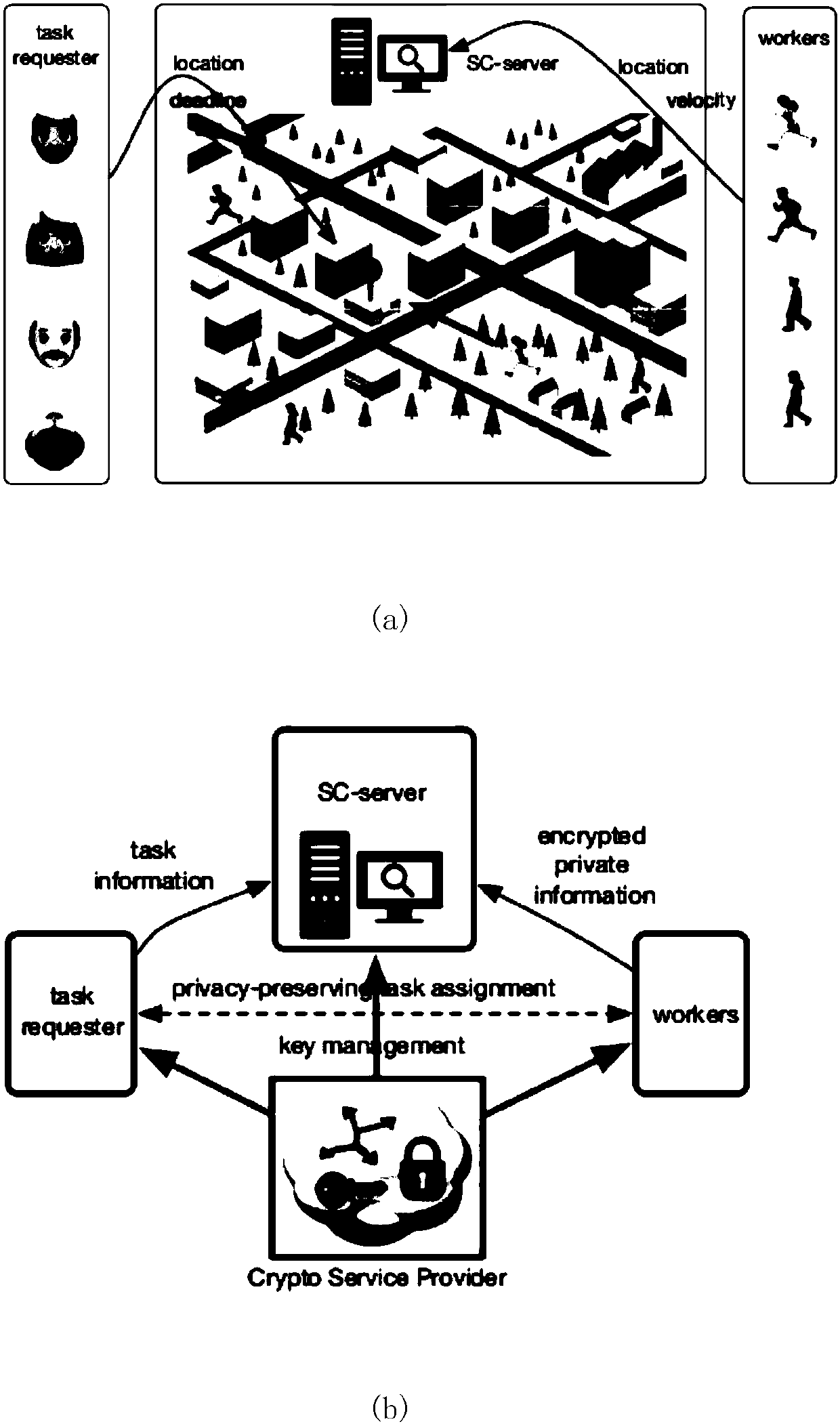
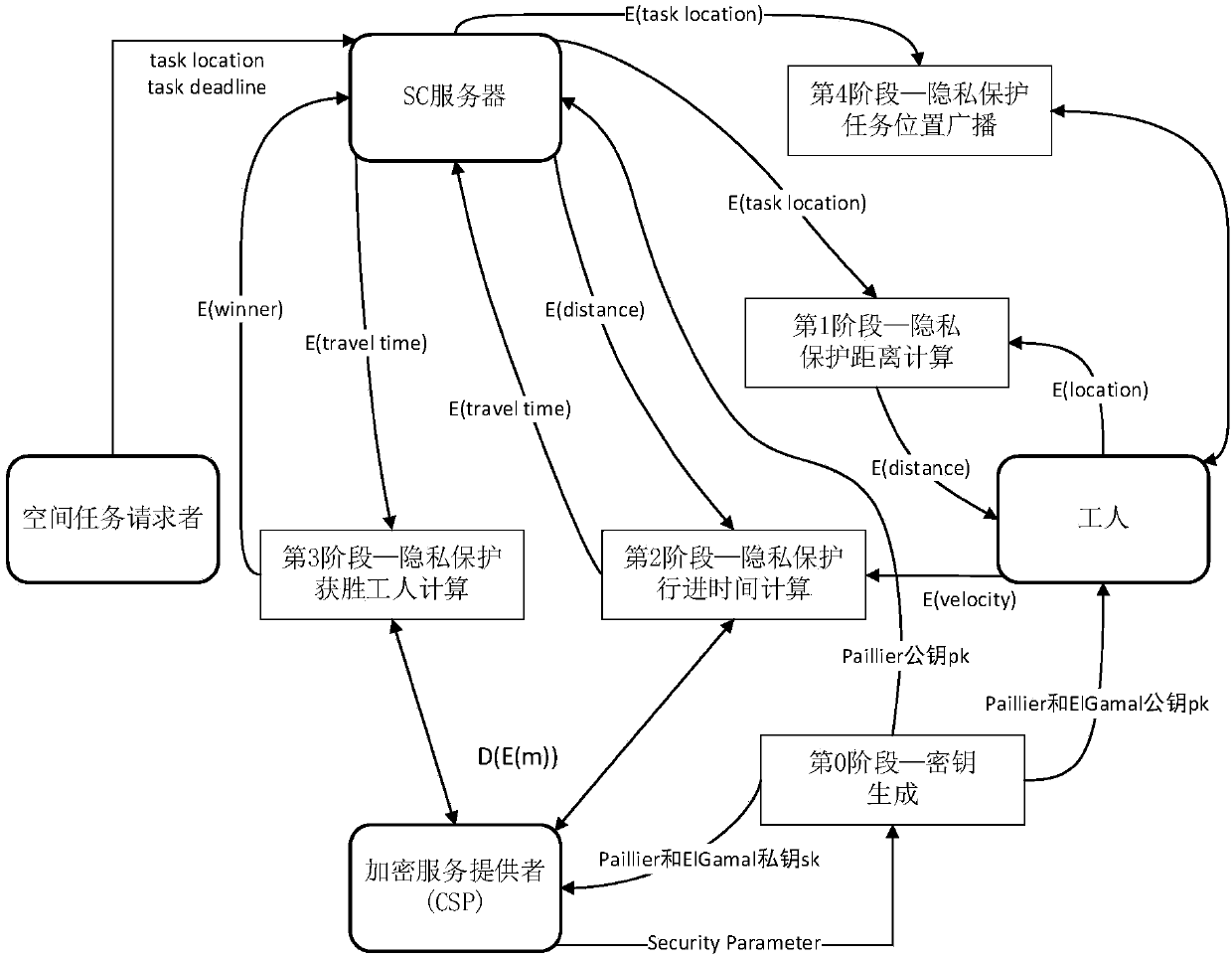
Warrantable privacy protection space crowdsourcing task distribution system and method
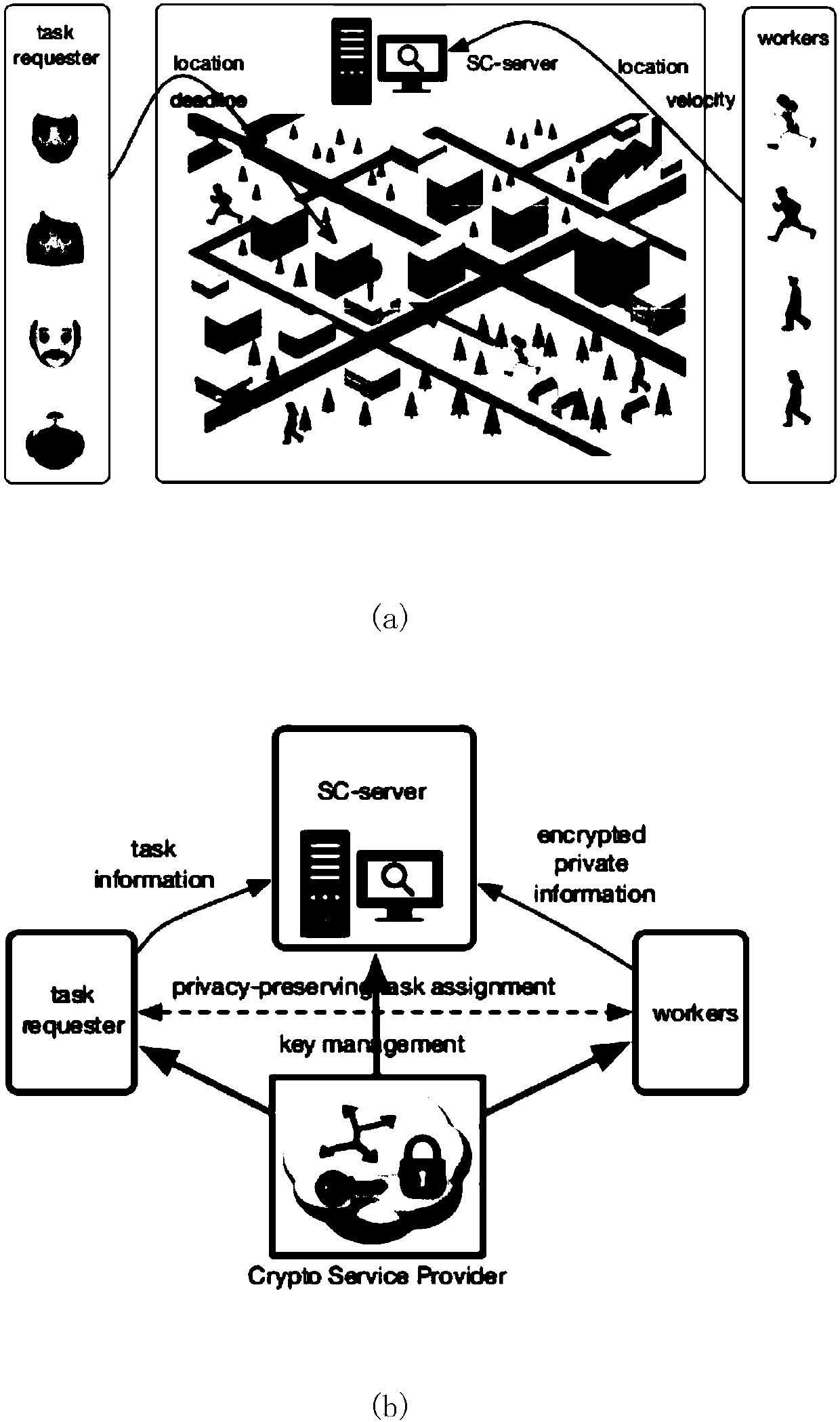
ActiveCN107360146APrivacy protectionStrong mutual protectionKey distribution for secure communicationEncryption apparatus with shift registers/memoriesDistribution systemService provider
The invention discloses a warrantable privacy protection space crowdsourcing task distribution system and method, and the system comprises an SC server, an encryption service provider, a space task requester, and workers. The encryption service provider generates a secret key, and employs a Paillier password and ElGamal password system. The space task requester creates a space task, and returns the position of the task to the SC server. The SC server encrypts the position of the task, and each worker calculates the distance between the position of the task and the position of the worker. The speed of each worker is encrypted and transmitted to the SC server, and each worker calculates the travel time of his own, and encrypts the travel time and transmits the encrypted travel time to the SC server. The SC server calculates the winning workers through the encryption service provider, and the encryption service provider enables the winning worker set comprising a plurality of winning workers to be encrypted and returned to the SC server. The SC server encrypts the position of the task, and broadcasts the encrypted position of the task to all workers, and the winning workers arrive at the specified position to execute the task. According to the invention, the system achieves the double-side privacy protection in the space crowdsourcing, greatly reduces the calculation, and can guarantee that the task is accepted at high probability.
Owner:SHENZHEN UNIV
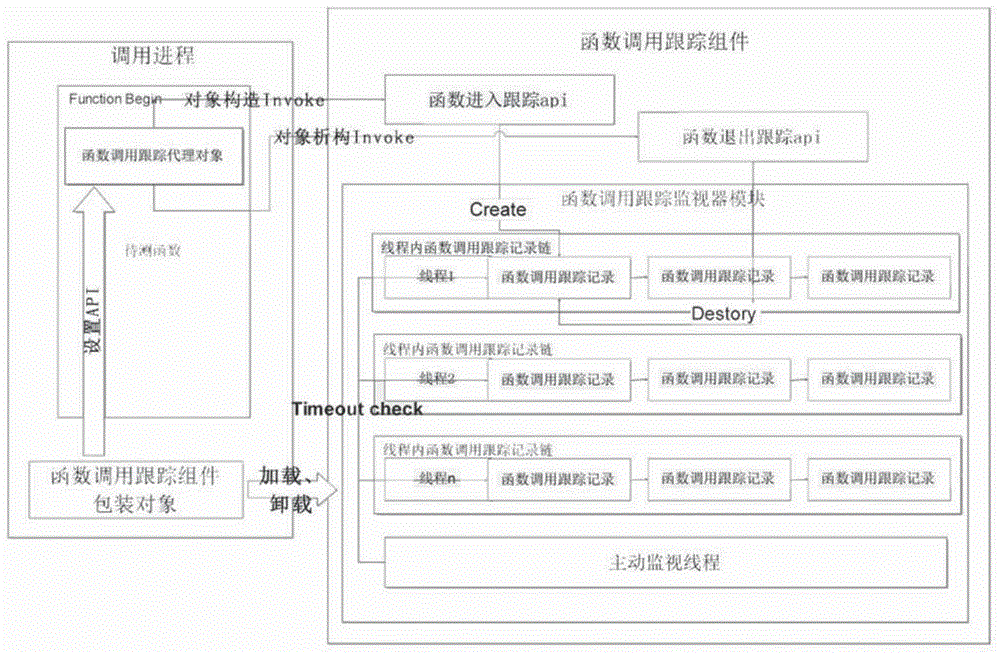
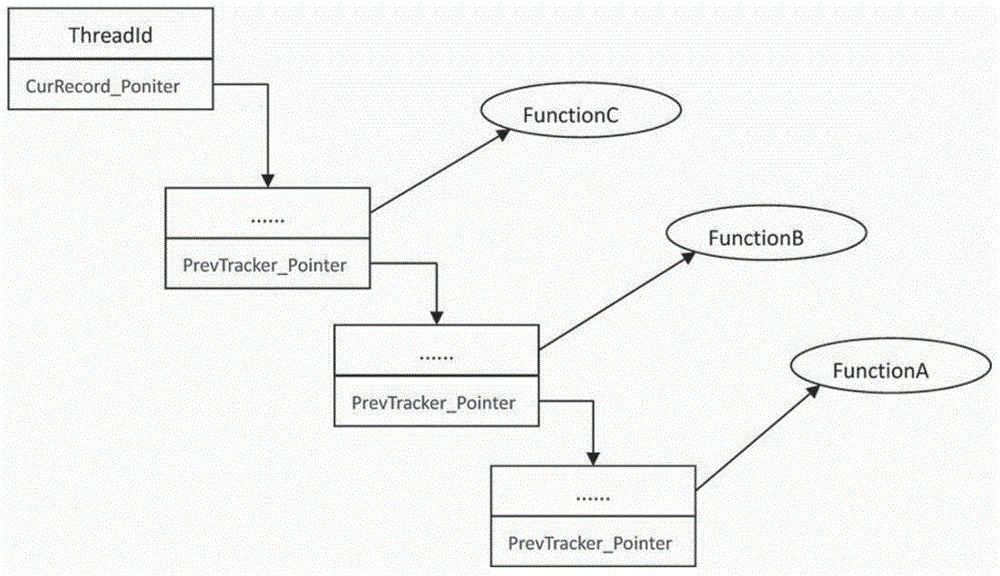
Function execution timeout and deadlock detection method based on dynamic tracking of operating period
ActiveCN104636259ADoes not affect the operating logicPerform tracking work normallySoftware testing/debuggingInformation objectRunning time
The invention relates to the technical fields of computers. A function execution timeout and deadlock detection method based on dynamic tracking of an operating period comprises the following steps: A, a section of tracking code is inserted in operating inlets of to-be-detected functions, the current operating threads of the to-be-detected functions are distinguished, characteristic information of the to-be-detected functions in operation is registered, and reference data of characteristic information objects are returned to the to-be-detected functions for temporarily saving; B, corresponding tracking codes are also inserted in operating outlets of the to-be-detected functions, and according to the access information of the characteristics information objects returned in A, the characteristic information objects of the to-be-detected functions are unregistered from the data structures of the current operating threads; and C, an independent monitor thread is established in the process, wherein the time count of the to-be-detected functions exceeds the first-stage time count threshold, which means that the operating time of the to-be-detected functions is too long, namely timeout, is proved; however, the time count of the to-be-detected functions exceeds the second-stage time count threshold, which means that the operating time of the to-be-detected functions is too long, namely timeout. The method can judge the timeout and deadlock effectively.
