Malicious code analysis method and system under Linux platform
A malicious code and analysis system technology, applied to the malicious code analysis method and system field under the Linux platform, can solve the problems of not being able to obtain information related to malicious code, poor robustness, and instruction trapping, so as to improve speed and avoid performance Loss, the effect of improving usability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
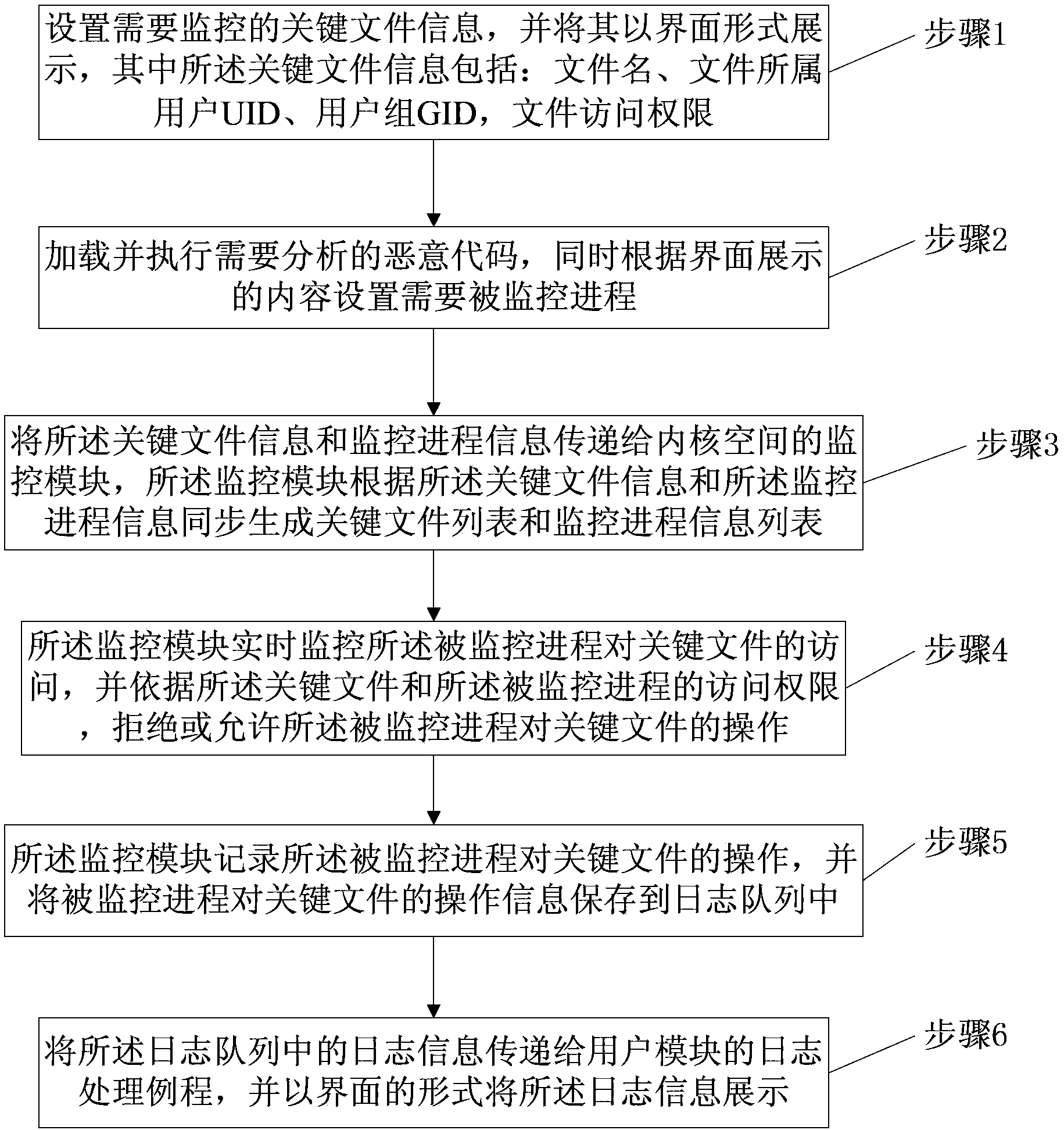
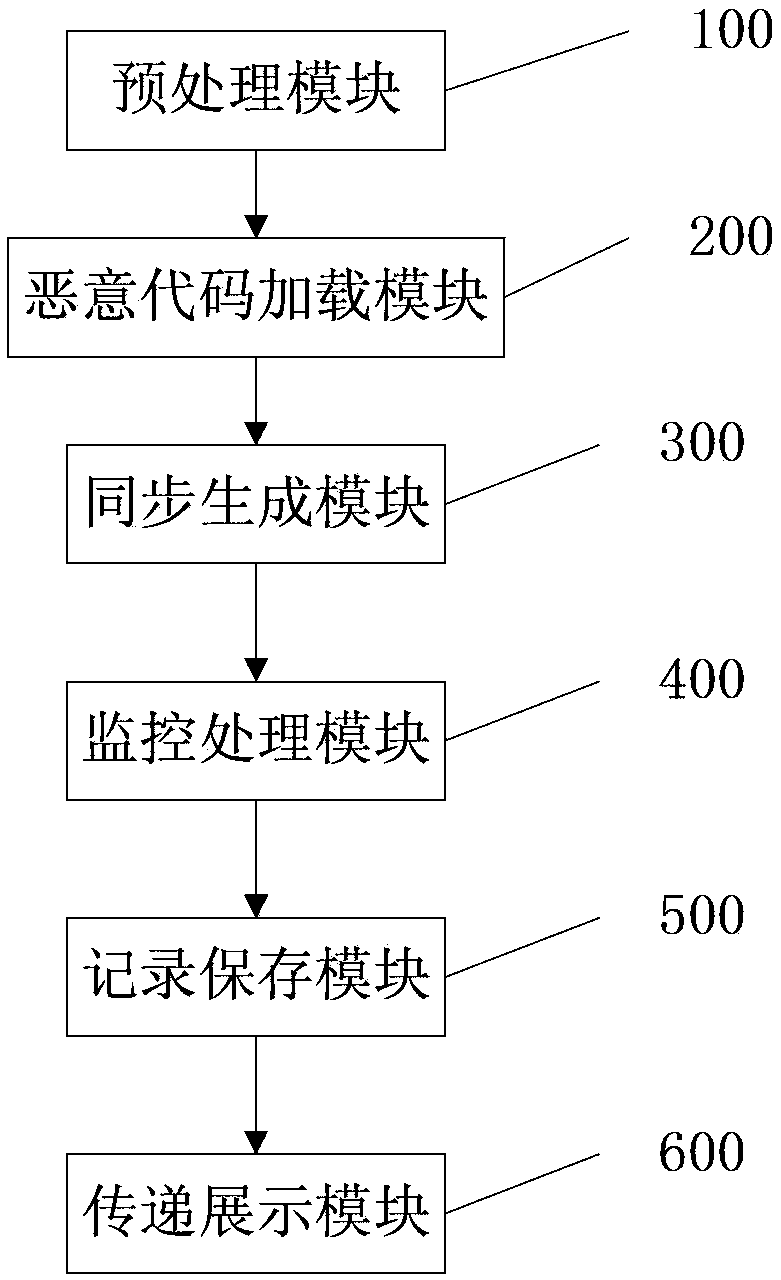
