Data wiping system in virtualization environment and method thereof
A virtualized environment and data erasure technology, which is applied in the field of data security and user privacy in cloud computing, can solve problems such as leakage, sensitive data leakage, and increasing the time window of sensitive data, achieving minimal performance loss, ensuring confidentiality, The effect of strong scalability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
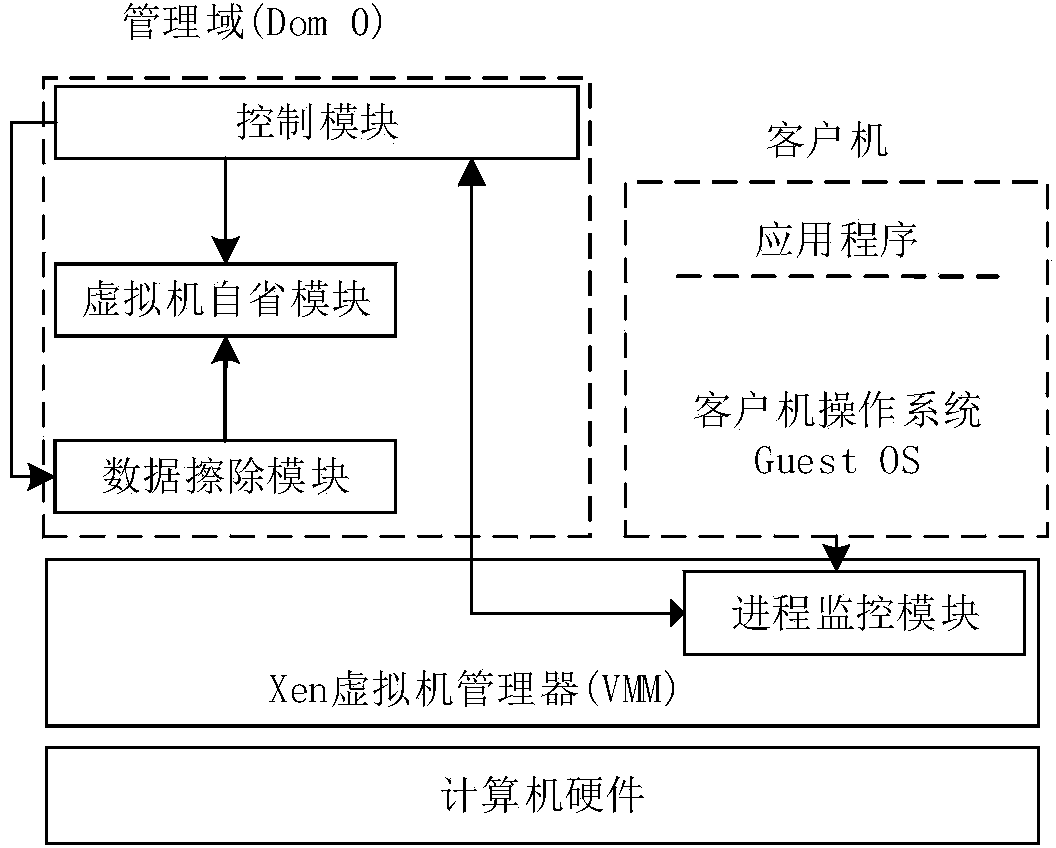
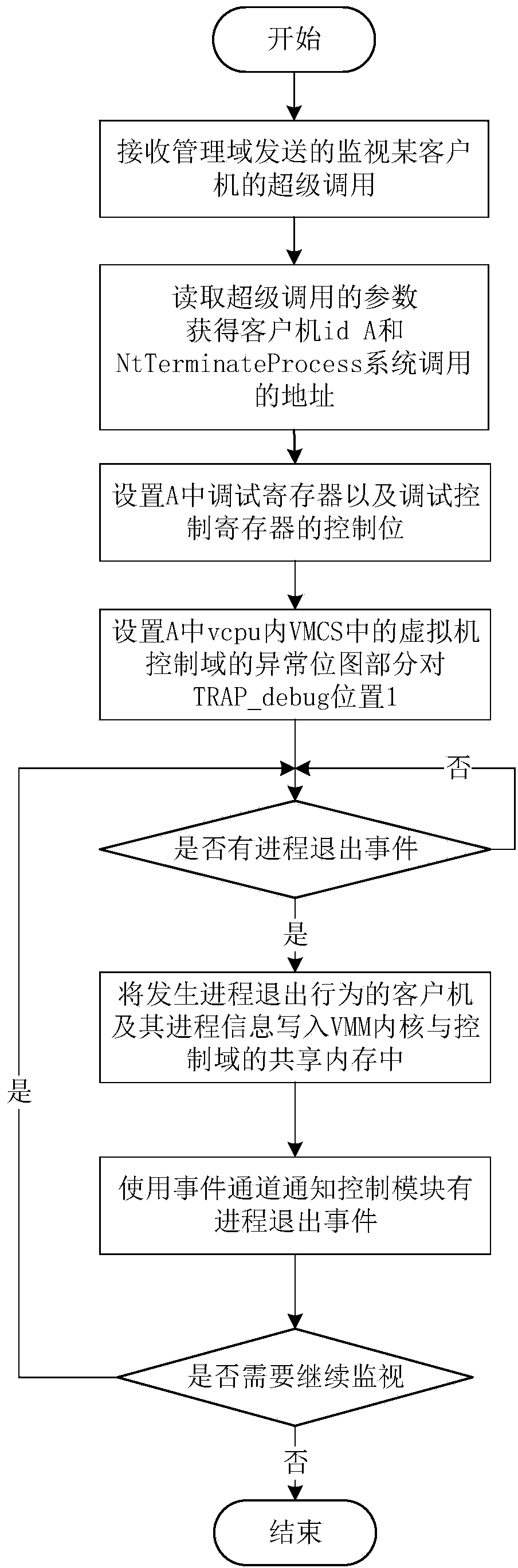
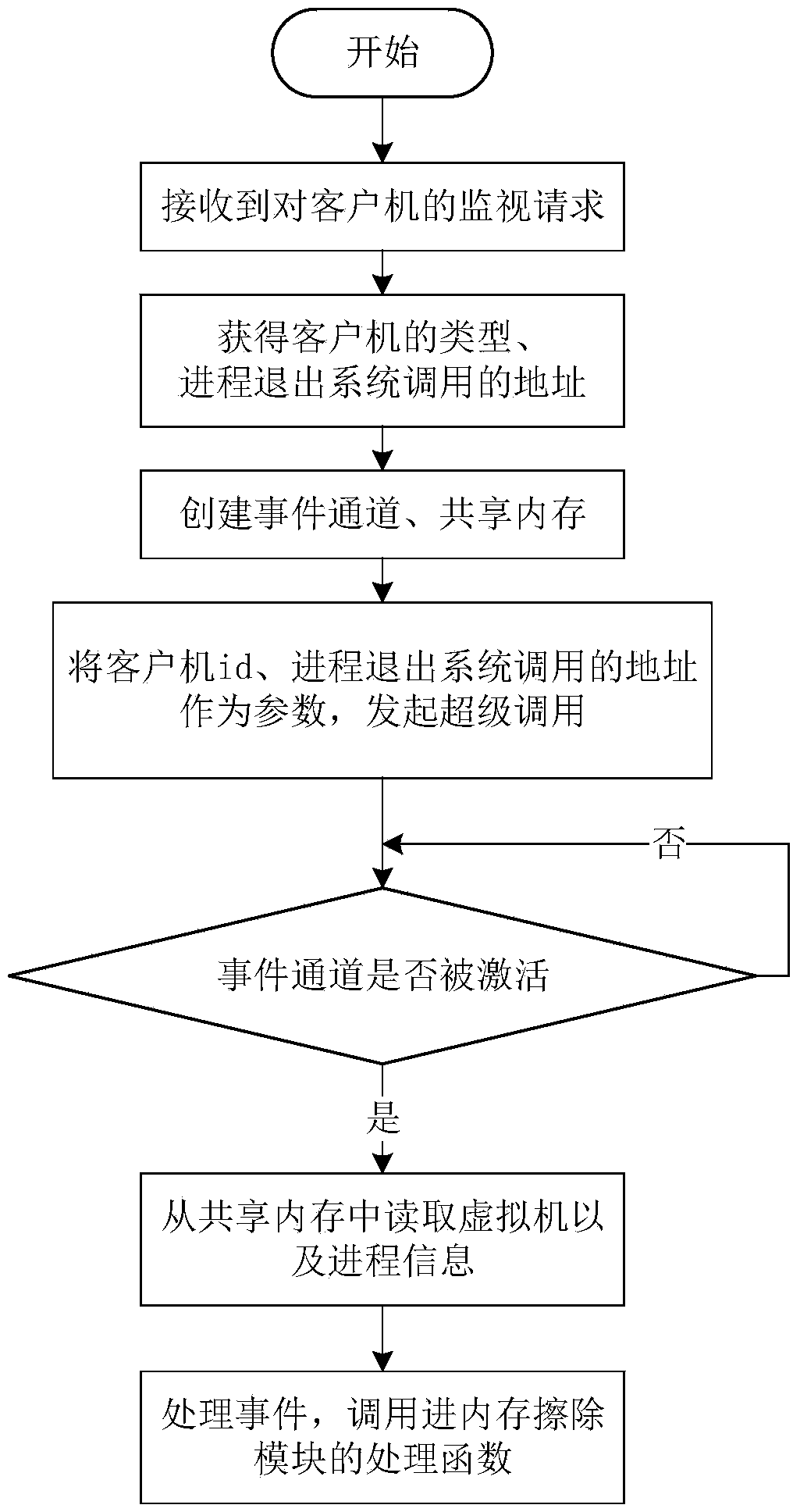
[0025]How to avoid the leakage of sensitive data in the cloud environment is a matter of great concern to both cloud service providers and users. The invention utilizes the virtualization technology to realize erasing the data area of the process when the process running in the client computer exits, and reduces the threat faced by the sensitive data when the user client computer is running from the perspective of shortening the time window for sensitive data leakage. The memory space of the running process in the client can be divided into code area, global data area, heap area and stack area. The user's sensitive data may be stored in the global data area in the form of global variables or static variables, or in the stack area in the form of local variables, or in the heap area in the form of dynamic application variables. Considering sensitive data ( Keys, passwords, etc.) are rarely hard-coded into the program in the form of static variables, and the stack area frequent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com