Owner:XIAMEN YAXON NETWORKS CO LTD
Arithmetic logic unit using asynchronous circuit to implement
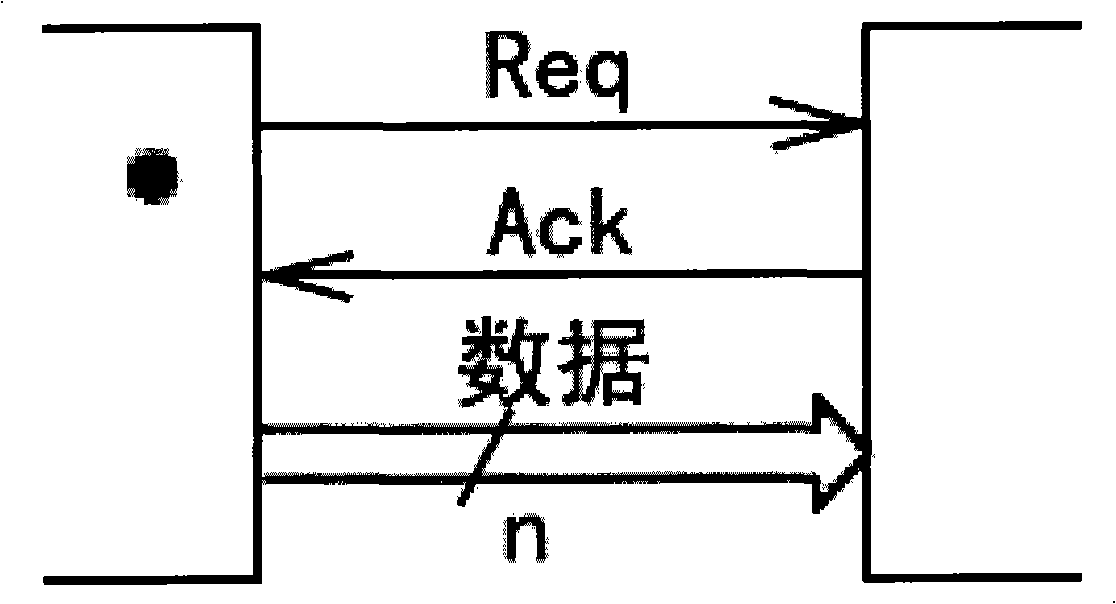
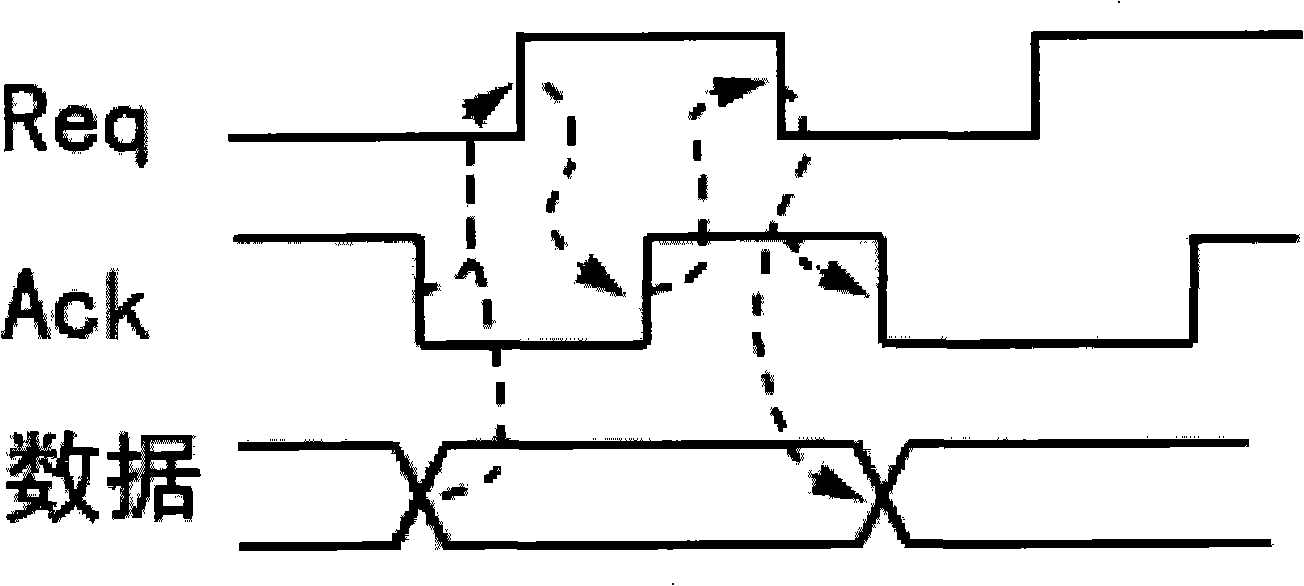
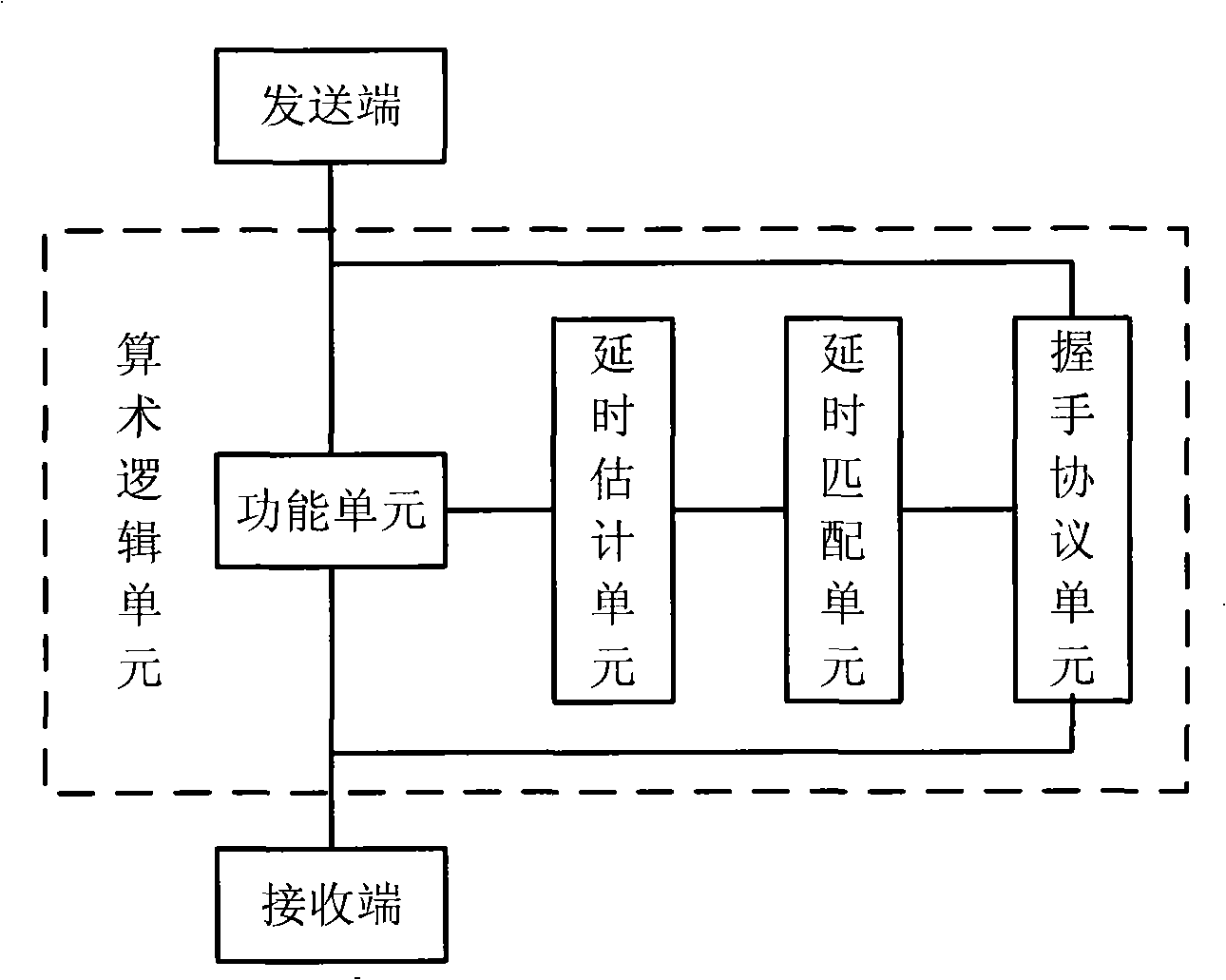
InactiveCN101303643AAvoid performance lossImprove performanceProgram controlMemory systemsArithmetic logic unitAsynchronous circuit
The invention relates to an arithmetic logic unit which is realized by adopting an asynchronous circuit. The arithmetic logic unit includes a functional unit which receives the calculation control command and input data of a transmitting end and implements the arithmetic logic calculation of the input data; a timelag evaluation unit which carries out timelag evaluation according to the type of the calculation control command and the detail input data received by the functional unit; a timelag matching unit which selects a calculation timelag matched with the functional unit; a handshake protocol unit which controls the transmitting end to generate a request signal simultaneously when the transmitting end transmits the input data to lead the input to be synchronous. The handshake protocol unit informs a receiving end to take out the output data of the functional unit after the calculation timelag and controls the receiving end to generate a reply signal to lead the output to be synchronous. The arithmetic logic unit of the invention has the characteristic of high property, overcomes the property loss of a synchronous circuit which can only realize the timelag of the worst situation; has the characteristic of low power consumption and saves the circuit area.