[0064] figure 1 It is a flowchart of the malicious code analysis method under the Linux platform of the present invention. Such as figure 1 As shown, the method includes:
[0065] Step 1, set key file information to be monitored, and display it in an interface, wherein the key file information includes: file name, user UID to which the file belongs, user group GID, and file access rights;
[0066] Step 2, load and execute the malicious code that needs to be analyzed, and set the process to be monitored according to the content displayed on the interface;
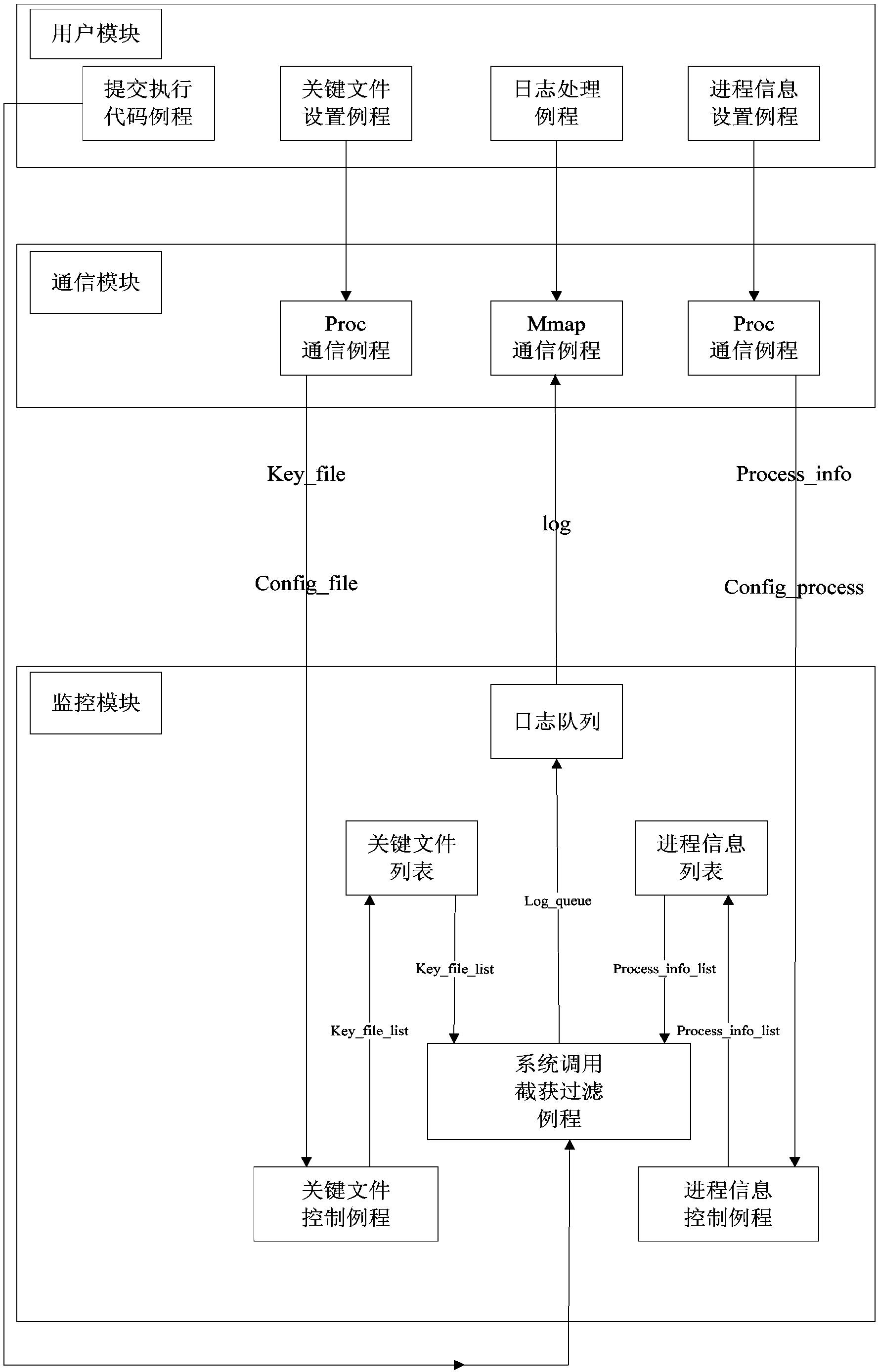
[0067] Step 3, passing the key file information and monitoring process information to the monitoring module of the kernel space, and the monitoring module synchronously generates a key file list and a monitoring process information list according to the key file information and the monitoring process information;
[0068] Step 4, the monitoring module monitors the monitored process's access to the key file in real time, a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com