Task distribution system model of privacy protection space crowdsourcing and realization method
A technology for privacy protection and task allocation, applied in the computer field, it can solve problems such as only considering worker location privacy, not taking it into account, and unsatisfactory allocation results.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0051] The present invention is described in further detail now in conjunction with accompanying drawing. These drawings are all simplified schematic diagrams, which only illustrate the basic structure of the present invention in a schematic manner, so they only show the configurations related to the present invention.
[0052] 1. System model and problem definition
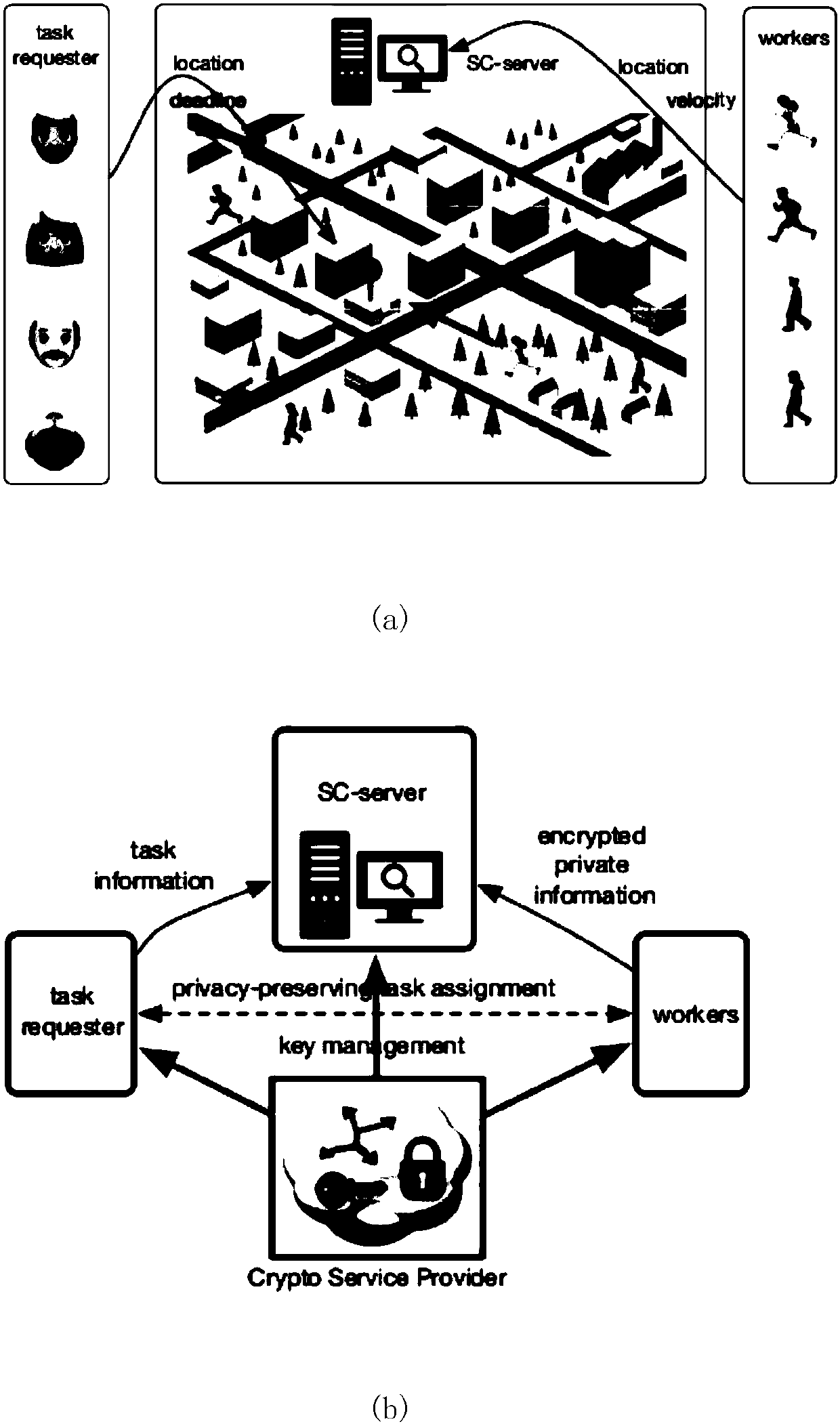
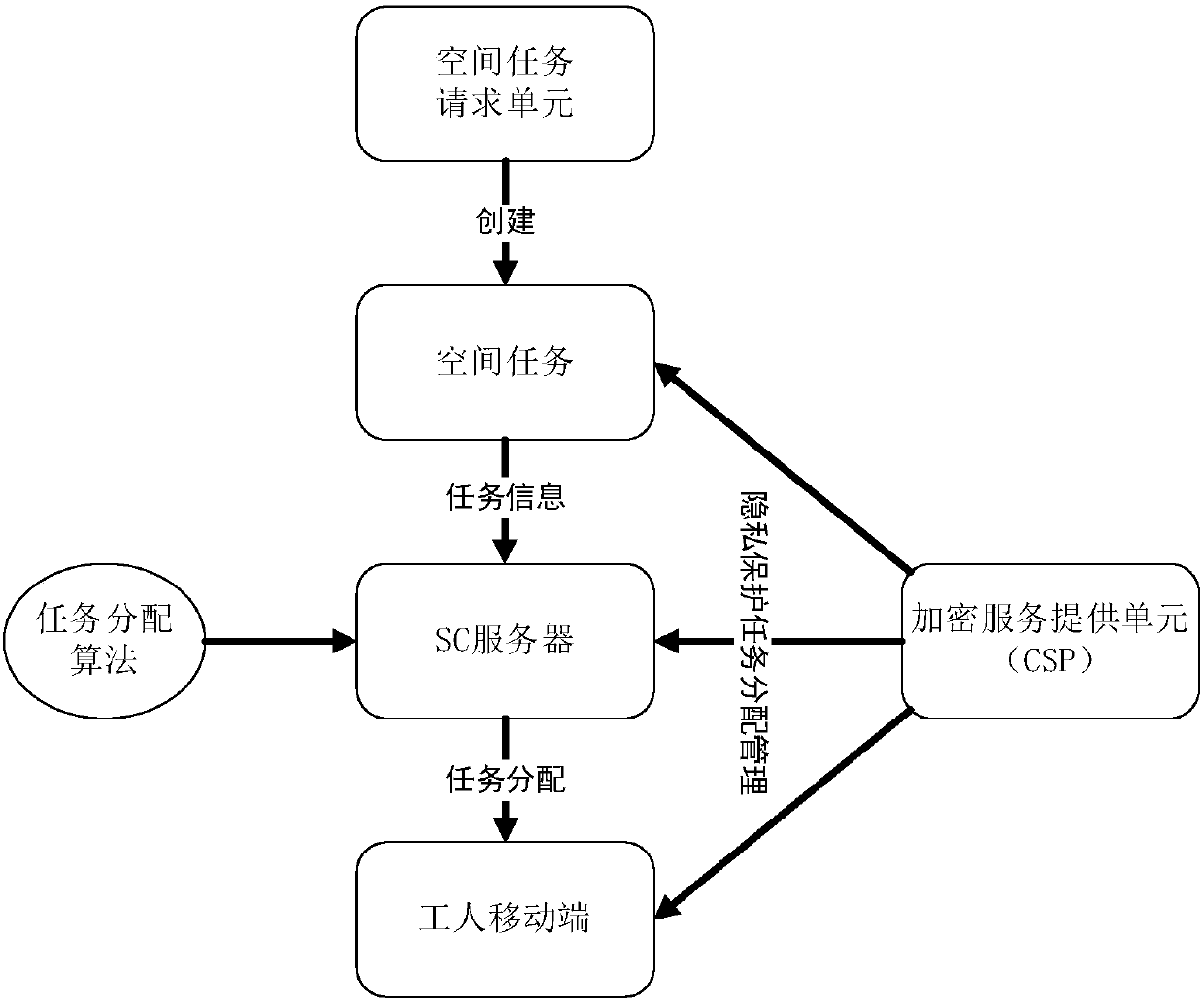
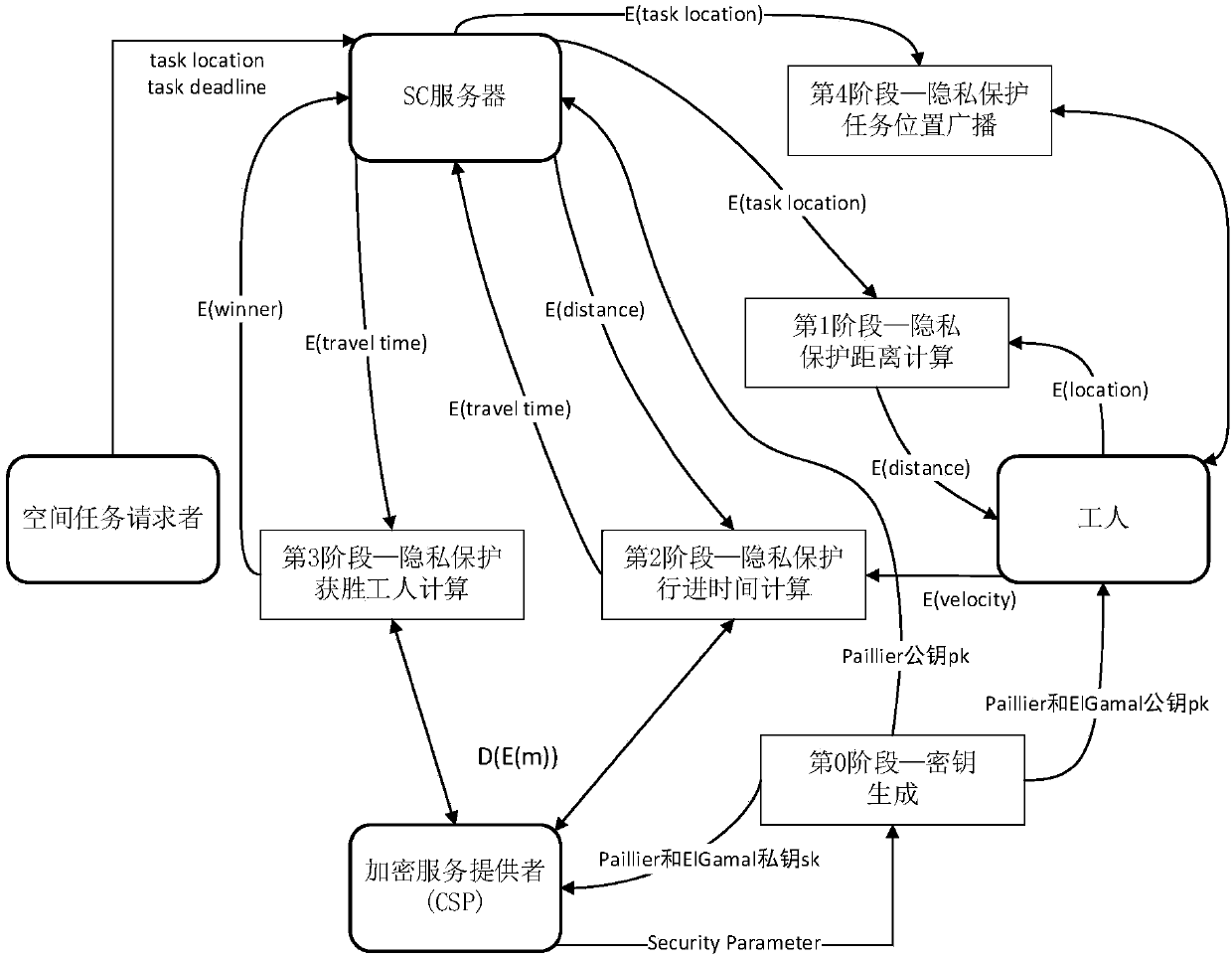
[0053] figure 1 A system model for spatial crowdsourcing is described. For non-private space crowdsourcing (see figure 1 (a) There are three components, namely SC server (SC-server), workers (workers) holding mobile devices and space task requester (taskrequester). The SC server is responsible for assigning appropriate workers to space tasks created by task requesters. Workers need to report their private information (such as location and velocity) to the SC server through their mobile devices. Based on this framework, we give the following definitions.
[0054] Definition 1 (space mission) space mission s ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com