Owner:RESEARCH INSTITUTE OF TSINGHUA UNIVERSITY IN SHENZHEN
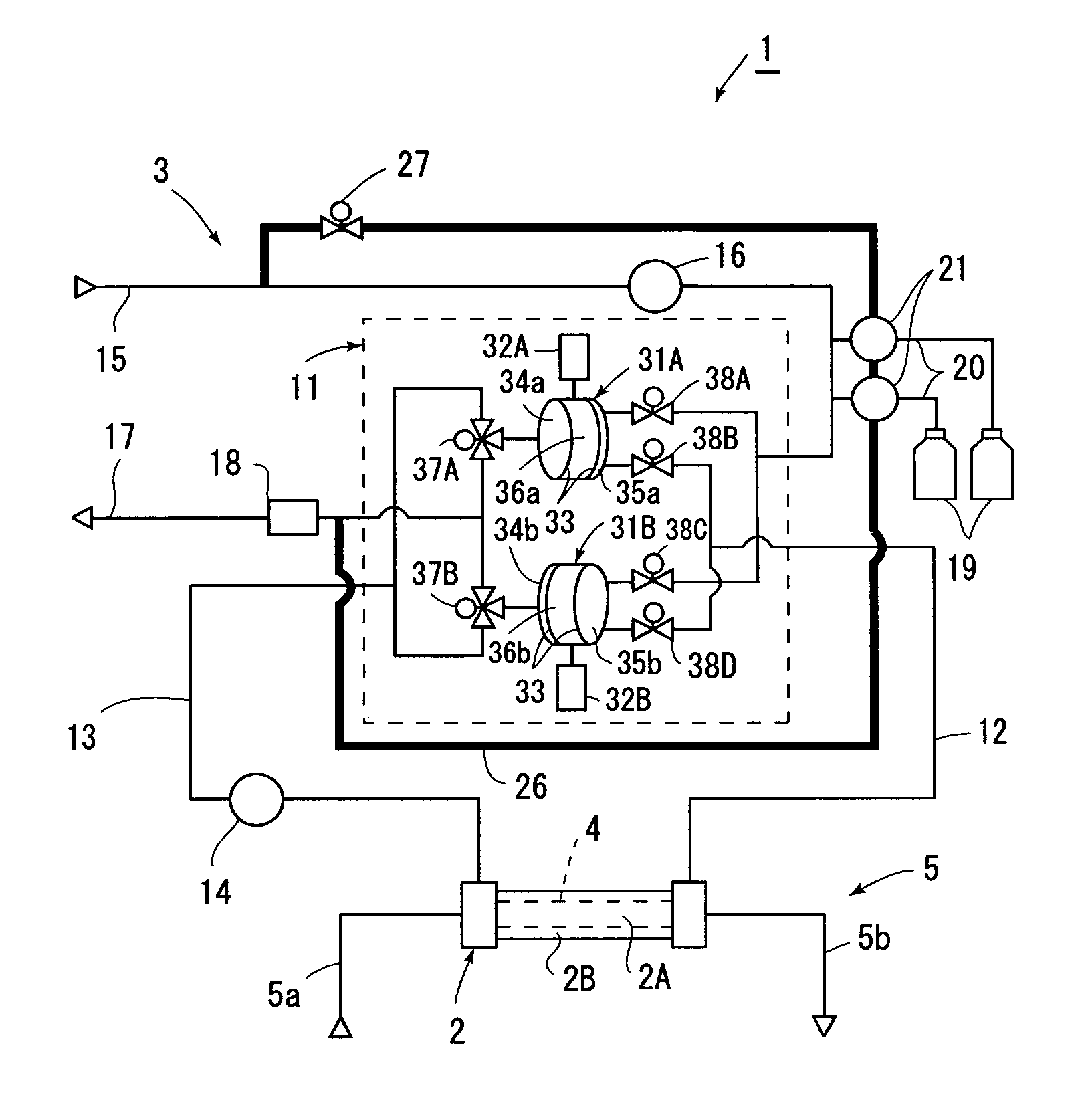
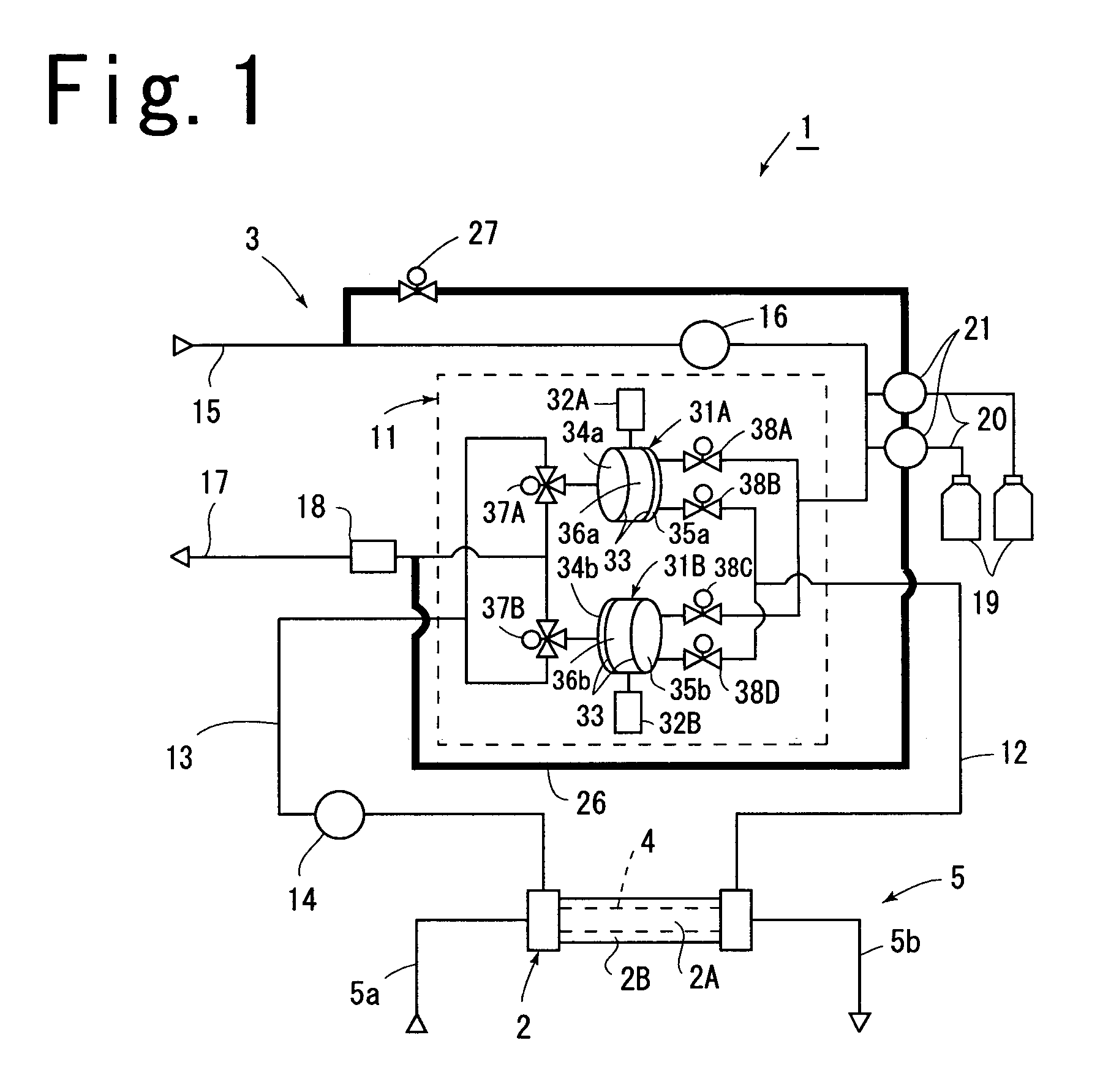
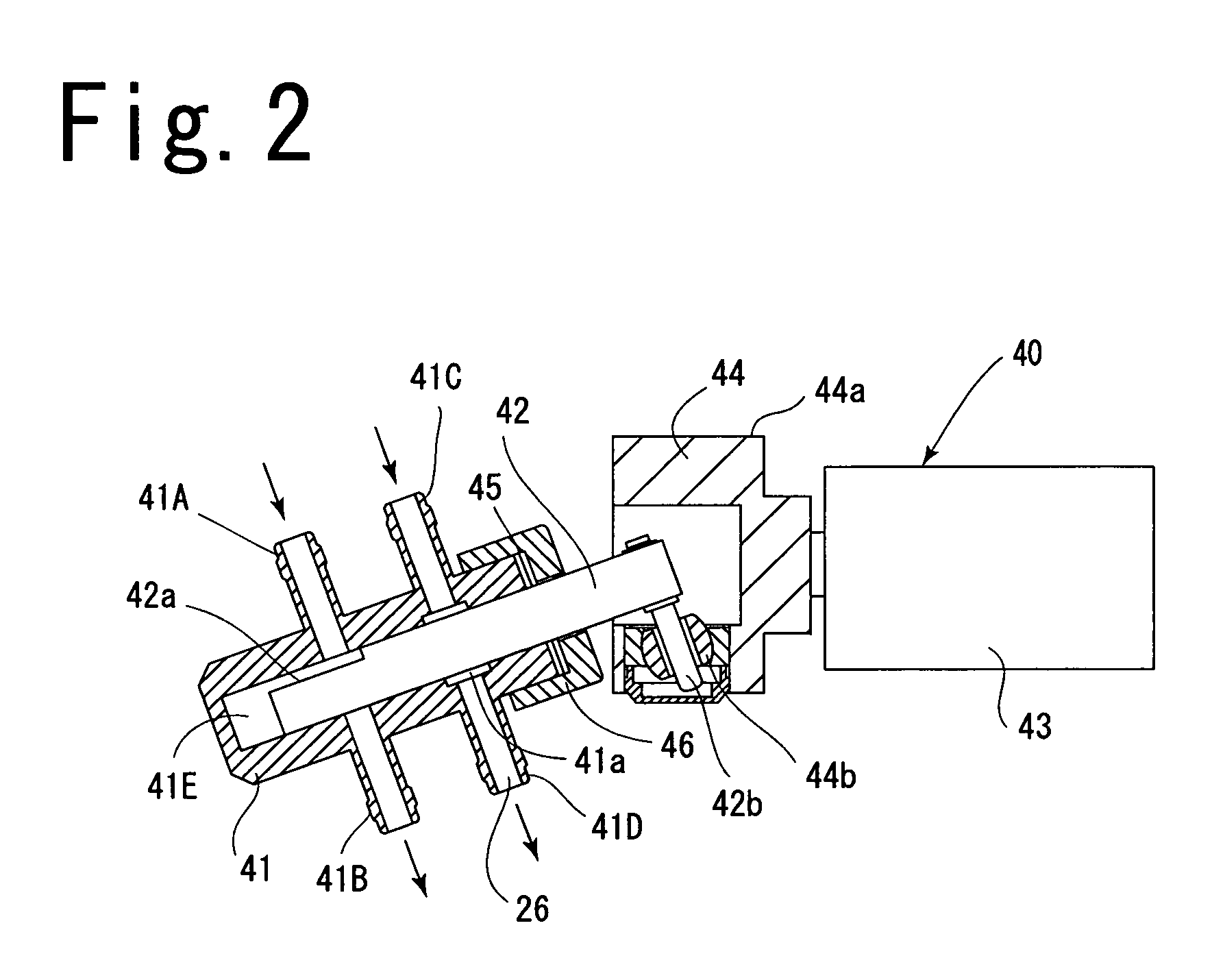
Dialysis device
ActiveUS7045061B2Prevent water leakageAvoid performance lossDialysis systemsDialysisMedicineClean water
A dialysis device 1 includes a water supply passage 15 for supplying clean water to solution supply chambers 35a and 35b, and a waste solution passage for discharging a used dialysis solution from solution collection chambers 34a and 34b, and the water supply passage includes a concentrate solution pump 21 that supplies a dialysis concentrate solution from concentrate solution supply source 19. The concentrate solution pump is a piston pump 40 that moves a piston 42 up and down in a cylinder 41 to feed a solution, the piston pump is provided in the way of washing passage 26 provided between the water supply passage and the waste solution passage, and an open / close valve 27 that intermittently opens and closes is provided in the washing passage to flow the clean water in the water supply passage through a gap between the cylinder and the piston.
Owner:SHIBUYA IND CO LTD
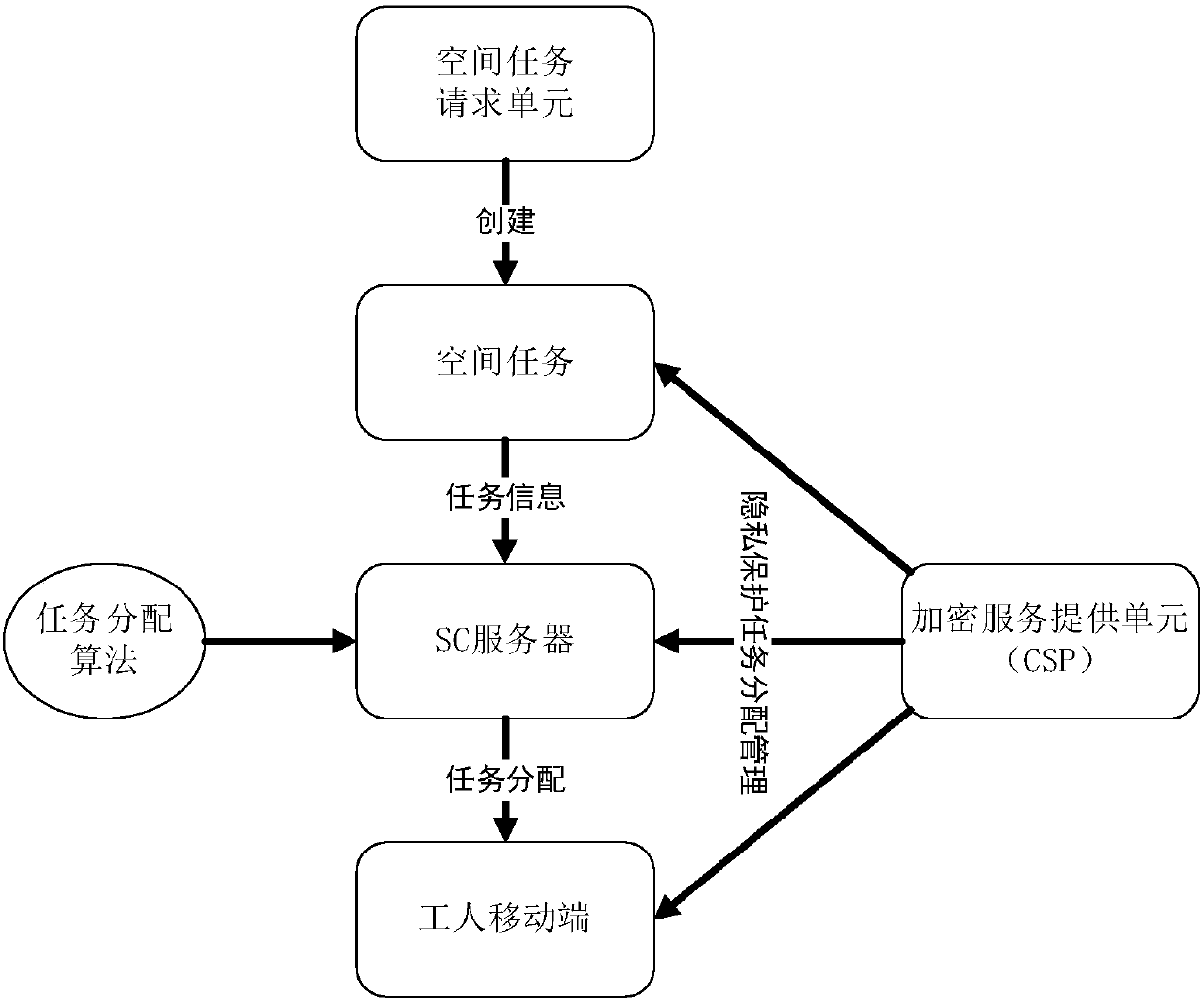
Task distribution system model of privacy protection space crowdsourcing and realization method
ActiveCN107257381APrivacy protectionStrong mutual protectionEncryption apparatus with shift registers/memoriesCommunication with homomorphic encryptionDistribution systemMobile end
The invention discloses a task distribution system model of privacy protection space crowdsourcing. The task distribution system model comprises a space outsourcing server, an encryption service providing unit, a space task request unit and a worker mobile terminal; the space task request unit is used for creating the space task, and transmitting the task information to the space crowdsourcing server; the space outsourcing server is used for distributing the task to the worker mobile terminal; the encryption service providing unit is used for providing the privacy protection task distribution management for the space task request unit, the space crowdsourcing server and the worker mobile terminal. Furthermore, the invention further discloses a realization method of the system model. The system model firstly realizes the dual-party privacy protection in the space crowdsourcing, not only protects the privacy of the worker, but also protects the task privacy. The efficient task distribution is performed in the space crowdsourcing, and the privacy protection on two aspects of the worker and the task is provided.
Owner:SHENZHEN UNIV
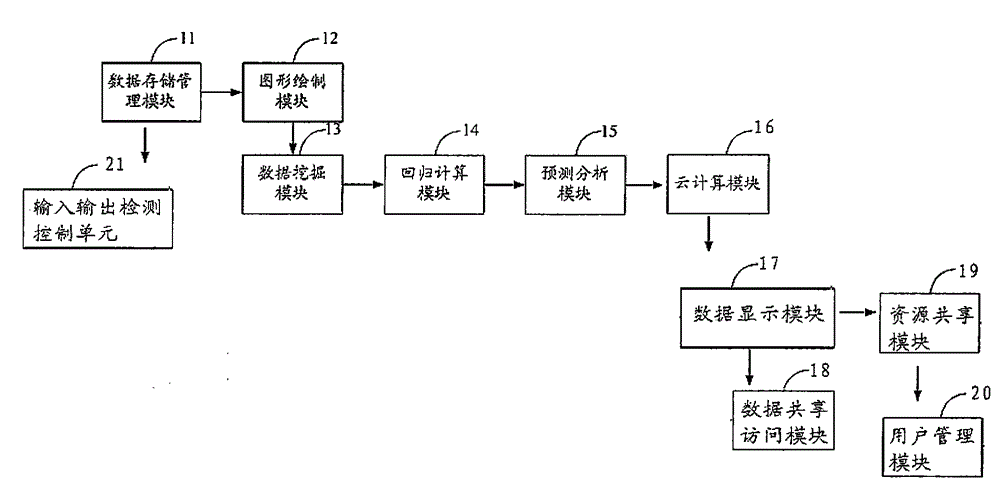
Enterprise management data processing system
InactiveCN104836792ARealize monitoringImprove work efficiencyData miningTransmissionData displayThe Internet
The invention discloses an enterprise management data processing system. The enterprise management data processing system comprises a data storage and management module, an input / output detection and control unit, a data mining module, a graph drawing module, a regression calculation module, a prediction and analysis module, a cloud computing module, a data display module, a data sharing access module, a resource sharing module and a user management module. According to the invention, redundancy and complementation information among sensors are combined by rule comprehensive monitoring of enterprise data is achieved, the working efficiency of a manager is improved, a database can be accessed in manner of being not directly though the Internet, hackers are prevented from directly attacking a database system, the safety of the database system is guaranteed, and performance loss caused by attack is avoided. when the database is accessed, by searching access records, the access efficiency can be improved. Once the secret key is used, the secret key is updated, an encryption algorithm of plain text division and redundant section addition is used, and the encryption effect is good.
Owner:NANYANG INST OF TECH
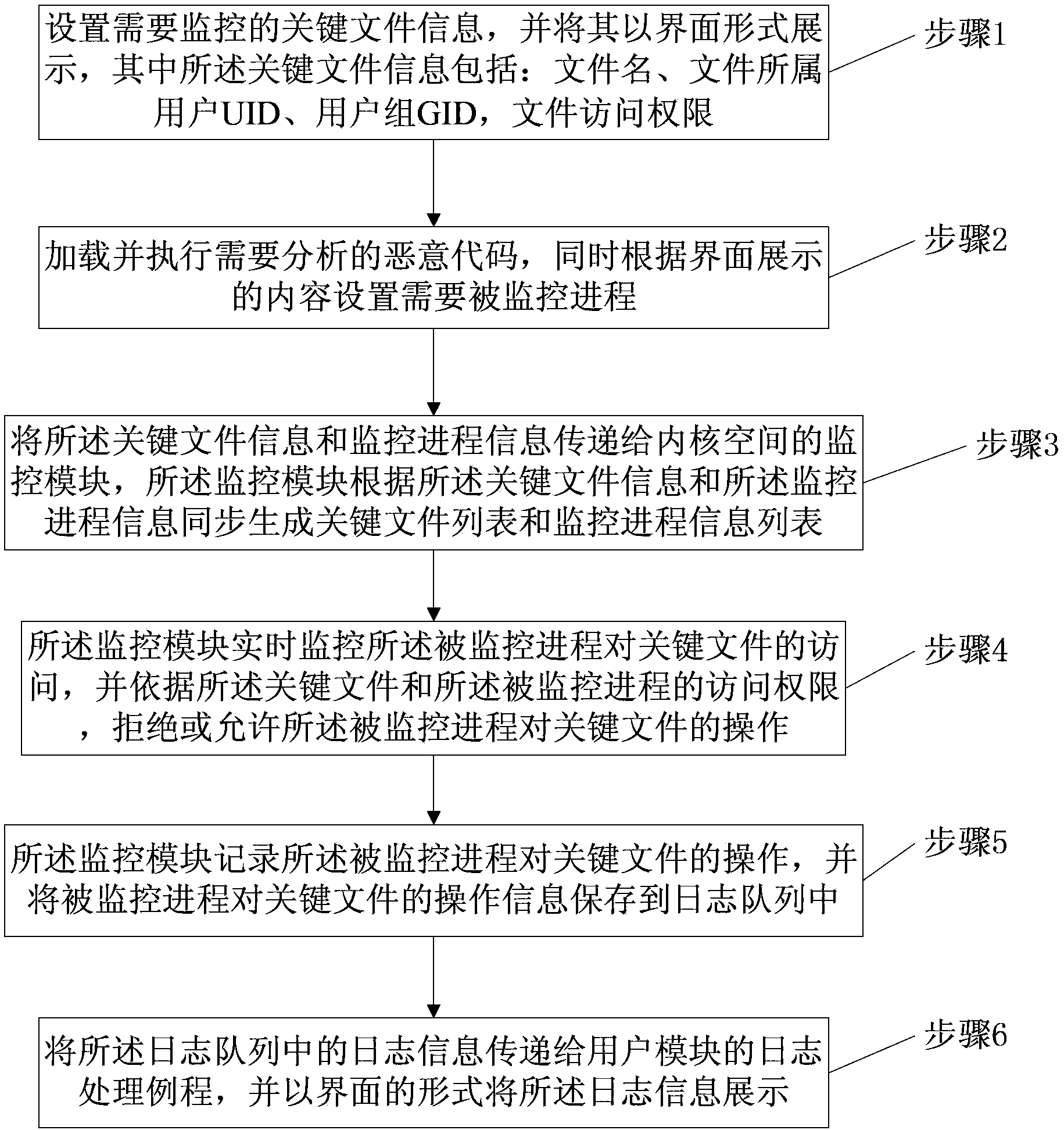
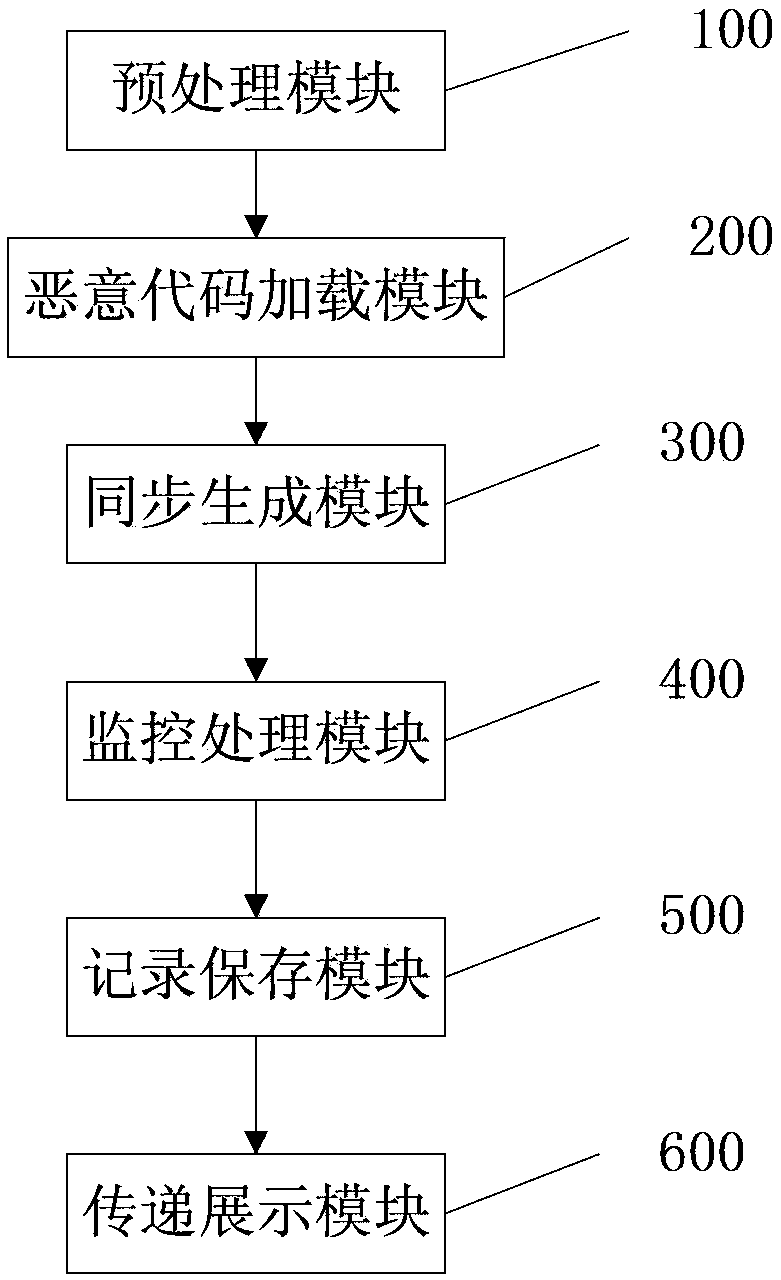
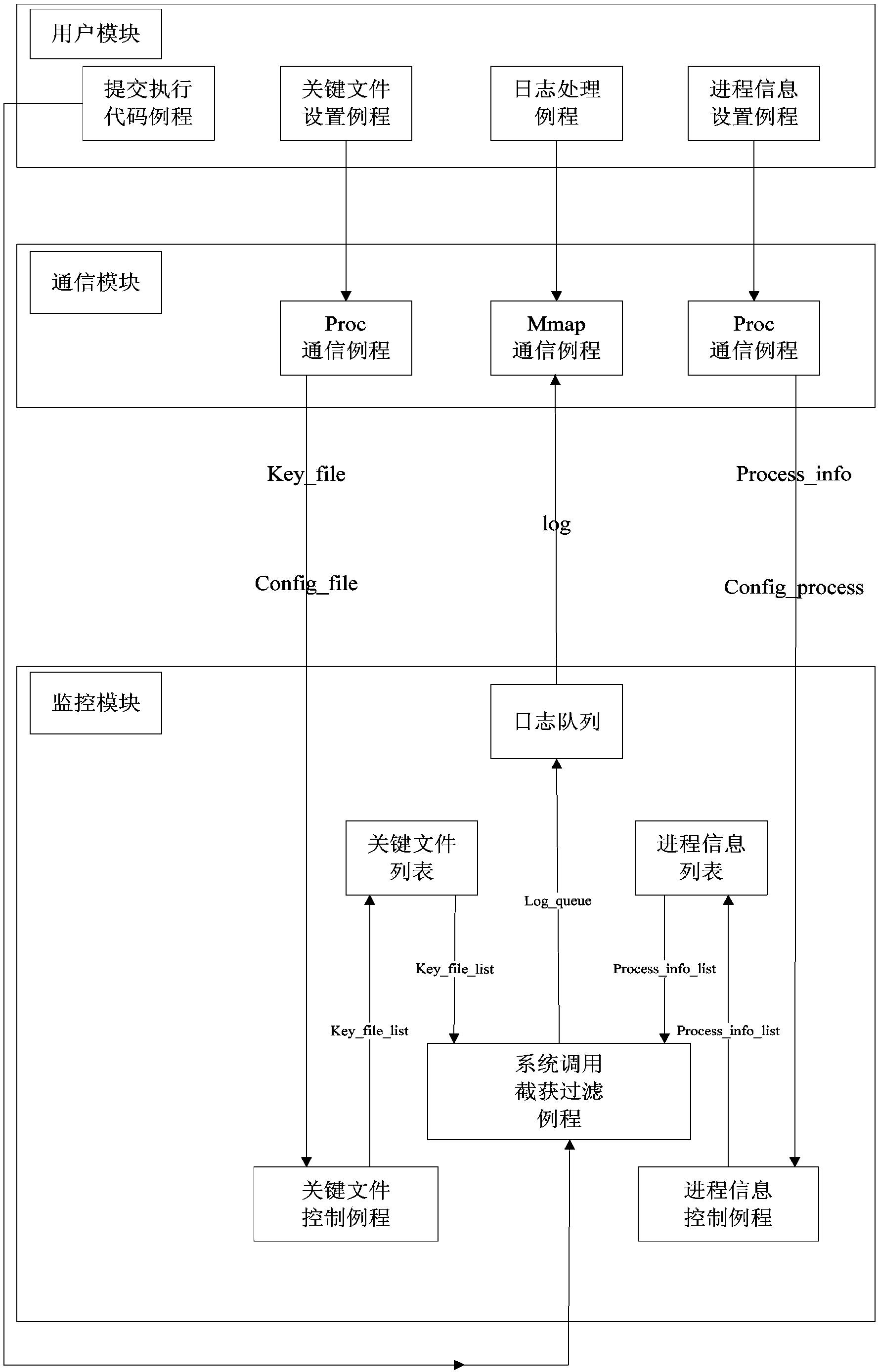
Malicious code analysis method and system under Linux platform
ActiveCN104102878AImplement dynamic loadingAccurate and useful monitoring informationPlatform integrity maintainanceVirtual file systemGNU/Linux
The invention provides a malicious code analysis method and system under a Linux platform. According to the method and the system provided by the invention, dynamic loading can be realized by using an LKM (Loadable Kernel Module) technology, a position of intercepting system call is positioned between a VFS (Virtual File system) layer and a detailed file system so as to acquire more information related to file operation and provide more accurate and useful monitoring information. The system call can be intercepted without the need of correcting a system call table, so that the potential safety hazards brought by the traditional method of correcting the system call table are avoided; a shared memory mechanism is adopted to increase the communication speed of a kernel module and a user progress, and the data volume of communication transmission; key files and progresses needing to be monitored are selected by a user so as to improve the usability, the flexibility and the high efficiency of the system, and the demands of the user on malicious code analysis are well met; the selected malicious code progresses and a plurality of important key files are monitored so as to avoid great performance loss of the system and improve the operation speed of the analysis system.
Owner:INST OF COMPUTING TECH CHINESE ACAD OF SCI
Complex likelihood ratio track-before-detect method based on dynamic planning
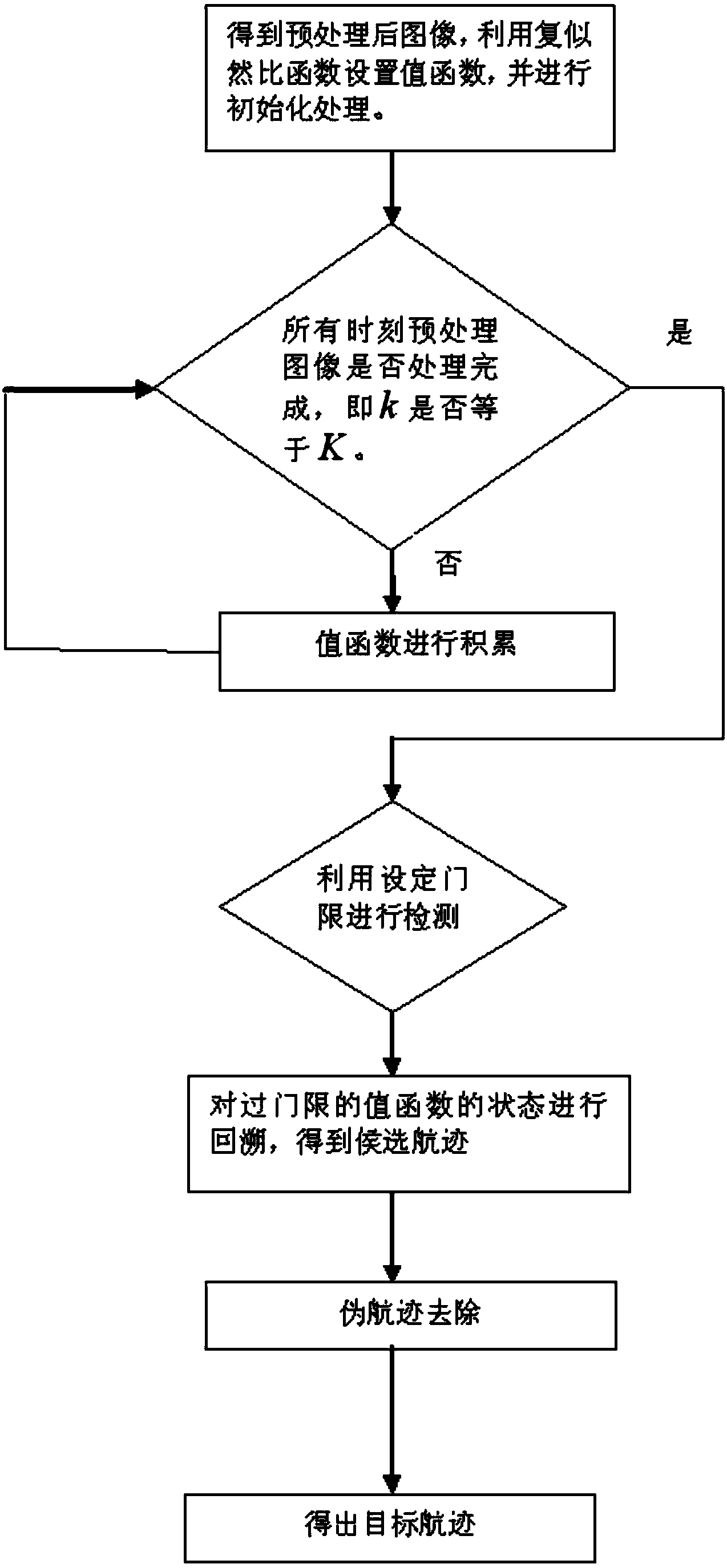
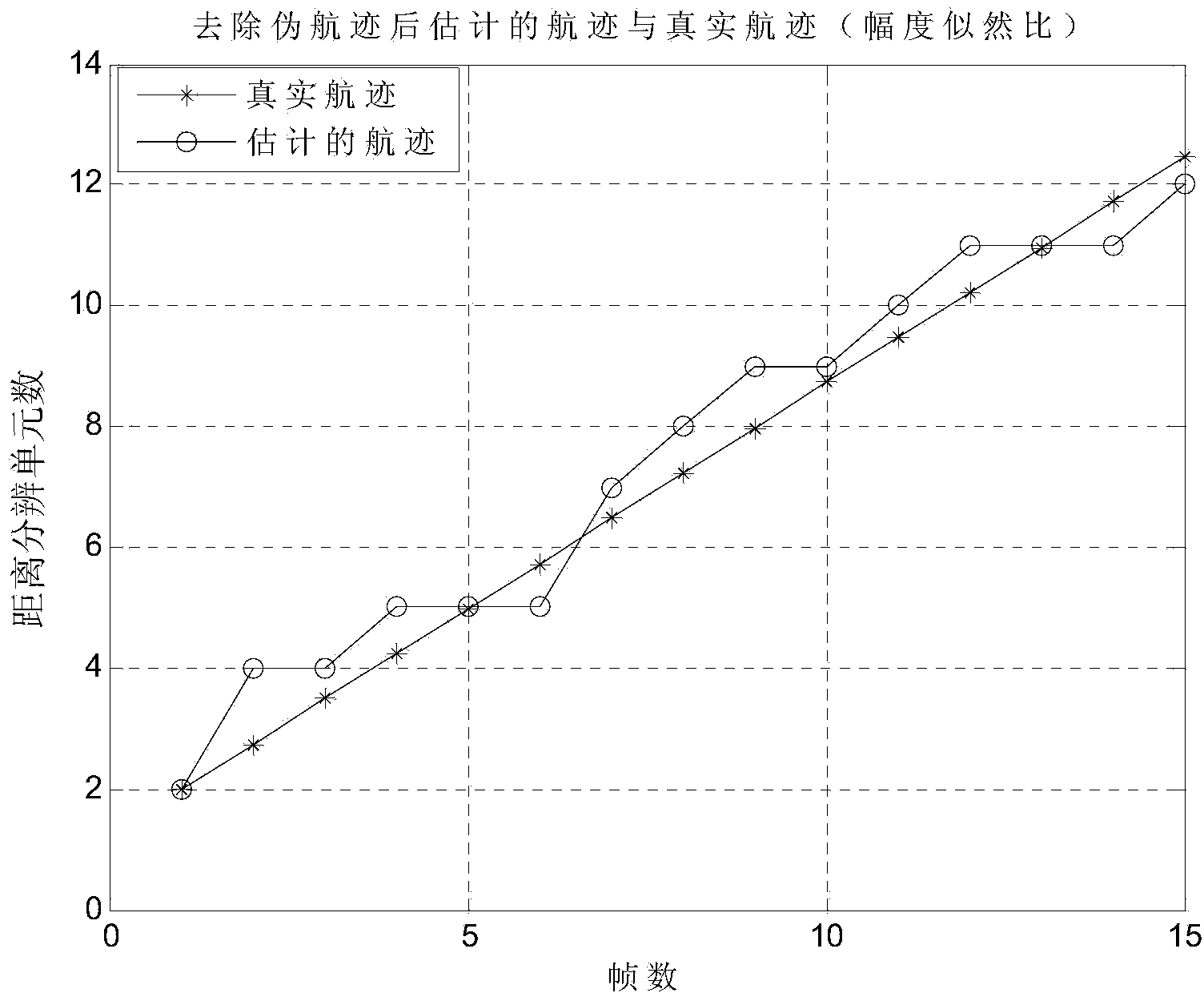
ActiveCN104007422AReduce calculationSatisfy real-timeRadio wave reradiation/reflectionDynamic planningTrack-before-detect
The invention belongs to the technical field of radar target detection tracking, and particularly relates to a complex likelihood ratio track-before-detect method based on dynamic planning. The method includes the following steps of receiving radar echo data by means of radar, preprocessing the radar echo data to obtain a preprocessed image, carrying out track-before-detect by means of a dynamic planning method according to the preprocessed image to obtain a target track, building a complex likelihood ratio function according to the preprocessed image when track-before-detect is carried out in the dynamic planning method, and building a value function of the dynamic planning method according to the complex likelihood ratio function.
Owner:XIDIAN UNIV
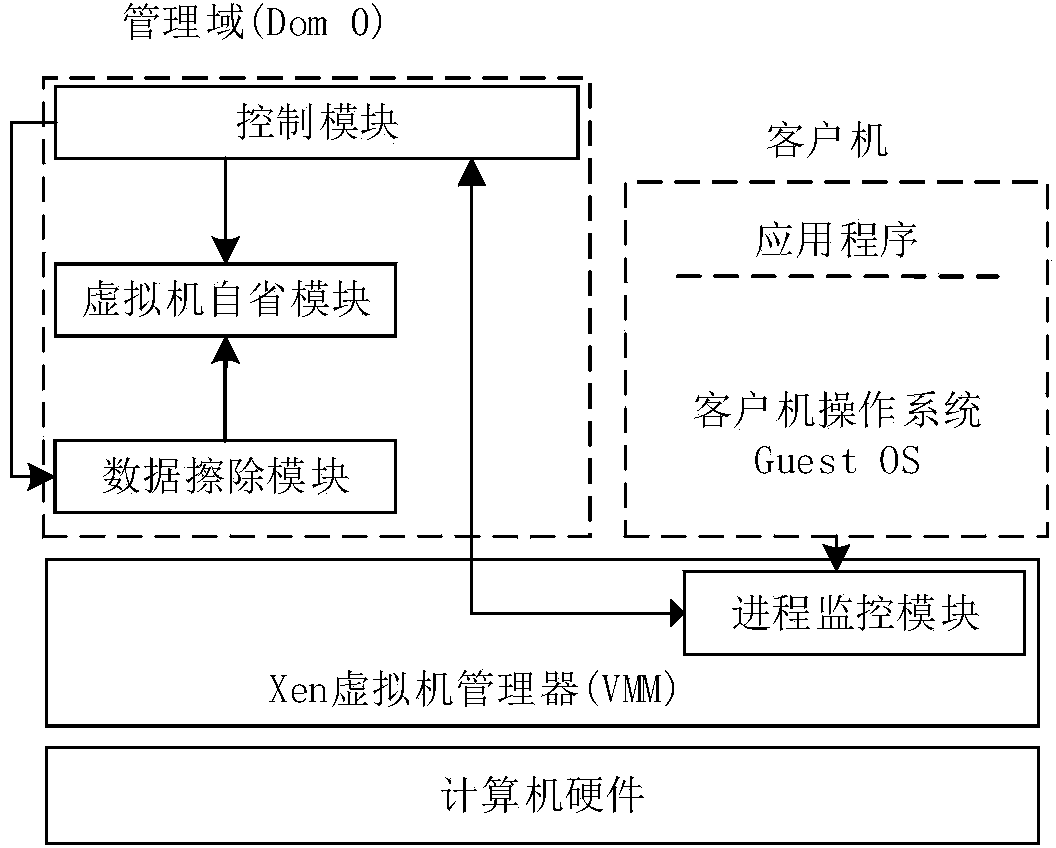
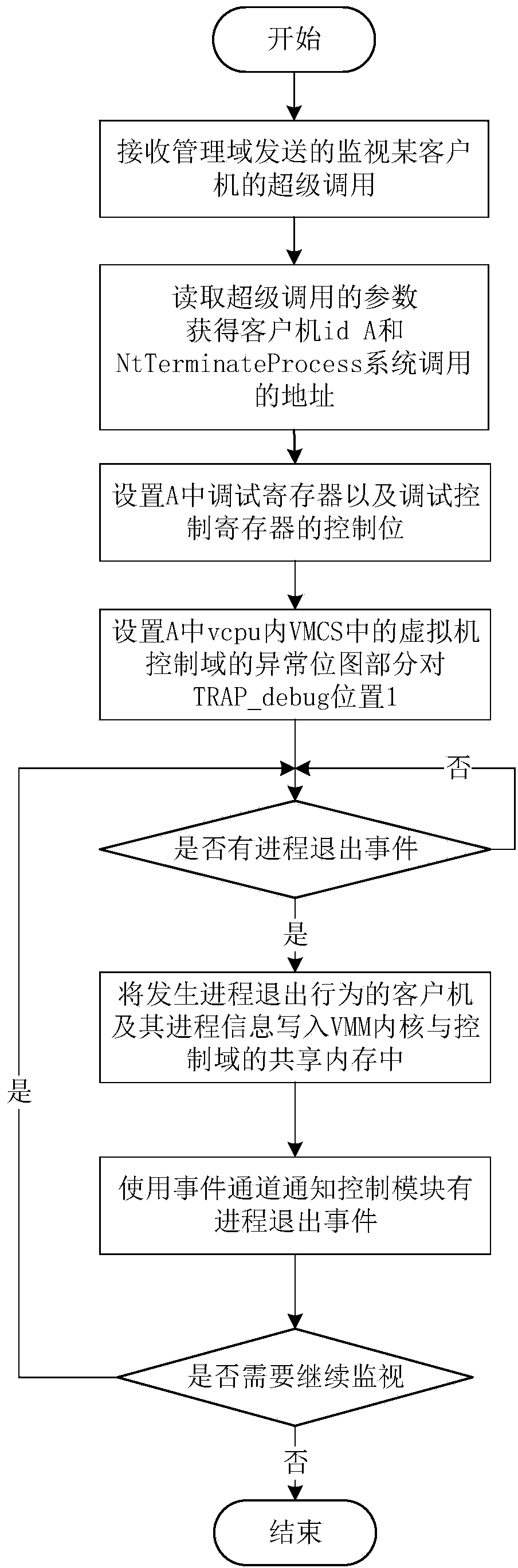
Data wiping system in virtualization environment and method thereof
ActiveCN103996003ANo effect on operationOperation impactDigital data protectionPlatform integrity maintainanceVirtualizationUser privacy
The invention relates to a data wiping system in a virtualization environment and a method thereof, and belongs to the field of data safety and user privacy in cloud computing. Based on a Xen virtualization framework, the data wiping system comprises a process monitoring module, a control module, a virtual machine introspection module and a data wiping module. The control module, the virtual machine introspection module and the data wiping module are deployed in a management field, and the process monitoring module is deployed in a virtual machine manager, namely a VMM kernel. The data wiping system in the virtualization environment and the method thereof are used for reducing the threats to sensitive data stored in an internal storage when a user client operates, a time window which is attacked by the sensitive data is shortened at a possibly small cost, and the security of the sensitive data in the user client is guaranteed.
Owner:AVICIT CO LTD
Systems and methods for roster management in fantasy sports contest applications
InactiveUS20130303291A1Add featureAvoid performance lossVideo gamesSpecial data processing applicationsEngineeringTeam Roster
The fantasy sports contest application of the present invention alerts the user of necessary roster changes before an upcoming fantasy sports competition. The fantasy sports contest application may evaluate the user's team roster before an upcoming fantasy sports competition to ensure that all roster spots on the team roster are filled with athletes available for real-life competitions. The fantasy sports contest application may also identify roster changes and roster transactions that may be beneficial to a user's fantasy sports contest team roster.The fantasy sports contest application may recommend roster changes and roster transactions to the user by evaluating the performance of athletes using performance criteria. The performance criteria can be based on the past performance of athletes, either overall, or for certain situations. The performance criteria may he predefined by the system, user-editable, or any suitable combination thereof.
Owner:ROVI TECH CORP
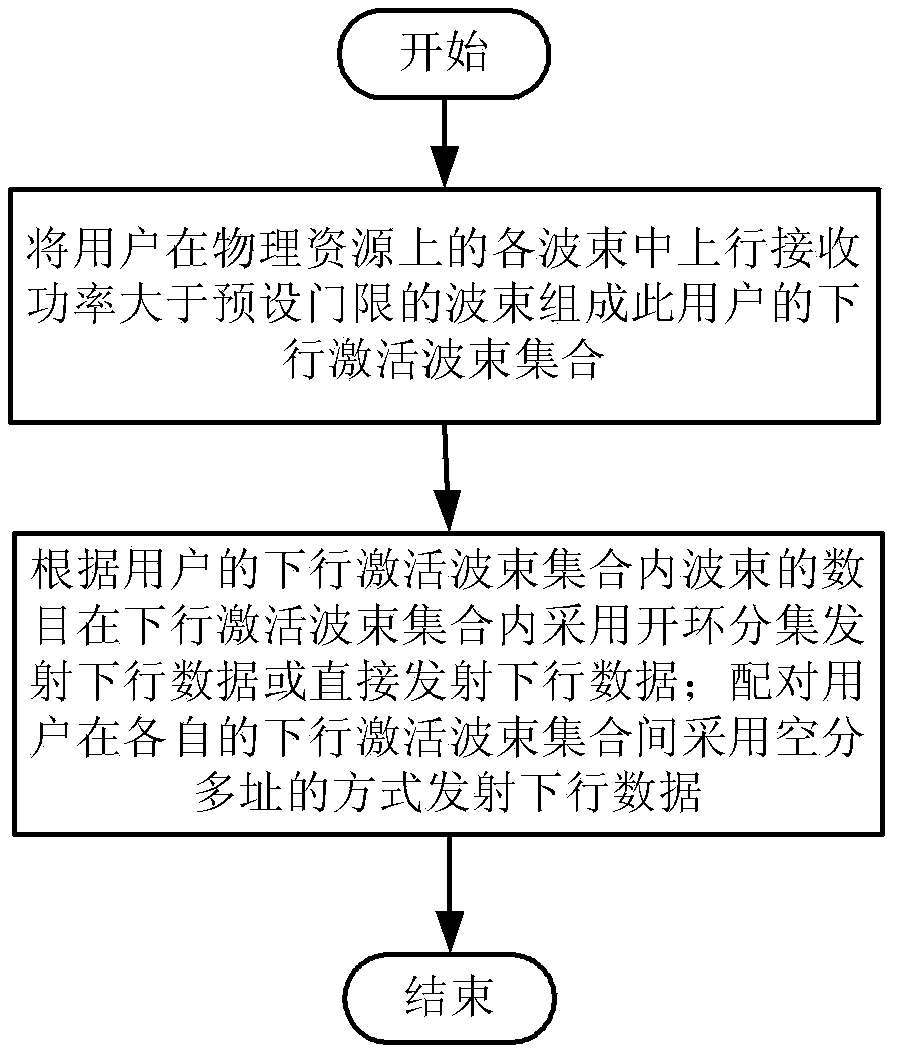
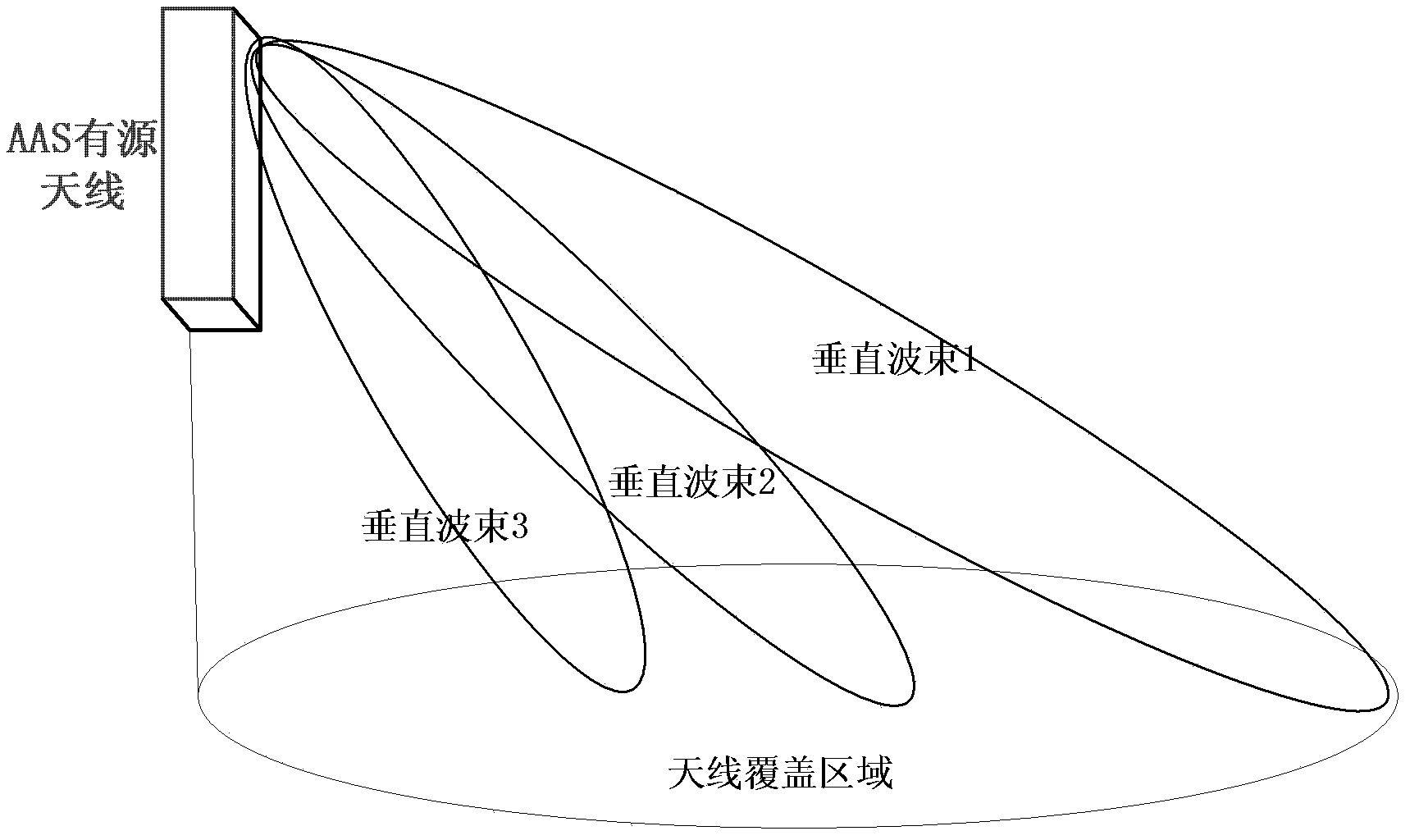
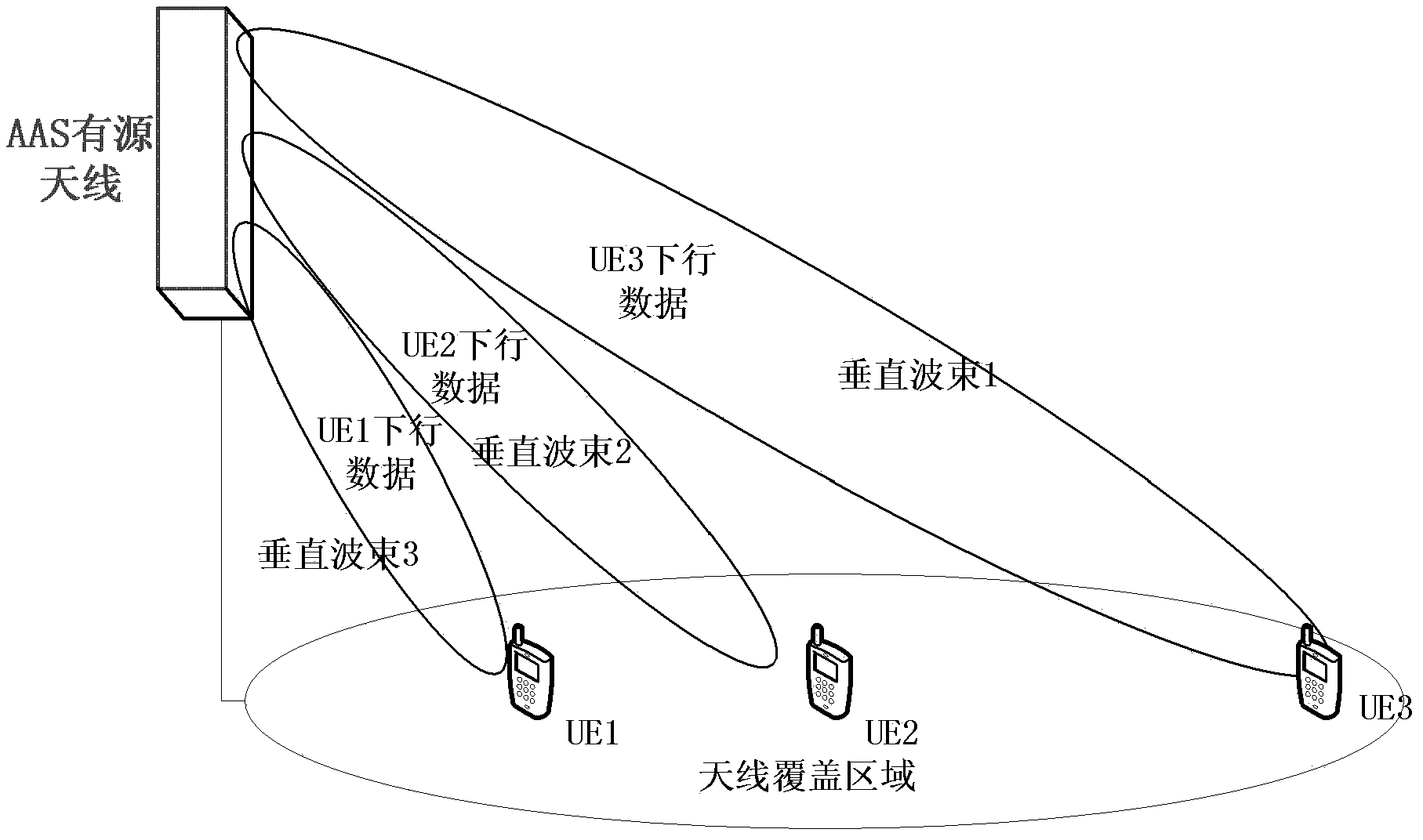
Method and device for realizing downlink data transmission by utilizing active antenna system
ActiveCN103516410AReduce distractionsIncrease system capacitySpatial transmit diversityData transmissionTraffic volume
The invention discloses a method and device for realizing downlink data transmission by utilizing an active antenna system. The method is characterized in that: constituting wave beams, the uplink receiving power is larger than a preset threshold, of all wave beams in physical resource of a user into a downlink activation wave beam collection of the user; according to the number of the wave beams in the downlink activation wave beam collection of the user, sending downlink data of the user by utilizing open loop diversity technique or directly sending the downlink data of the user in the downlink activation wave beam collection; and sending the downlink data by utilizing a space division multiple access mode in downlink activation wave beam collections of matched users, wherein the users, the downlink activation wave beam collections do not have intersections, form the matched users. Multi-beam activation determination and the pen loop diversity sending and combined and the method is utilized to solve the problem of related interference in vertical wave beams or horizontal wave beams, thereby preventing performance loss of a downlink data channel due to interference in the LTE system, and improving data traffic and system performance.
Owner:ZTE CORP
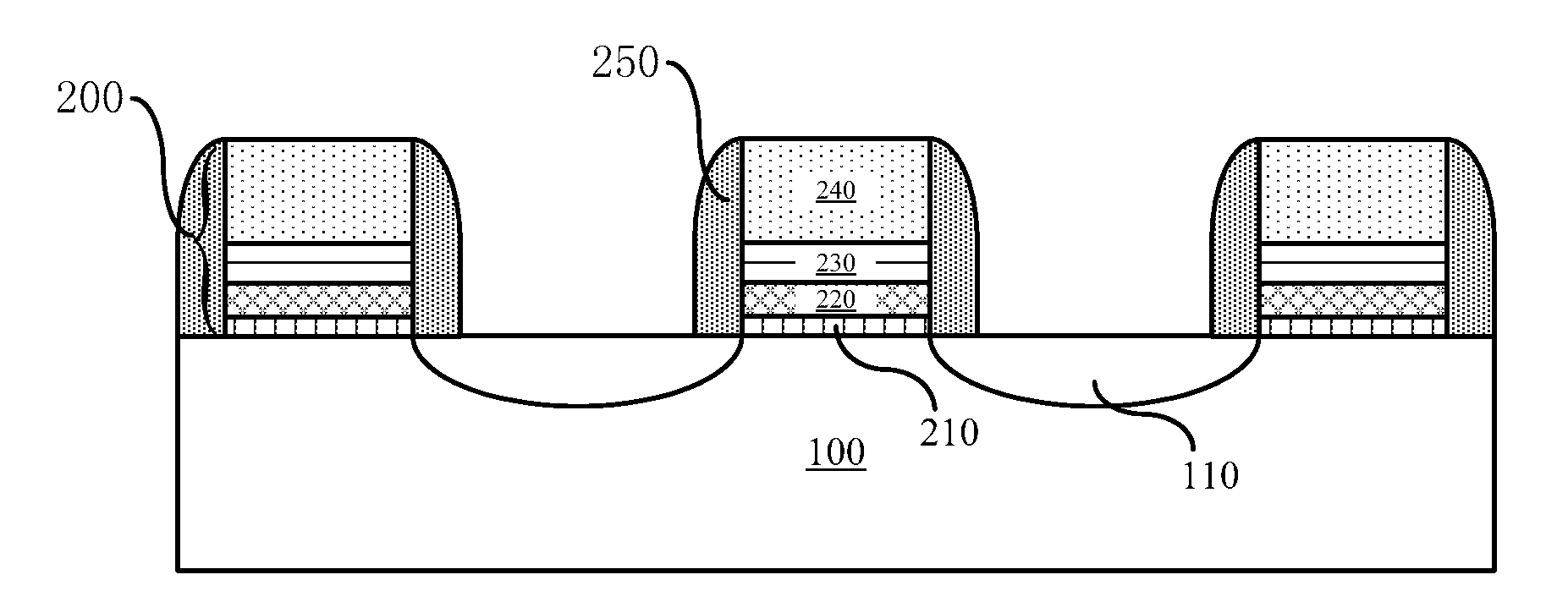
Semiconductor structure and method for manufacturing the same
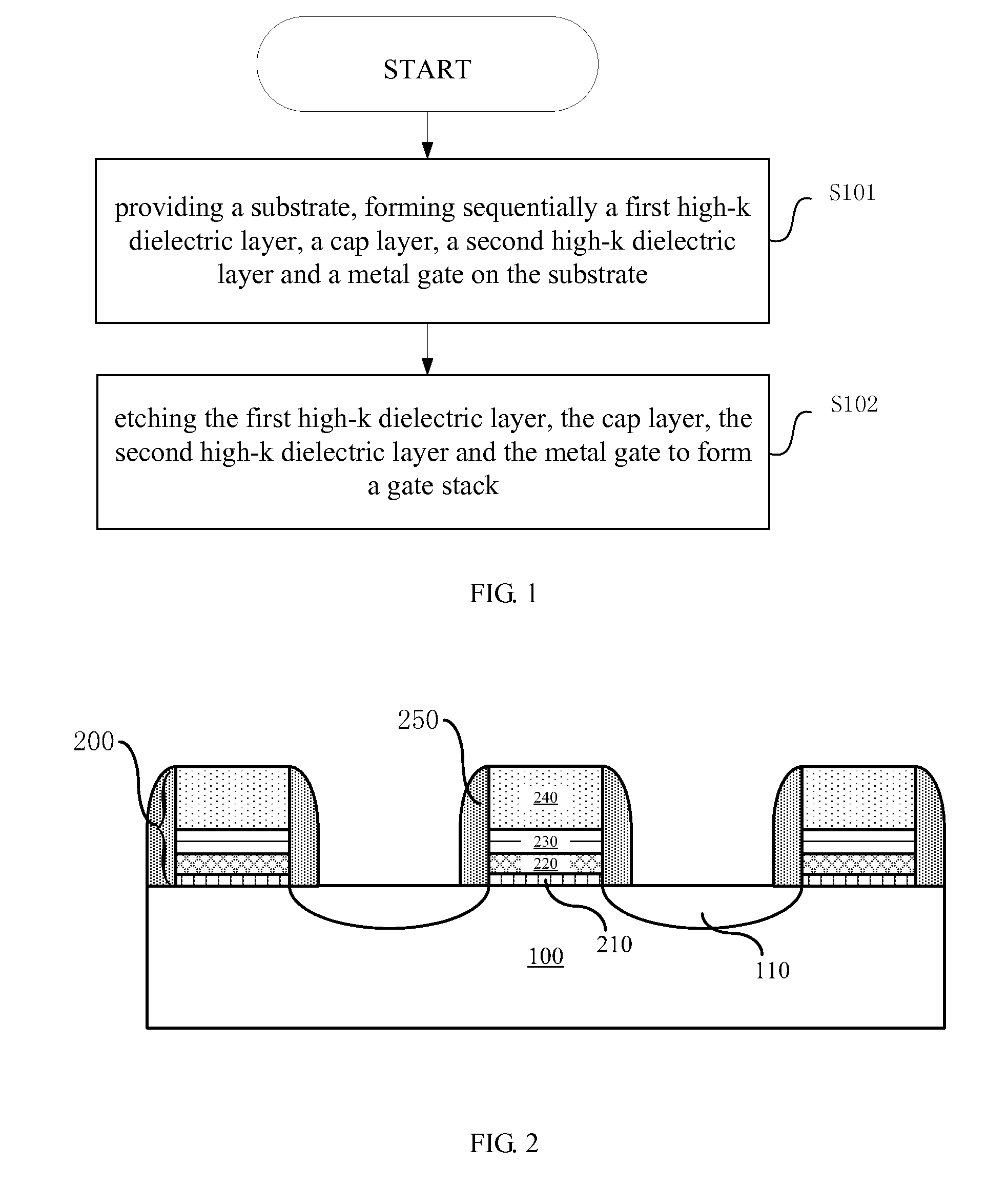
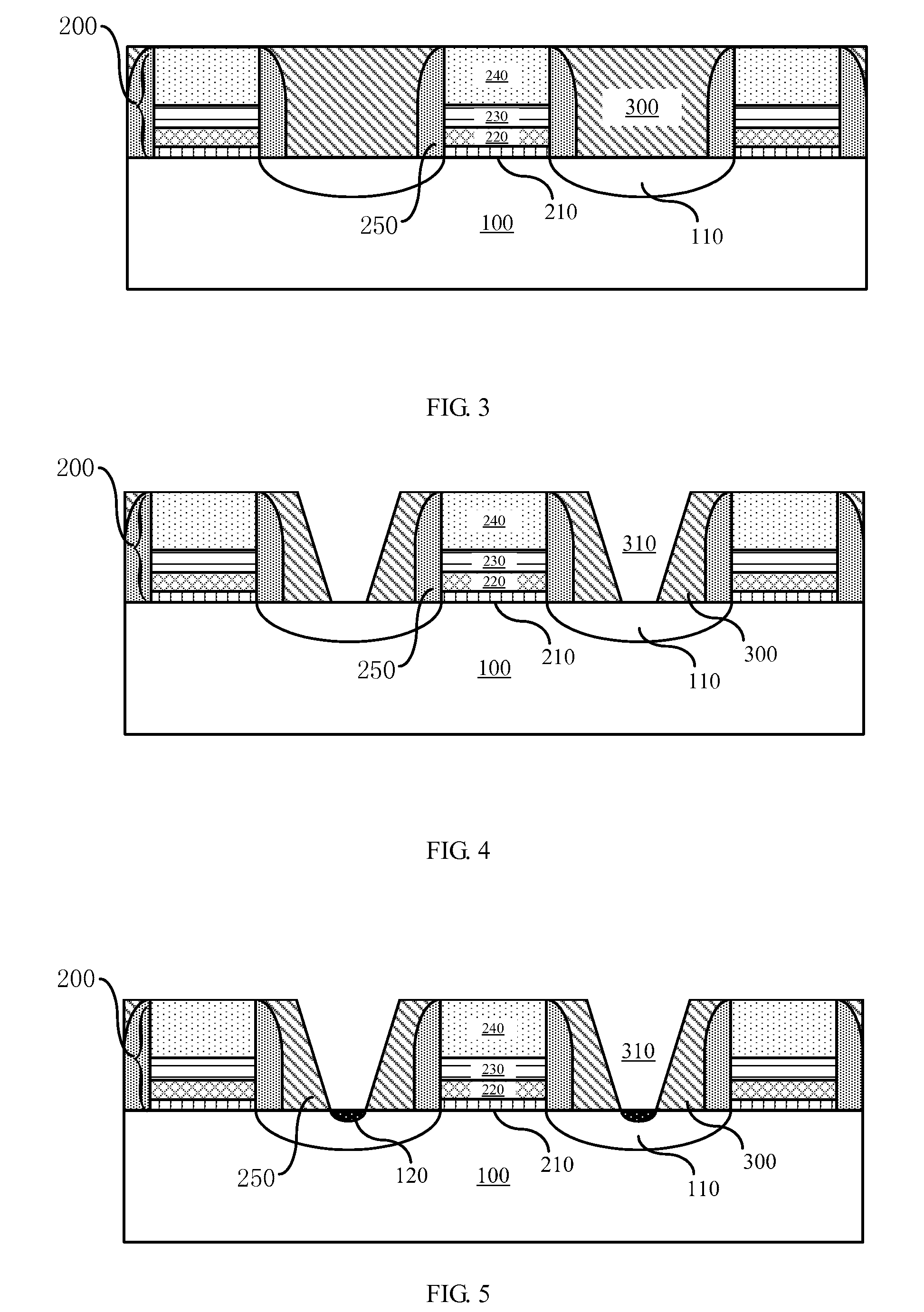
InactiveUS20120313158A1Impairs performance of semiconductor deviceAvoid adjustmentTransistorSemiconductor/solid-state device manufacturingSemiconductor structureGate stack
The present invention provides a semiconductor structure and a method for manufacturing the same. The method comprises: providing a substrate, forming sequentially a first high-k dielectric layer, an adjusting layer, a second high-k dielectric layer and a metal gate on the substrate, etching the first high-k dielectric layer, the adjusting layer, the second high-k dielectric layer and the metal gate to form a gate stack. Accordingly, the present invention further provides a semiconductor structure. The present invention proposes to arrange an adjusting layer between two layers of high-k dielectric layer, which effectively avoids reaction of the adjusting layer with the metal gate because of their direct contact, so as to maintain the performance of semiconductor devices.
Owner:INST OF MICROELECTRONICS CHINESE ACAD OF SCI +1
Rate matching method and device
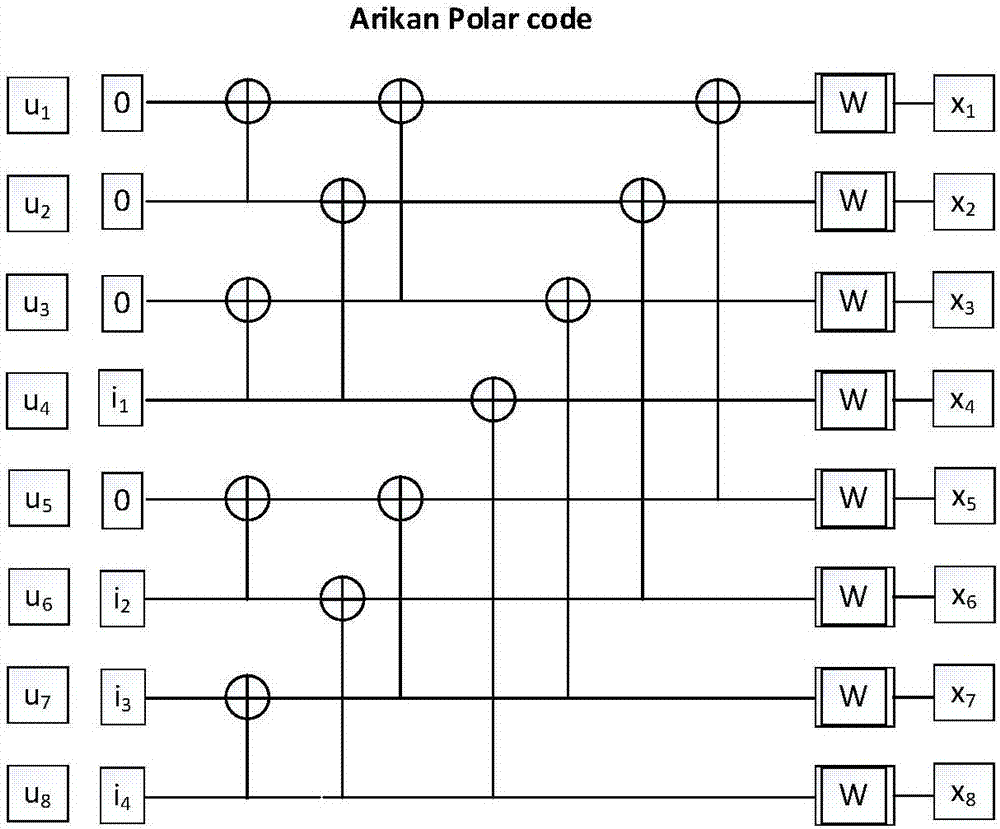
ActiveCN107342845AAvoid performance lossNetwork traffic/resource managementChannel coding adaptationPunchingComputer science
The application discloses a rate matching method. The method comprises the following steps: network equipment determines transmission bit rate R, wherein R is equal to K / M, K relates to the length of an information bit, M relates to the length of a target code, and K and M are positive integers; if the transmission bit rate R is greater than or equal to a first bit rate threshold, the network equipment determines to adopt a shortening mode for a bit sequence of which the length is N, and if the transmission bit rate R is smaller than the first bit rate threshold, the network equipment determines to adopt a punching mode for the bit sequence of which the length is N, N is the length of a mother code and is a positive integer; the network equipment performs Polar coding for the bit sequence of which the length is N by adopting a polar code to obtain a first coded sequence of which the length is N, and the network equipment performs shortening or punching for the first coded sequence to obtain a second coded sequence of which the length is M. The application also provides rate matching equipment corresponding to the method. By adopting the above method and equipment, the punching / shortening mode can be flexibly selected, and the performance loss caused by the punching / shortening process can be overcome.
Owner:HUAWEI TECH CO LTD
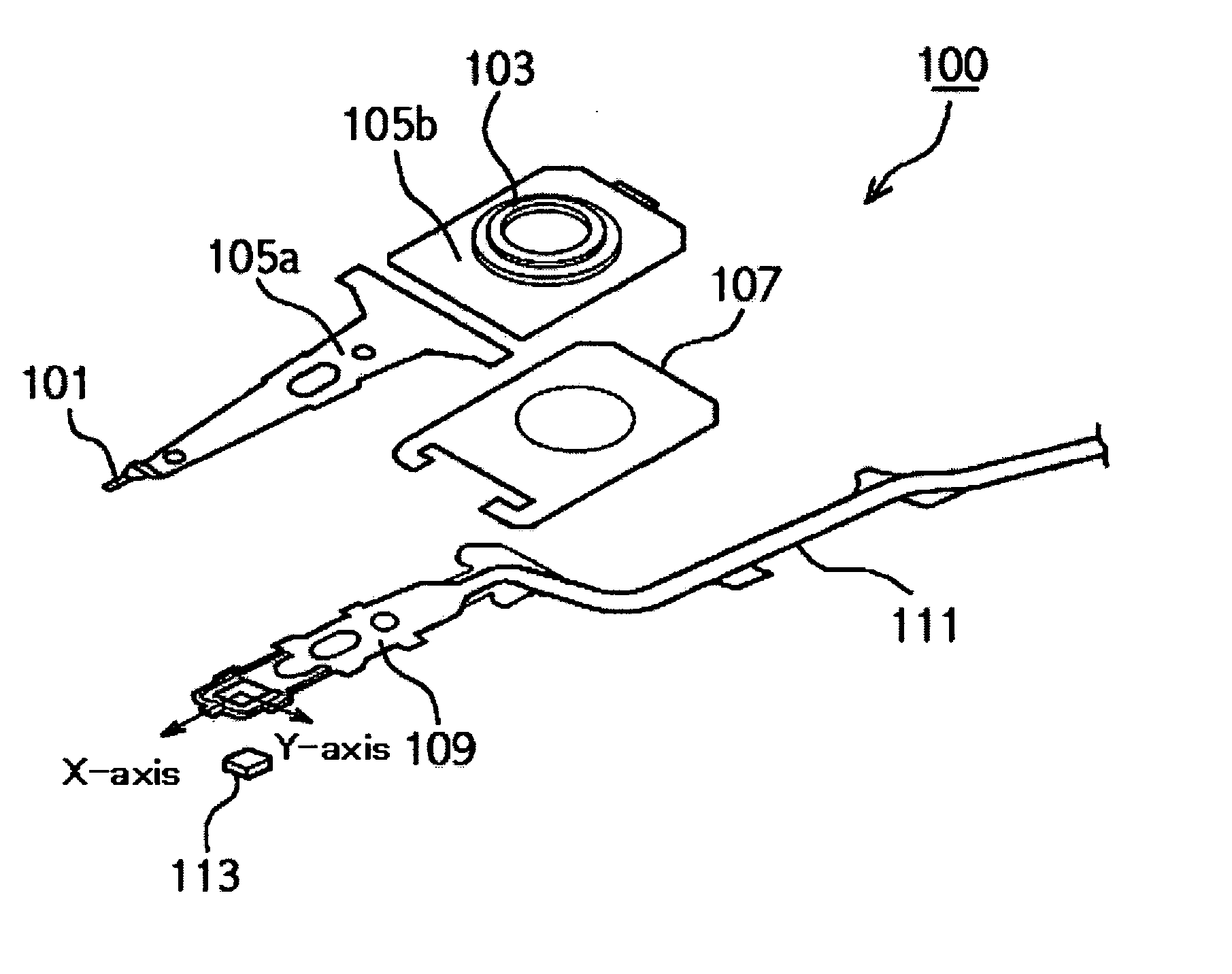
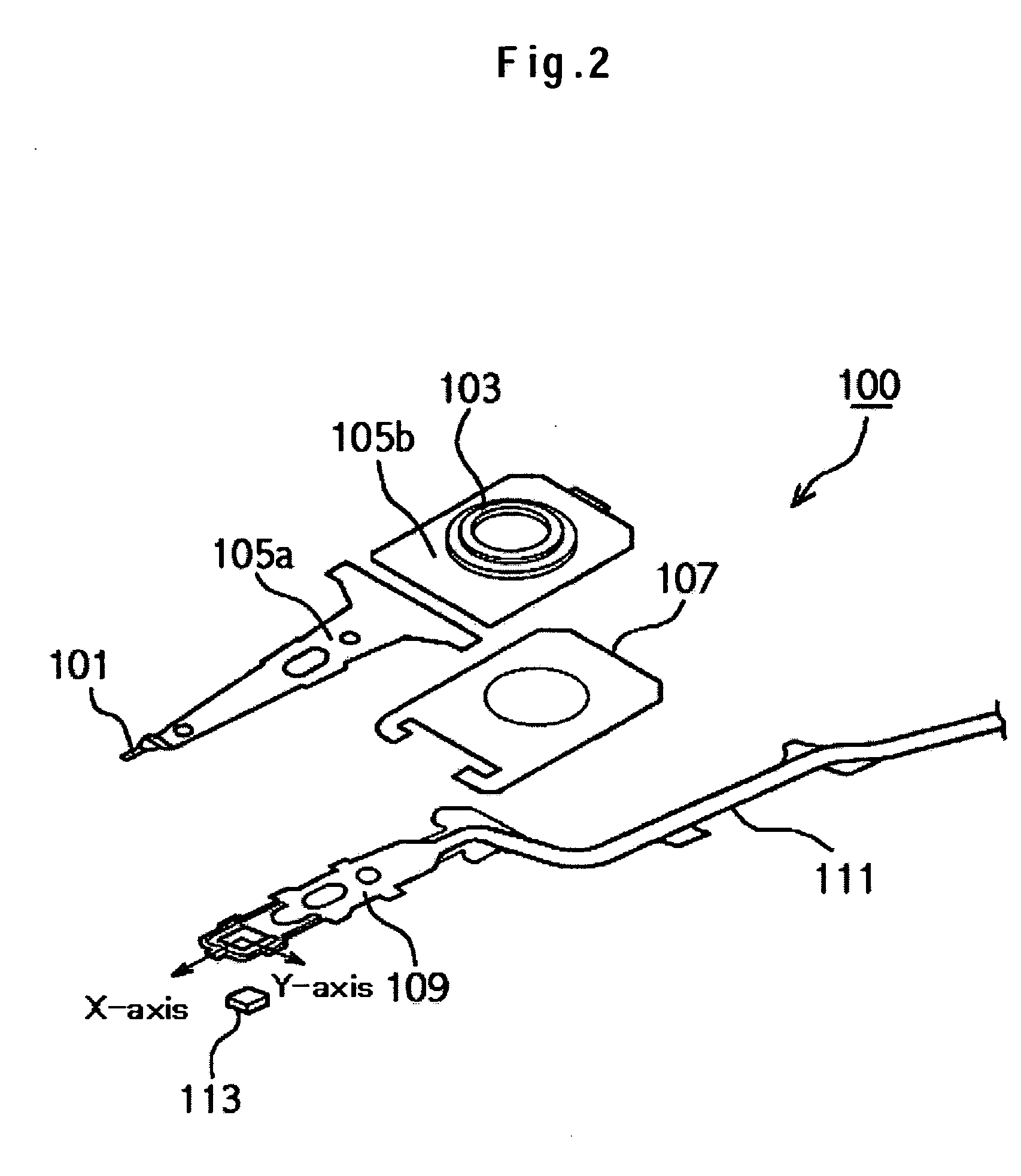
Femto slider for small form factor hard disk drive
InactiveUS20050275971A1Avoid performance lossLow linearityRecord information storageFluid-dynamic spacing of headsHard disc driveGram
A magnetic disk drive includes a magnetic disk and a femto slider. The magnetic disk has a minimum track linear velocity of 1 to 5 m / s. In one embodiment, the magnetic disk drive includes a negative pressure type femto slider and adopts a load / unload method. A gram load “GL” of a head suspension assembly HSA is set at a value exceeding about 3 mN and smaller than about 15 mN and a pitch static attitude “PSA” (deg) and pitch stiffness “Kp” (Nm / deg) satisfy the expression ((PSA×Kp) / GL)<0.25 mm. As a result, it is possible to prevent the femto slider from assuming a meta-stable flying high state referred to as a bi-stable height. Further, by setting the pitch static attitude “PSA” at a value of larger than 0 deg, it is possible to prevent the slider from assuming a state of meta-stable contact with the magnetic disk surface referred to as semi-stable drag.
Owner:HITACHI GLOBAL STORAGE TECH NETHERLANDS BV
Energy-saving stove
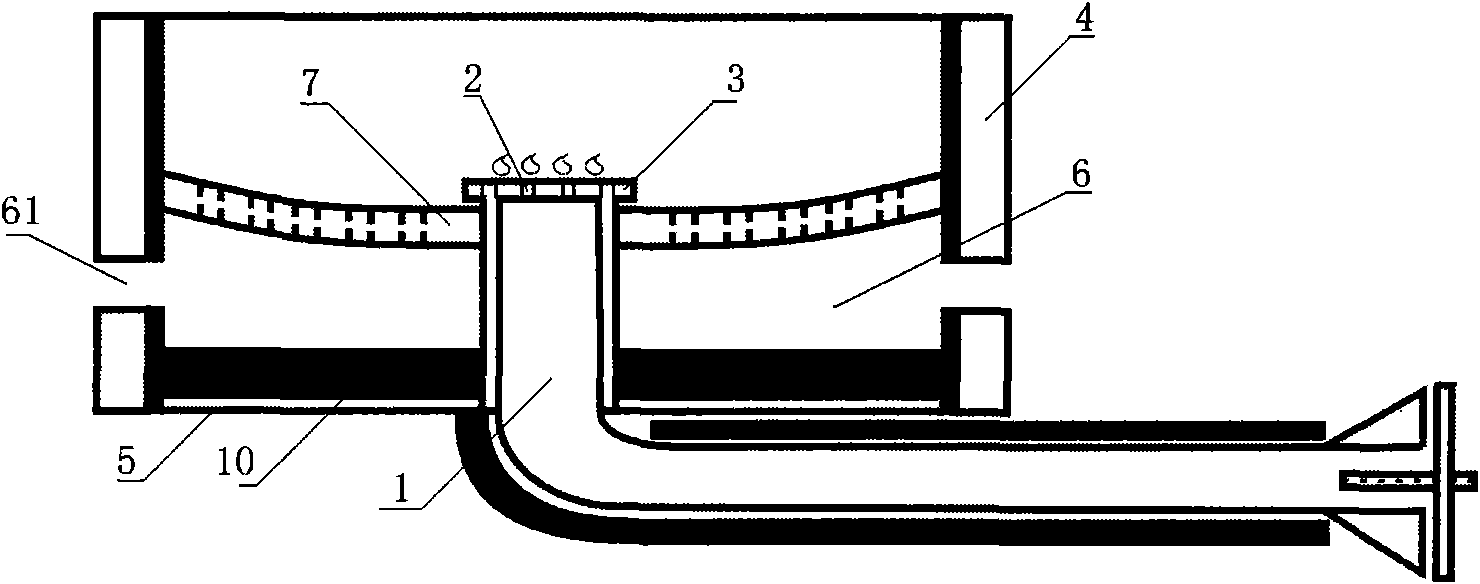
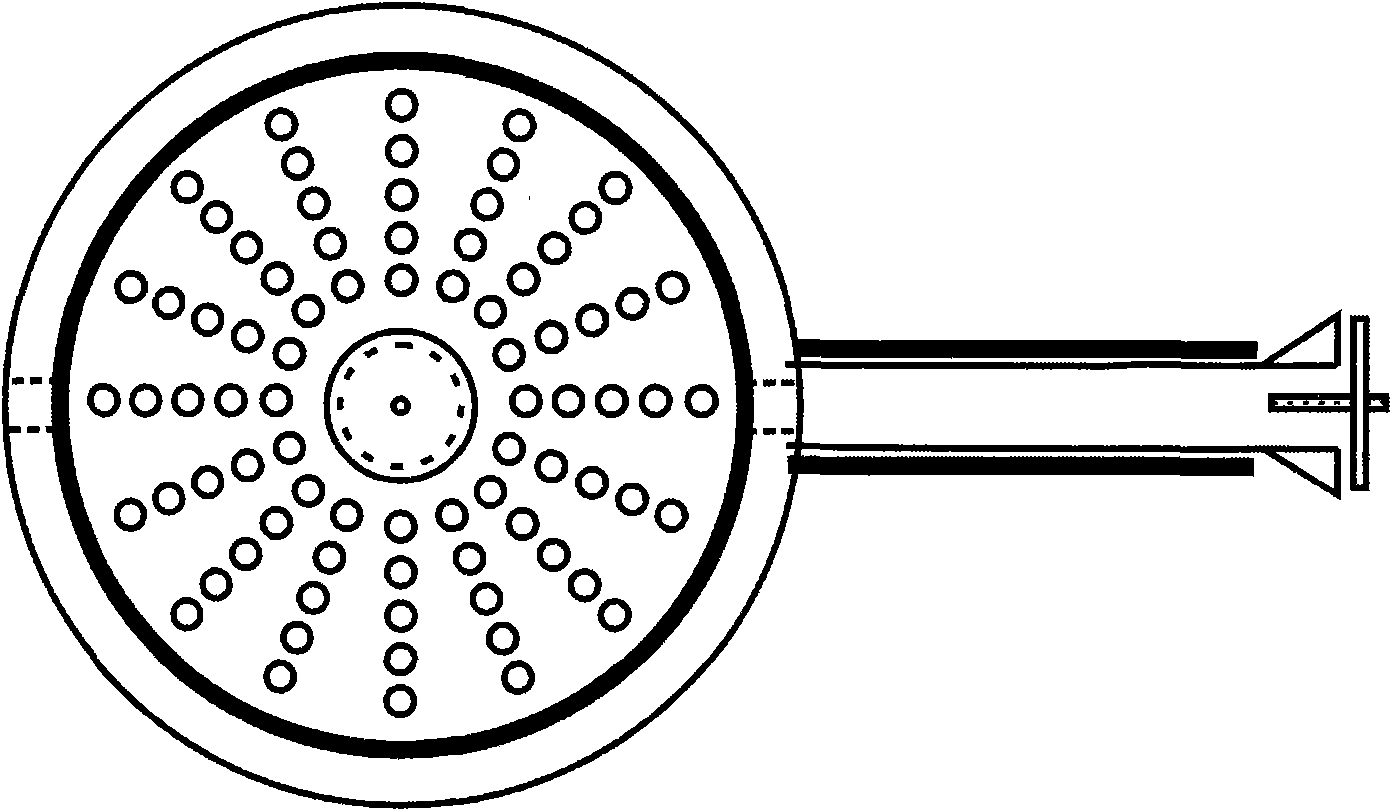
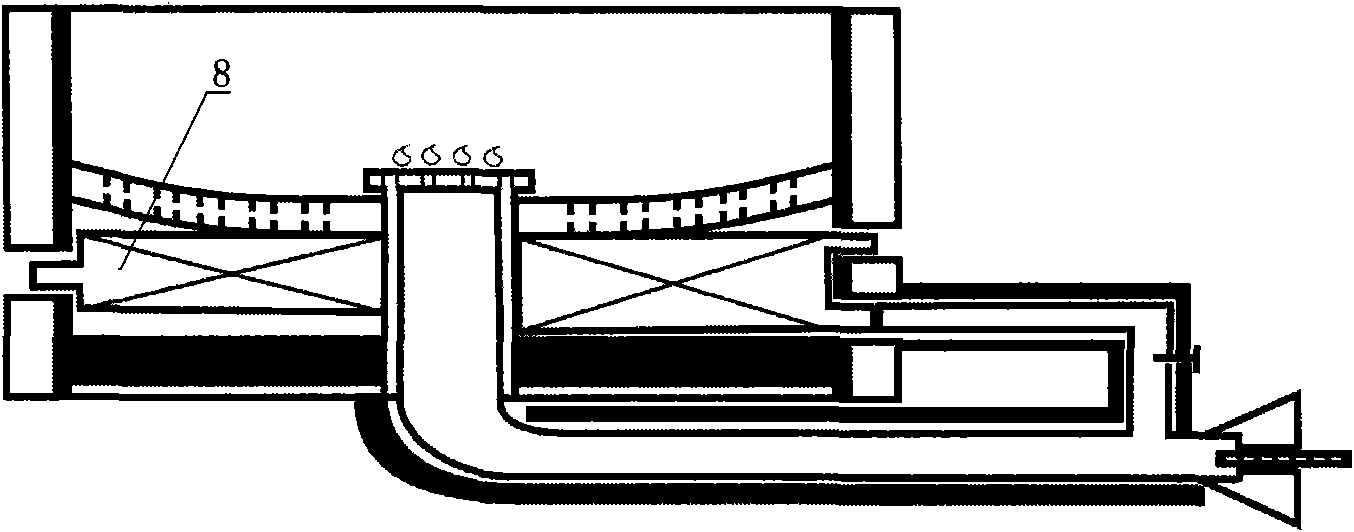
InactiveCN101581455AAvoid performance lossHigh flame temperatureDomestic stoves or rangesLiquid heating fuelCombustionHeat losses
The invention provides an energy-saving stove. The stove comprises a mixing chamber of fuel and air, the mixing chamber is communicated with a jet hole on a combustion head; the combustion head is arranged in a furnace tank circled by a stove ring and a stove bottom; the closed furnace is provided with a smoke gas outlet; a smoke gas flow passage is formed between the combustion head and the smoke gas outlet; the smoke gas flow passage is provided with porous thermal storage radiant panels for stopping. The energy-saving stove has the advantages of small heat loss and high heat efficiency.
Owner:ZHEJIANG UNIV OF TECH
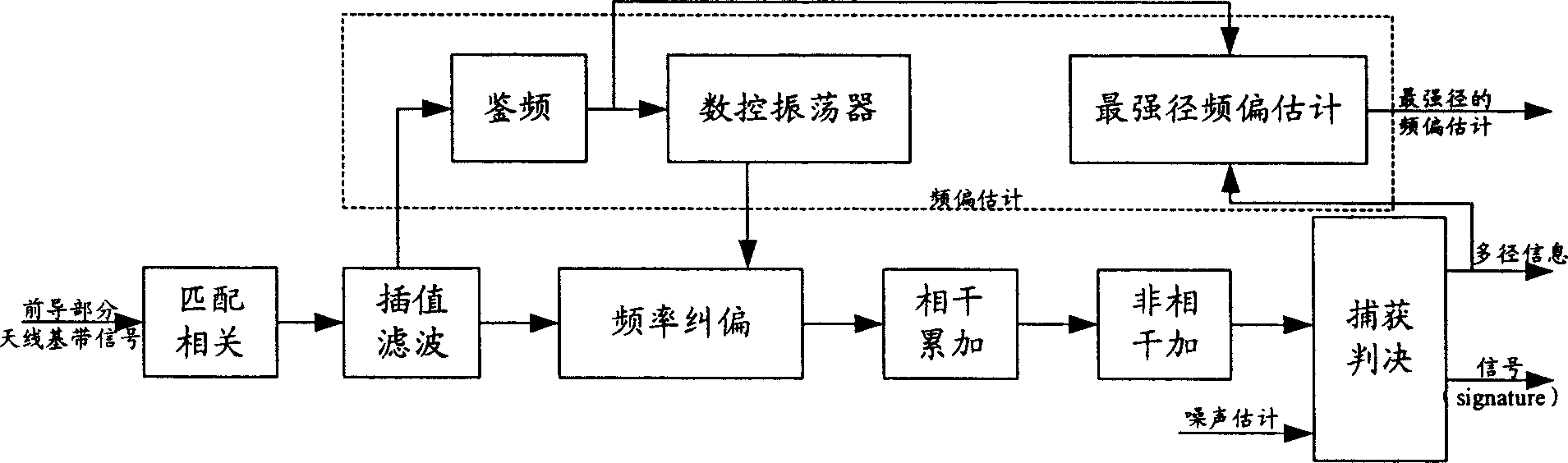
Method and device for realizing automatic frequency control
ActiveCN1859019AHigh control precisionGuaranteed performanceRadio transmissionAutomatic frequency controlComputer science
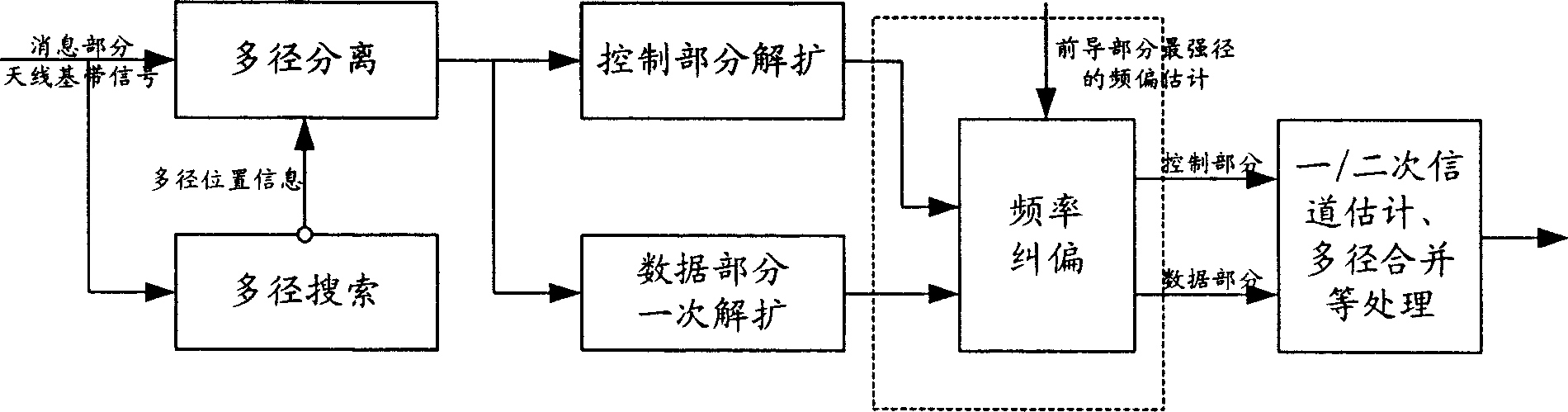
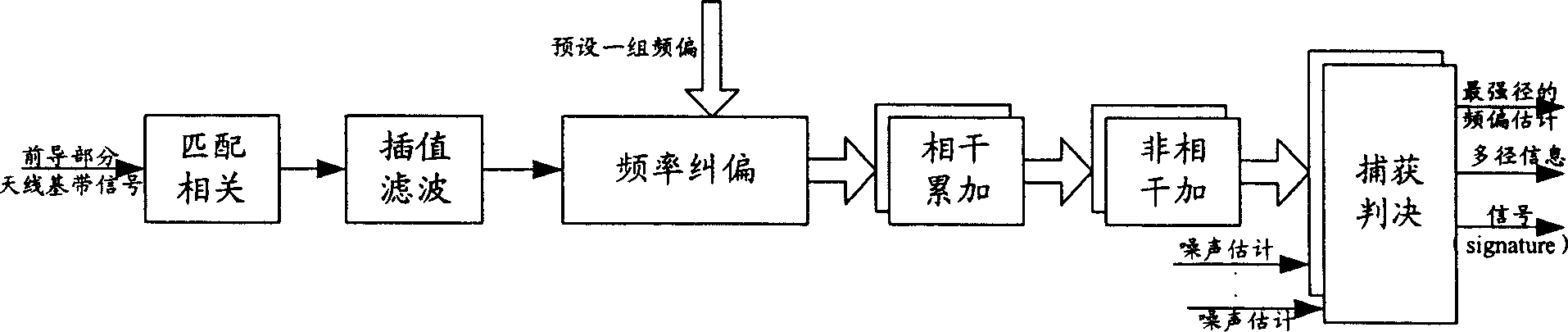
This invention discloses a method for realizing AFC including: carrying out multi-path search by the precursor part and the message part of a channel to get multi-path information to be used to de-spread the control part and the data part to get information of the control part and the data part then to carry out frequency deviation estimation to the de-spread information of the control part to get the deviation information, then carrying out frequency deviation correction to the de-spread information of the control part and the data part by the deviation frequency to realize AFC, a device for realizing automatic frequency control is also disclosed.
Owner:HUAWEI TECH CO LTD
Neodymium iron boron magnetic material with excellent magnetic performance
InactiveCN103617855AHigh energy productImprove remanenceInorganic material magnetismNiobiumDysprosium
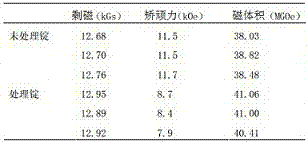
The invention discloses a neodymium iron boron magnetic material with the excellent magnetic performance. The neodymium iron boron magnetic material with the excellent magnetic performance is formed by a main-phase alloy and a secondary-phase alloy through mixing. The main-phase alloy comprises, by weight, 64.5-68.5% of iron, 1.0-1.2% of boron, 30.2-34.3% of neodymium, 0.05-0.4% of niobium and 0.1-0.4% of aluminum. The secondary-phase alloy comprises, by weight, 50.8-54.2% of iron, 0.8-1.2% of boron, 18.9-21.1% of neodymium, 12.8-16.3% of praseodymium, 8.9-11.1% of dysprosium and 0.8-1.2% of copper. The neodymium iron boron magnetic material prepared with the method has the excellent magnetic performance and high intrinsic coercivity.
Owner:NINGBO STAR MATERIALS HI TECH
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com